Salesforce is an enterprise cloud computing company that provides business software on a subscription basis. The company provides on-demand customer relationship management (CRM) solutions such as Sales Cloud, Service Cloud, Data Cloud, Collaboration Cloud, and Custom Cloud. As the Customer Zero team (CISO group), we are currently monitoring and securing access to Salesforce internally with a breadth of products that are developed and maintained by the development and QA teams. These capabilities include areas such as client enforcement, inline protection, API-enabled protection, SaaS security posture management (SSPM), and Cloud Firewall, to name a few. In this guide, we will provide a perspective of how Netskope’s products and capabilities are used internally for securing enterprise data.
Real-time Protection
- We are restricting access to the Salesforce app for Netskope employees through client enforcement, whereby access to Salesforce would be granted only if users are connecting to our corporate tenant, making use of dedicated egress IP ranges. More details regarding this can be found here.
- This helps achieve two goals for the Customer Zero team. One is to secure access to Salesforce through the Netskope client. The other one is to initiate more users to connect to our corporate tenant via the client so that their web access is subject to our policy and security stack.
Access is locked out when a user is not connected to corp tenant via NS client or when the client is disabled.
- Traffic originating from managed endpoints [Windows, Mac, and Linux OS], is currently being steered via the Netskope Client to the cloud, where deep inspection takes place, in the form of policies.
- This gives us the capability to manage the traffic to Salesforce in a granular manner.
- Netskope’s Cloud Confidence Index (CCI) has analyzed and classified Salesforce as an enterprise application, and provides an overview of the activities that are identified by the Netskope proxy for inline traffic. These activities include:
- Create
- Delete
- Download
- Edit
- Follow
- Invite
- Login Attempt
- Login Failed
- Login Successful
- Logout
- Post
- Rename
- Send
- Share
- Unshare
- Upload
- View
Policy capabilities currently in place:
For Salesforce, some of the real-time policies in place:
- Threat protection (Cloud Threat Exchange) to block upload and download activities based on the CRM, Technology, and Business categories.
- This ensures that malware, ransomware, and redirects to malicious sites are guarded against.
- DLP profile with Github file hash list to alert upload and download activities within CRM, Technology, and Business categories.
- This profile is looking for known sensitive data being transferred outside of the organization.
- Activity tracking DLP profile to alert uploads and downloads within CRM, Technology, and Business categories.
- This policy ensures compliance with Privacy and PCI content.
- Alert policy as part of IPS.
API Protection
Netskope API Data Protection works by directly connecting to a cloud app using the APIs published by the app, and uses OAuth to gain delegated access to the app.
Netskope's API Data Protection provides a complementary deployment model to provide cloud visibility, policy, and data security services by directly connecting to a cloud service using the APIs published by the cloud services. The API Connector works in conjunction with the Netskope cloud proxy to provide defense-in-depth security services.
For Salesforce, we currently have the following API protection policies:
- DLP - PCI policy to alert all sharing options for all file types.
- DLP - certificate and password check to alert all sharing options for all file types.
This ensures data is protected in the Salesforce instance at all times.
SaaS Security Posture Management (SSPM)
SaaS Security Posture Management (SSPM) is a service that provides an organization insight into the security posture of their SaaS applications. According to Gartner, SSPM is defined as “tools that continuously assess the security risk and manage the security posture of SaaS applications. Core capabilities include reporting native SaaS security settings' configuration and offering suggestions for improved configuration to reduce risk."
Some of the benefits of SSPM include:
- Continuous security assessment into policy violations of SaaS apps.
- Guided remediation of misconfigurations.
