Summary
With release R99 Netskope introduced a new feature “Periodic Validation on Device Classification” which is very important to enforce Zero Trust principles. Before that release, Device Classification of the client was only accomplished, when client service was started. With the new feature a validation interval can be configured for more frequent device posture checks.
Requirements:
- NS Client version R99 or later is required.
- Please contact your Customer Success Manager, Netskope Support or your Account Team to get this feature enabled.
- Today this feature is disabled by default!
Tenant Configuration
Device Classification Profile
The “Device Classification Profile” is a policy about a single or multiple checks, whether a device is compliant or not. This part of the configuration has not changed and will not be covered in detail in this post. Here is the link to public documentation.
For testing on Windows a simple profile can be created to check if “notepad.exe” is running (managed) or not (unmanaged).
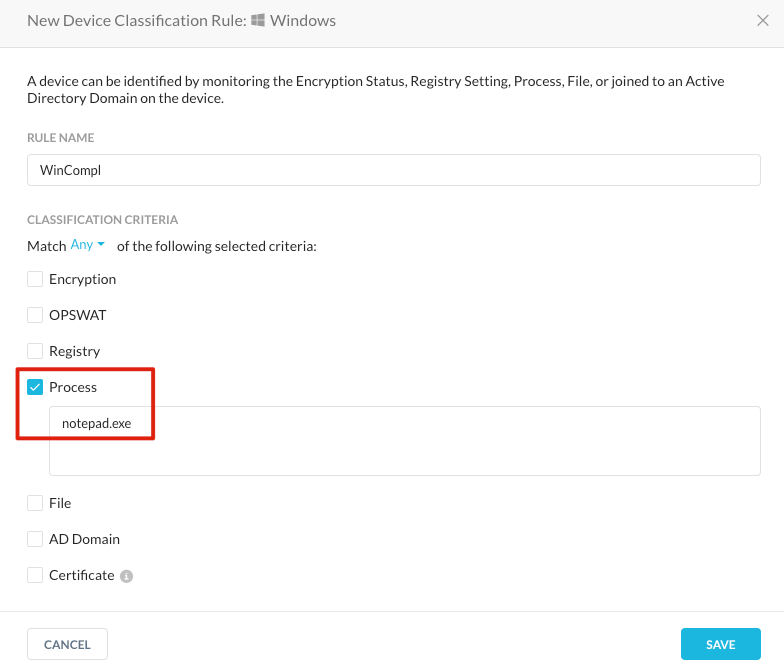
Client Configurations
If the feature is enabled in the Netskope tenant, a new UI option in the client configuration menu under “Settings - Security Cloud Platform - Devices - Client Configurations”. Under the first tab “Traffic Steering” there is a new checkbox “Periodic Validation on Device Classification”. When enabled the administrator can configure a validation interval between 5-120 minutes.
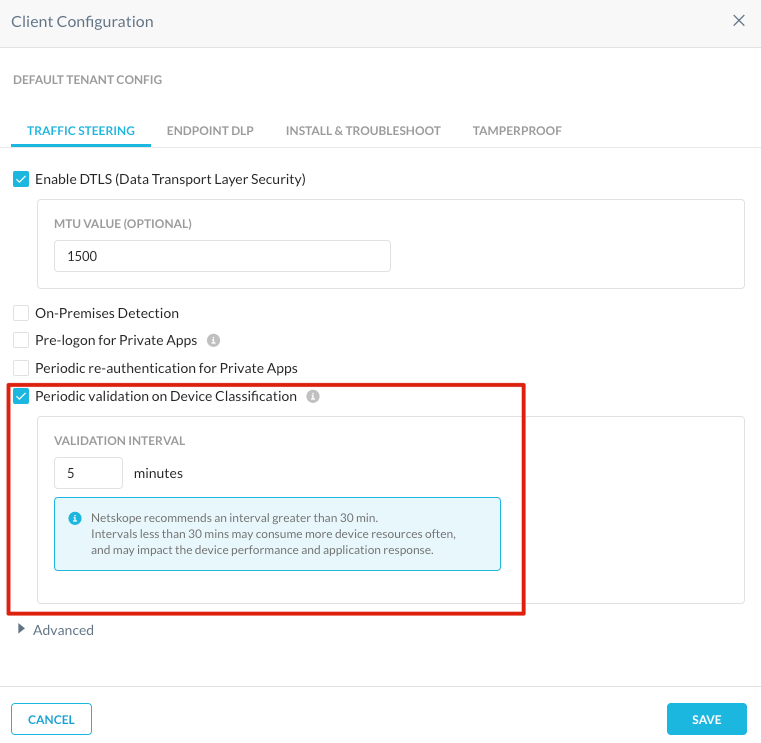
For testing the lowest value of 5 minutes is recommended. If the interval is set below 30 minutes a warning message about device performance is displayed.
