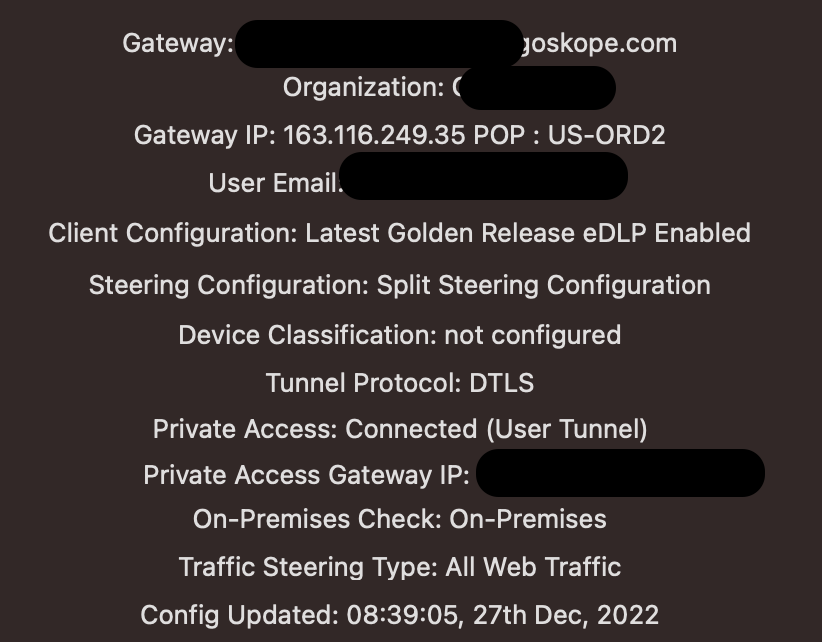
Hello,
New user here.. I have a Mac device that doesn't want to connect to the internet at all unless we disable NetSkope. I noticed a ton of errors in the logs that show this as well as UDP like the one below and well as the Network interface errors. Any help will be much appreciated
stAgentNE p3662 t6691 error nsClientFlow.mm:150 nsClientFLow Flow networkInterface is nil
stAgentNE p3662 t6691 info bypassAppMgrUDP.cpp:210 BypassAppMgr Blocking UDP connection from process: safari,