Hi Team,
I have a query regarding one of our customers who is currently using an existing DNS SEC setup for both outbound and inbound traffic. Customer already have NGSWG procured. Their current traffic flow is as follows:
[Roaming user] USER Endpoint >>> Active Directory DC >>> DNS Forwarder >>> DNS SEC CLOUD.
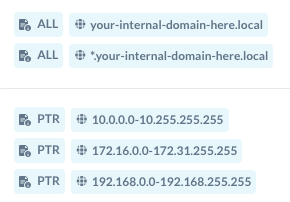
For Internal their is a differ IP configured for them to resolve but need to connect with Citrix VPN.
They want to understand how the traffic flow works with Netskope DNS SEC, which differs as it intercepts DNS queries for inspection.
Here’s the scenario: When a user queries a domain, the request first goes to the Netskope cloud for Deep Packet Inspection (DPI). If the domain is malicious, it gets blocked; otherwise, it is allowed and forwarded through the Secure Web Gateway (SWG).
My question is: If the user’s machine is configured with the DNS IP of the Active Directory (AD), does Netskope return the allowed traffic back to the client machine and then forward it to the DNS AD IP configured on the machine? Or does the Netskope cloud resolve the DNS query itself, (If the traffic is allowed) allowing the user to access the external domain directly?
I’m specifically referring to external domain traffic.
Additionally for internal domains they need to connect via citrix does we replace that with NPA configured in such a way that user access the private app or domain will resolve by their infra DNS it self while using publisher DNS ?