Netskope Global Technical Success (GTS)
Block AnyDesk using Netskope's SWG Module - Windows OS
Netskope Cloud Version - 118
Objective
The objective of this document is to describe the procedure for blocking AnyDesk using Netskope. While AnyDesk is referenced for example, this procedure can be applied for similar Remote Control Applications that an IT Administrator would like to access control over, within the organization.
Prerequisite
Netskope SWG license is required
Context
AnyDesk is a remote desktop application that enables users to connect to and control another computer over the internet. It is commonly used for remote support, remote work, and accessing files or applications from different locations. Although AnyDesk is available for free, it may not be sanctioned for use within the organization. Therefore, IT teams may need to manage and control its usage. This document outlines the procedure for blocking AnyDesk on Windows OS
Do You Know?
- As of August 29, 2024, Netskope recognizes AnyDesk as a cloud application. However, there is currently no predefined cloud app connector available for AnyDesk within the Netskope platform.
Details
- Netskope client will forward the Port 80/443 TCP/UDP traffic by default to Netskope Gateway when the Traffic steering type is set to Steer All Web Traffic (except the exceptions)
- If a Customer wants to exercise control over an Application that uses Non Standard ports for HTTP/HTTPs traffic, the traffic needs to be explicitly steered to Netskope using Netskope’s Steering configuration.
Path: Netskope Tenant UI >>> Settings >>> Security Cloud Platform >>> Steering configuration >>> Edit - Non Standard Ports
(If you do not see this module, please contact the Netskope Customer Support via raising a support case to enable this feature on your Netskope Tenant)
Step 1: Blocking AnyDesk using Netskope SWG Module :
- As per information available on AnyDesk’s website, it uses the Ports 80, 443 and 6568 for communication with protocols TCP / UDP on the domain : *.net.anydesk.com Link
- We will use the Steer Non Standard Port option on the Web UI to steer Non Standard port traffic for AnyDesk
Path: Netskope Tenant UI >>> Settings >>> Security Cloud Platform >>> Steering configuration >>> Edit - Non Standard Ports
Port - 6568
Domain - *.net.anydesk.com
Step 2: We will create a Certificate pinned Application entry for AnyDesk and block it
Find out the process name used by the Application on Windows. This can be found out from Task Manager in Windows.
For Windows the process name is : AnyDesk.exe
Path: Netskope Tenant UI >>> Settings >>> Security Cloud Platform >>> Steering configuration >>> Exceptions >» New Exception - Certificate pinned Application. Click on the “+” sign
NOTE : Always ensure to test the changes in a test steering configuration applied to a test set of users before rolling out in production.
Now, add the platform windows and add the below regex
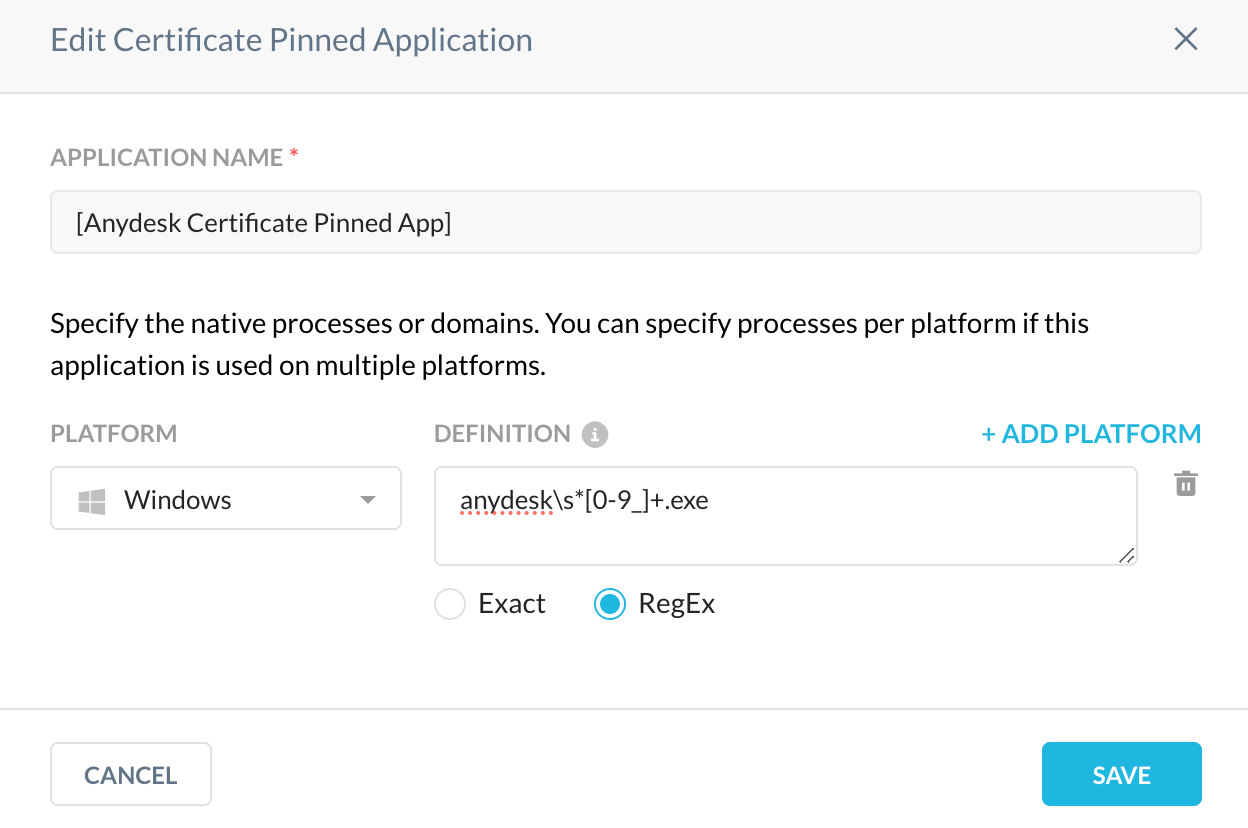
Regex : anydesk\s*>0-9_]+.exe.
Now add the Application to the list and Click “Add”. Add the domains for AnyDesk to which the application tries to connect to.Add an appropriate note is always a good practice in terms of managing exceptions.
Once you save this, go to a test machine and update the Netskope Client configuration.
Lab Recreate
Go to AnyDesk Application and try connecting to Any Remote computer. Note that if you have Anydesk running previously, please kill the process and relaunch it
You will see a Message prompt as shown below which indicates that AnyDesk has been blocked on the end user’s system
Verification through Netskope Debug Logs :
Save a copy of Netskope Debug Logs and open the file NSdebuglogs.logs
2024/08/30 10:47:26.887 stAgentSvc p960 t10c4 info bypassAppMgr.cpp:671 BypassAppMgr Dropping connection from process: anydesk.exe, host: boot.net.anydesk.com
2024/08/30 10:47:27.887 stAgentSvc p960 t10c4 info bypassAppMgr.cpp:671 BypassAppMgr Dropping connection from process: anydesk.exe, host: boot.net.anydesk.com
2024/08/30 10:47:29.887 stAgentSvc p960 t10c4 info bypassAppMgr.cpp:671 BypassAppMgr Dropping connection from process: anydesk.exe, host: boot.net.anydesk.com
If you change the Name of the executable just to try and bypass the policy, Netskope will still block the connections. Eg, I change the name of the executable from “Anydesk.exe” to “123.exe” or “wow.exe”, the connections will still be dropped. Refer the log lines below :
2024/08/30 17:31:53.700 stAgentSvc p960 t1334 info bypassAppMgr.cpp:671 BypassAppMgr Dropping connection from process: 123.exe, host: relay-301a8b57.net.anydesk.com
2024/08/30 17:31:54.653 stAgentSvc p960 t1334 info bypassAppMgr.cpp:671 BypassAppMgr Dropping connection from process: 123.exe, host: relay-301a8b57.net.anydesk.com
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.

