
Netskope introduced REST APIs for Netskope Private Access earlier this year in R91. These REST API endpoints allow for networking and security teams to automate application onboarding, infrastructure management, and policy for Private Access. Now if you aren’t familiar with Netskope Private Access, you can find an overview here. Netskope Private Access essentially has three key components used to manage access to your enterprise applications:
- Publishers are lightweight virtual machines that broker access to your internal applications by connecting to the Netskope cloud. Publishers are supported in public clouds including AWS, GCP, and Azure along with private data center virtualization such as Hyper-V or ESXi. Additional platforms are supported as well.
- App Definitions are Netskope objects used to determine the hostnames, ports, and IP addresses that your end users can access via Netskope Private Access.
- Real-time Protection Policies grant or deny access to your enterprise applications based on a combination of device posture, app definitions, users, groups, and OUs.
The good news is that Netskope has a robust REST API that allows you to automate or script the management of the first two objects (Publishers and App Definitions) and our support for application tagging allows you to automate real-time protection policies as well. For example, Netskope provides CRUD operations for both Publishers and App Definitions. Available Publisher operations include the ability to manage Publisher lifecycles from creation all the way to deprovisioning.
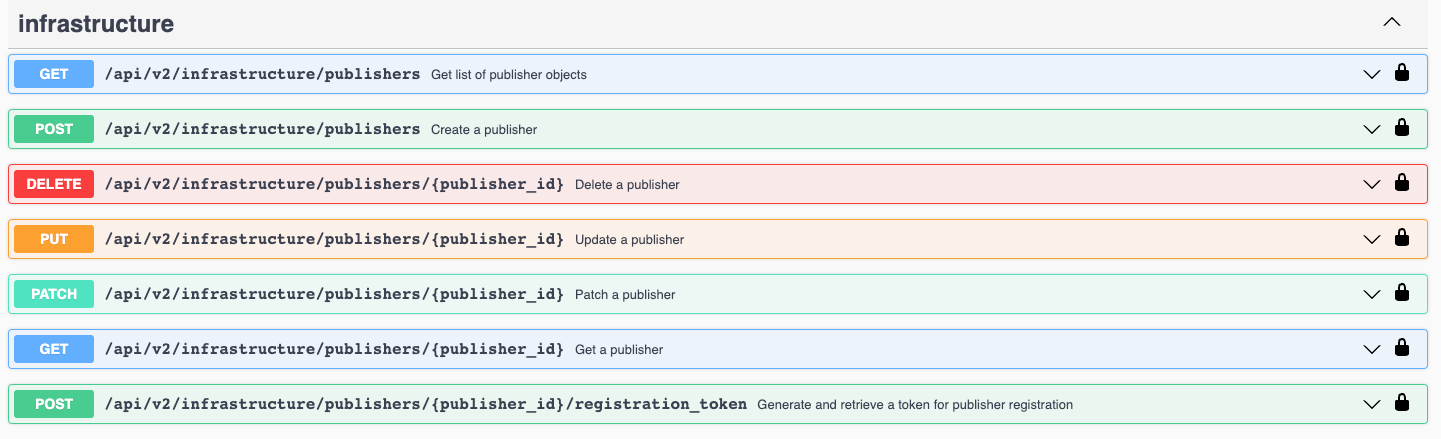
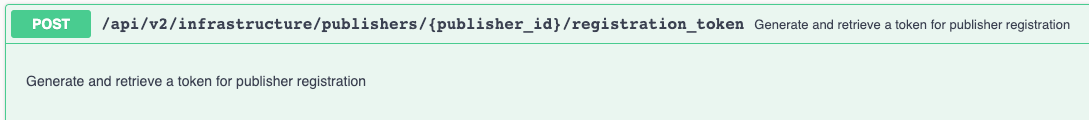
This includes creating the first time registration token for initial Publisher registration and onboarding:
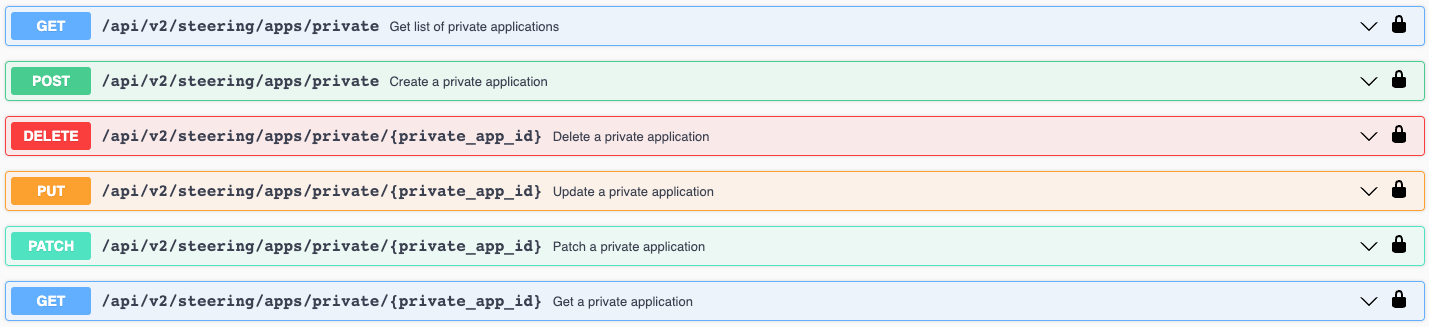
APIs for App Definitions include similar CRUD functionality to manage the full lifecycle of Private Applications including initial onboarding:
These APIs allow you to manage both the infrastructure (Publishers) and policy objects (App Definitions) used in Netskope Private Access. You can use your own custom scripts and tools to take advantage of these but Netskope has also created a number of prebuilt integrations with some of the most popular automation solutions available including:
- Terraform
- Provider
- Introduction to the Netskope Terraform Provider
- Managing Netskope Publishers in AWS using Terraform
