In our latest blog, we explore IAM best practices and AWS and highlight two findings:
- The majority of organizations don't enforce access key rotation for their IAM users.
- The majority of organizations aren't deleting inactive IAM accounts.
We access keys that were nearly a decade old and many IAM accounts that hadn't been used in over a year, exposing a lot of risk surface that can likely be locked down. How can you identify these old access keys and inactive IAM accounts? We have two Security Assessment rules that can help:
Remove/disable inactive user accounts within 90 days
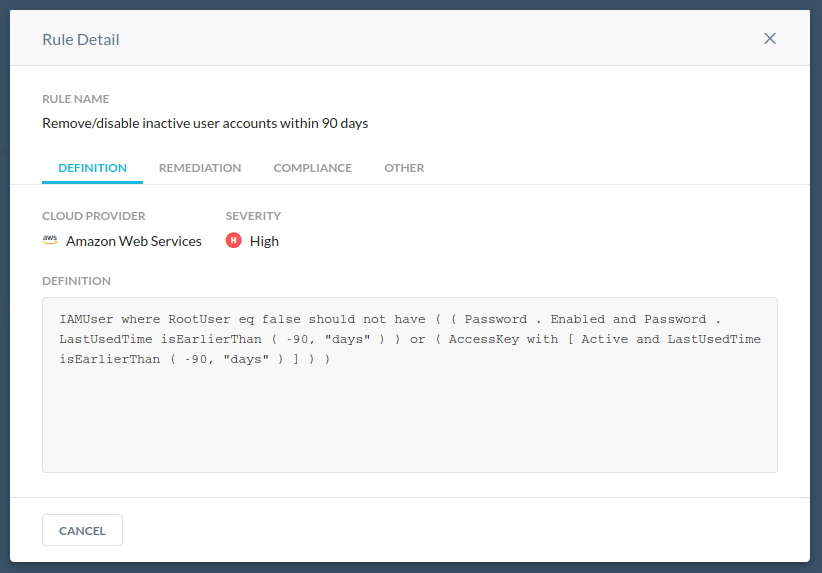
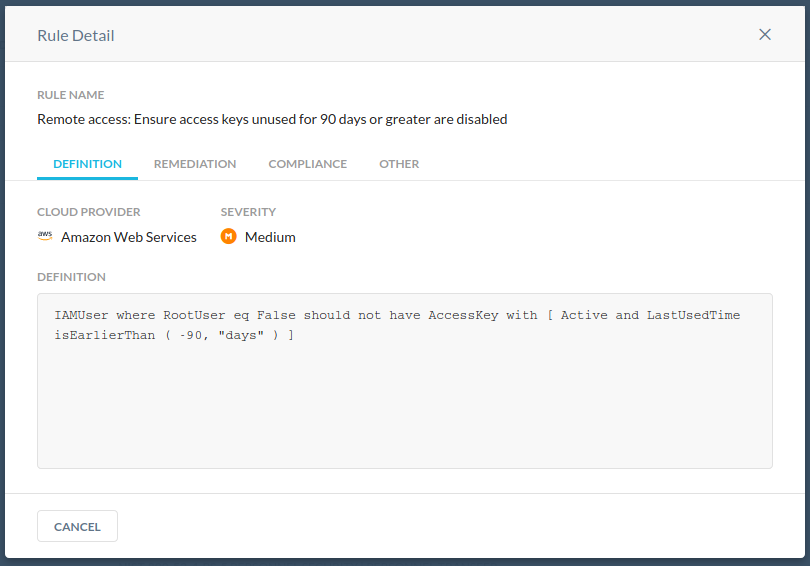
Remote access: Ensure access keys unused for 90 days or greater are disabled
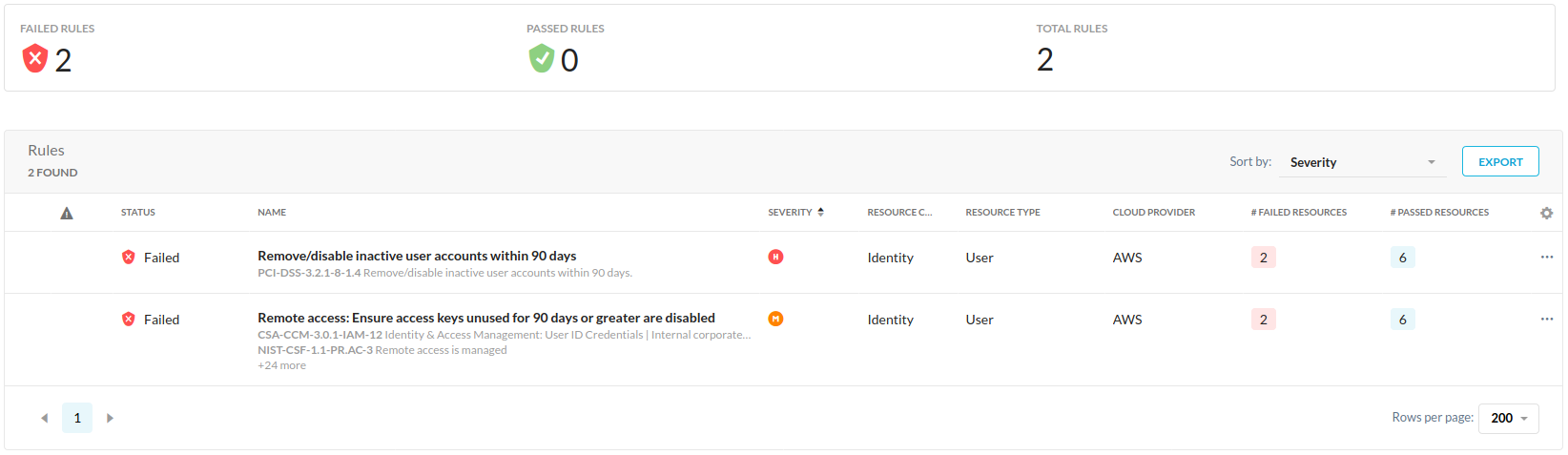
Once the rules have run, you will see the results in your compliance report.
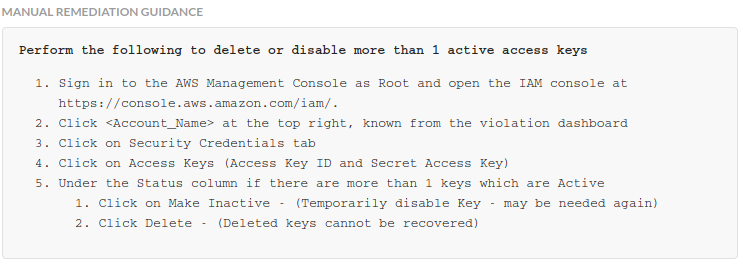
Oops, I have a couple of users in this AWS account that require some cleanup! I'll just follow the remediation guidance to ensure those two rules are marked green next time around.