Overview
The integration of Netskope SD-WAN with Microsoft's SSE solution facilitates inspection of internet bound originating from SD-WAN branches/VNETs destined for internet applications routed through Microsoft's SSE solution.
This guide encompasses a step by step guide to connecting Netskope SD WAN appliances to Microsoft's SSE solution, specifically for SaaS/internet applications.
Microsoft Entra Internet Access traffic, alongside Microsoft Entra Access, are integral components of Microsoft's SSE solution: Global Secure Access. Microsoft Entra Internet Access ensures secure access to internet and SaaS apps, providing robust protection for users, devices, and data against internet-borne threats. This document focuses on the Internet Access use case.
In this guide, you will be creating an Internet Protocol Security (IPSec) tunnel between a Netskope SD WAN Appliance, at your remote network and the nearest Global Secure Access endpoint. All internet-bound traffic is routed through the core router of the remote network for security policy evaluation in the cloud. This offers a seamless deployment to the MSFT SSE solution where the installation of a client isn't required on individual devices.
Architecture
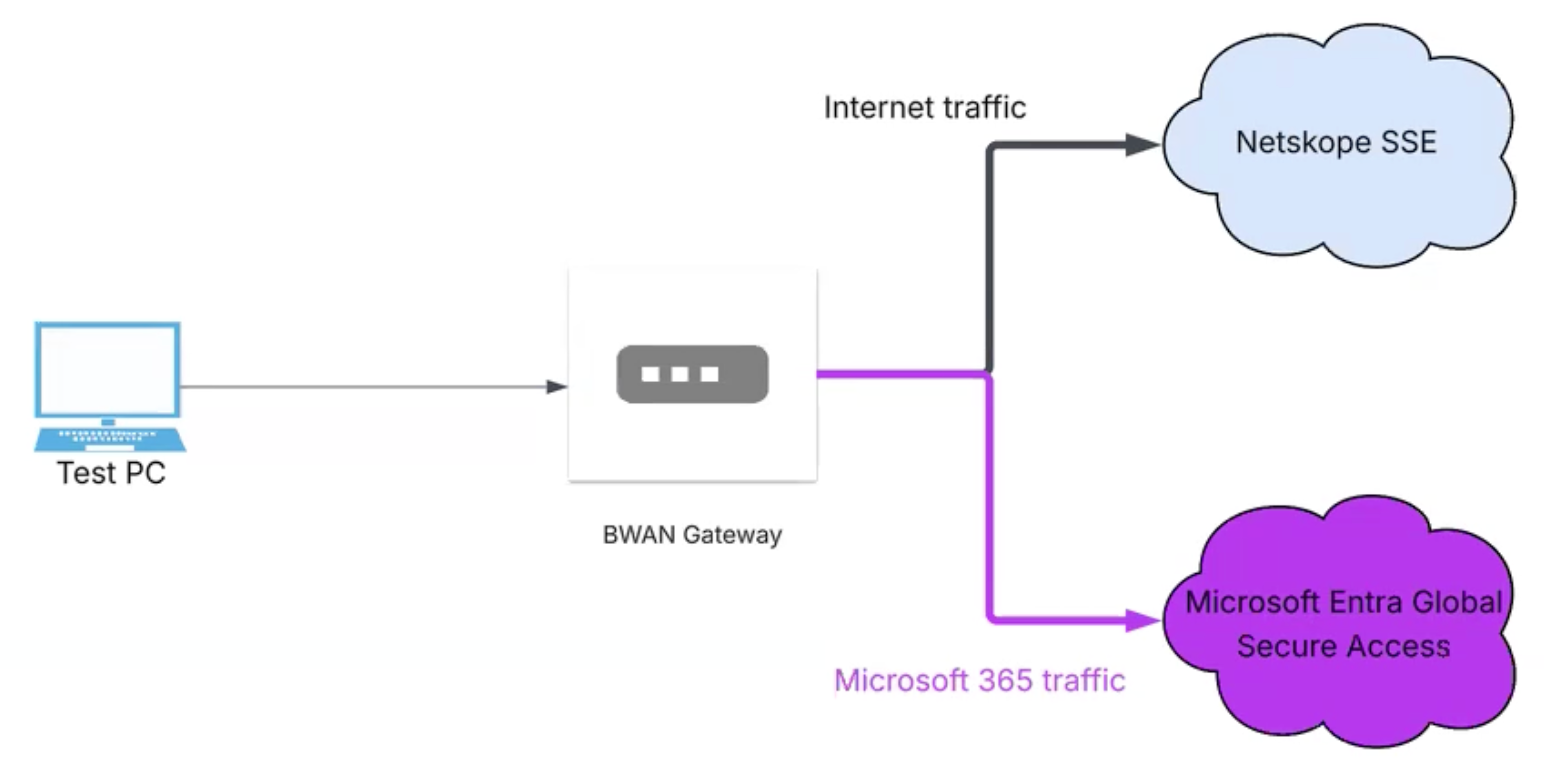
In this architecture workloads or endpoints sitting behind a BWAN appliance in either a Virtual Network or On Premise sites. A BWAN Gateway directs traffic via an IKEv2 IPsec tunnel to the closest Global Secure Access gateway.
Prerequisites
- Microsoft’s SSE solution account
- Netskope SDWAN Appliance/s
- BGP routing over IPsec (IKEv2 required)
Deployment Steps
Navigate to the Manage → Gateways tab and select the desired BWAN Appliance you want to connect to Microsoft Entra SSE gateway. (Spoke-India) In this example
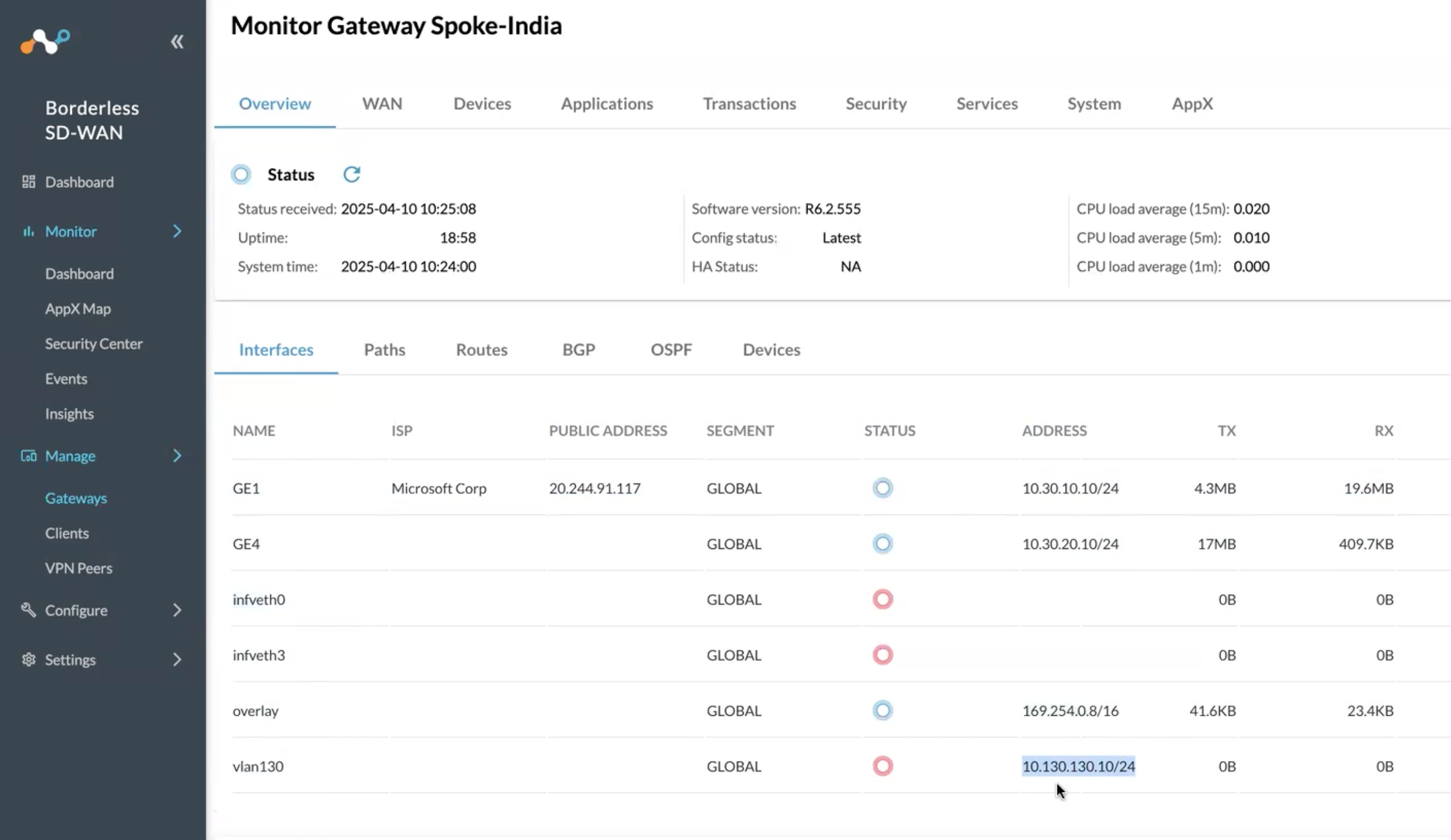
Note* For configuring BGP on the Netskope BWAN Appliance
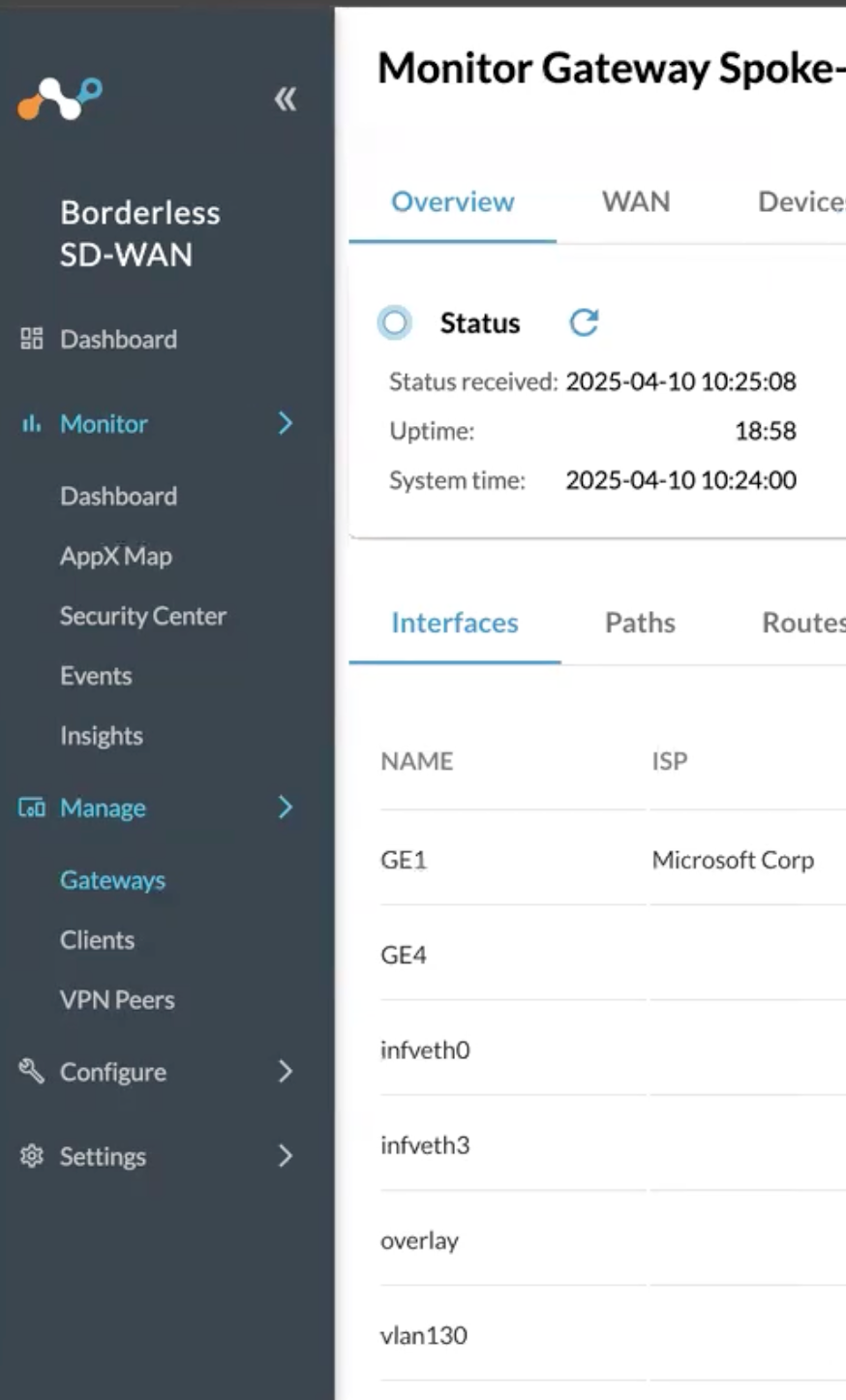
In this scenario we are using the IP in VLAN130 (see screenshot) for the BGP Router ID.
- 10.130.130.10
Next log into the Entra Portal to retrieve tunnel and peering information:
Navigate to Global Secure Access → Connect → Traffic Forwarding
When you select the traffic forwarding profile for Microsoft Traffic Profile this will ensure Microsoft only advertises BGP routes for Microsoft applications. (No more updating static routes for prefix changes!)