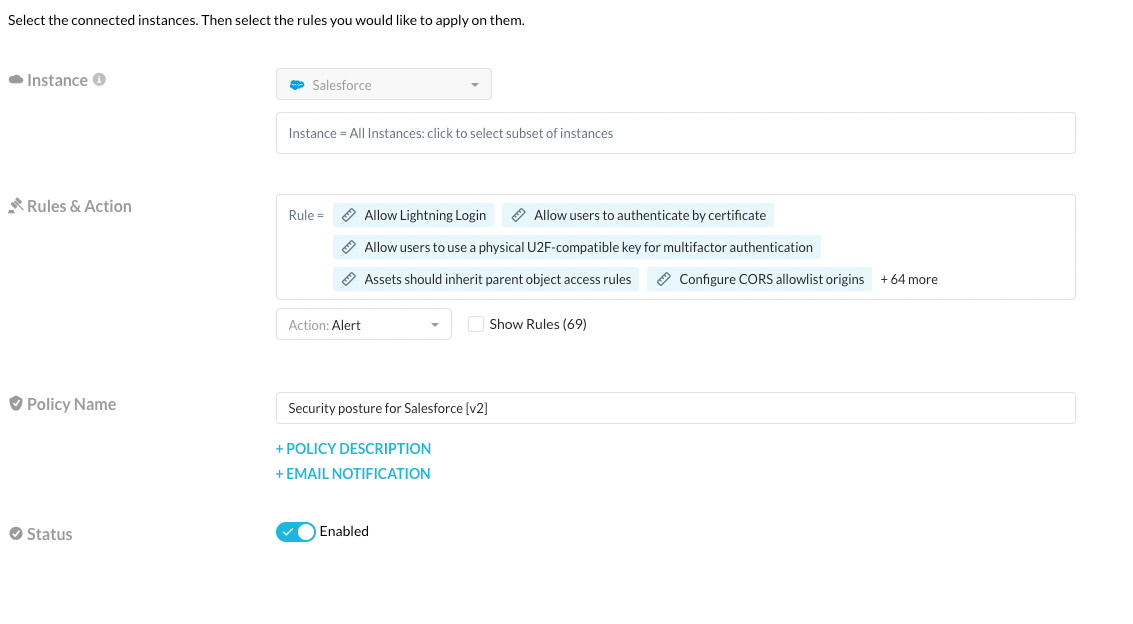
Each of these rules satisfy the following compliance standards:
- CSA-CCM-4.0
- GDPR-2016-679
- HIPAA-1996
- ISO-27002-2013
- NIST-CSF-1.1
- NIST-800-53-4
- PCI-DSS-3.0
- AICPA-SOC-TSC-2017
We have enabled the next gen SSPM flag on our tenant, which currently supports enhanced features for Salesforce security posture management. This provides some new features such as:
- Visibility to SaaS apps and sub resources (in Inventory page)
- Powerful Netskope Governance Language (NGL) which is a lot easier to use and also helps hunt down details such as:
- The name of all users who have access to any connected apps on Salesforce
- Names of users having access to a particular connected app installed on Salesforce
- A list of all connected apps a particular user has with access to on Salesforce
- Ability to create custom rules quickly based on NGL queries
- Revamped simplified Policies page (doing away with ‘Profiles’)
- Support for cross-application rule
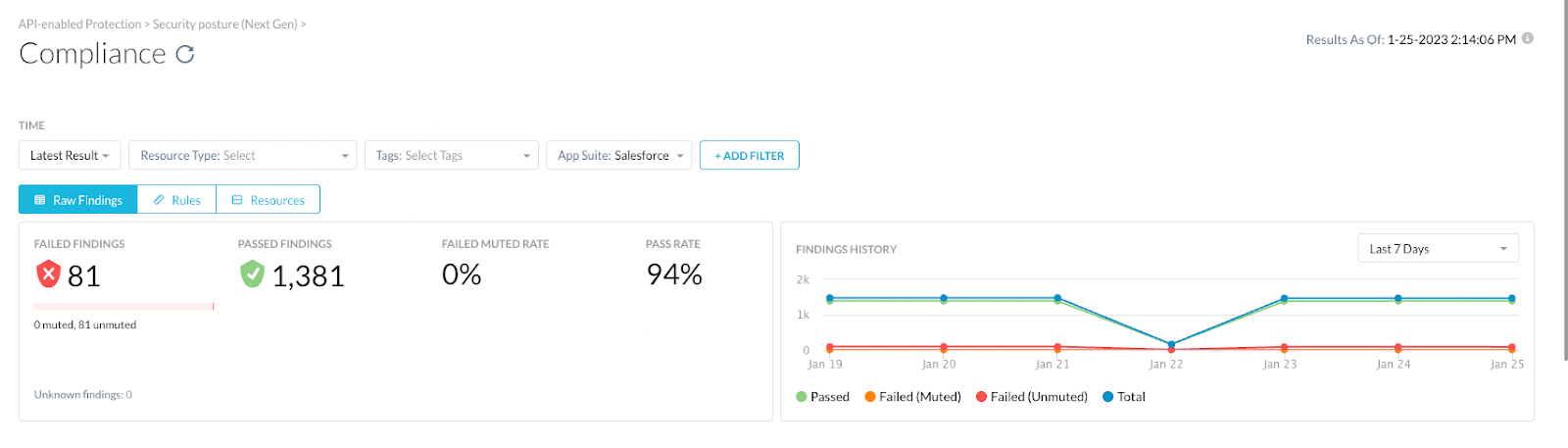
- There is also a findings history visualization available with the next gen feature. This shows the status of compliance findings for Salesforce over the last seven days visually.
- When checking the rules that failed, we can see the NGL definition the rule is based on:
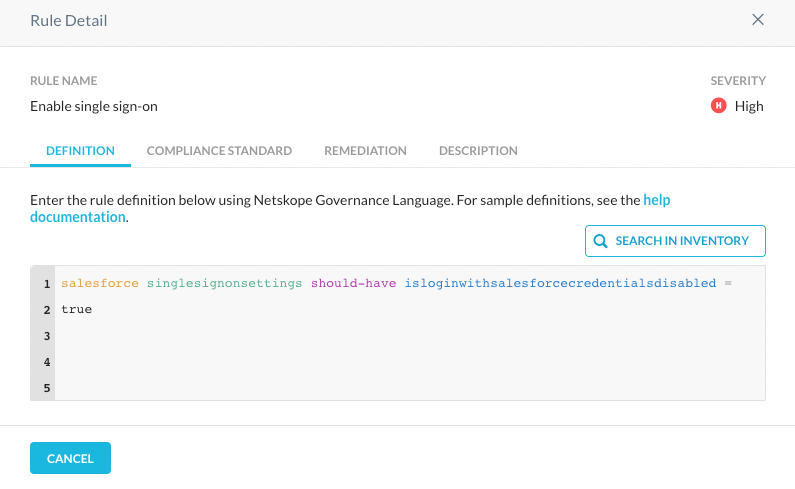
- The definition associated with each rule gives a good reference for searching the inventory for finding resources that don’t satisfy the criteria the rule is checking.
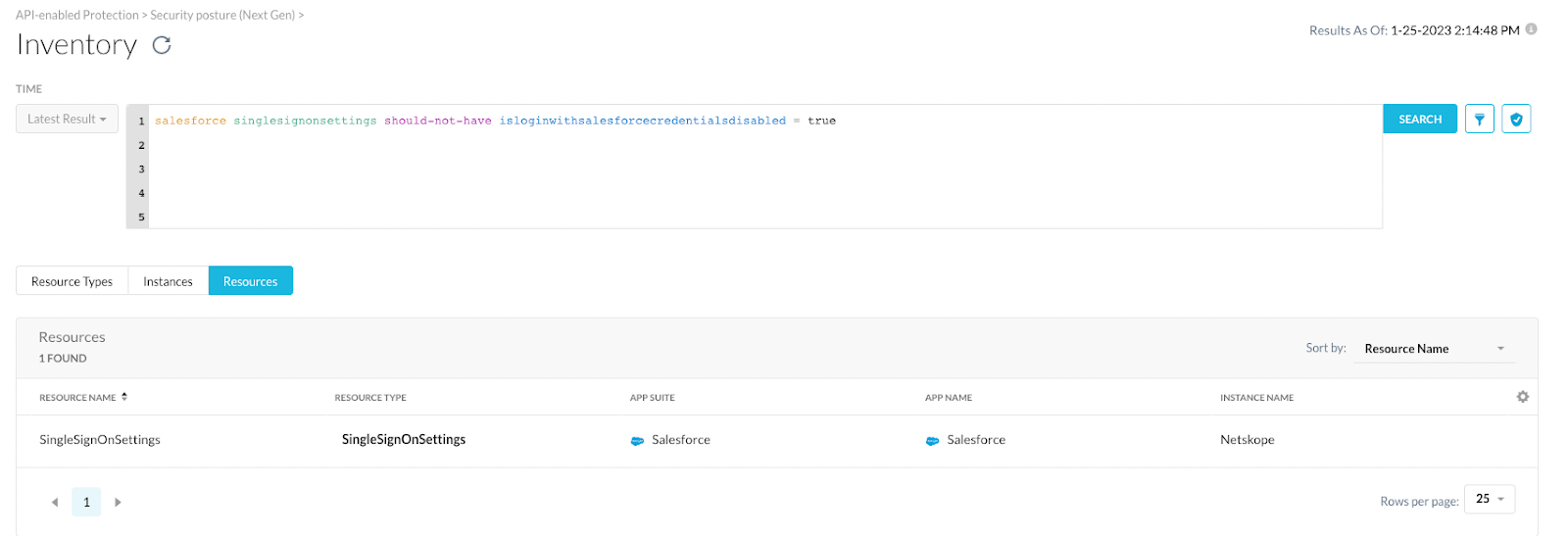
- Netskope begins building an inventory within five minutes of the account configuration. Subsequently, inventory updates are run at the same frequency as the compliance assessments. At the time of the account setup, you can choose to run the compliance assessments every 15 minutes, 30 minutes, 45 minutes, and 60 minutes.
