When deploying the Netskope Client (NSClient) using the "IdP" enrolment in order to associate the user to the endpoint profile asking the users to login to the desired IdP provider, and the IdP used is Microsoft Azure AD, we can encounter 2 use cases where it's useful to use the "Domain Hint" feature:
- Users logged onto the machine that belong to an Hybrid AD or to an Azure AD which is not the same AD used for the Netskope Client IdP enrollment will experience issues due to the Single-Sign-On process that will transparently use the same credentials of the logged-in user against the IdP, hence failing the Netskope Client enrolment
- Administrators may want to redirect the SSO process to the right Azure AD tenant, doing so avoiding to prompt the user all the possible different accounts they could use for the SSO, as some may not belong to the same SSO IdP domain:

On the aforementioned use cases we can rely on a Microsoft Azure AD SSO feature called "Domain Hint". Details of the feature can be found here: https://learn.microsoft.com/en-us/azure/active-directory/manage-apps/home-realm-discovery-policy#domain-hints
In essence we want to add the string ?whr=contoso.com to the SAML IdP SSP URL under the Forward Proxy SAML integration, replacing "contoso.com" with the Azure AD domain used for the Netskope Client IdP enrolment:
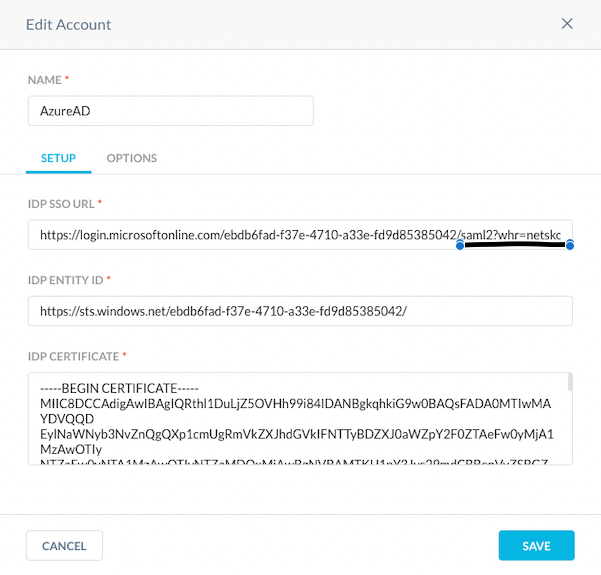
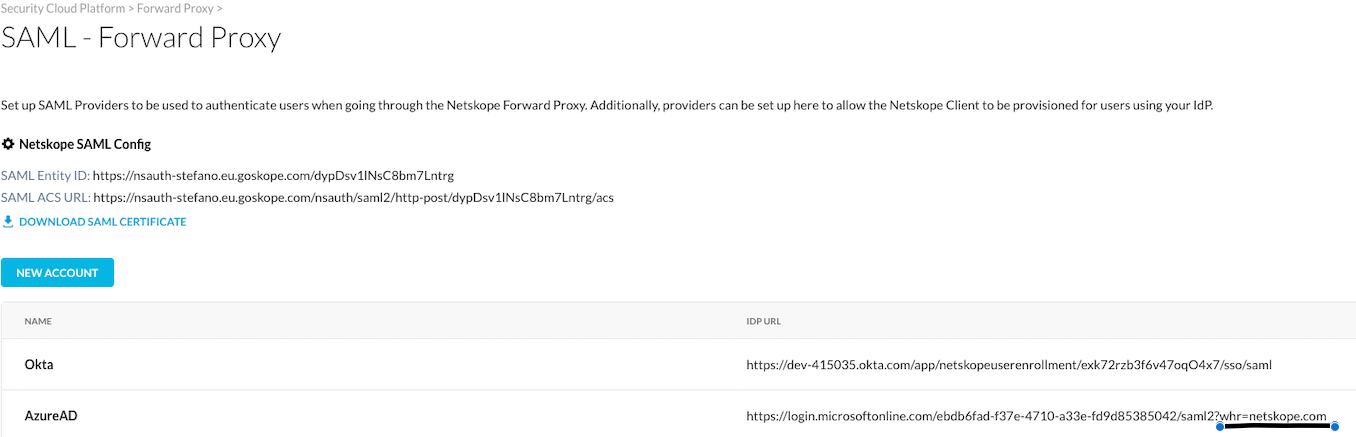
This will prevent the user not belonging to the same Azure AD to attempt transparent authentication as the logged-in user doesn't belong to the same realm, prompting then the user to authenticate against the correct AzureAD domain (realm), and it will automatically point to the correct Azure AD SSO tenant preventing Windows to display other user login options:


