How do you feed the Netskope SSPM Alerts to SaaS Application Administrators?
The Netskope Cloud provides a wide range of innovative and competitive products, among which one of the most important offerings should be Netskope SSPM. SSPM stands for SaaS Security Posture Management and is used to continuously monitor cloud-delivered Software-as-a-Service applications. This service monitors the SaaS applications' configuration to ensure that they are configured securely and in compliance with regulations. Security administrators can set policies and receive alerts for SaaS application instances that do not adhere to the required policy.
Typically, SaaS application administrators are not part of the company's core security team. Instead, the security team receives the SSPM alerts for all the SaaS applications. These alerts must be forwarded to the respective SaaS application owners so that they can work on remediation. In some cases, the security team might be hesitant to grant SaaS application owners access to the Admin portal solely for checking the SSPM violations.
This post will guide you through a script used by the Netskope Information Security Team to retrieve all the SSPMv2 alert data via API and pass it on to our SaaS application administrators. They can then use this information to make the necessary changes and enhance the application's security. By following this method, the SaaS application owners are not granted access to the Netskope Admin portal, but can receive regular updates on the SSPM results for the applications they administer using the script and API.
Create a REST API v2 Token with required privileges:
To create a REST API v2 token for use, follow the below steps:
- Navigate to the Netskope Tenant (Admin Portal)
- Navigate to the ‘Settings’ screen with the button found on the bottom left corner of the tenant.
- Navigate to ‘Tools - REST API v2’ and click on ‘New Token’ to create a fresh token.
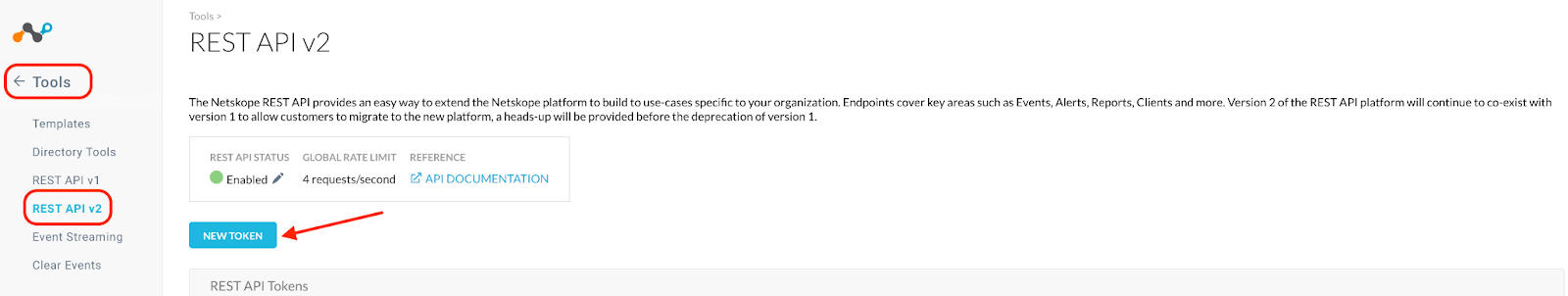
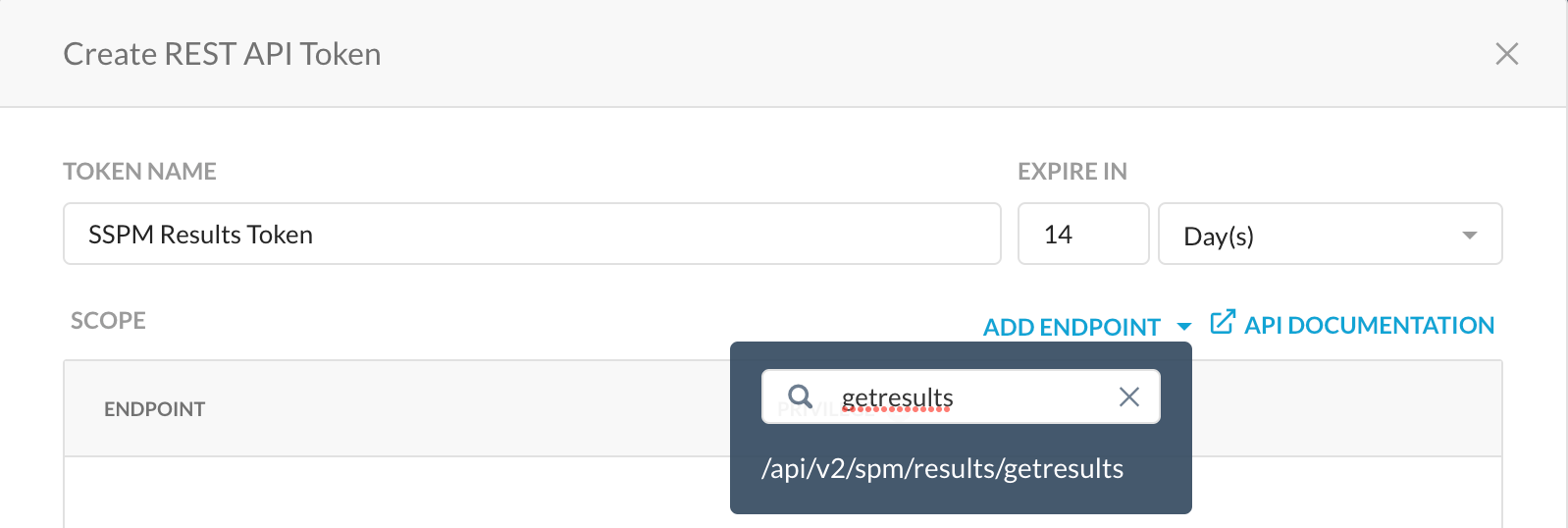
- Name the token per requirement and set the expiry as required. Click on the “ADD ENDPOINTS” button and search for “/api/v2/spm/results/getresults” to get the endpoint.
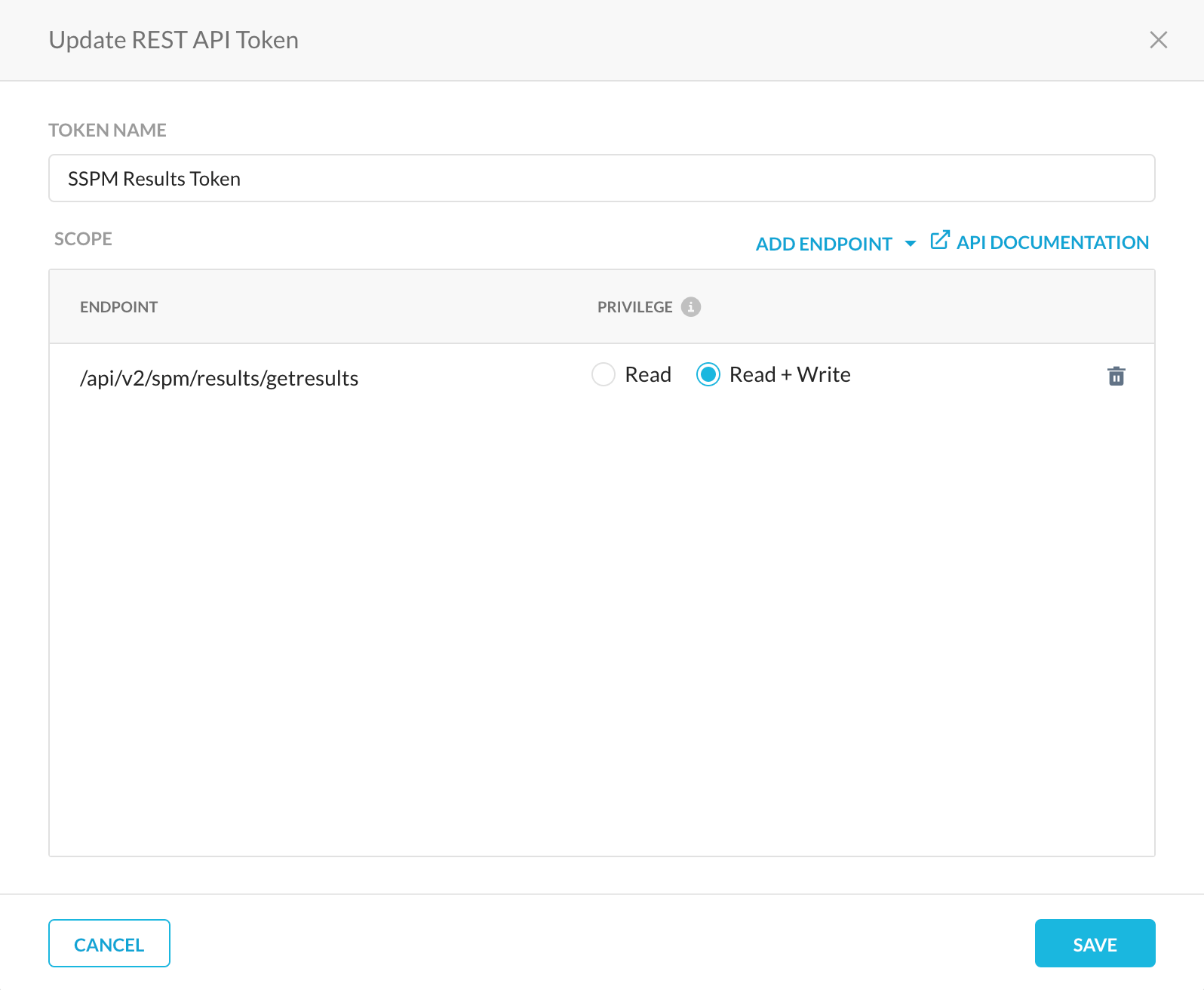
- Click on the endpoint to add it to the sources, change the privilege to ‘Read + Write’ and save the token.
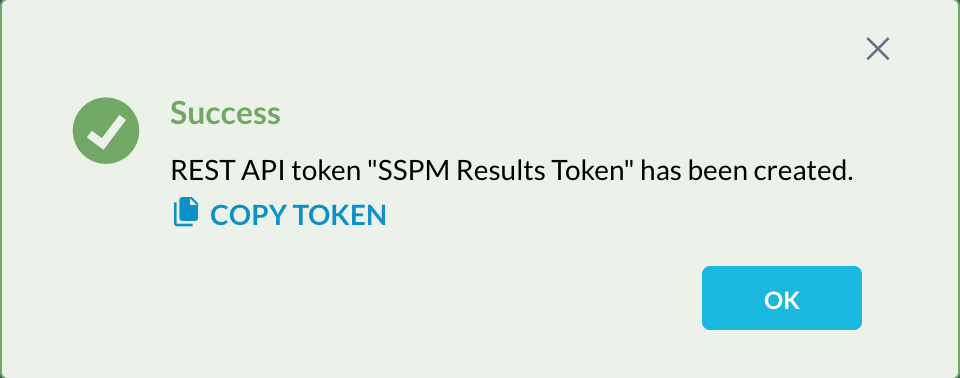
- Once the token is created, copy it and store it in a secure location for future reference.
Script Execution & Output
The script was tested with Python version 3.9.0 and we request the users to execute it with the same version in order to avoid errors during execution. The users are also requested to install the following modules so that the script can import them during execution for smooth operations. Use the below commands to install the modules:
Windows:
python -m pip install requests
python -m pip install csv
python -m pip install json
Mac OS/ Linux:
pip install requests
pip install csv
pip install json
Post installation of the modules, the script must be downloaded and edited per requirements of the user. Variables to be edited are mentioned below:
- Line 17: The Timestamp variable should point to the current Unix epoch time. [timestamp_var]
- Line 18: The status variable can be changed to include the failed results or passed results. (All entries are case sensitive) [status_var]
- Line 19: The App Suite variable should be replaced with the SaaS Application results to be obtained (All entries are case sensitive). [app_suite_var]
- Line 20: The Instance ID variable should point to the Instance ID of the App Suite. It can be found in the Netskope Tenant (All entries are case sensitive). [instance_id_var]
- Line 23: Enter appropriate Tenant details. [url]
- Line 27: Enter the REST API token created earlier in the Netskope Tenant. [API_TOKEN_HERE]
Once the script is executed without any error, the output must appear in the directory in which the script was executed. 4 separate CSV files will be created with each file having the results differentiated based on the severity of the finding. Each of the CSV would have the Instance Name, Resource Name, Resource Type and Rule Name fields.
Every time when the script is executed, it overwrites the previous execution output. So save or move the output files accordingly. Please feel free to make changes to the script per your requirement.
The link to the script can be found in the attachment below.