- Reports can also be generated for further analysis of compliance findings.
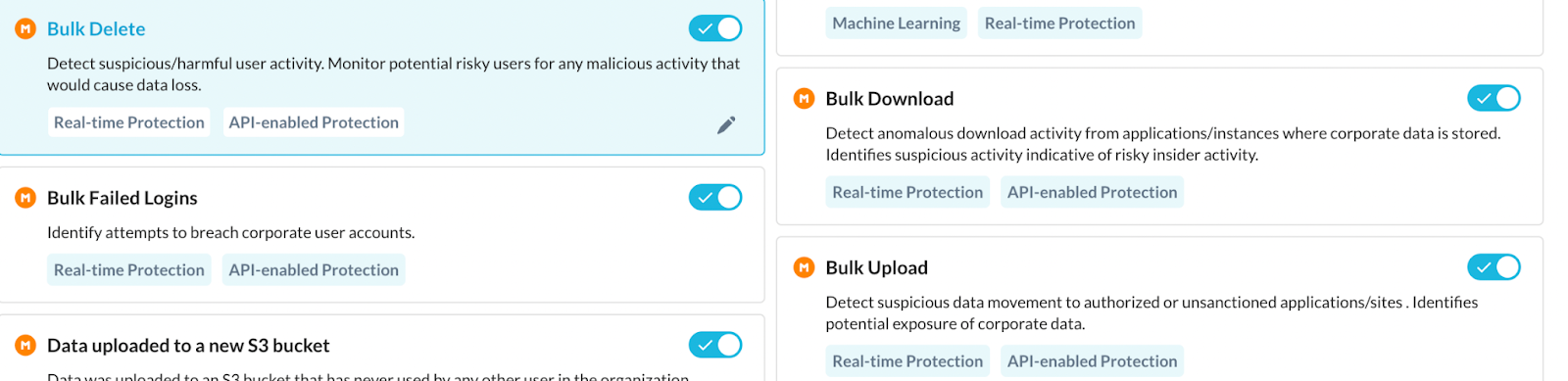
User Behavior Analytics
For both real-time as well as API-based Salesforce traffic, machine learning algorithms can be used and classified, as part of Netskope Behavior Analytics. Netskope's User Behavior Analytics tool looks at patterns of human behavior, and then applies algorithms and statistical analysis to detect meaningful anomalies from those patterns—anomalies that indicate potential threats. Instead of tracking devices or security events, behavior analytics track users. There are a set of predefined Behavior Analytics rules that can be used to create policies for detecting any abnormalities in both real-time, as well as API connector-based Salesforce instances. Few of these are mentioned in the screenshot below.
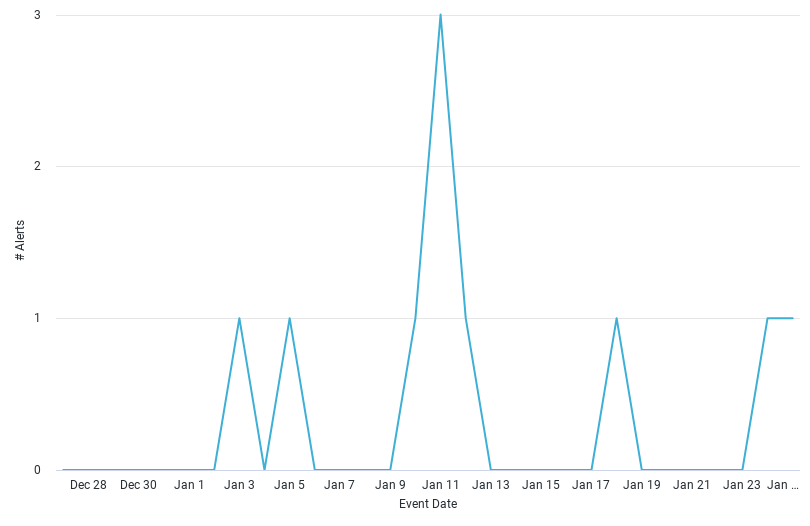
We can see the trend in UBA alerts using Advanced Analytics for Salesforce over the last 30 days.
We would love to know how your team secures Salesforce and other critical SaaS apps using Netskope.