Now navigate to the Remote Networks tab and add a Remote Network:
Click select
Provide a name for the remote Network (NS GW in this example which maps to a deployed GW)
Click Next to be navigated to Connectivity
Click Add a link and provide the following details on the right:
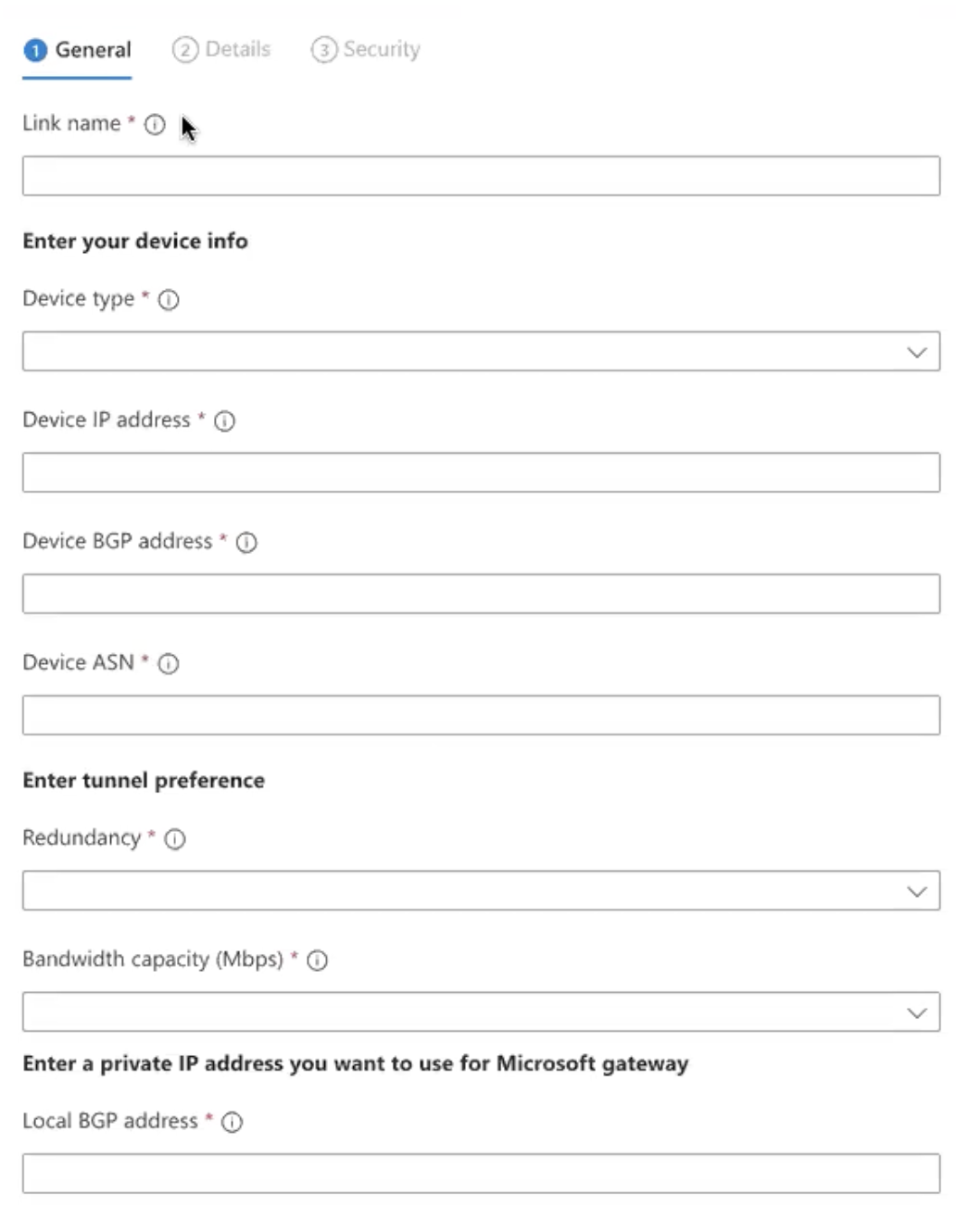
Provide a Link Name
Device Type select: Other
Device IP Address: This is the public IP of the BWAN Appliance (See GE1 in screenshot)
Device BGP Address: This is the VLAN interface 130 from the earlier screenshot
Device ASN: 400 (This is static and the Netskope BWAN ASN will always be 400)
Redundancy: No Redundancy
Bandwidth capacity: 1000 Mbps
Local BGP Address: Enter whatever private IP that does not overlap with anything in your environment. 10.10.10.10 for example
- Save this IP Address as you will need it to configure a static route on the Netskope SD WAN appliance over the IPsec tunnel.
Click Next and enter the tunnel details: (select custom)
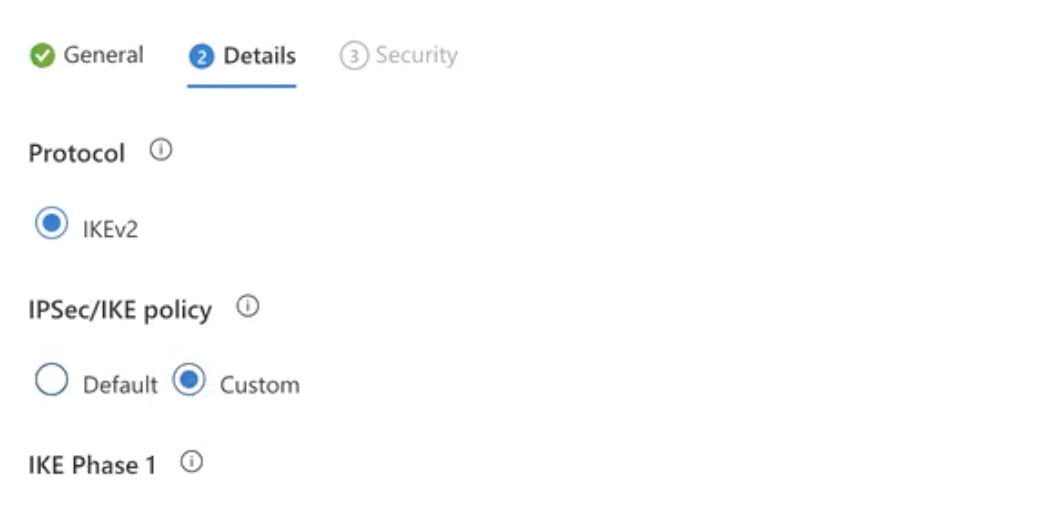
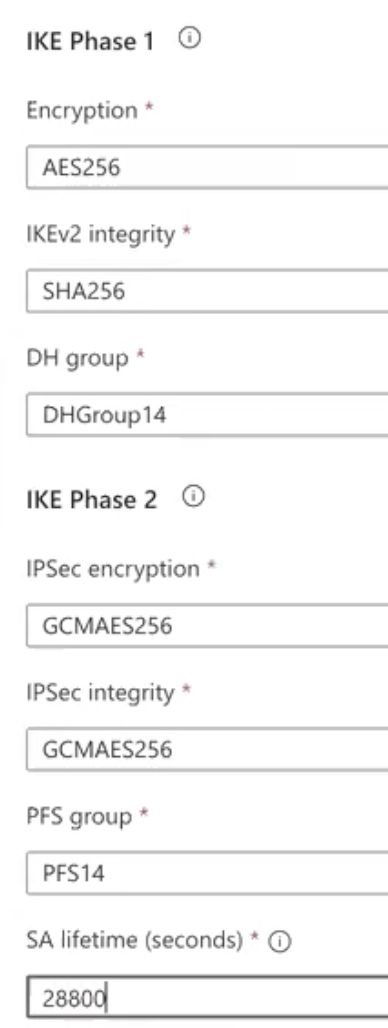
Enter the following phase 1 parameters as seen in the screenshot above.
Select Next and enter a Pre Shared Key and save this to be entered in the Netskope Dashboard later.