Real-time Policy
For testing a simple block policy for the category “Cloud Storage” is used with the source attribute “Device Classifications = Unmanaged”:
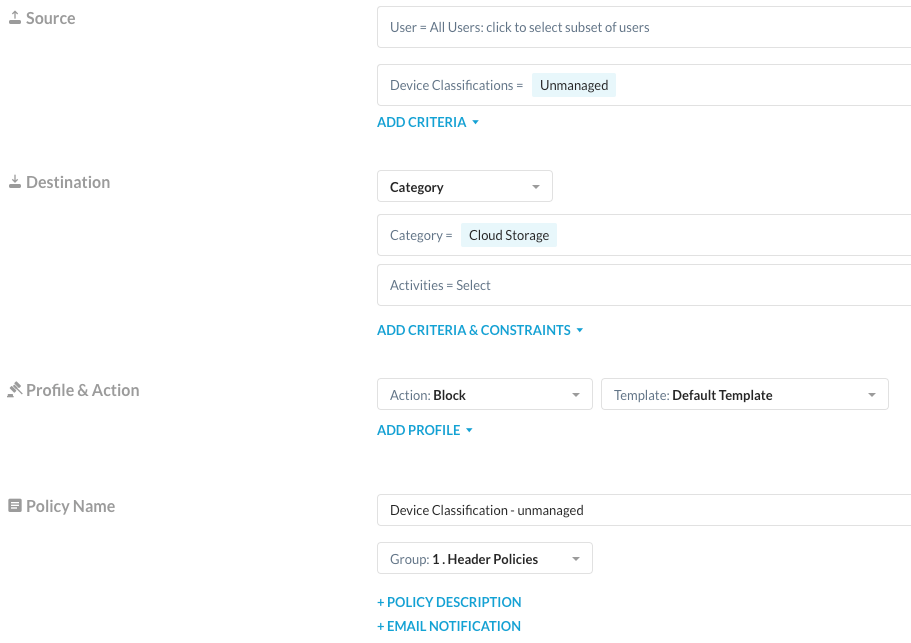
How to test this feature
First verify that the client configuration is up-to-date: Right click on the NSClient icon - Configuration. The new feature will also change the client configuration and therefore the client configuration should be updated.
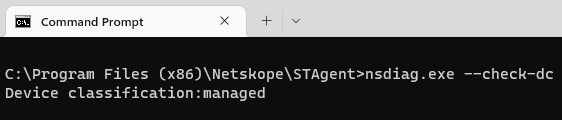
With R99 there is also a new flag for “nsdiag.exe”. The flag “--check-dc” triggers the client to evaluate the device classification policy instantly. With that trick you do not have to wait until the re-evaluation is triggered by the validation interval. “nsdiag.exe” is located for
- Windows in “C:Program Files (x86)NetskopeSTAgent”
- MacOS in "/Library/Application Support/Netskope/STAgent”
- Linux in “/opt/netskope/stagent”
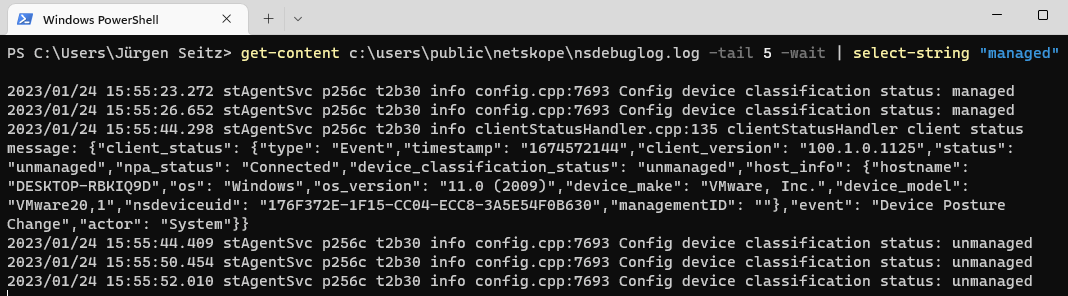
In addition I recommend monitoring the nsdebuglog.log for device classification status changes. Here are sample commands for the different platforms.
