What is attack surface management?
Attack surface management (ASM) is the continued discovery, classification, and monitoring of an organization's external assets. It is crucial that teams leverage the hacker mindset to look for attack vectors into the organization when performing ASM in order to prioritize the most risk prone assets for remediation. To get the most out of an ASM program, teams should leverage tactics techniques and procedures (TTP) in use by threat actors. Not only is this good practice to develop the hacker mindset but also determine the hygiene of the current security implemented by the organization. Risk in ASM typically comes from three common areas which are vulnerabilities, misconfigurations, and weak/default credentials. The goals of attack surface management are identifying and gauging the risk, and reducing the attack surface. Attack surface management aims to find what assets are being exposed by the applications, networks, and devices in your environment.
Understanding your attack surface
Understanding an organization's attack surface is an important piece of being able to effectively identify and gauge the risk of exposed assets. Organizations have seen their attack surface grow in size but also become more complex due to the propagation of IoT devices, cloud computing, and remote work. Each one of these can lead to the organization having a shadow asset, an asset that lacks visibility by the organization's cybersecurity team, leading to an unknown attack vector. This is why all ASM programs should be continually scanning for previously unknown assets within the organization's environment. However not all assets in an organization are easily visible to ASM tools.
Many ASM scanning tools will focus on the externally facing server and cloud infrastructure of an organization. However another good source of asset information can be pulled from the user endpoint. While endpoints, like an individual's workstation, are not externally facing, like a web server, they are still part of the organization's attack surface that will be targeted by threat actors. A well-developed ASM program should be able to import EDR data from endpoint assets into the ASM program so that an organization gains visibility into the organization's endpoints.
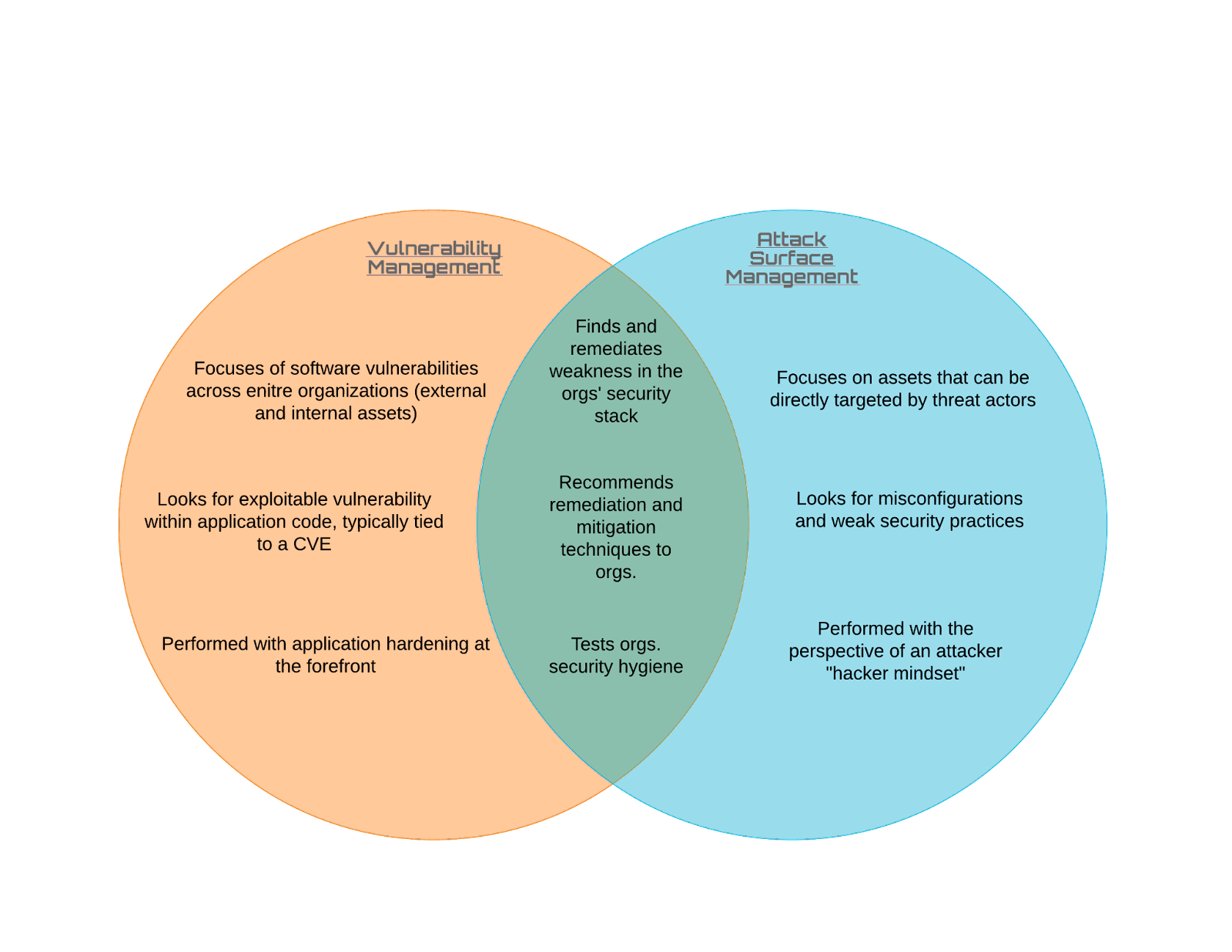
Vulnerability Management vs. Attack Surface Management
Attack surface management tools are similar to vulnerability scanners, as both utilize scanning for the purposes of identification of applications, services and vulnerabilities. It is important to understand the key differences in these tools in order to build out a successful ASM program. ASM tools are designed around finding externally facing known and unknown assets that are in an organization environment. ASM tools do not need to be installed on hosts and use ASN ranges, domain registries, and OSINT on the organization to find organizations assets. ASM tools may also contain their own risk assessment based on potential vulnerabilities or open ports. Even though ASM tools can help a team in remediation of vulnerabilities they should not be used as a replacement for vulnerability scanners.
