One of the things I enjoy discussing the most with Netskope administrators and users is integrations. Netskope’s Cloud Exchange and REST API allow for a wide range of Netskope provided and custom integrations. These integrations range from threat intelligence and risk sharing to automated ticket creation in your service management platform. You can also utilize Netskope’s integrations to monitor Netskope events and platform status with your collaboration tools such as Slack and Microsoft Teams. I provide two examples of this with Microsoft Teams. The first integration allows you to receive status notifications from the Netskope Trust Portal to Microsoft Teams while the second allows you to generate Teams messages to specified channels when a specific policy triggers and a user enters a justification. Let’s take a look.
Monitoring the Netskope Trust Portal With Netskope Teams
Netskope publishes platform status updates on maintenance, cloud status, and more on the Trust Portal. As a side note, he Trust Portal is for platform status and maintenance but if you’d like info on product changes or application updates and domains you can subscribe to Netskope’s Release Notes and Product Changes. Back to the Trust Portal, there’s an option to subscribe to these updates via email, webhooks, text message and other methods:

Since Teams supports Webhooks natively and via the Status Page app, we can easily have these sent to a specific Teams channel. Start by opening the Team where the Channel you want the messages posted to is and then select Manage team.
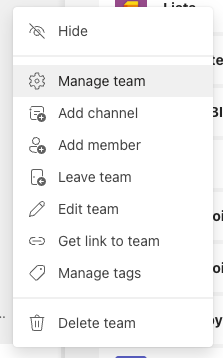
Select Apps and then More Apps. Search for StatusPage and click Add on StatusPage.io:
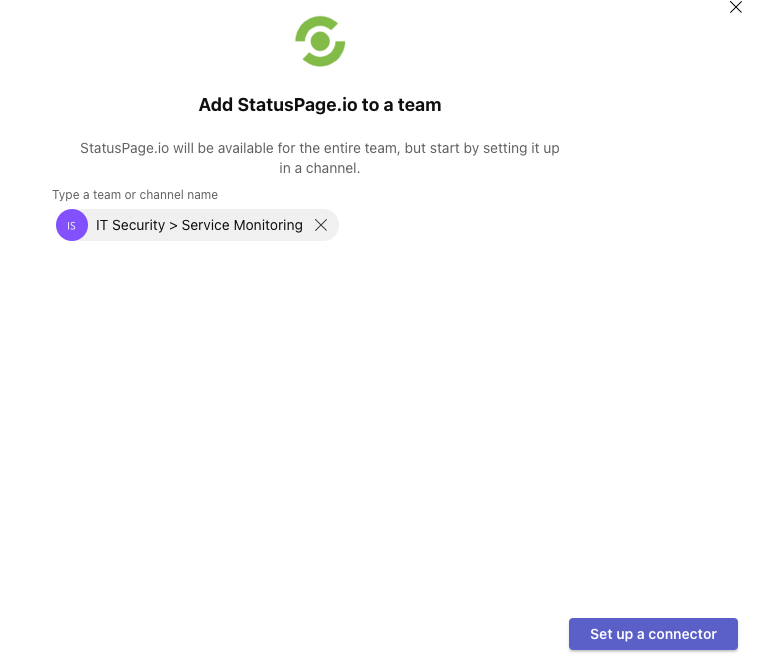
Click Add to a team and ensure that the correct Team and Channel are selected. Then click Set up a connector:
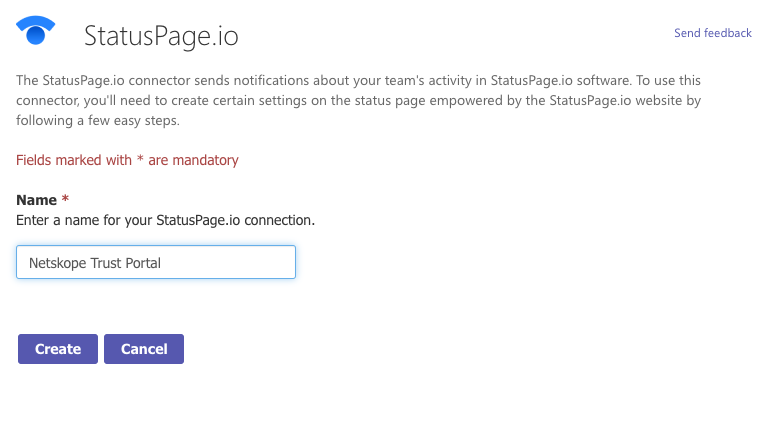
Give it a name and click Create:
On the next page ensure you copy the Webhook URL that’s provided and follow the instructions on that page by navigating to the Netskope Trust Portal and subscribing via Webhook:
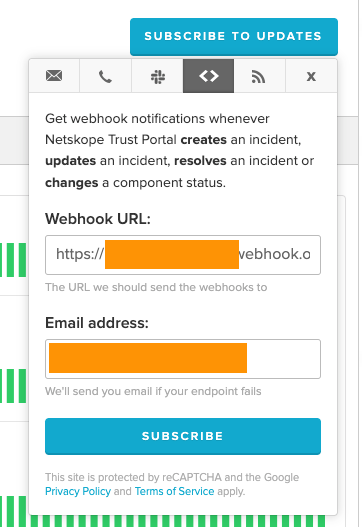
