
Netskope Global Technical Success (GTS)
Blocking All Destination Traffic On Port 80
Netskope Cloud Version - 129
Objective
Blocking All Destination Traffic On Port 80
Prerequisite
Netskope Cloud Firewall (CFW) license is required
Context
Blocking all destination traffic on port 80, regardless of the destination web category
The customer may have a use case to restrict access to destinations over port 80.
Do You Know?
HTTP (port 80) destinations are not considered secure—why is that?
- Unencrypted communication:
HTTP sends data in plain text, meaning anyone intercepting the traffic (e.g., on public Wi-Fi or via malicious actors) can see everything—your passwords, messages, credit card info, etc.
- Susceptible to man-in-the-middle attacks (MITM):
Without encryption, attackers can intercept and modify data between your browser and the website without either side knowing.
- No authentication of the server:
HTTP doesn’t verify the identity of the server, so users can be tricked into visiting fake or malicious websites (phishing).
- Data integrity issues:
Because traffic is not protected, data can be tampered with during transmission.
Configuration
Follow the steps below to block port 80 traffic using Netskope Cloud Firewall (CFW).
Step 1 - Create a custom Firewall app
Path: Netskope Tenant UI >>> Security Cloud Platform >>> Traffic Steering >>> App Definition >>> Cloud & Firewall Apps >>> Firewall App
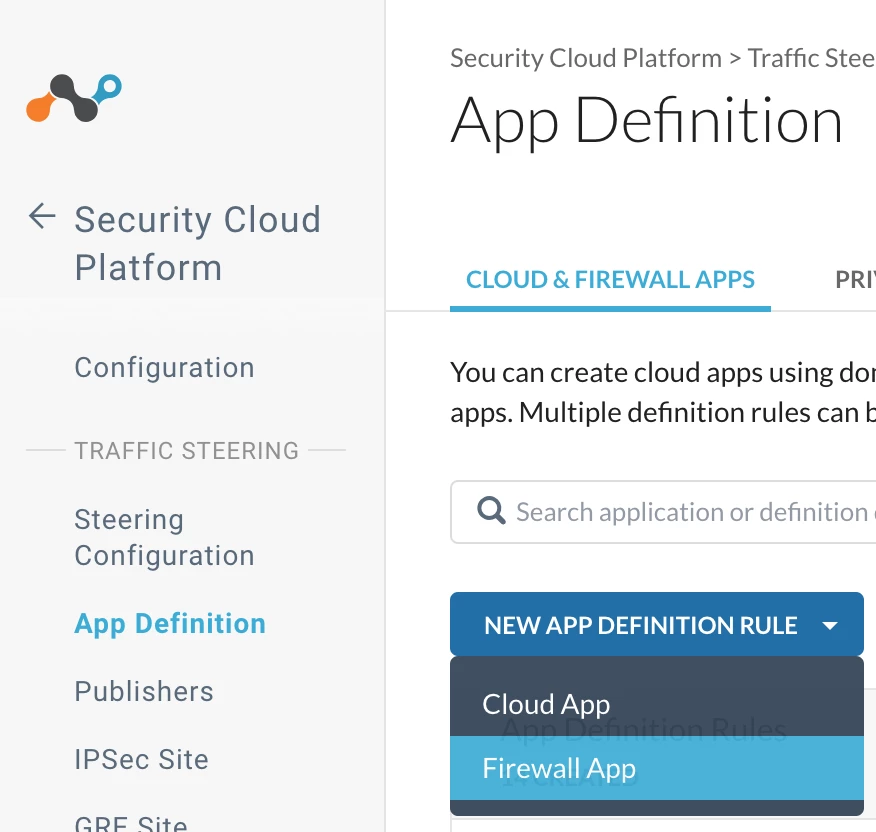
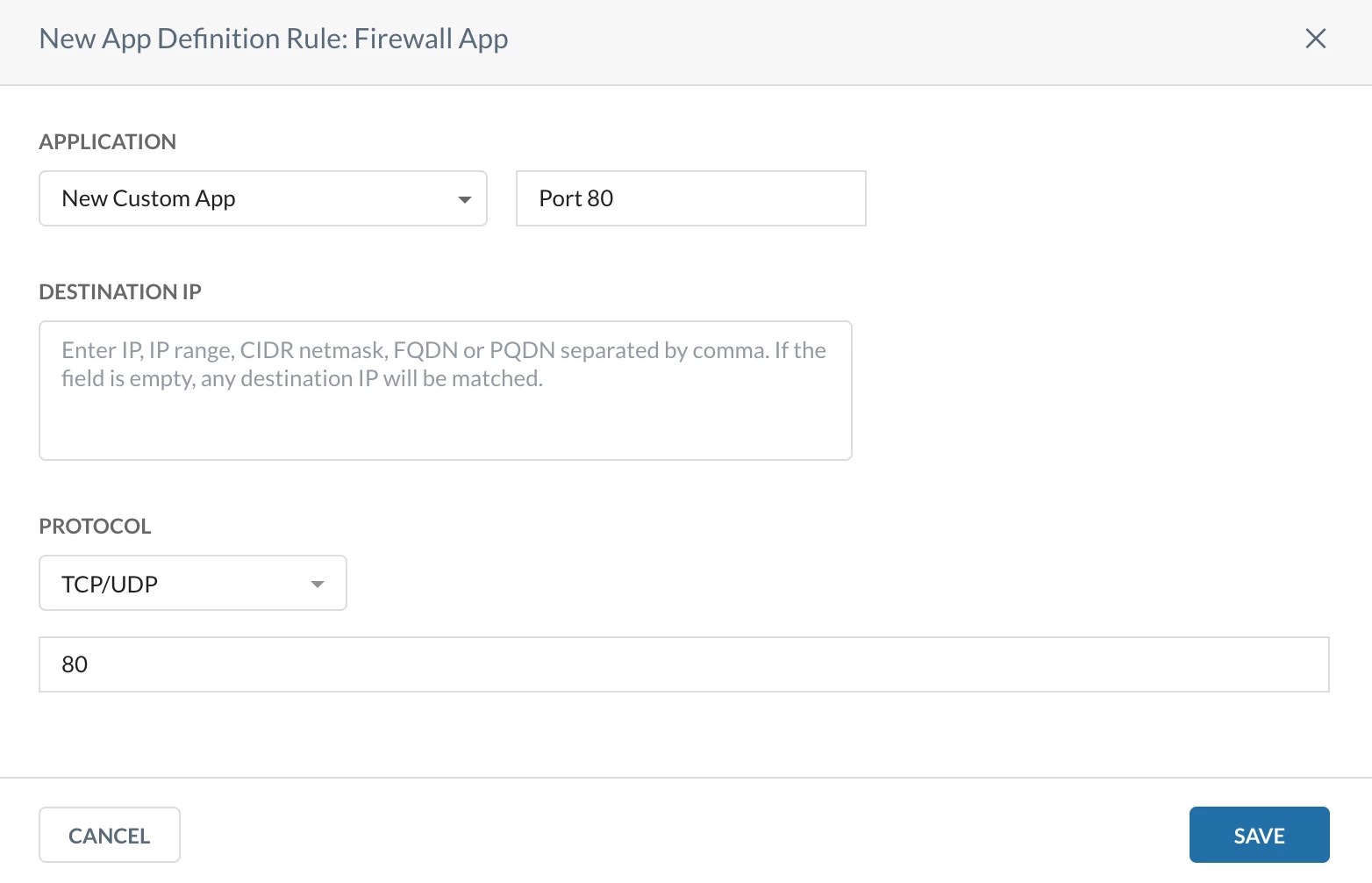
Step 2 - Create a Realtime Protection Policy
Path: Netskope Tenant UI >>> Policies >>> Realtime Protection >>> New Policy >>> Firewall
