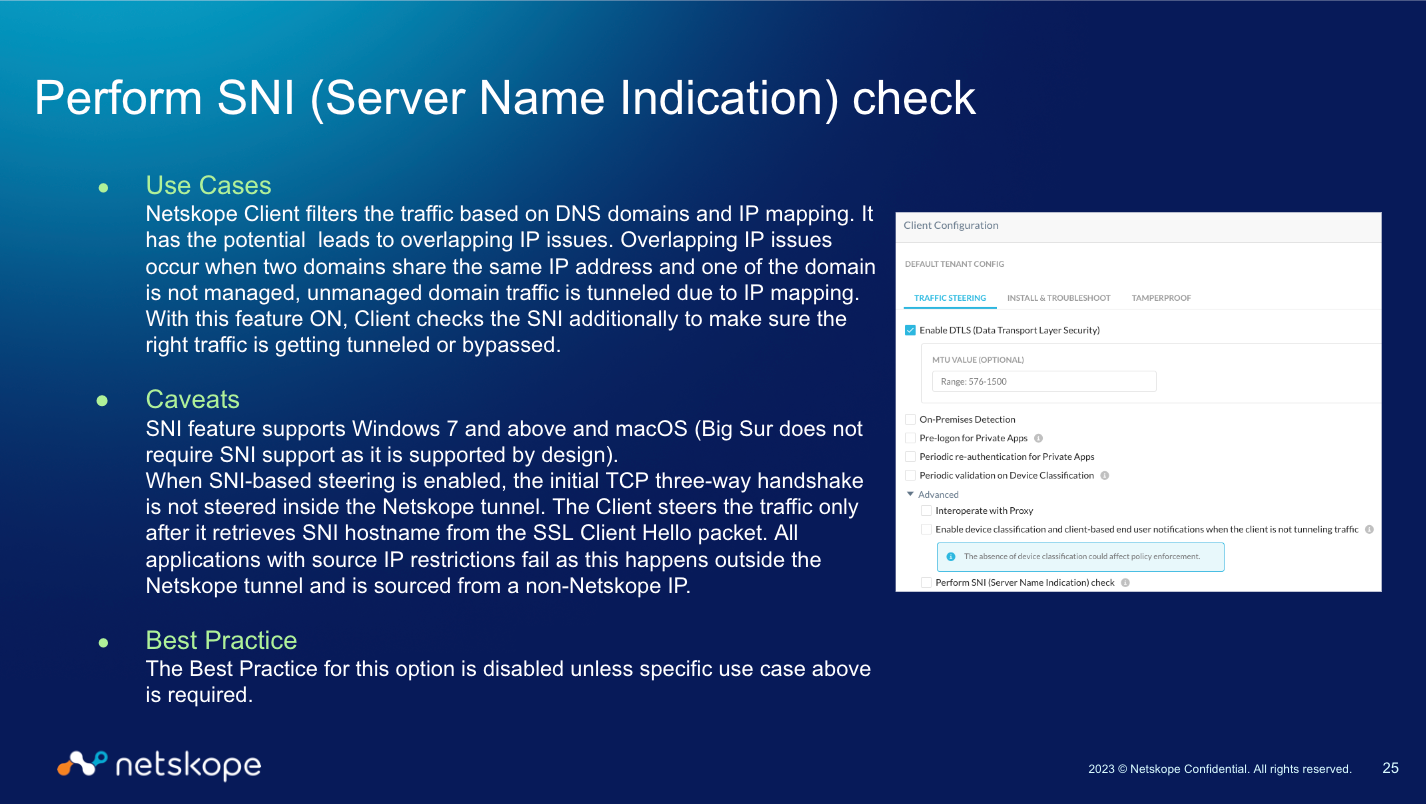
I am looking for thoughts on if people have enabled the setting in the Client Configuration for Perform SNI (Server Name Indication) check ? We are migrating VPN technologies and have noticed some traffic occurring outside of the Netskope tunnel when we do not expect it. We believe this setting to be the reason as it indicates that the initial three-way handshake for traffic occurs outside the tunnel to retrieve the hostname. Additionally we have several third-party applications that we use Source IP allowlisting with and believe that this may be causing issues with some of those as well. This was enabled (I believe) during our initial configuration and now want to gather pros and cons of having it enabled/disabled?
Solved
SNI Checking at the Client Configuration level
Best answer by Fatehd
Hi Twoods,
if the perform SNI is checked So, the SNI check is performed outside of the NS Tunnel.
It does a handshake directly with the remote server and sends the TLS Client Hello waiting for Server Hello with SNI, then sends RST.
That all happens outside of NS Tunnel. Then once it knows the SNI, it looks up what it should do with that traffic (tunnel/bypass etc) based on config and takes the action for the full flow.
In short answer here is - do NOT use this option unless you have a scenario that requires it(which should not be the case in vast majority of deployments).
This topic has been closed for replies.
Sign up
Already have an account? Login
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Login to the community
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.