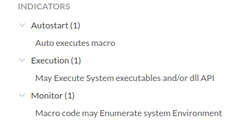
The Ragnarok ransomware gang had been around since 2019, and suddenly ceased operations today, posting a universal decrypter and instructions on how do use it.
What does this mean for the risk of ransomware? Not much. This week, we published a blog post about BlackMatter, a newcomer to the ransomware space. This is just the normal revolving door of ransomware operators, all following the same ransomware-as-a-service business model, using the same tactics, and trying to put controls in place so their affiliates don't target anyone that results in too much attention for the operators.
Netskope protects against ransomware using a multi-layered approach that includes signatures, machine learning, static heuristics, and sandbox analysis to prevent ransomware from making its way onto any of your endpoints. One of the most common ransomware delivery tactics we are actively blocking is ransomware delivered as next-stage payloads by malicious Microsoft Office Documents. Our Office Document Analyzer (part of our Advanced Threat offering) was built specifically to identify day-zero malicious Office documents using a combination of heuristics and machine learning. This screenshot shows a typical detection, which uses the name Gen.Malware.Detect.By.StHeur.MsOffice
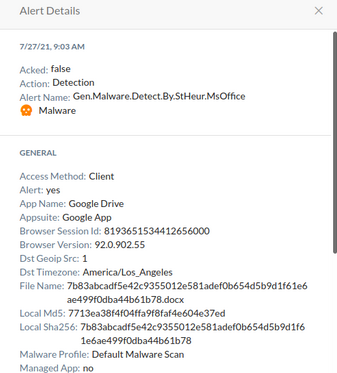
The details illustrate the reasons why the sample was detected: