Netskope Global Technical Success (GTS)
KB - Identifying “Upload” activity on Anthropic Claude to introduce DLP controls
Netskope Cloud Version - 129
Objective
Implement DLP controls to prevent data leakage through Anthropic Claude. This can be achieved by identifying "Upload" activity using the Netskope Custom Connector.
Prerequisites
Netskope Next-Gen SWG / CASB license.
Context
To support the growing adoption of innovative applications like Anthropic Claude, Netskope is actively developing predefined cloud connectors. While a predefined connector for Anthropic Claude is on our development roadmap, you can implement security controls today using Netskope's versatile Universal and Custom Connector features. Within this article, we will provide full guidance to ensure the configuration meets your specific security requirements as we work to deliver the new connector.
Do You Know?
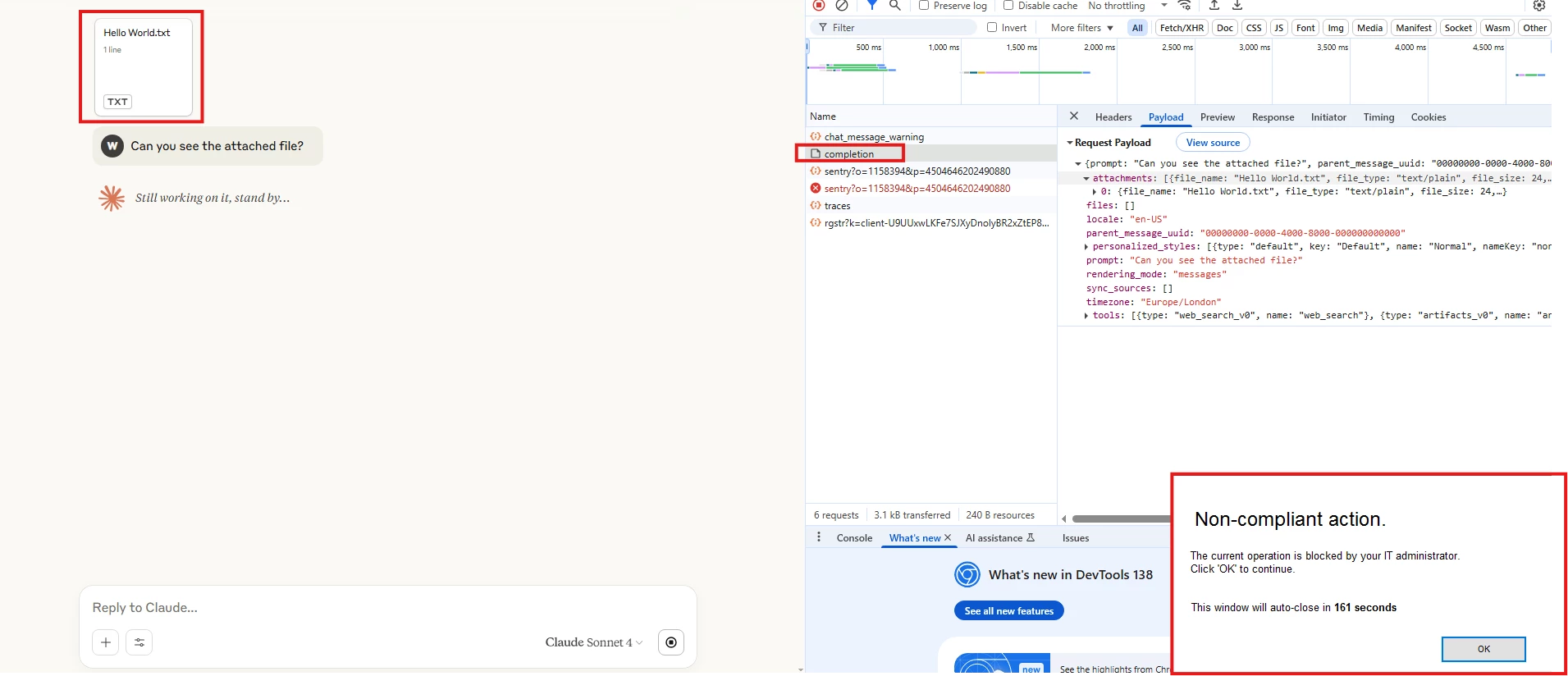
When Plain Text Files are uploaded to Anthropic Claude, the application parses the content of the file within the same “Post”/Prompt, for instance: The below is an example of uploading a file named: “Hello World.txt” with content: “Hello Netskope Community” and a prompt: “Can you see the attached file?”
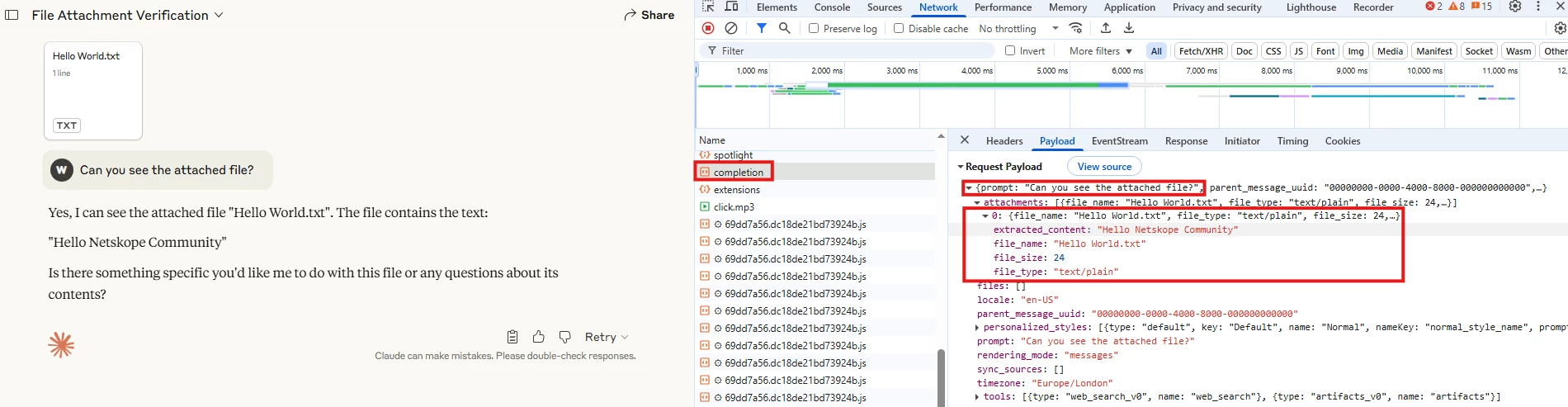
The above will be our first limitation, we will not be able to differentiate between a prompt with or without a plain text file.
In addition, our second limitation would be that Custom Connector does not apply DLP on “Post” activity, however, it does allow applying DLP on “Upload”, therefore we will merge “Post” activity with “Upload” activity in order to apply DLP.
On the other hand, the application uploads other file extensions on a different path outside of the prompt, for instance: The below is an example of uploading a file named: “Hello World_2.docx” with content: “Hello Netskope Community” and a prompt: “Can you see the attached file?”
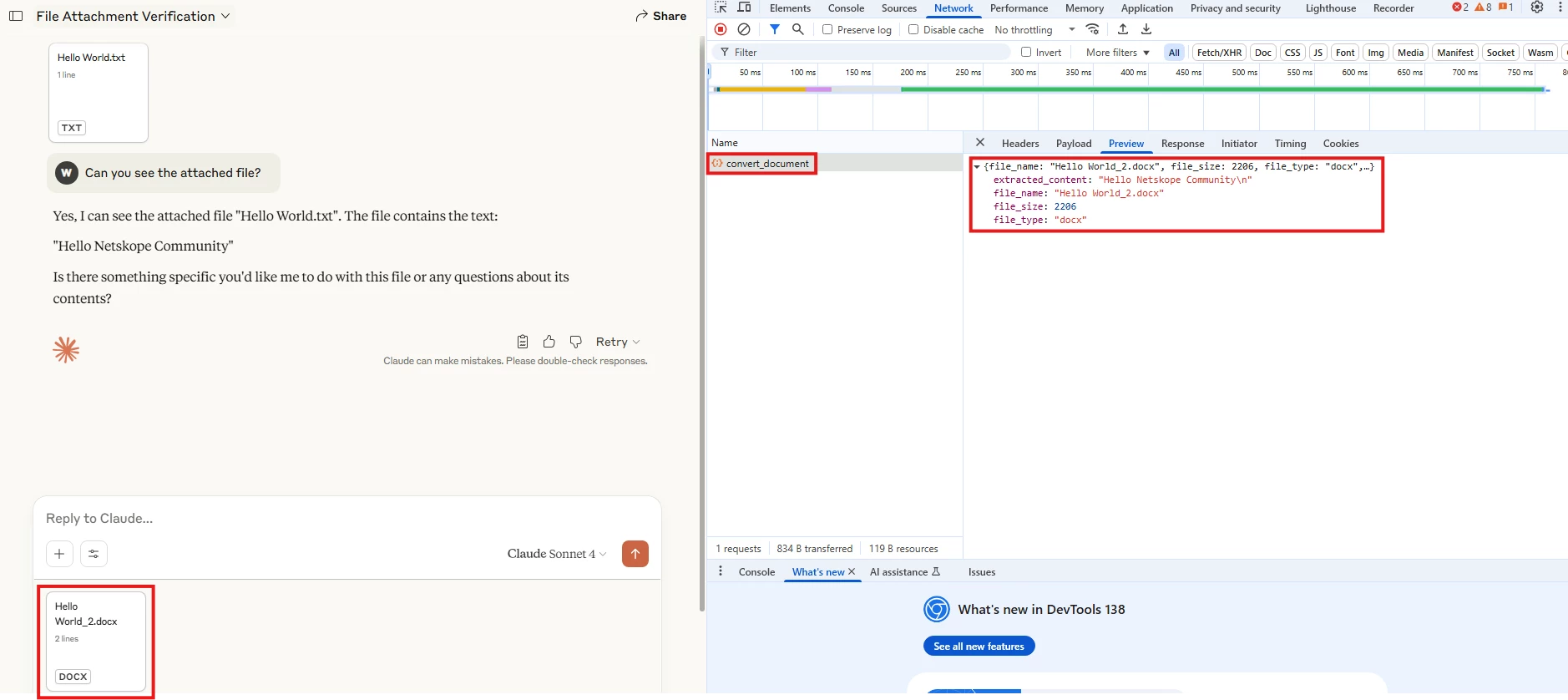
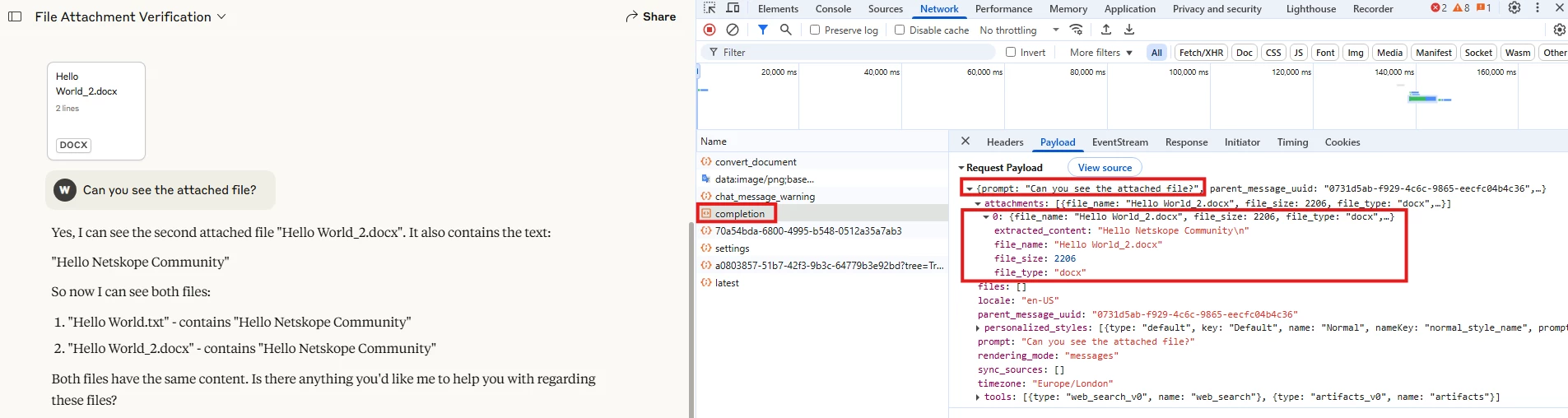
With the above example, you can notice that the file is uploaded before the prompt is sent, then the extracted content is also shown when sending the “Post”,
Similar to other files but plain text files, images are uploaded before the prompt. For instance: The below is an example of uploading a file named: “Hello World_3.JPG”
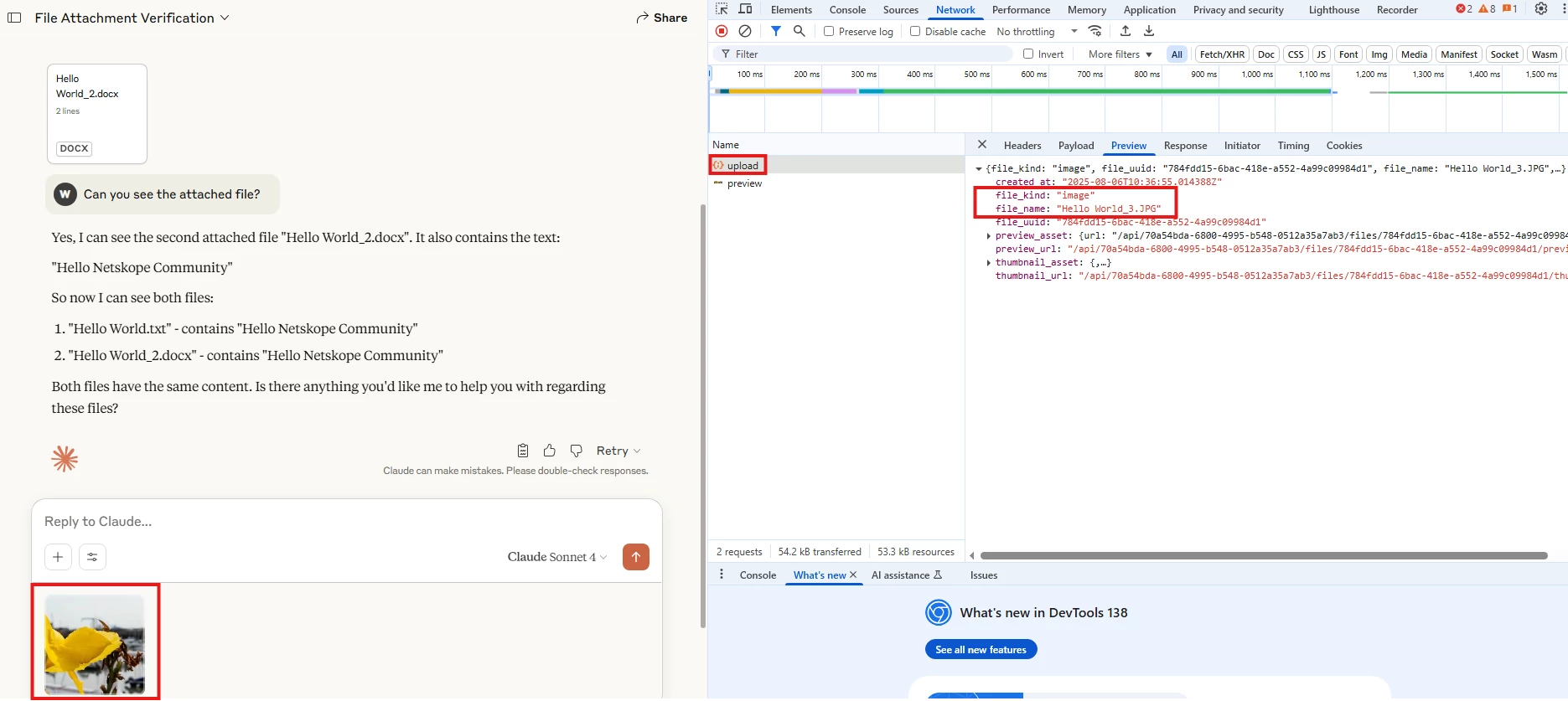
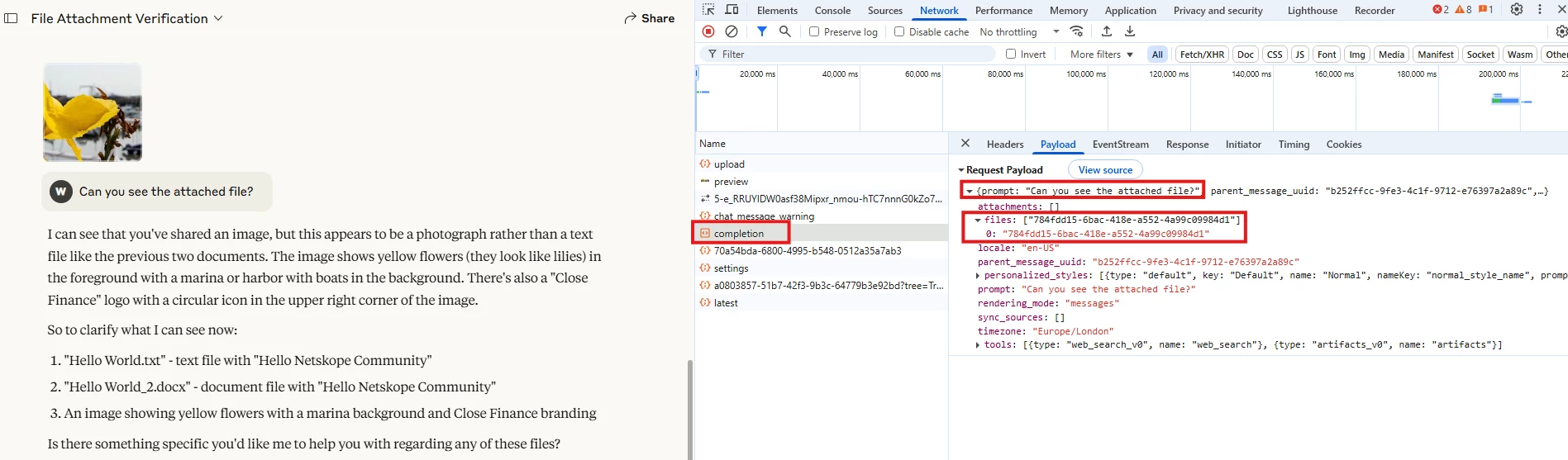
When sending an image as a file uploaded, the prompt only references the file UUID,
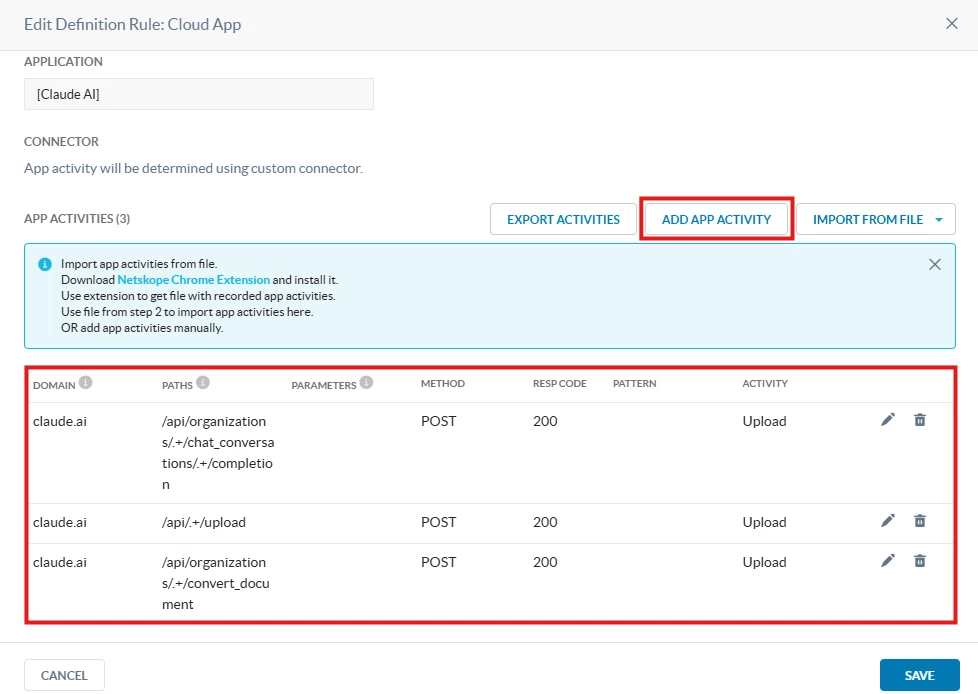
Based on what we have seen after analysing the application, this is the custom connector configuration:
| Domain | Paths | Method | Resp Code | Activity | Notes |
| claude.ai | /api/organizations/.+/chat_conversations/.+/completion | POST | 200 | Upload | Post + Upload of plain text files |
| claude.ai | /api/.+/upload | POST | 200 | Upload | Images |
| claude.ai | /api/organizations/.+/convert_document | POST | 200 | Upload | Other files except for plain text |
| ℹ️ “.+” is a regex meant to capture a long string seen on these paths, for example: claude.ai/api/organizations/70a54bda-6800-4995-b548-0512a35a7ab3/chat_conversations/a0803857-51b7-42f3-9b3c-64779b3e92bd/completion |
Configuring Custom Connector
To add a custom connector, we need to create an app definition.