- Windows Powershell
- get-content c:userspublic etskope sdebuglog.log -tail 5 -wait | select-string "managed"
- MacOS
- tail -f /Library/Logs/Netskope/nsdebuglog.log | grep managed
- Linux
- tail -f /opt/netskope/stagent/log/nsdebuglog.log | grep managed
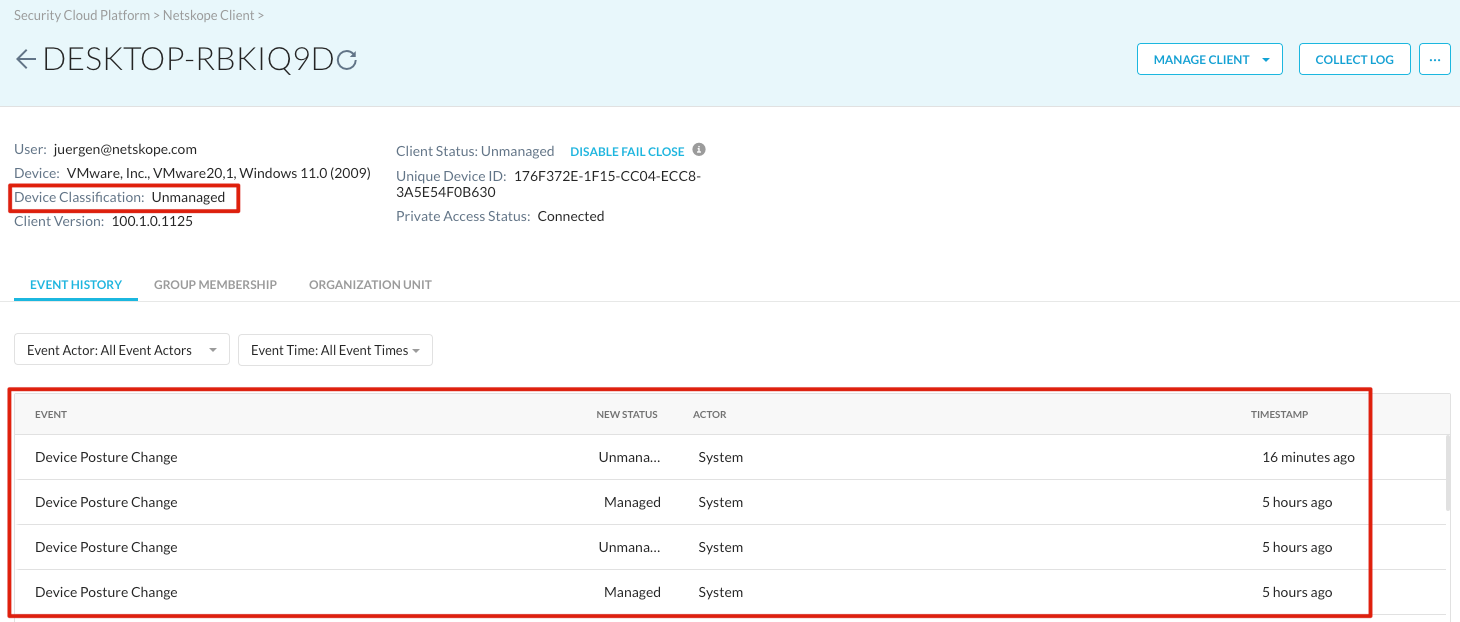
The device status is also instantly reflected in the UI under “Settings - Security Cloud Platform - Devices” in the details page of a device.
Demo Workflow for Windows:
- Notepad.exe is not running
- Device is “unmanaged”
- Access to Cloud Storage services is blocked
- Start Notepad.exe
- Run “> nsdiag.exe --check-dc” or wait for the periodic validation
- Device status will change to “managed”
- Access to Cloud Storage services is immediately allowed



