Hi all,
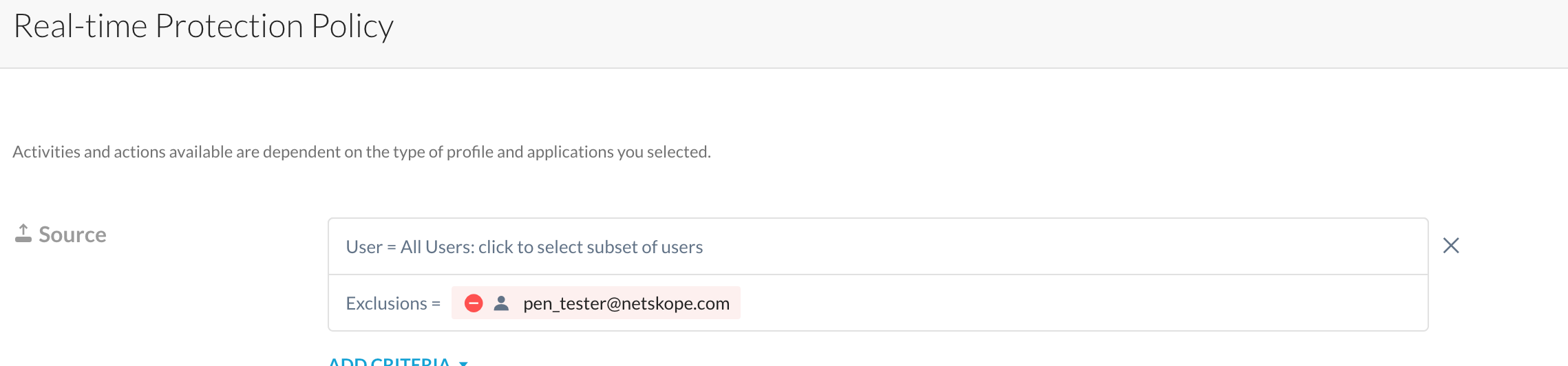
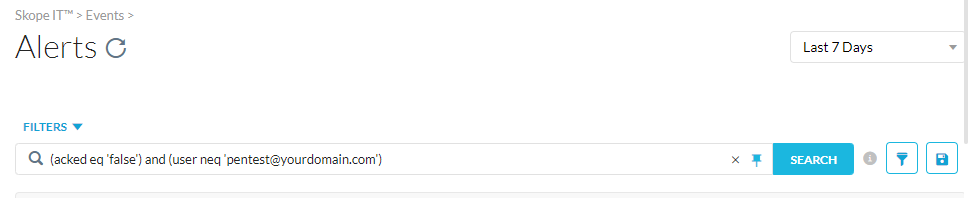
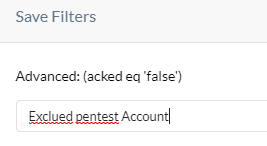
Wanted to get your thoughts on how to best approach something. We have a specific user account that's leverage for internal pen testing. As expected, there are Real-time Protection Policies that fire off alerts for this account's activity when active.
We've had a request to see if it's possible to filter this account out of either the policies or the alerts. Is there currently a way to omit a given account from a specific policy or alert (triggering)?