A few items to note, the Trust Portal supports providing an email address if the webhook fails. You can make this a service desk or listserv email address but you can also use the Team channel itself as each Teams channel has an email address assigned to it (if enabled in your organization). Either way, once you hit Subscribe, you should see a message from the StatusPage app indicating that the integration has been configured.
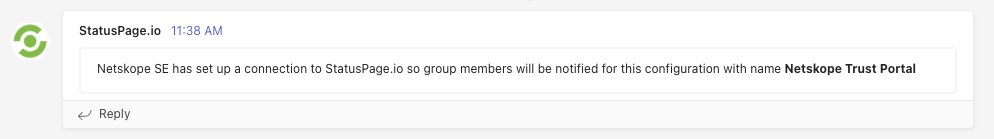
Now subsequent Maintenance and Service Notifications should be posted to the specified Teams Channel.
Monitoring and Alerting on Netskope Events with Microsoft Teams
Netskope’s Cloud Exchange has a module that you can enable called Cloud Ticket Orchestrator (CTO). CTO can be used to retrieve events and alerts from Netskope and forward them to a variety of third party ticketing, collaboration, and communication tools including ServiceNow, Jira, Slack, Microsoft Teams, and more. Administrators can configure Business Rules that determine which events should trigger a ticket creation or message in these respective systems. As a quick example of how you can use this with Microsoft Teams, I have a policy that blocks access to the Weapons category:
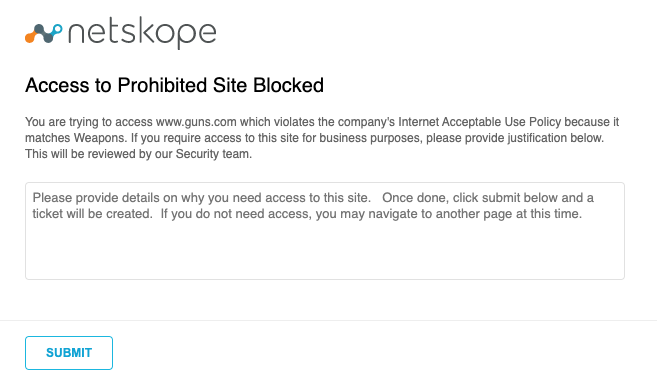
I’ve provided a prompt to the user stating that they can provide details to this and a ticket or message to an administrator will be created. I provide justification and submit the message.

I’ve already configured Cloud Ticket Orchestrator with plugins for both Microsoft Teams and Netskope. These plugins are responsible for the API integrations between Netskope and Microsoft Teams. They periodically send and receive events from Netskope to Teams.
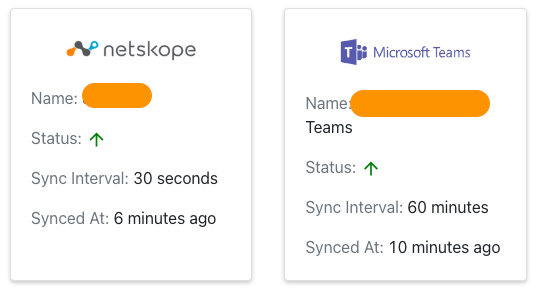
Cloud Exchange uses the concept of Business Rules which are essentially filtering rules that can be used to specify what Netskope events should generate messages or tickets in external platforms. In my case, I’ve created a Business Rule that filters events based on a policy name and that the justification has been entered. This will filter out cases where the user hit the block but did not enter a reason why they need access.