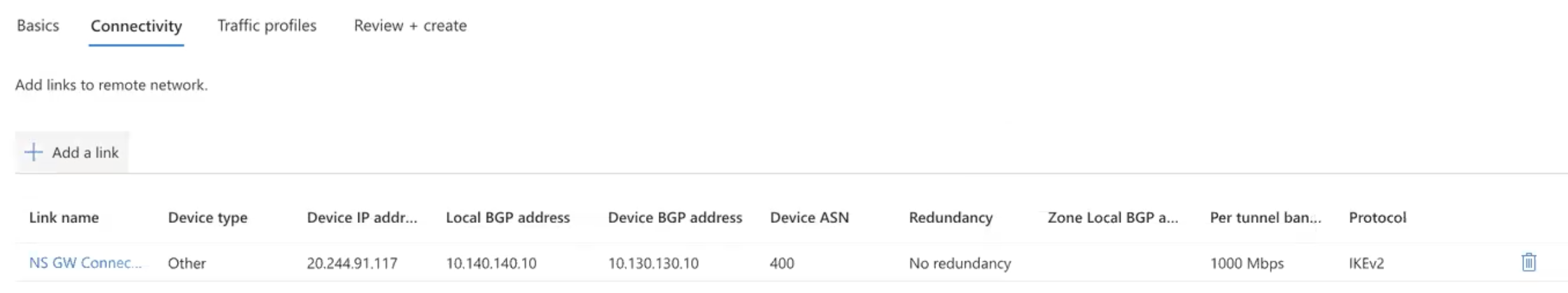
Now the Connectivity part for the site is done. Naviate to Traffic Profiles on the right:
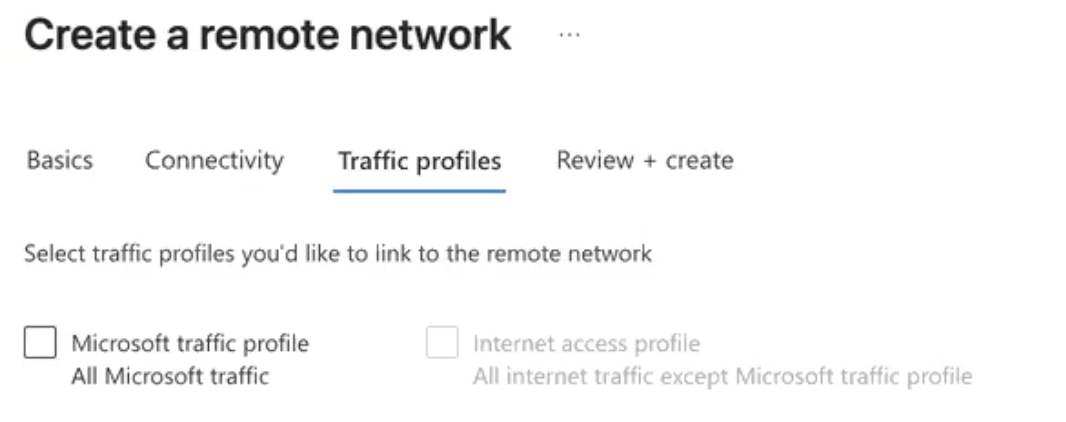
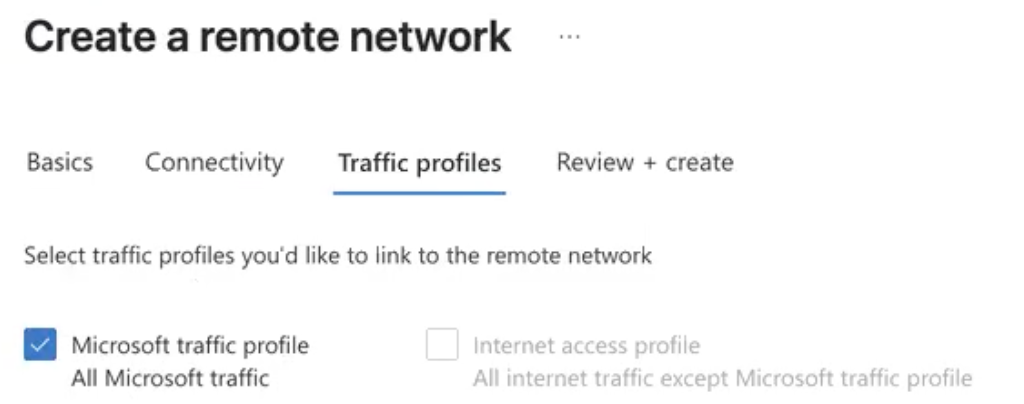
Seect the Microsoft traffic profile so those prefixes are advertised over the BGP session to the netskope appliance.
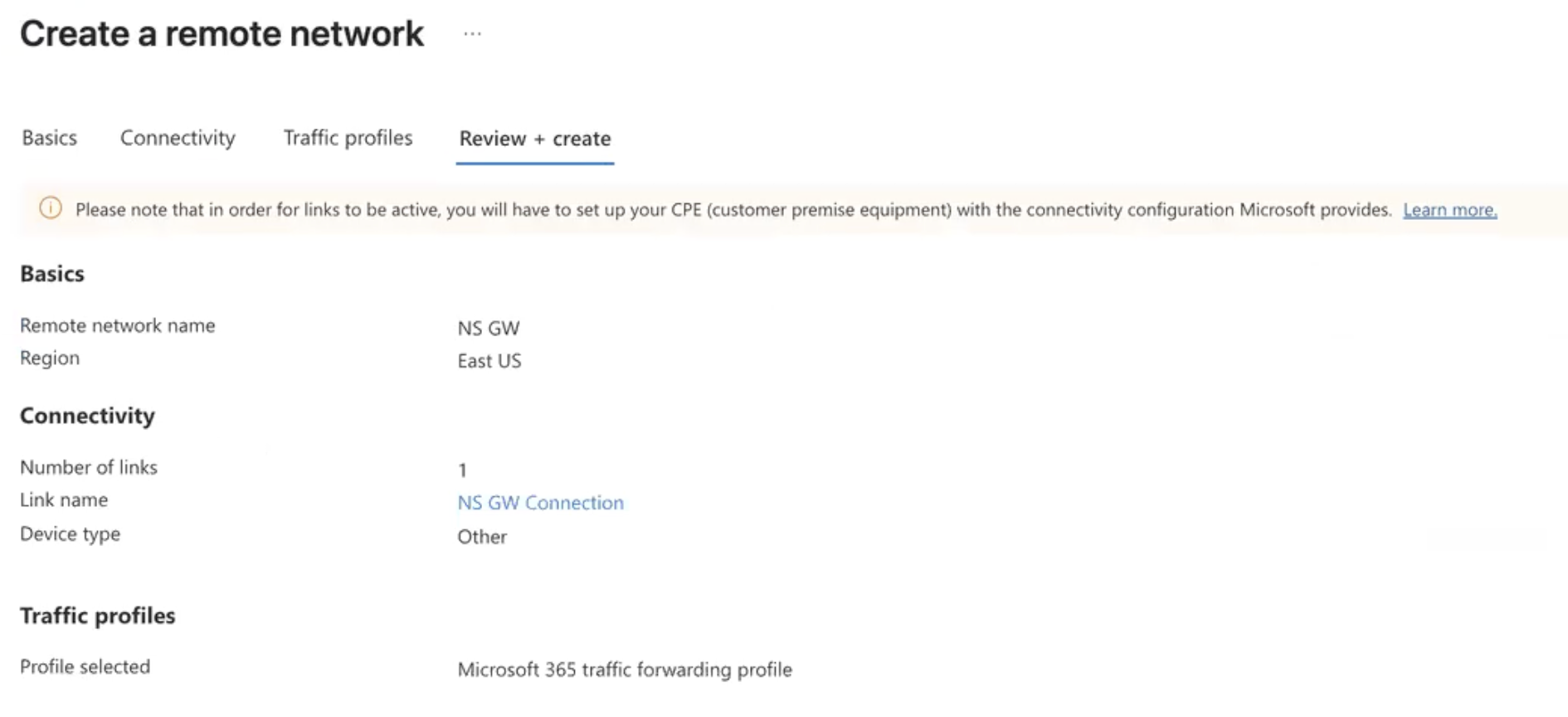
Navigate to Review and Create
Once you click Create you are done with the Microsoft configuration! Congratulations
Now navigate to the Netskope BWAN portal to the gateway:
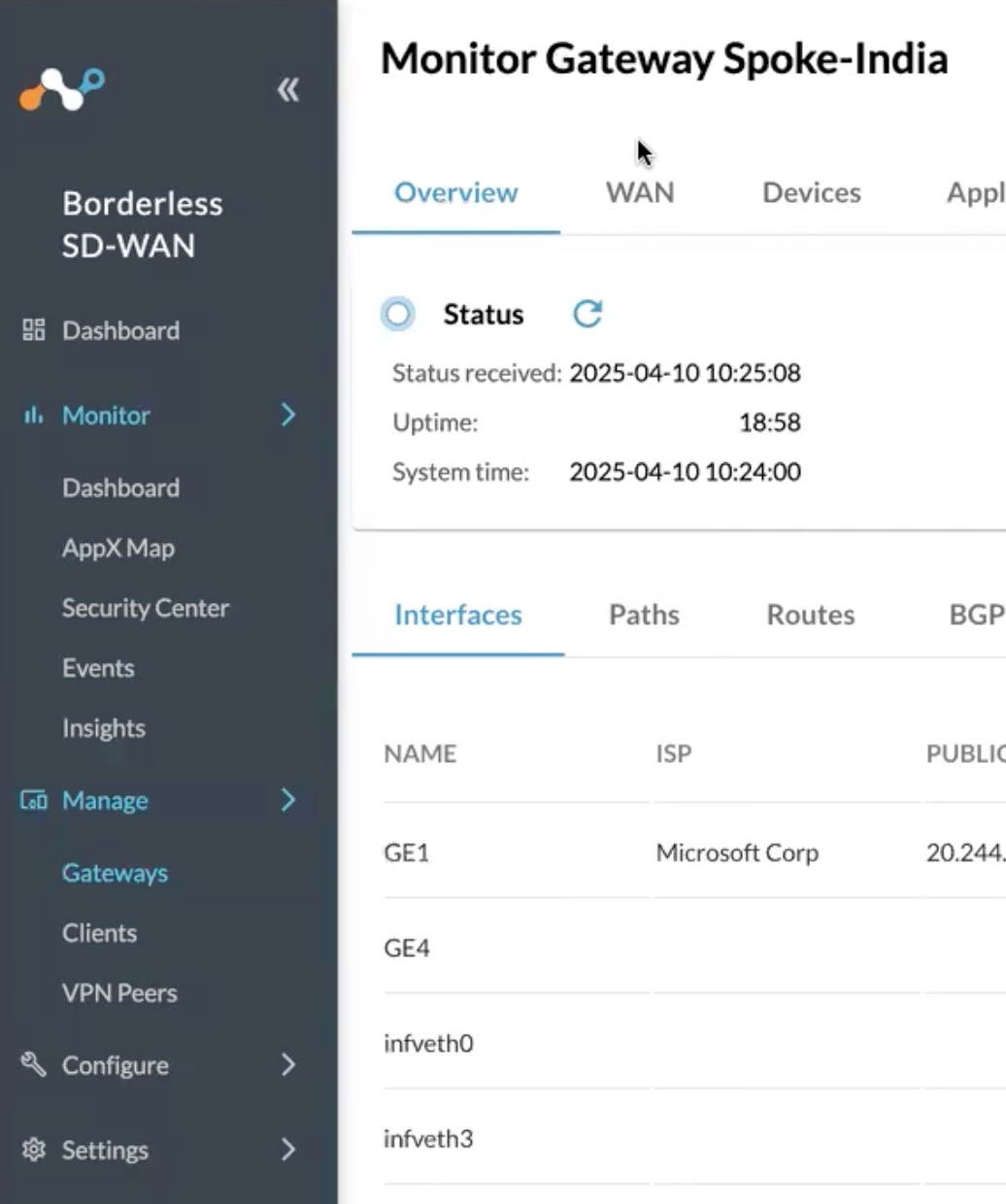
Now navigate to the VPN Peers tab:
Click the blue checkbox to create a new VPN peer:
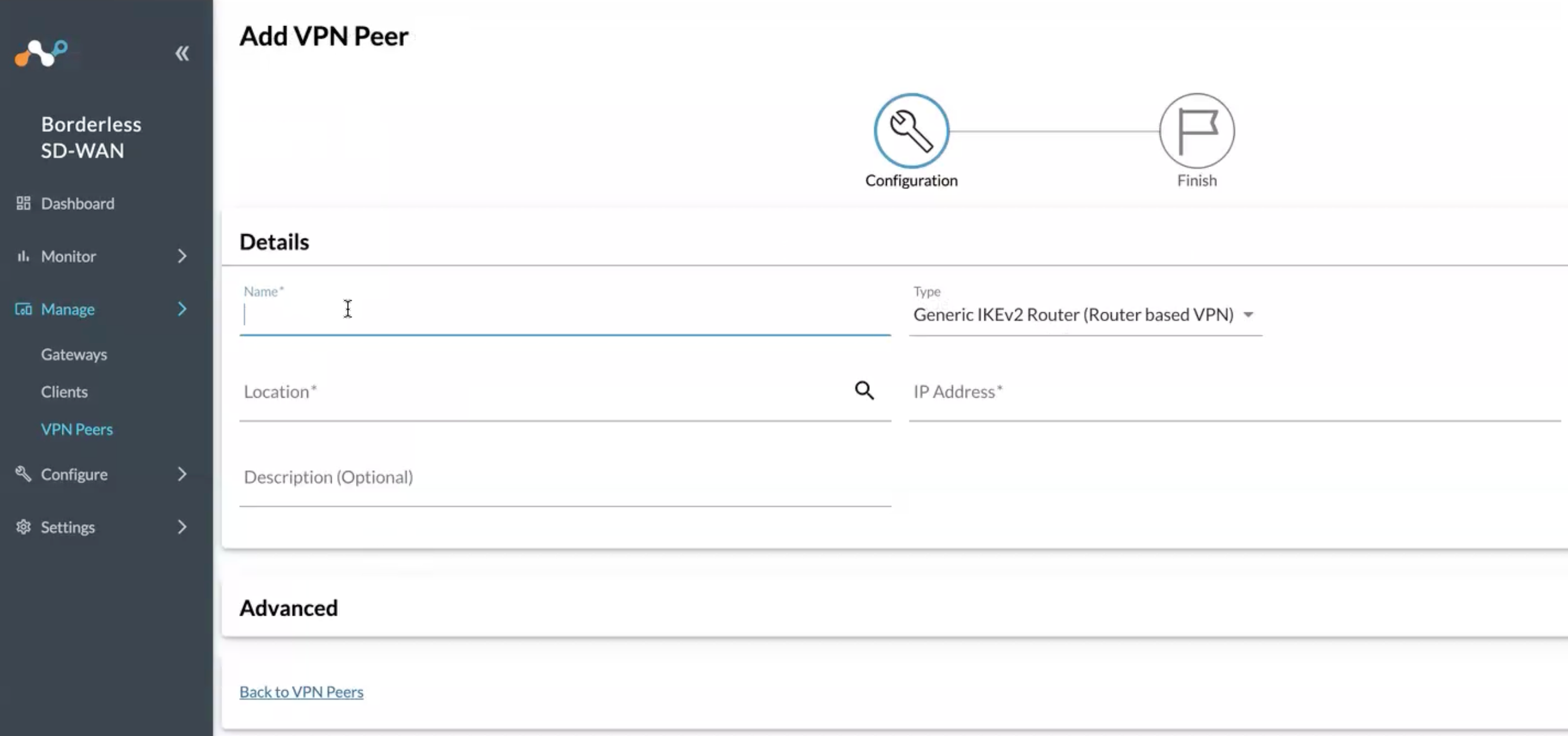
Enter a name (like MS Entra)
Location (Match to your region)
IP Address: (This is important) You need to retrieve this from the Microsoft Entra dashboard under Remote Networks
Click on View Configuration
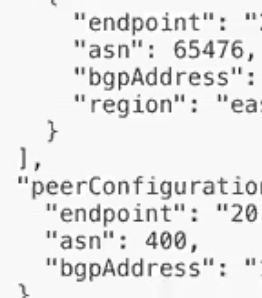
The following data will be presented for BGP and IP Address info.
Copy where it says endpoint and this is the IP you want for IP Address
Now navigate back to the Netskope Dashboard and copy the IP Address and under Advanced enter the following IPsec parameters:
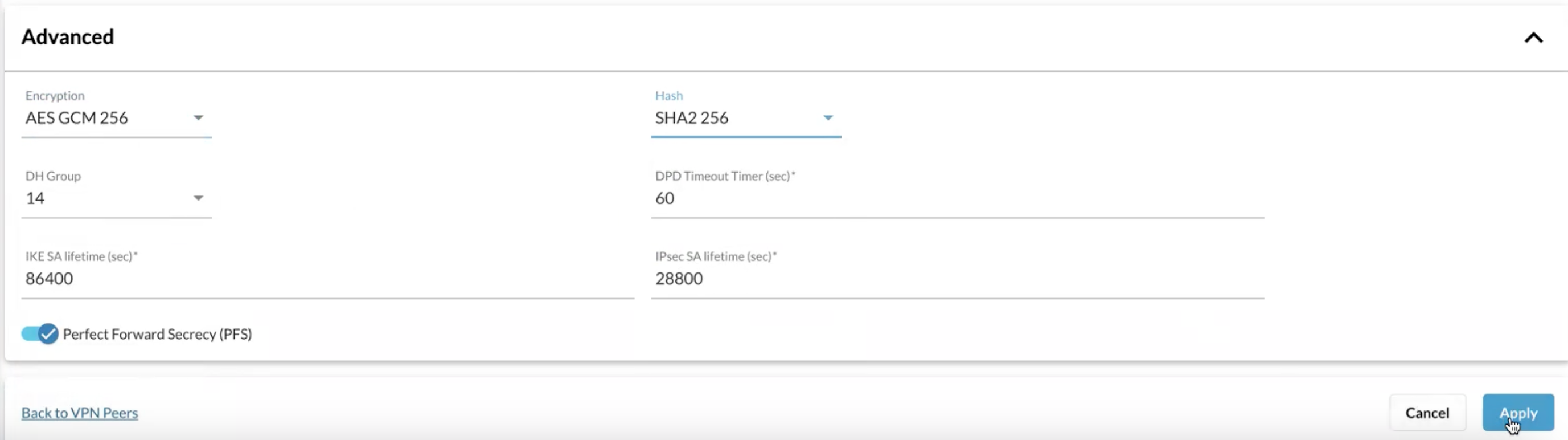
Click Apply and you will now see a VPN peer created:
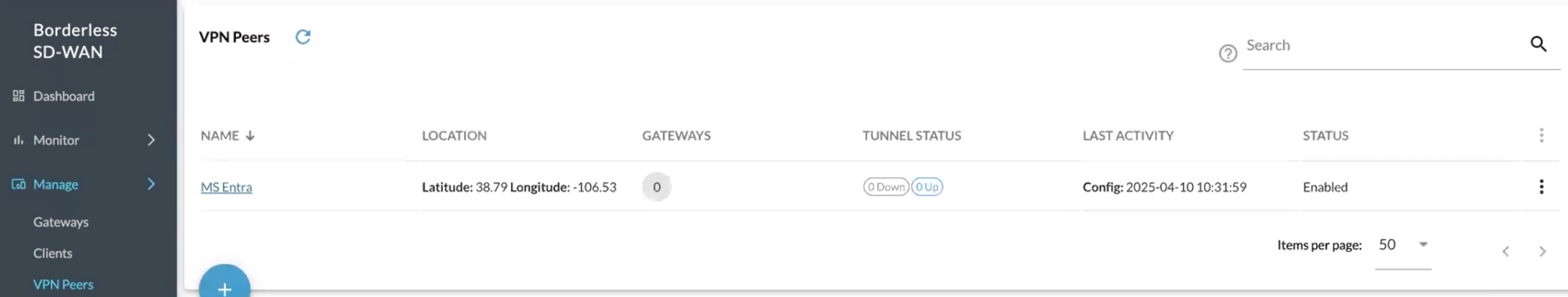
Now we created a VPN peer so we need to apply it to the Gateway.
- For this go to Gateways
- Select your Gateway (3 dots on the right)
- Click Configure

Navigate to Segments and click the Global segment:
There is a lot of configuration that needs to be done here
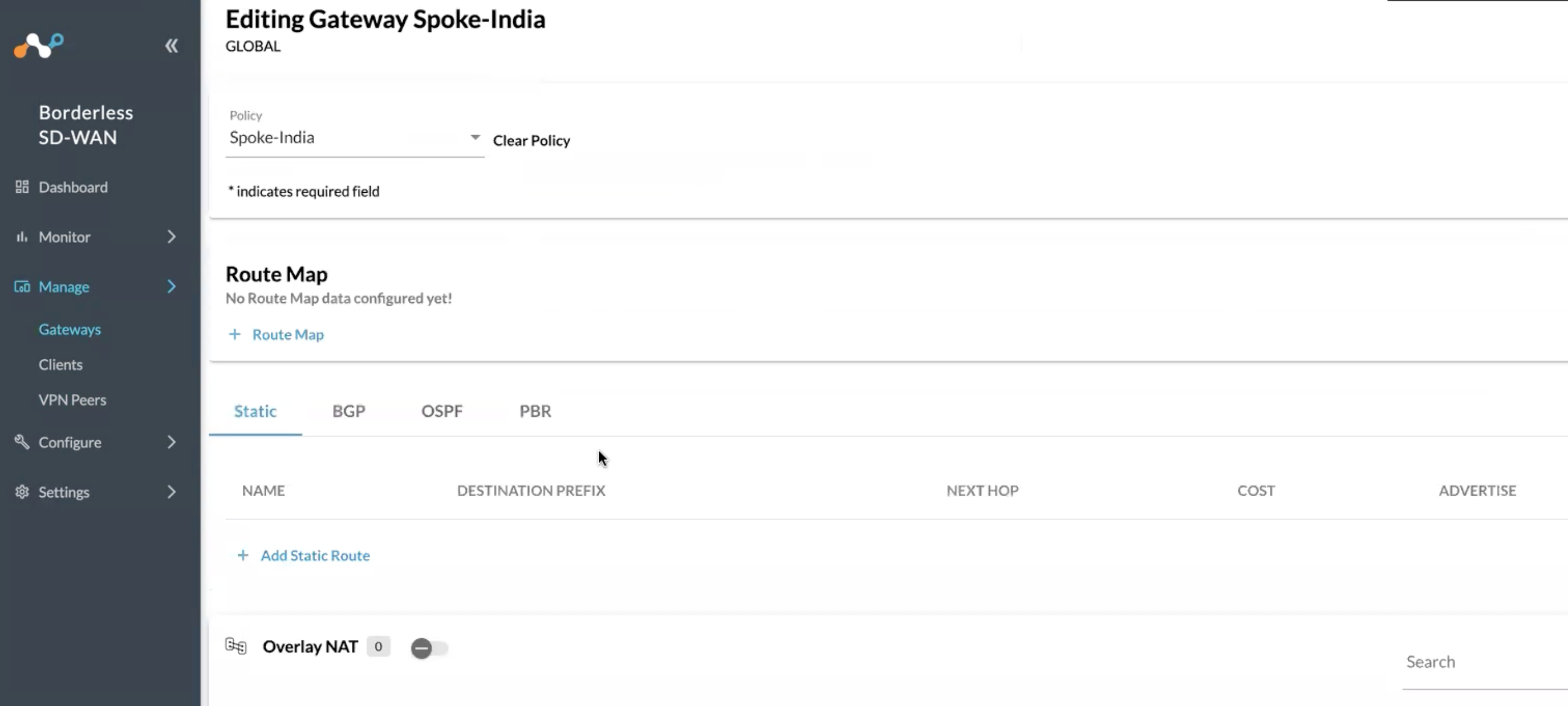
First thing we need to do is get the IPsec tunnel up.
Scroll down and select Add VPN Peer
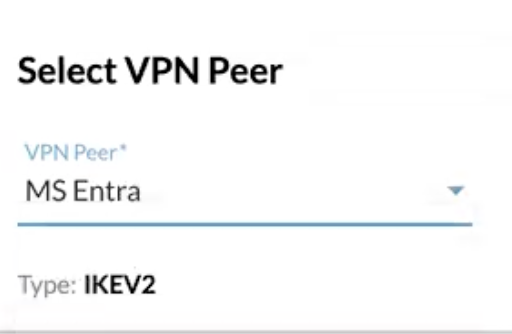
Select your VPN Peer that you configured in the previous steps from the dropdown.
Now select Add Tunnel
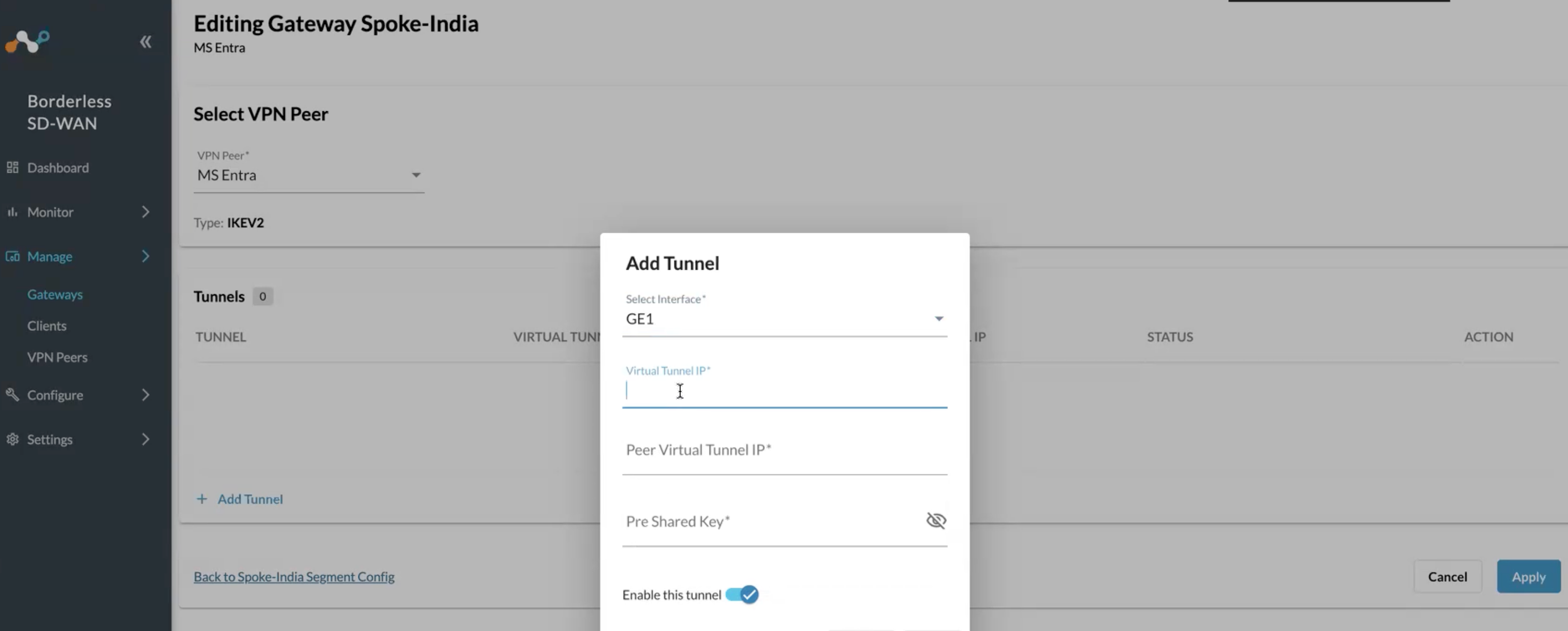
Select the WAN interface GE1 with the Public IP we entered in the Entra portal earlier.
Virtual Tunnel IP: (Netskope Appliance IP) pick any unused martian or private IP
Peer Virtual Tunnel IP: (Entra GW IP) pick any unused martian or private IP
Pre Shared Key: Paste same key from earlier steps in Entra Dashboard
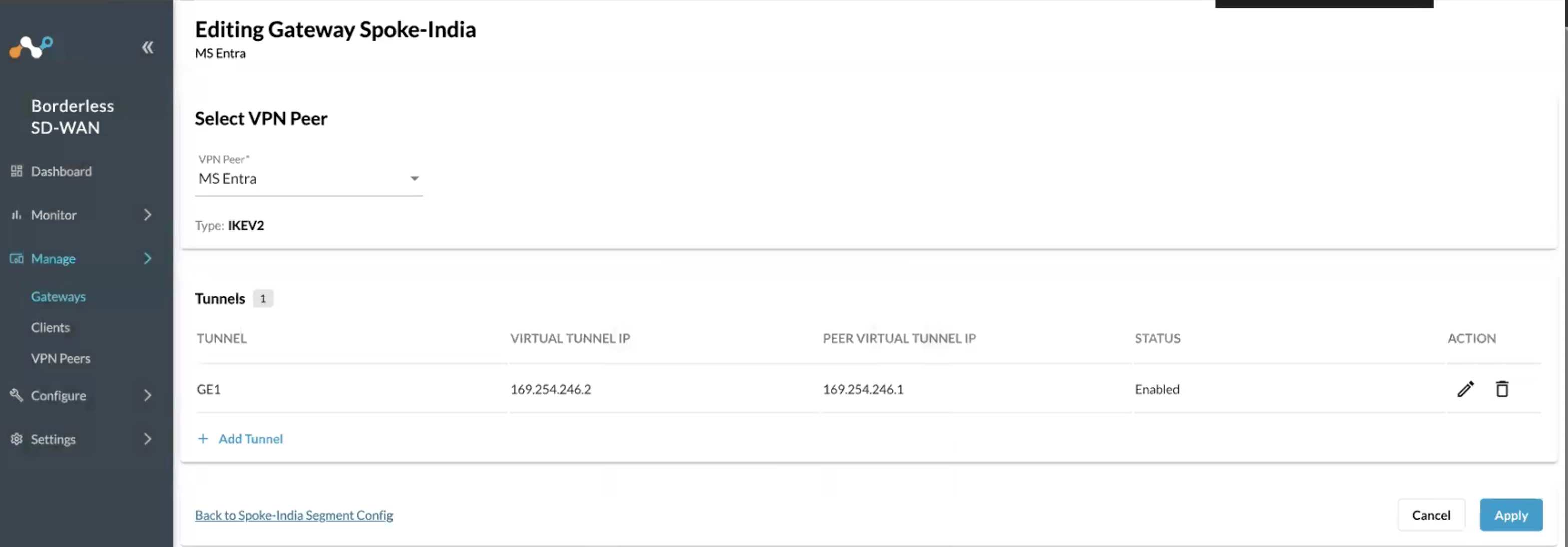
Now click on Apply
Next we need to add a static route to the Entra BGP Peer IP/Router ID:
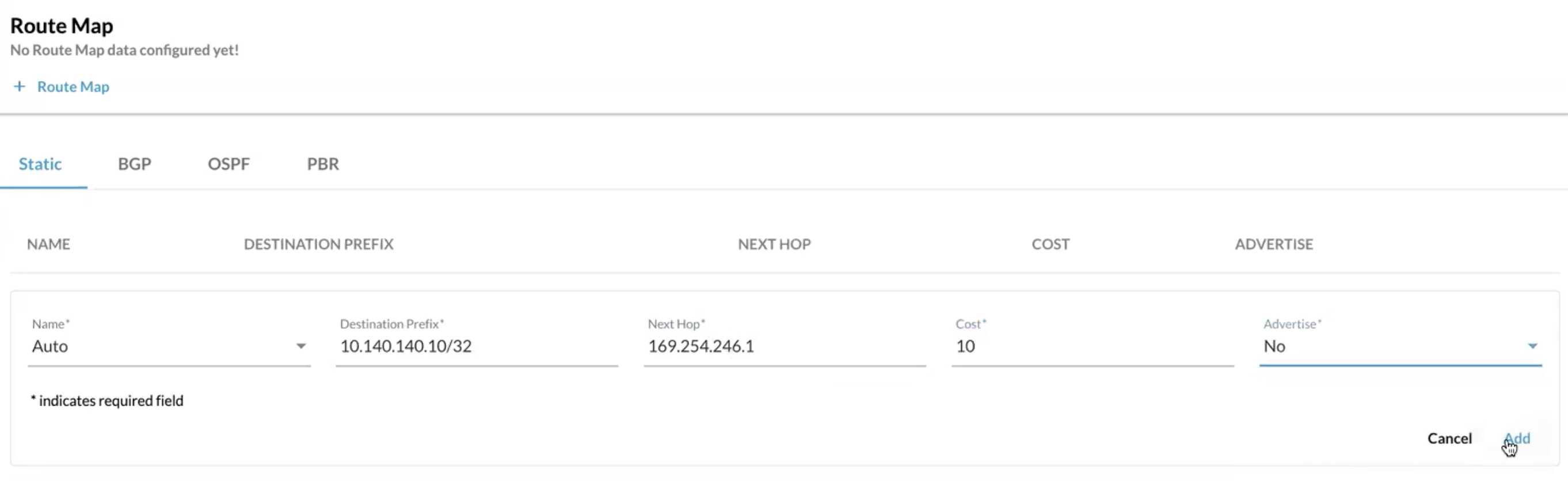
- Name: Enter Name
- Destination Prefix: BGP Peer IP for Entra (x.x.x.x/32)
- Next Hop: Peer Virtual Tunnel IP
- Cost: 10
- Advertise: No (We do not want to advertise this route to Microsoft or any other BGP peer)
The last thing to do is configure BGP Peer over the IPsec tunnel to Microsoft:
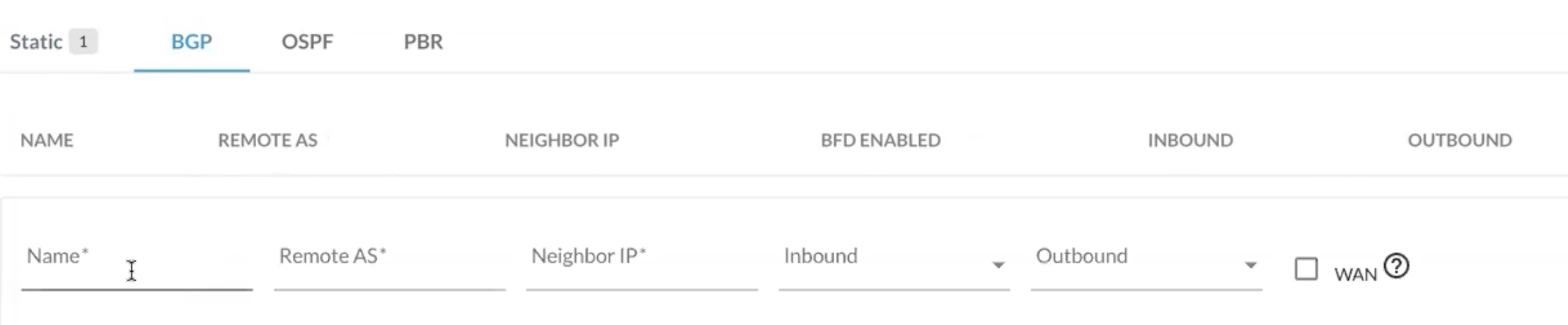
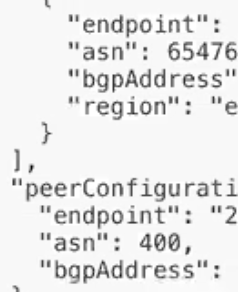
After you enter name you will need to provide the Remote ASN you copied from the View Configuration step above. Here Remote ASN would be “asn” 65476
Neighbor IP is the bgp Address
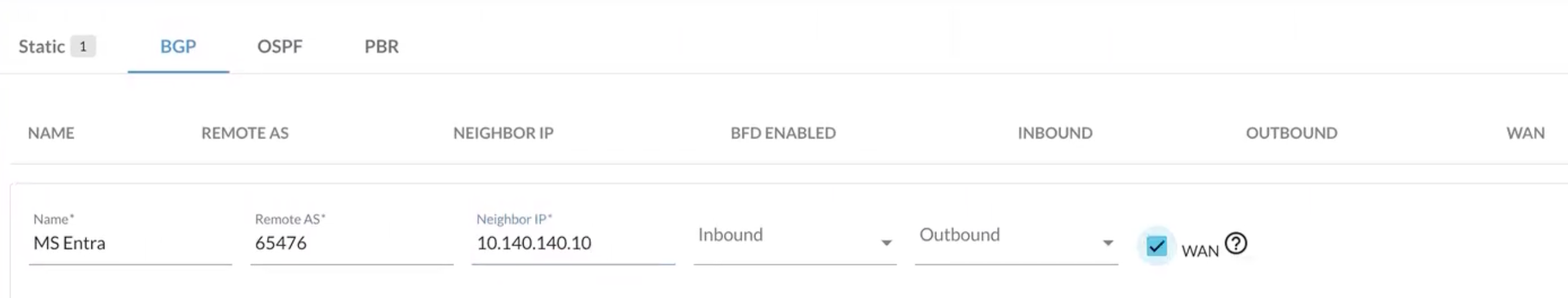
Also select WAN and finally click on Add
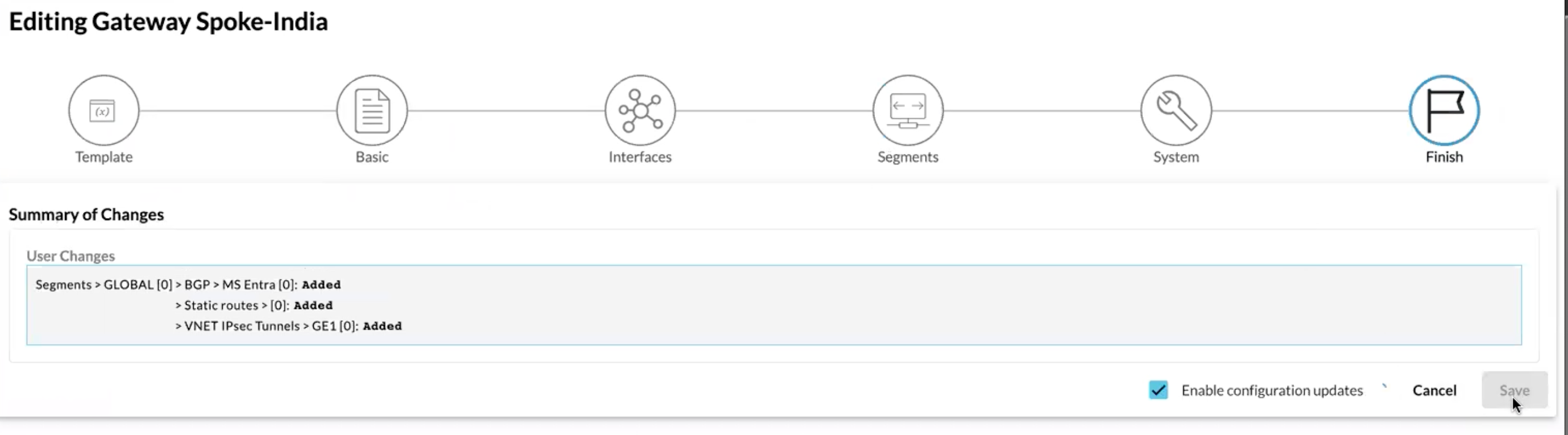
Finally Apply the configuration







