Hi everyone, happy Friday/weekend!
I just have a couple of things that I wanted to ask and get answers. I've searched the documentation and have found no information regarding my question, though I might have used incorrect keywords
1. If I am steering all web traffic to Netskope, what happens to web traffic that did not hit any policy ? Does Netskope have implicit deny?
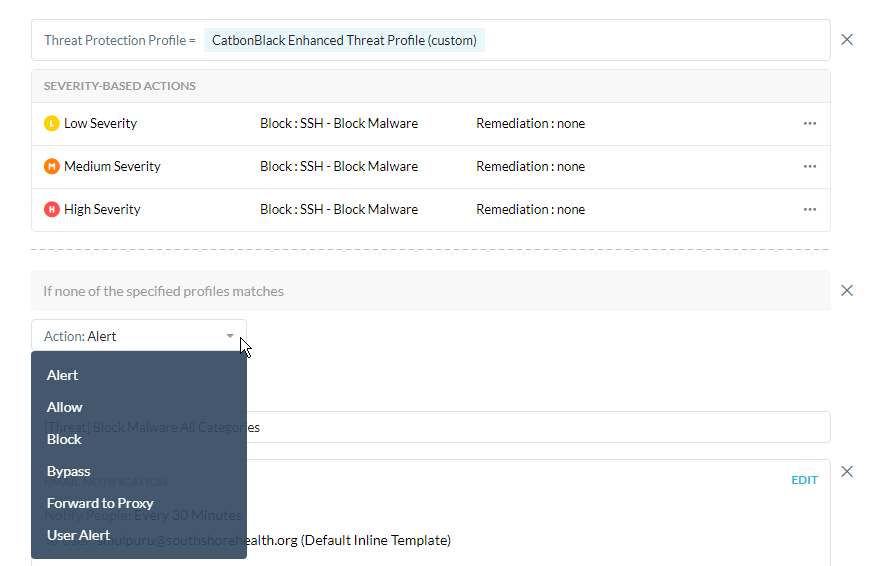
2. If I have Realtime Threat Protection policy below,
- Source: Any
- Destination: Any Categorized web traffic
- Activities and Constraints: Upload and Download
- Profile and Action: Default Malware scan where all severities are just alerting with no Remediation Profile
what happens when a categorized site did not hit any severity? will it load the site or not?
I know these are basic questions and I appreciate you all for taking time in providing answers.
Thanks and have a great weekend!