The requirement is :- User should able to access a corporate instance of Git-hub but not any other instance of git-hub.
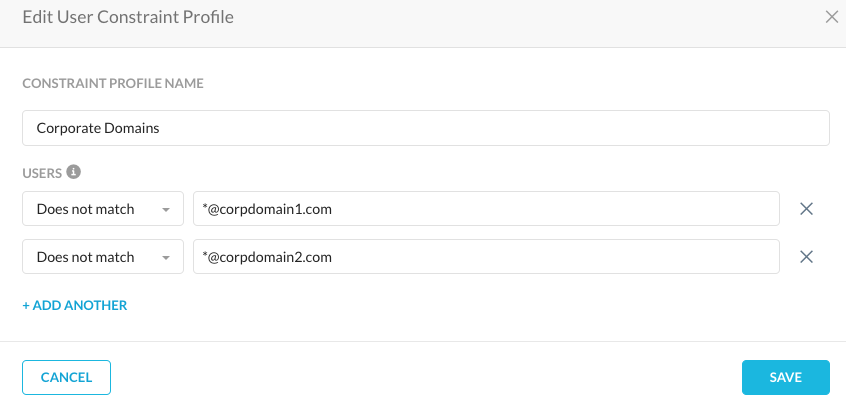
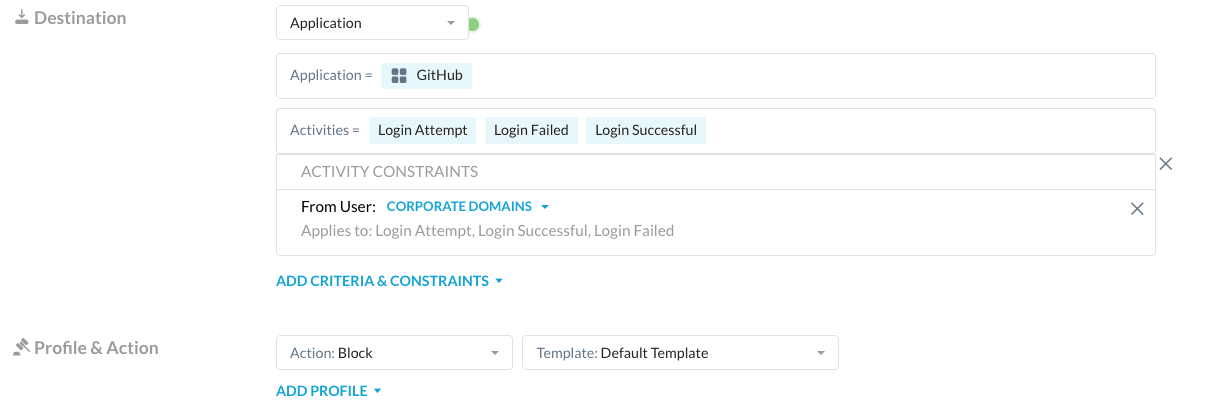
I have created app instance for a corporate instance of Git-hub and configured the policy to allow all activities.
2nd policy after that is to block all activities for the application Git-hub ( to match all other git-hub instances)
with this, I am not getting an expected result
When user is accessing corporate instance, Netskope is showing Browsing activity and getting blocked in 2nd policy.
I have checked the list of activities for app Git-hub but there is no Browsing activity mentioned
Any expert comments and guidance here pls...