Path: Netskope Tenant UI >>> Settings >>> Security Cloud Platform >>> App Definition >>> Cloud & Firewall Apps
- Click on “New App Definition Rule”, select “Cloud App”, add a name, click on “Custom Connector”, then add each activity as mentioned in the above table, then select “Save”, for example:
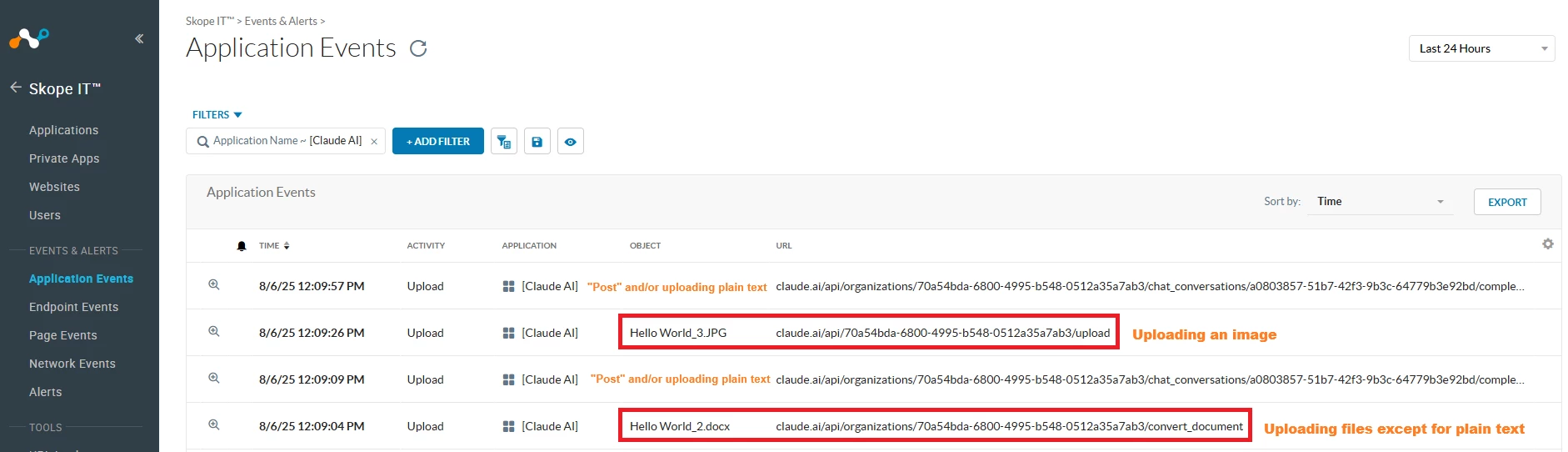
After Netskope Client updates its steering configuration profile, we will start seeing activities being recorded onto “Application Events” page, for example:
Key Use Cases
Use Case #1: Block all file upload (including plain text files) using DLP
- Create a DLP identity with the following regex: .*?"file_name":"n^"@\s]+"
- Create a DLP Rule selecting the above identity with the following configuration
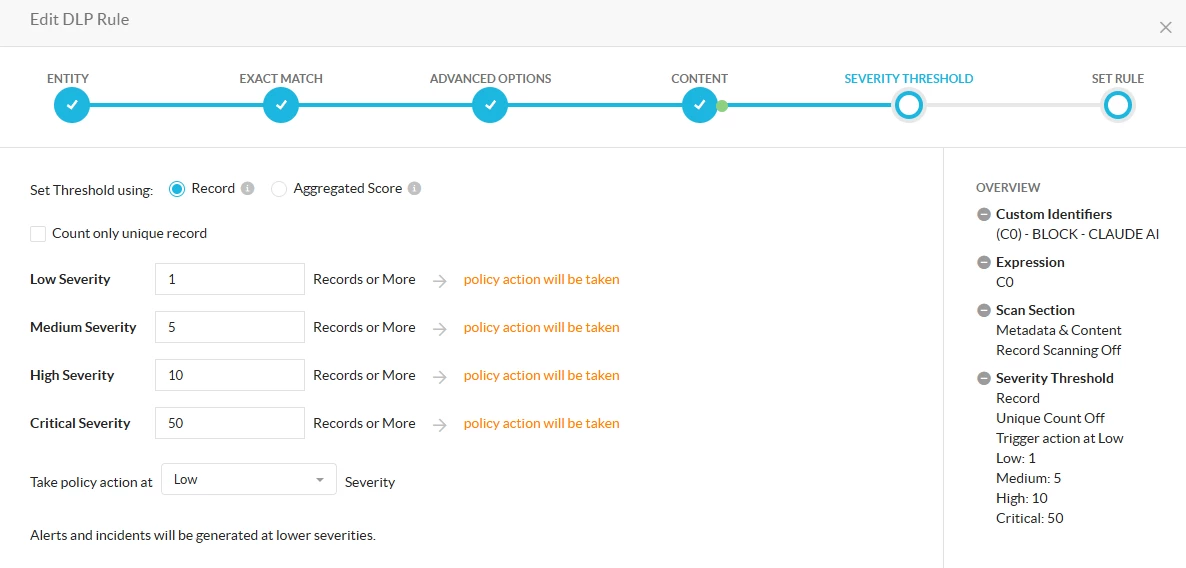
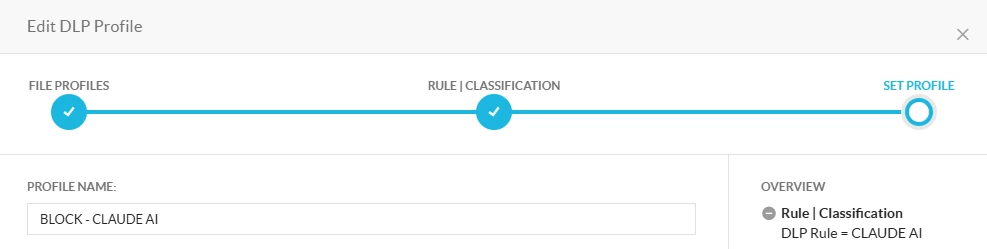
- Create a DLP Profile selecting the above DLP Rule
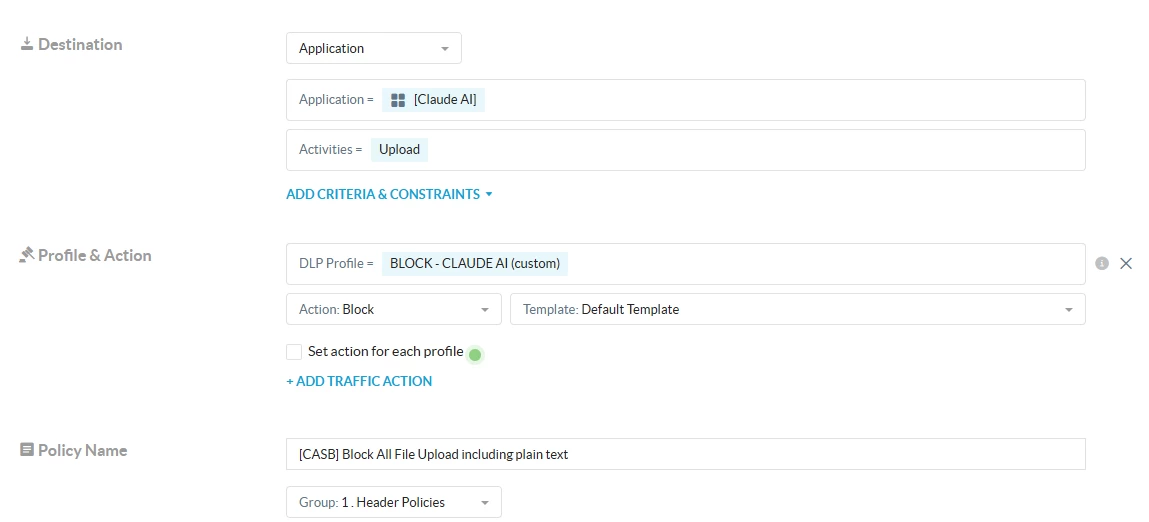
Policy configuration:
- Create a Real-Time Policy with the below configuration
Path: Netskope Tenant UI >>> Policies >>> Real-Time Protection
Testing:
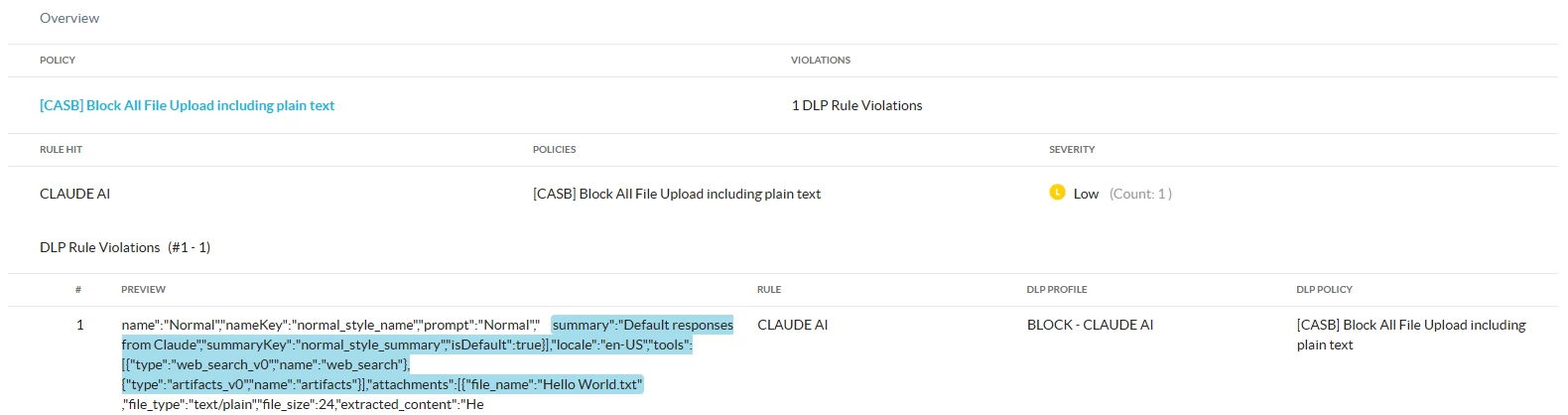
1- Uploading a text plain file:
DLP Incident:
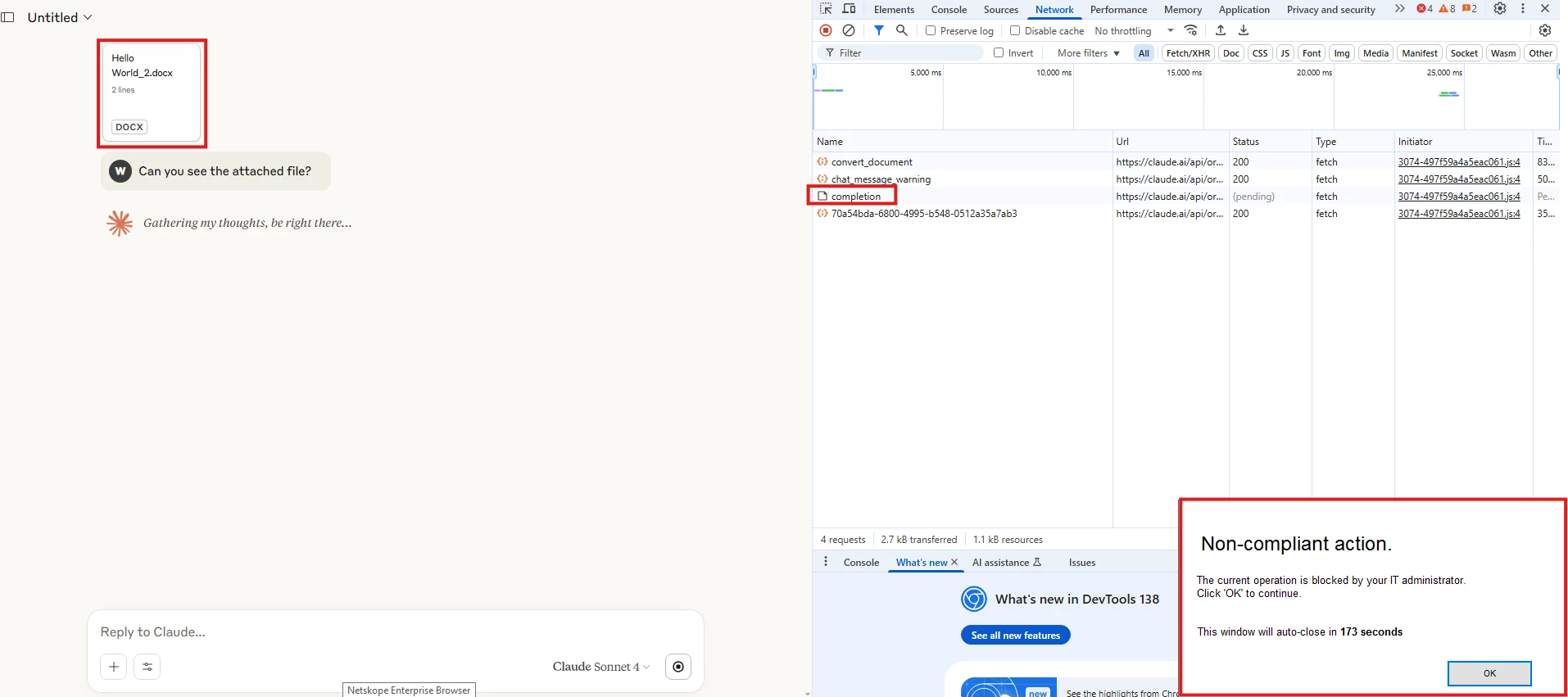
2- Uploading a word document:
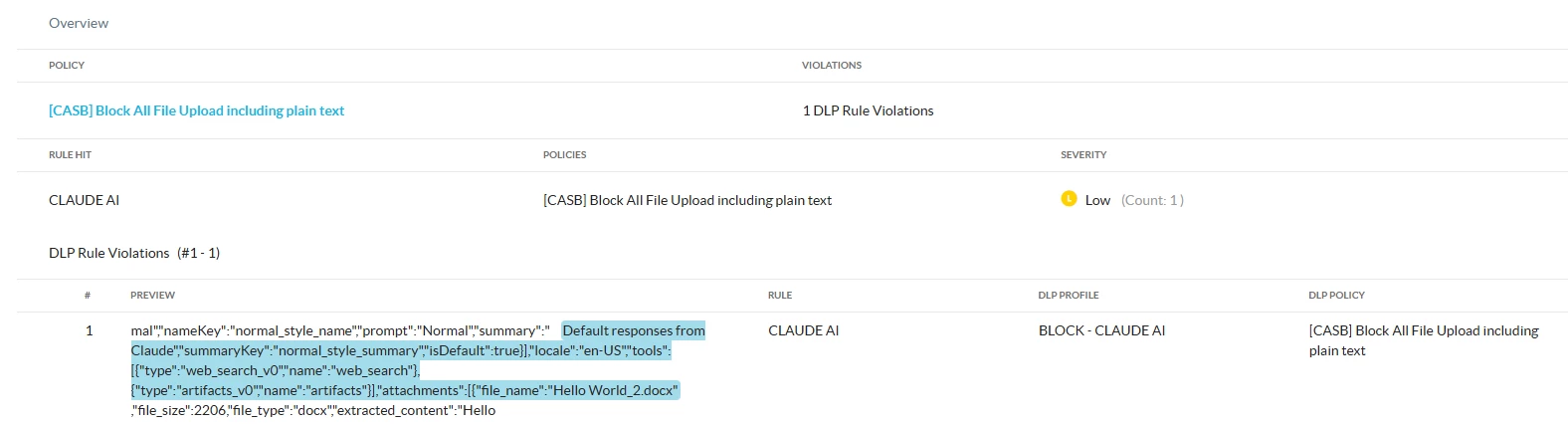
DLP Incident:
Use Case #2: Block word documents, images, and other extensions (except for plain text files)
Policy Configuration:
- Create a Real-Time Policy with the below configuration
Path: Netskope Tenant UI >>> Policies >>> Real-Time Protection
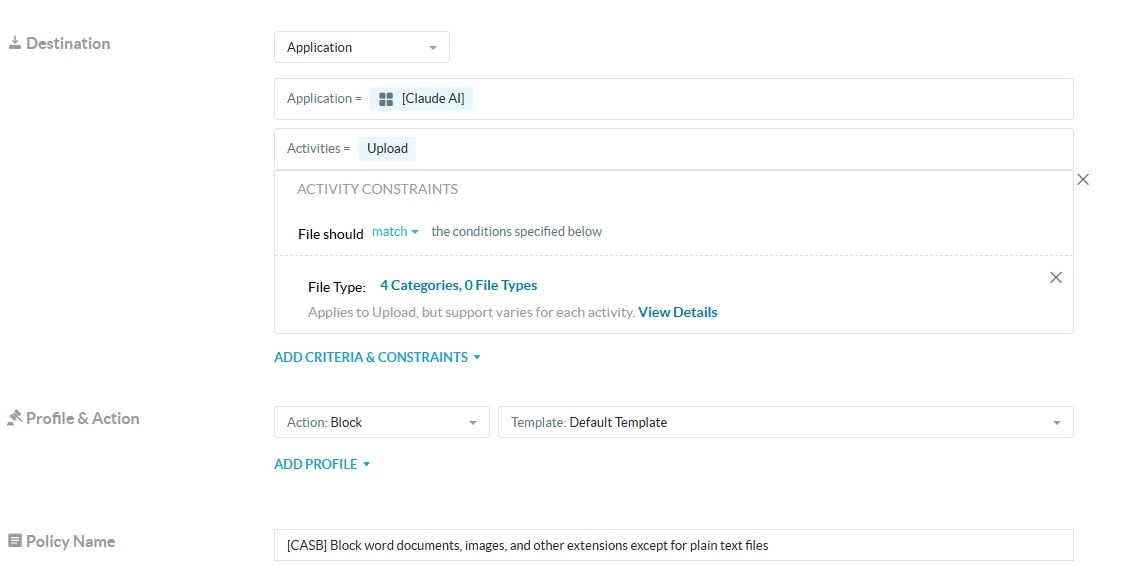
When constraint profile is based on File Type which we do see when the file is uploaded (except for plain text files, these are parsed).
Testing:
1- Uploading a word document:
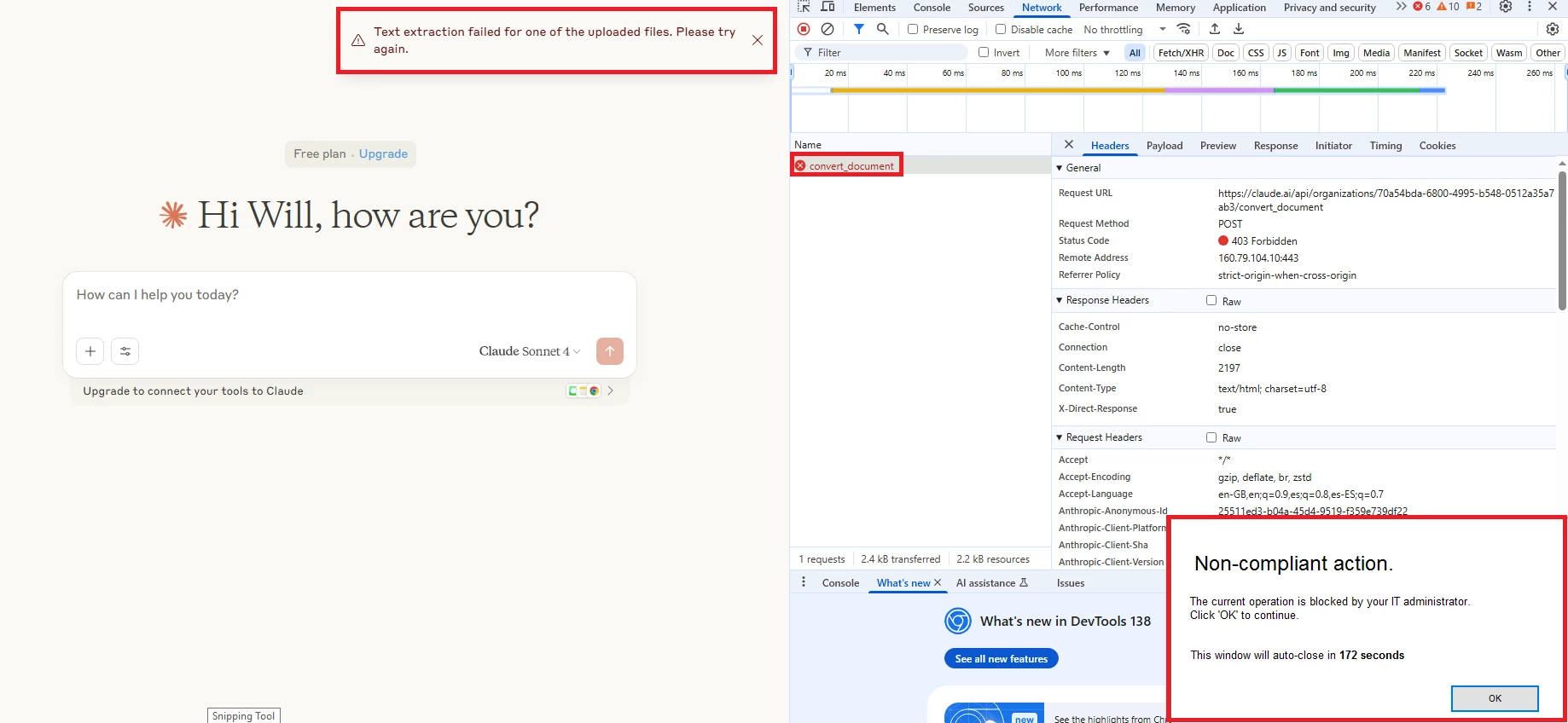
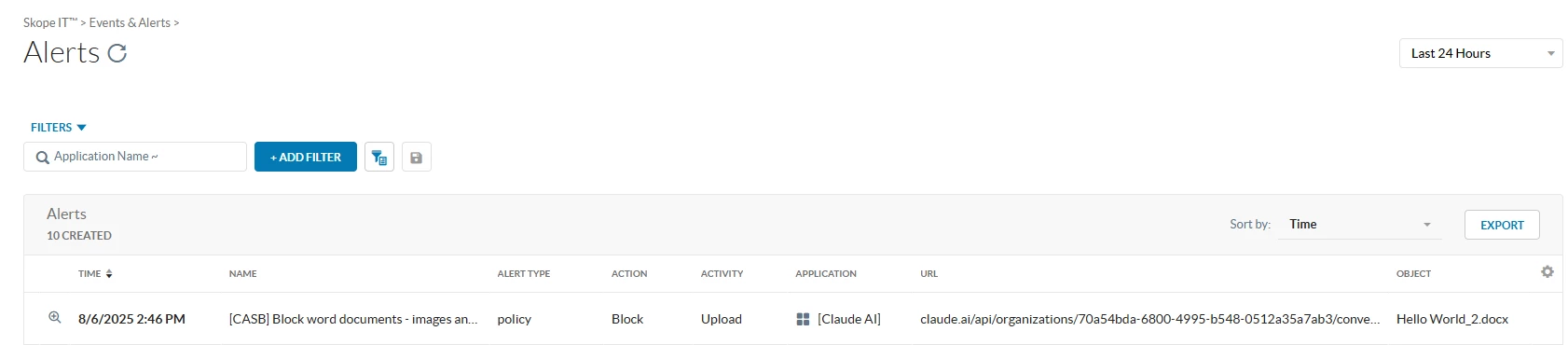
SkopeIT Alert:
2- Uploading an Image:
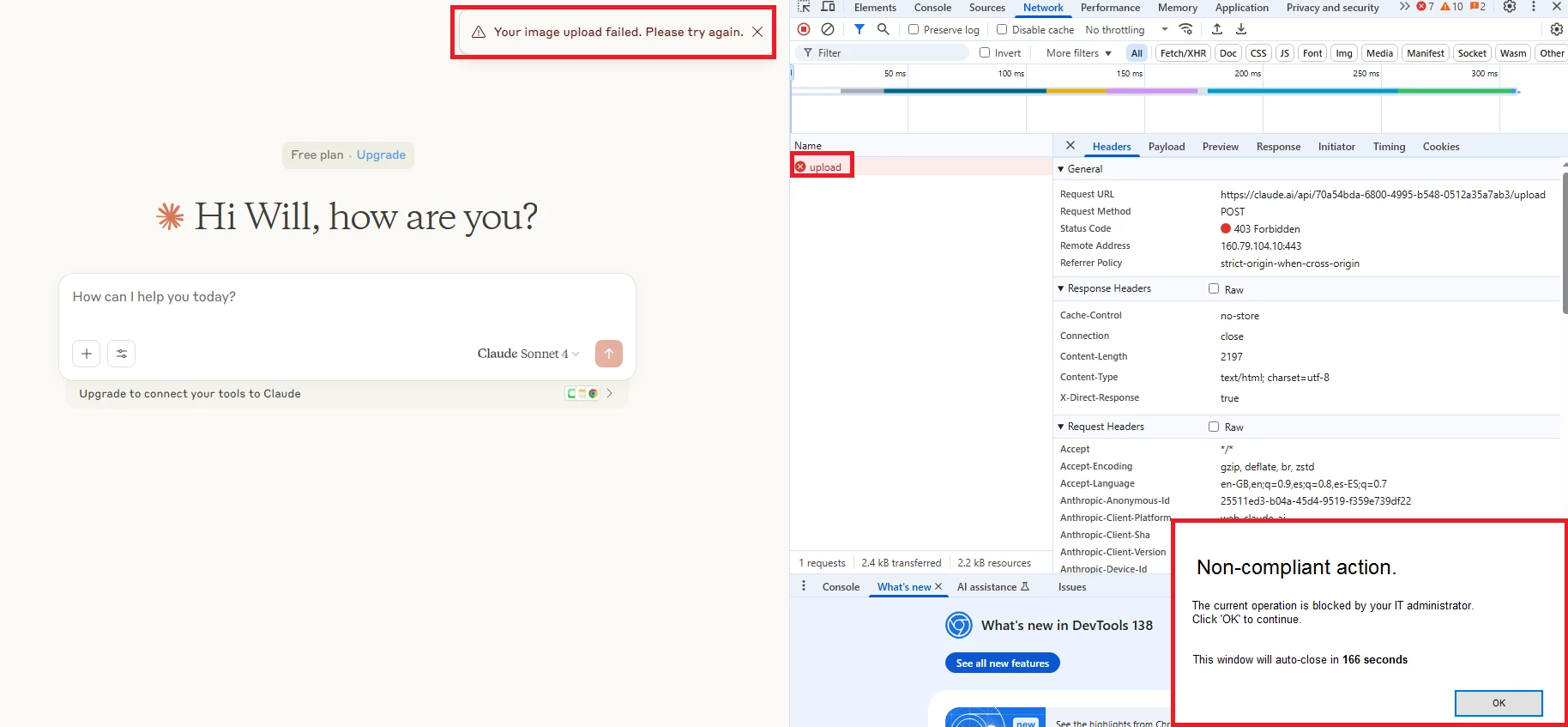
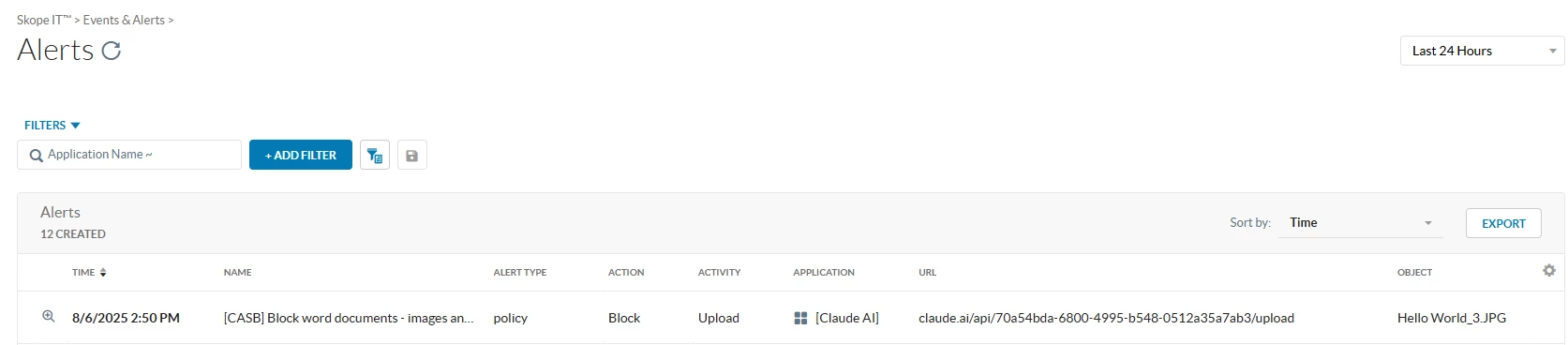
SkopeIT Alert:
Use Case #3: Block uploading “confidential” within document content or prompt (Reference: DLP - Scan documents for a particular keyword)
Policy Configuration:
- Create a Real-Time Policy with the below configuration
Path: Netskope Tenant UI >>> Policies >>> Real-Time Protection
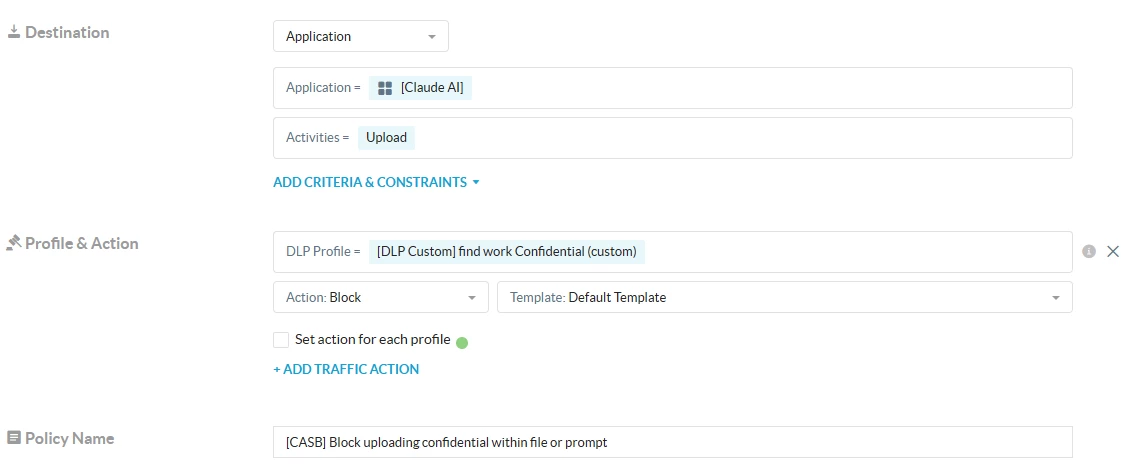
Testing:
1- Sending the word “confidential” on prompt:
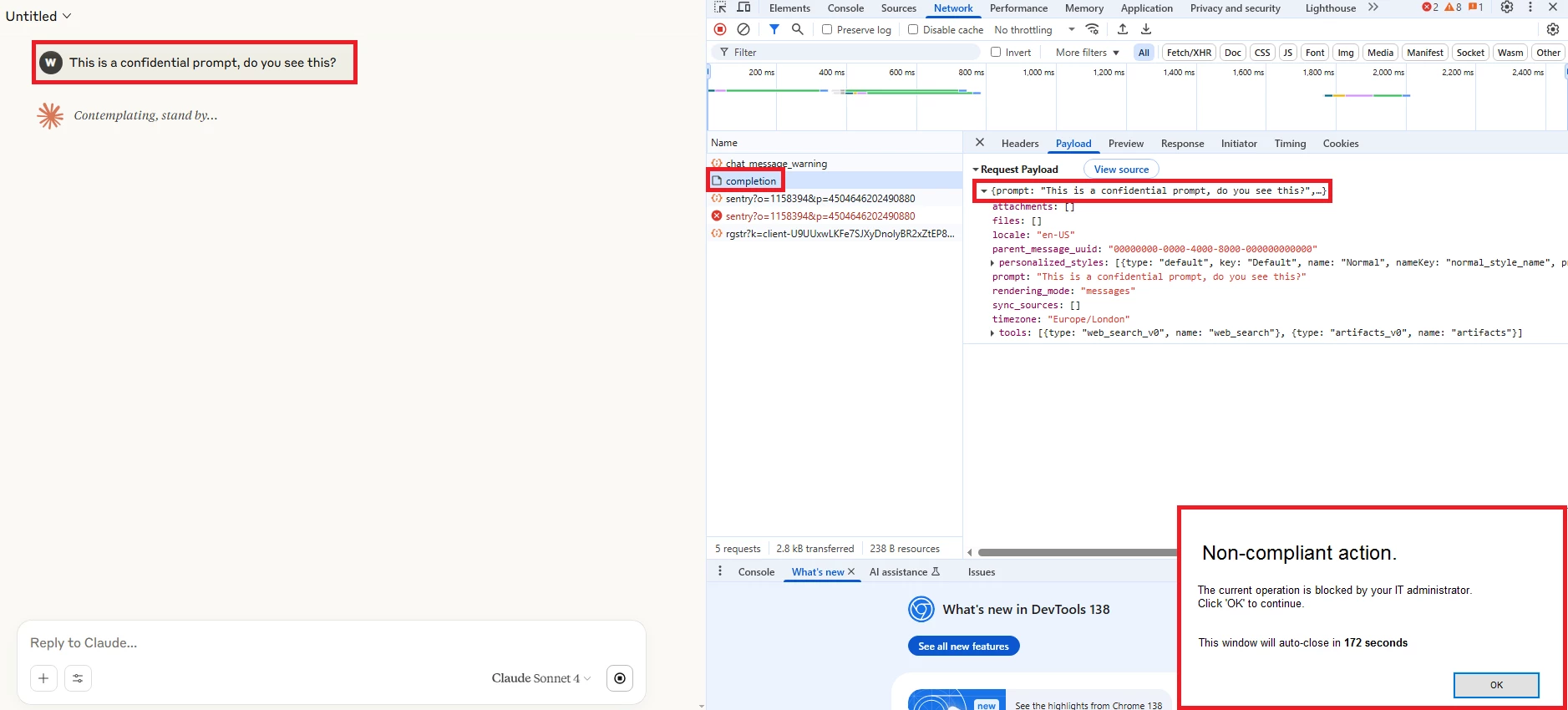
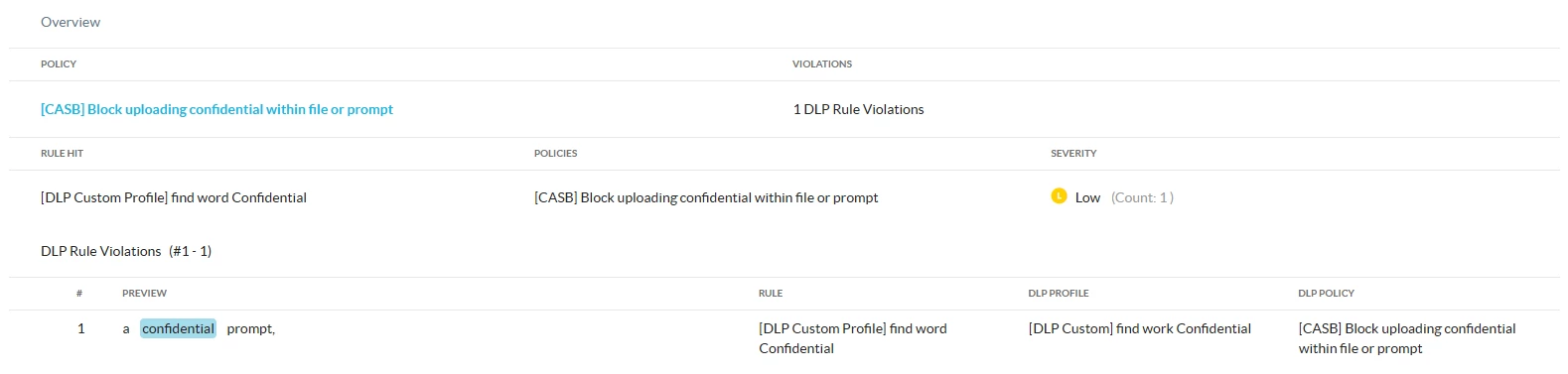
DLP Incident:
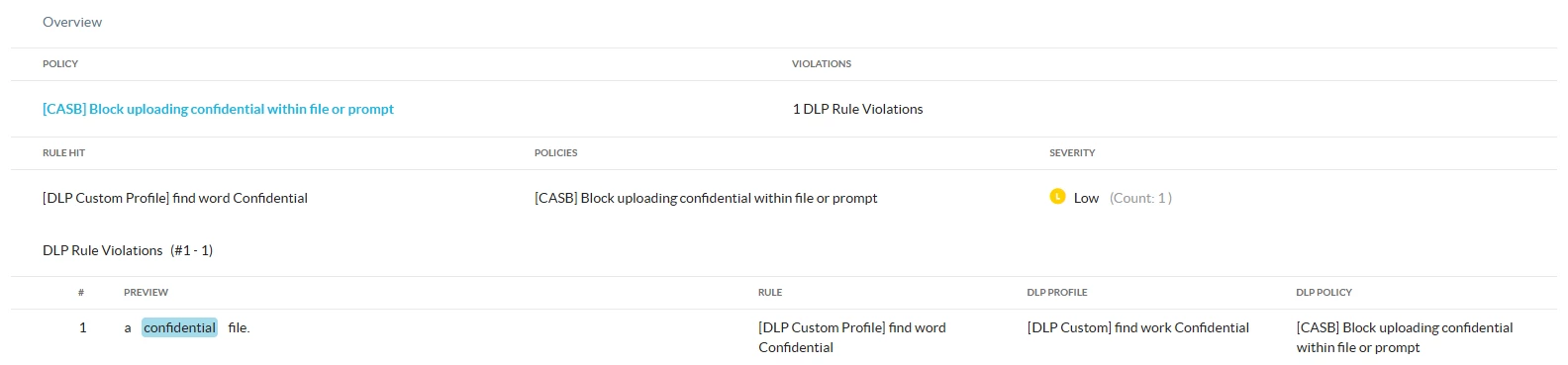
2- Uploading a file with the word confidential within its content:
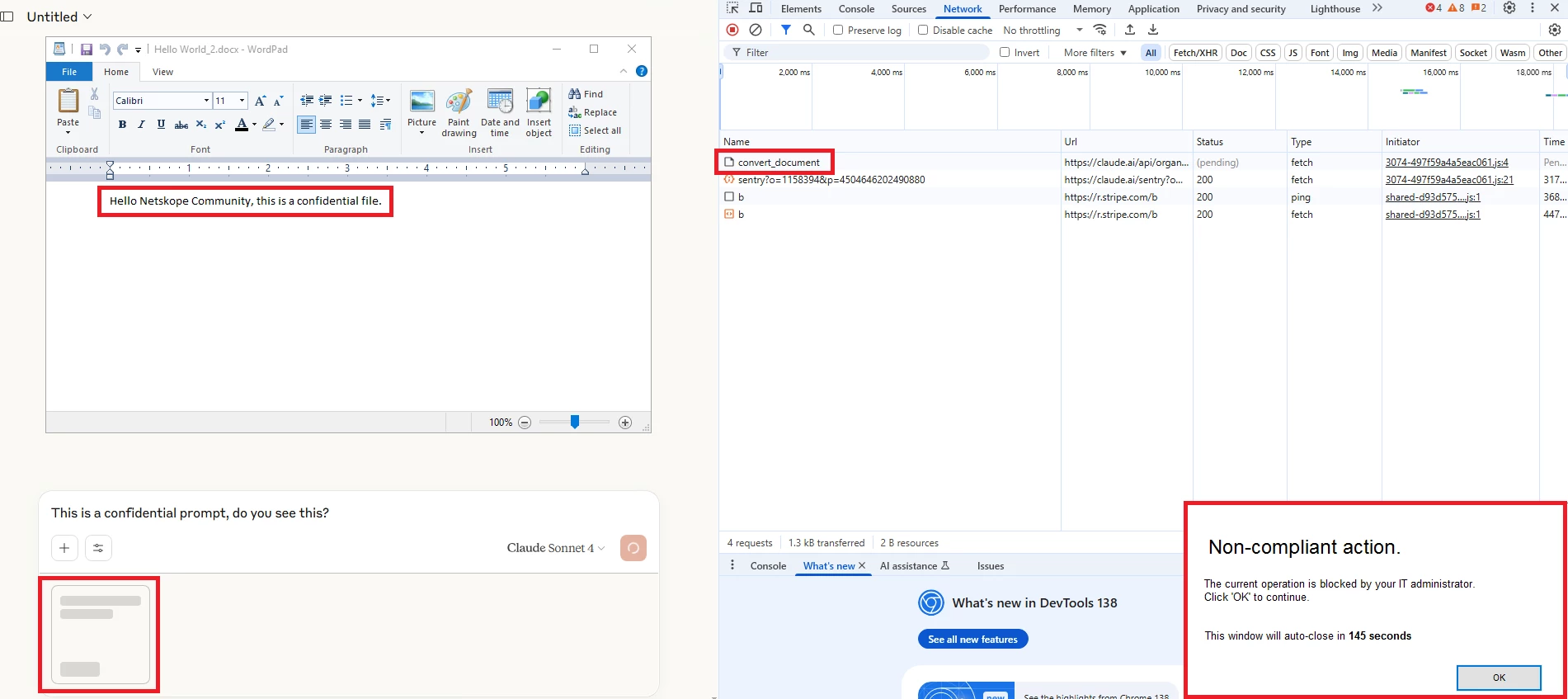
DLP Incident:
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.