- AWS Autoscaling
These integrations are tailored to public cloud environments but the Terraform provider has functionality for general Publisher and App Definition management so you can still leverage them even if you aren’t using a public cloud provider. For those of you leveraging public cloud, these tools allow you to automatically provision and deprovision Netskope components that can enable access in dynamic environments. The video on this post allows you to see this in action with Terraform and Amazon Web Services along with a general overview of our automation capabilities. As a quick example of how this can enable end to end automation to provide access to applications, I have an EC2 instance in AWS that I need to provide access to:
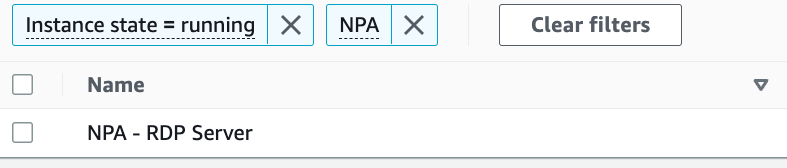
This host has no connectivity to my other networks and is not publicly available. I’ve written a short Terraform configuration that performs the following steps:
- Provisions an instance of the Publisher into the AWS VPC where the EC2 instance and registers it to my Netskope tenant:
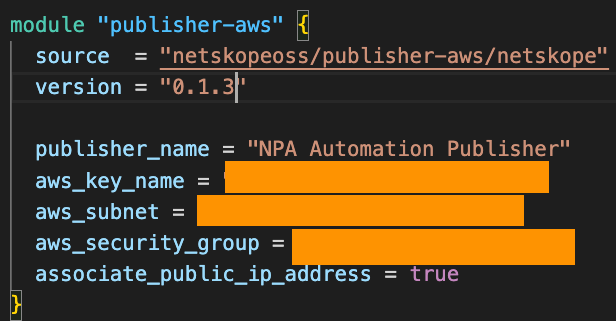
- Creates a new App Definition with a tag and assigns the newly provisioned Publisher to it:
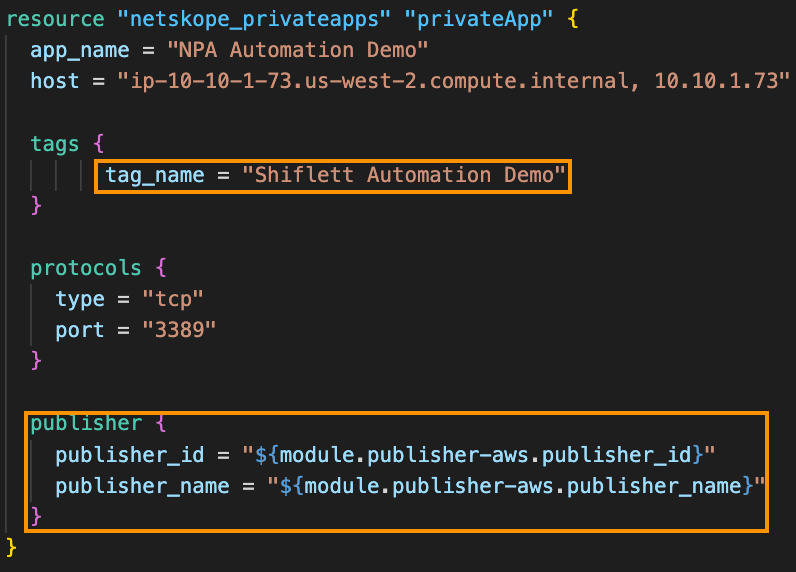
Now when I execute the terraform apply command, Terraform proceeds with the creation of 3 objects (Publisher EC2 instance, Publisher object in my tenant, App Definition in my tenant):
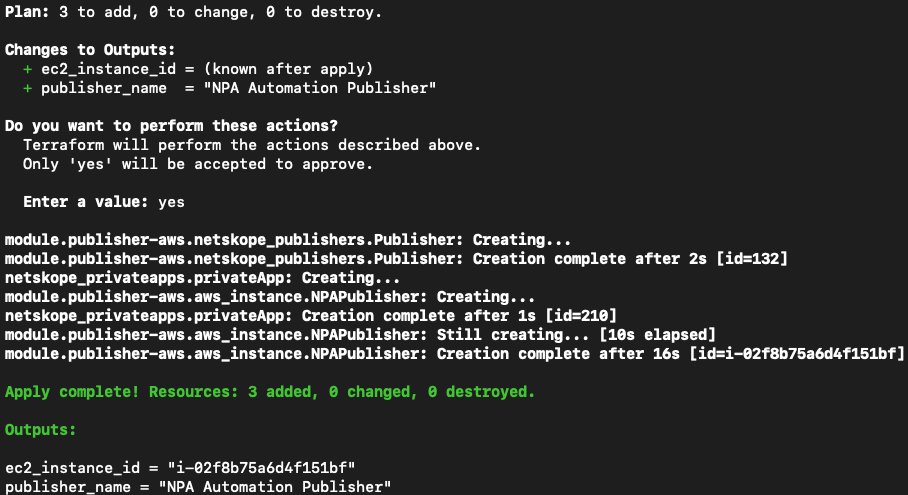
In my tenant, there is now a registered, connected Publisher and an App Definition:
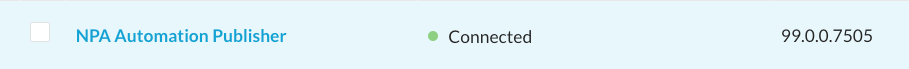

You’ll notice that this app has a tag assigned to it called “Shiflett Automation Demo.” Since I’ve tagged this app and I have a Real-time Protection Policy that grants a specific user access to the apps with this tag, my end user will automatically get access to this host:
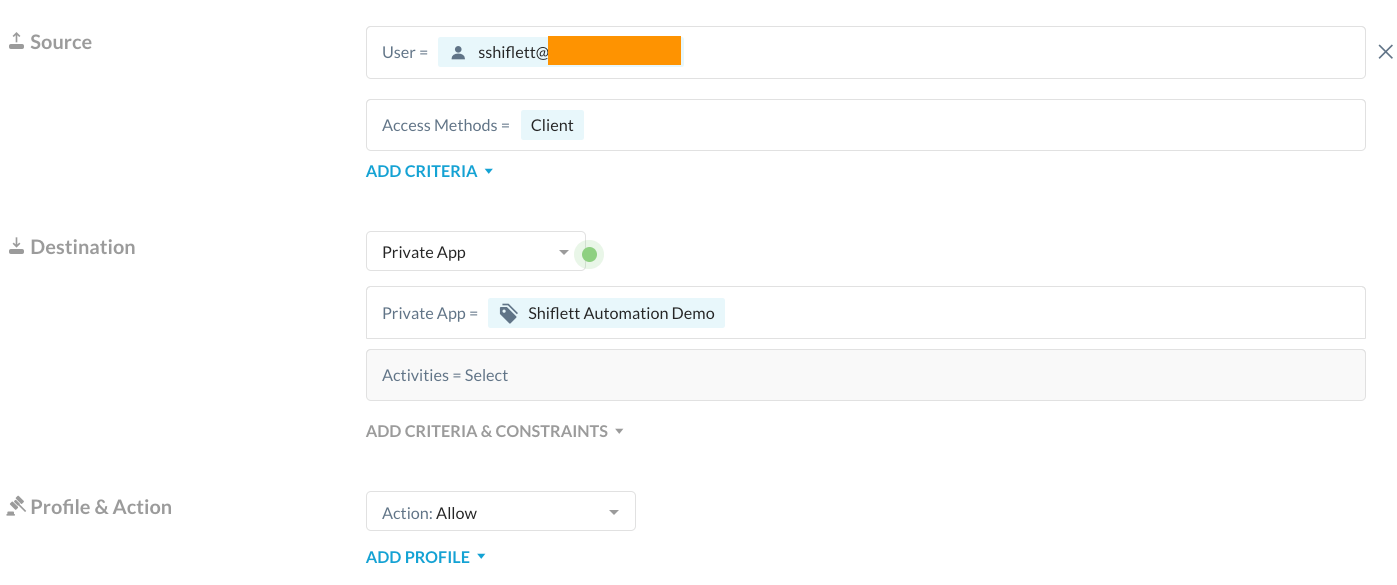
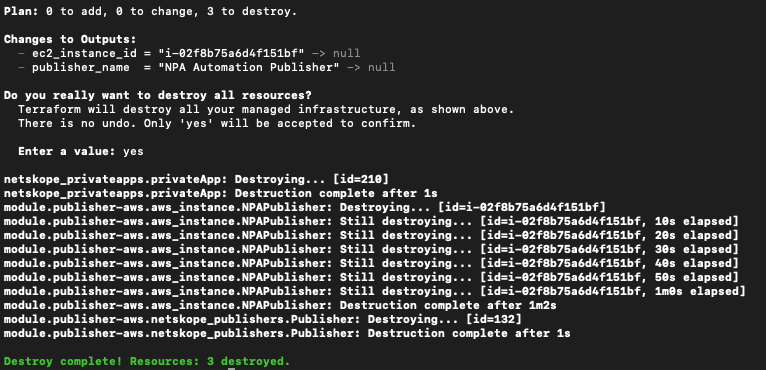
Now to wrap this up, we mentioned that the REST APIs support CRUD functionality so let’s see the delete functionality in action. If I run a terraform destroy command, it will use the Terraform provider and Netskope REST API to delete the three objects we created:
For a full overview of the available APIs you can navigate to the documentation in your specific tenant under Settings > Tools > REST API V2 > API Documentation or here.