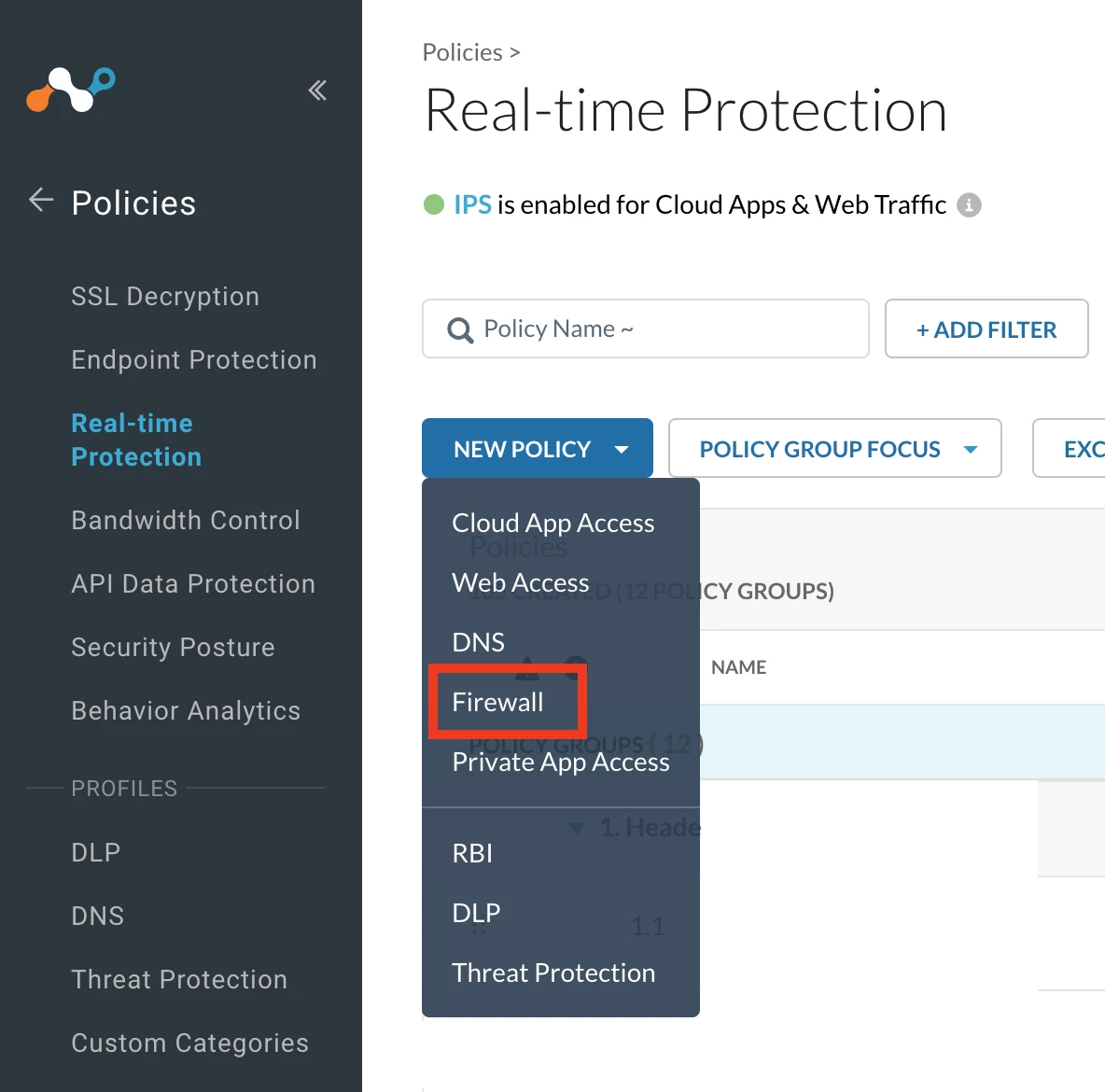
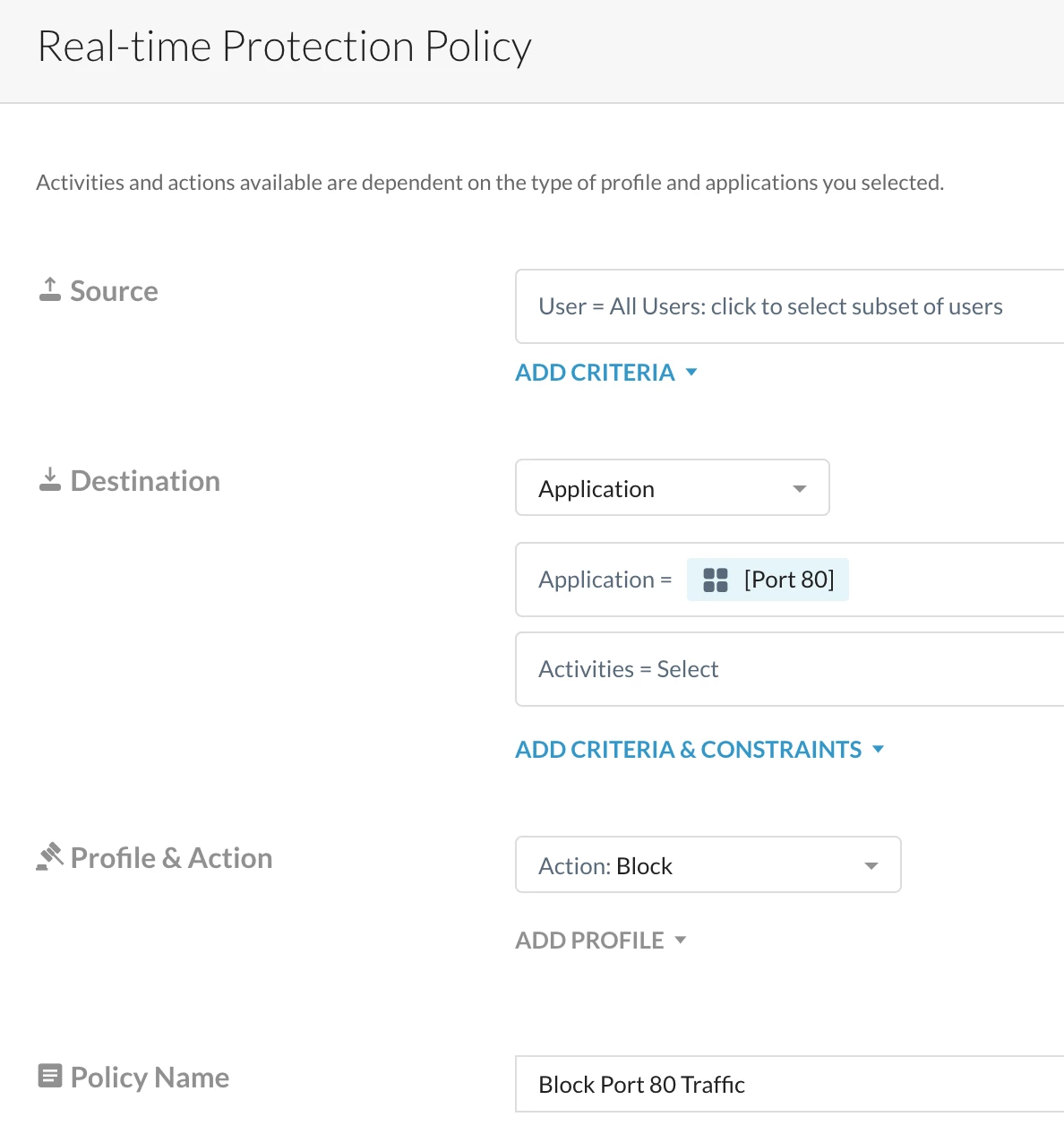
Verification
- Access http://oldwebsite.com
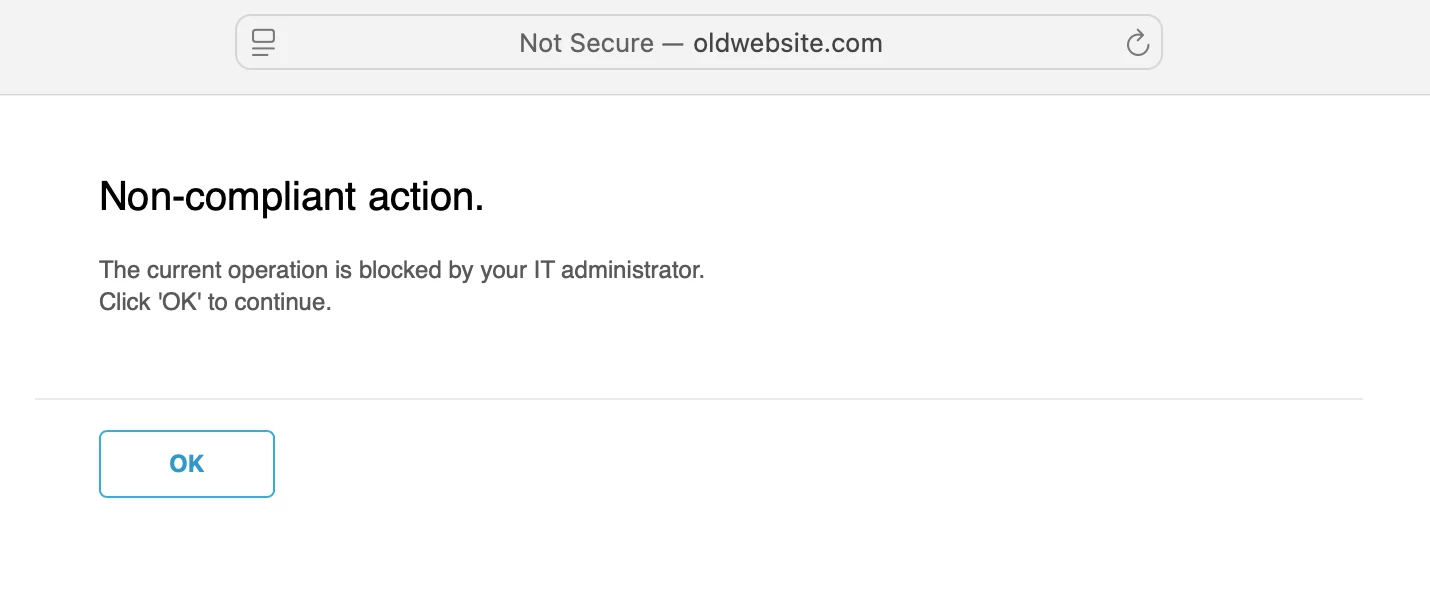
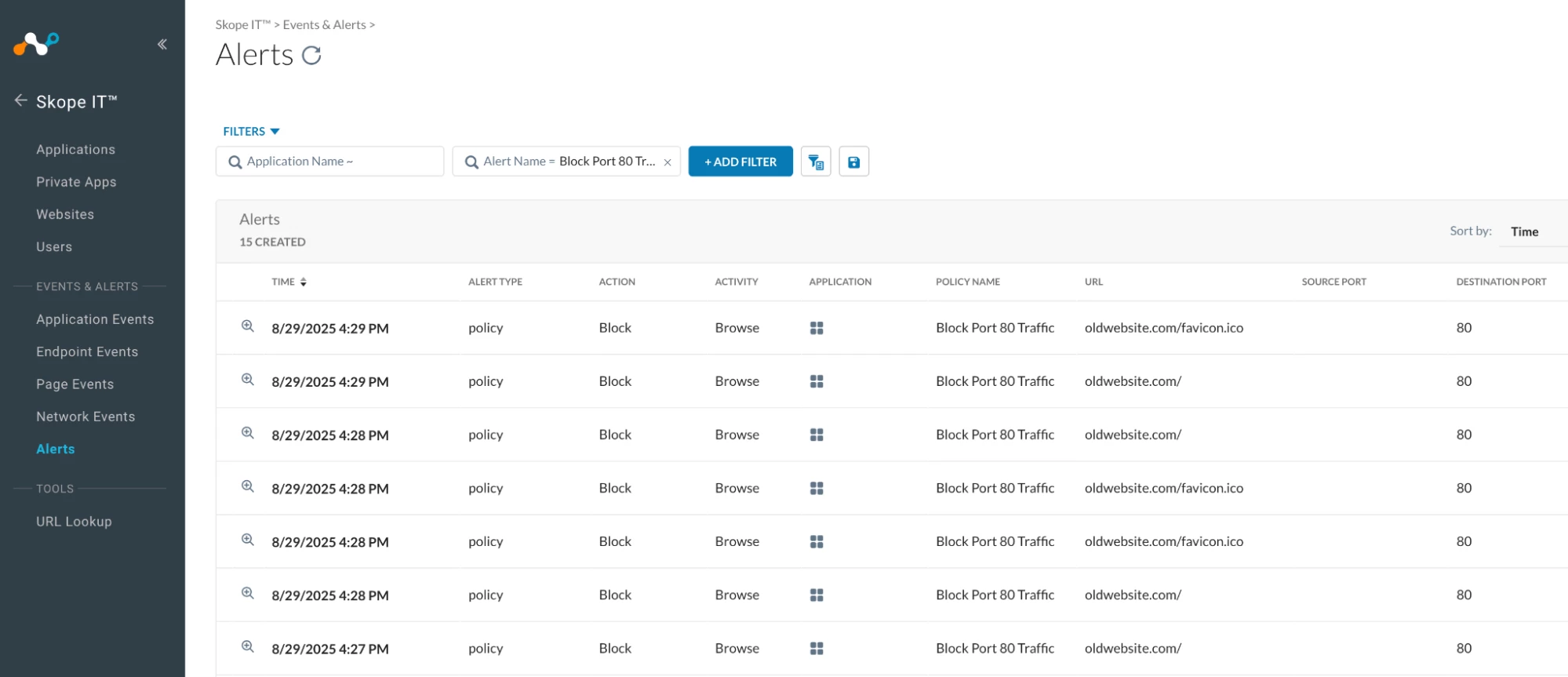
- Policy hits
Author Notes
- For details about the Netskope Cloud Firewall license, please contact your Netskope Account Manager.
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.