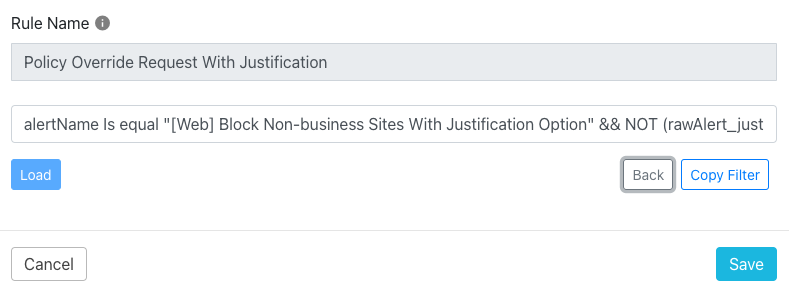
I then use this Business Rule in a Queue to specify that events matching this rule should be sent to Teams with a custom message including details on the user, their justification, the site they tried to go to. Administrators can customize the message to include all relevant details.
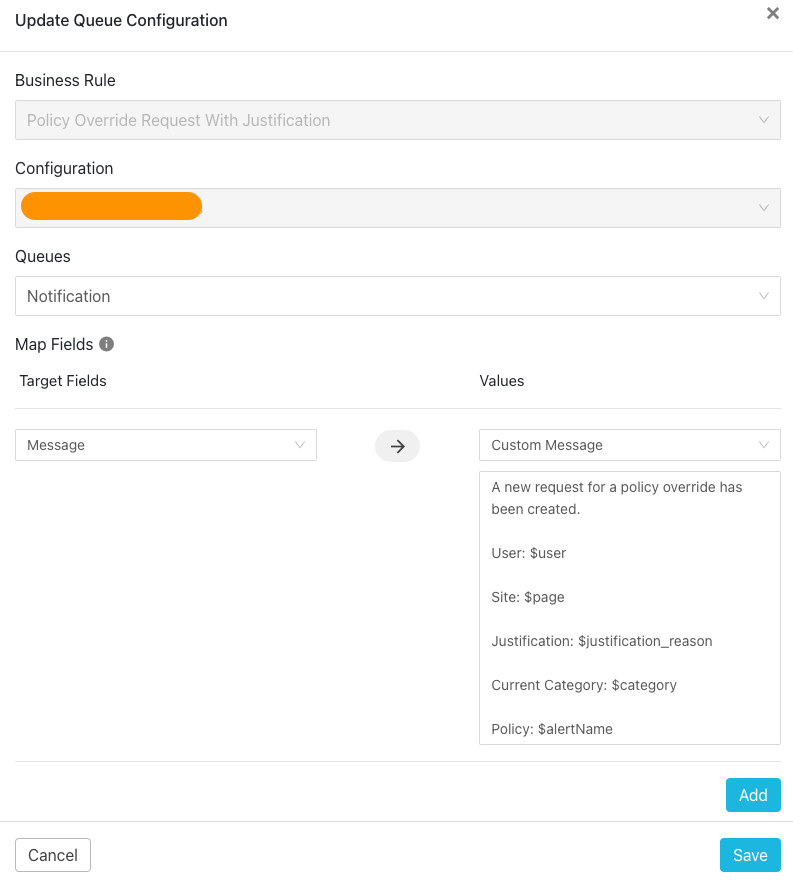
Since I generated a policy hit and entered a justification, a message is generated in Teams with the custom message configured in the Queue.
I showed a case of monitoring Secure Web Gateway events with Teams but since the Business Rules are customizable, you can include other event types like Malware and DLP events:

As a final note, these two quick examples show using one of the most popular collaboration tools, Microsoft Teams, to streamline your administration and monitoring of Netskope. The flexibility of Cloud Ticket Orchestrator allows you to be notified of the most critical or common events in your Netskope tenant.