While building an attack surface management program there are many parallels to vulnerability management. Teams should view ASM as a way to augment their vulnerability management programs, not necessarily replacing it. ASM will discover unknown assets that could be fed into your vulnerability scanner. In addition, your vulnerability scanners can be used as an additional source of asset information. ASM should be viewed as a branch of vulnerability management that is specifically focused on the attack surface of the organization, while the vulnerability management part of ASM focuses on the software vulnerabilities found.
Automation and Operationalizing ASM
Automation in ASM is growing more important than ever with organizations' attack surface becoming larger and more complex. ASM tools and vulnerability scanners help by automating a lot of the work that goes into a good ASM program. Here at Netskope, we monitor thousands of IPs everyday to accommodate and scale to demand. Automation is key and the best place to start is with asset seeding through available tools you may already own and use. We leverage APIs within our own tools to fully seed our asset information multiple times throughout the day. Teams should consider daily scans at a minimum as popular vulnerabilities could be weaponized within hours. Automation should be incorporated into asset updating, report generation, and ticket creation to minimize possible exposure times.
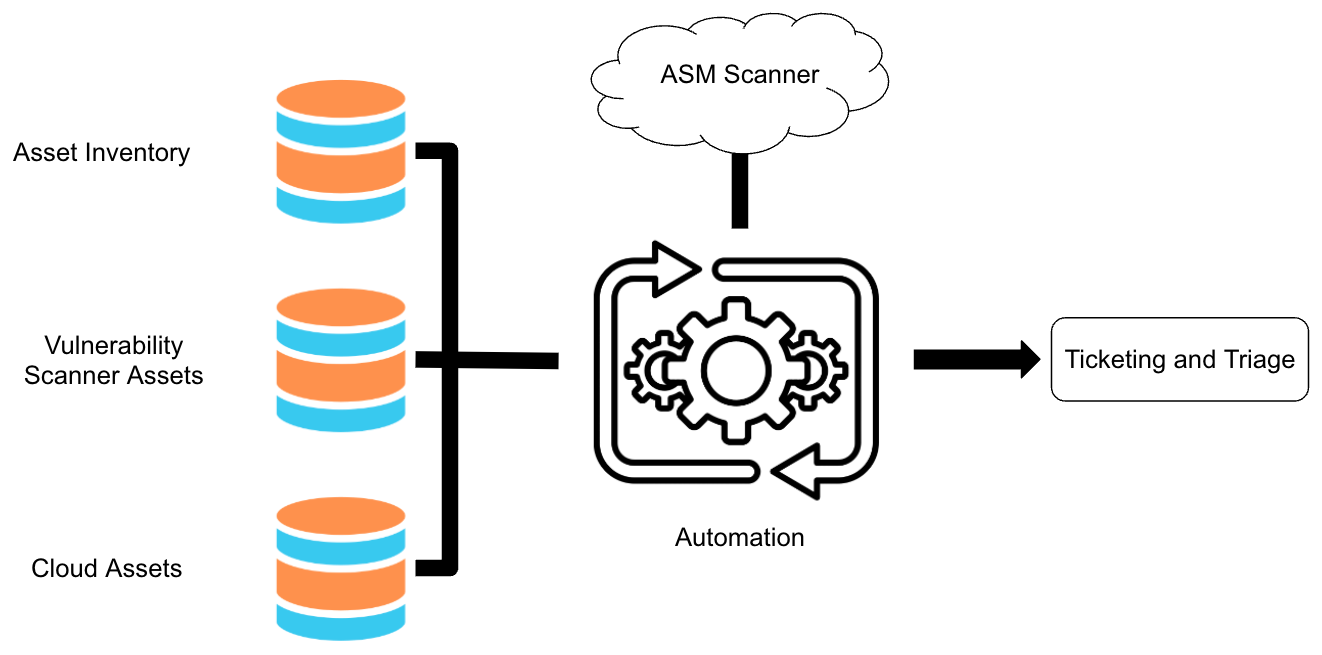
Here at Netskope the Threat and Vulnerability Management team has built out an attack surface management program with full automation from discovery to ticket generation in order to best secure Netskope’s attack surface. Using a combination of ASM tools, vulnerability scanners, and in-house built tools for scanning, credential brute-forcing, and analyst notifications, we are able to manage more than 5,000 assets on our attack surface with a team of four.


