Sending Alerts and Events to Microsoft Sentinel using the Codeless Connector Framework
Seamless Log Shipping: Unlocking Netskope’s Native Integration with Microsoft Sentinel
In today’s security landscape, visibility and real-time insights into your organization’s data are critical for effective threat hunting and incident management. To meet these needs, Netskope has developed a native integration with Microsoft Sentinel using the Codeless Connector Framework—allowing organizations to easily stream all CASB alerts, DLP incidents, and threat logs into Microsoft’s cloud-native SIEM.
This blog explores how this new integration simplifies log shipping and delivers a scalable, cost-efficient way to leverage Microsoft Sentinel without deploying additional infrastructure like Cloud Exchange.
Why This Matters for Security Teams
Security teams are constantly battling an increasing volume of threats while juggling multiple tools and platforms for managing data and incidents. Many enterprises use Microsoft Sentinel for incident response and threat hunting, but previously, getting comprehensive Netskope data into the Azure console involved additional steps and costs.
With this integration, you now have a simplified, direct path to push logs and alerts into Microsoft Sentinel—no need to deploy the Cloud Exchange platform.
Key Benefits of the Netskope–Microsoft Sentinel Integration
- Effortless Setup at No Additional Cost: The Microsoft Codeless Connector Framework allows you to send your logs directly into Microsoft Sentinel without the complexities of custom configurations or expensive middle layers. You’ll save both time and money by skipping Cloud Exchange, making this integration a cost-efficient choice for businesses. Please note that while using the codeless connector incurs no extra cost, you’ll still need to manage data storage costs within the Azure environment.
- Comprehensive Data Insights in Microsoft Sentinel: Netskope’s integration ensures all CASB alerts, DLP incidents, and threat intelligence are piped directly into Microsoft Sentinel. This gives you full visibility into potential risks and incidents, all within the Azure console, where your SOC team already operates. Having everything in one place makes it easier to manage incidents and launch threat-hunting initiatives without needing to switch platforms.
- Enabling Your SOC with Scalable Log Shipping:The integration offers a scalable approach to log shipping, supporting businesses of any size as they grow. Security teams can now quickly send large volumes of Netskope data to Microsoft Sentinel without infrastructure bottlenecks or manual overhead. The Codeless Connector allows for one-click integration, meaning your logs are ready to go with minimal setup, while being easily digestible for SOC analysts to act on.
- Focus on Incident Response and Policy Changes, Not Infrastructure: With this integration, security teams can focus on what really matters—incident response and policy enforcement—without getting bogged down by infrastructure concerns. All your Netskope alerts and logs will be accessible within Microsoft Sentinel, allowing your SOC team to quickly investigate and respond to incidents. The integration also helps streamline threat-hunting operations, reducing the need to log into multiple systems unless necessary for specific policy adjustments.
How Indexing on Netskope Rest API works
For a detailed overview on how iterator endpoints work on the Netskope platform please refer to: https://docs.netskope.com/en/using-the-rest-api-v2-dataexport-iterator-endpoints/
In Netskope's REST API v2 Data Export Iterator endpoints, the index is a unique string identifier used to manage and track data retrieval. Netskope uses this index to remember the position of previously fetched logs, enabling continuity between data requests. Consumers reuse the same index to sequentially retrieve subsequent data pages. Each consumer must use a distinct index; multiple consumers sharing an index can cause missed logs. For instance, using demo as an index to pull logs 1–1000 ensures the next request retrieves logs 1001–2000. Unique indexes ensure consistent data retrieval without overlap or data loss between different consumers.
Why this matters: This means in order to have the Codeless Connector Platform pull Netskope logs from a desired timestamp (ex: right now, 3 months ago etc) we need to get the index to the correct timestamp. The easiest way to accomplish this is to run a powershell script I have linked right below here:
You just have to fill out the following parameters and paste it in your azure portals cloud shell:
$OrganisationURL = 'alliances.goskope.com'$Index = 'testindex'$Timestamp = 'In Epoch'$ApiToken = ''
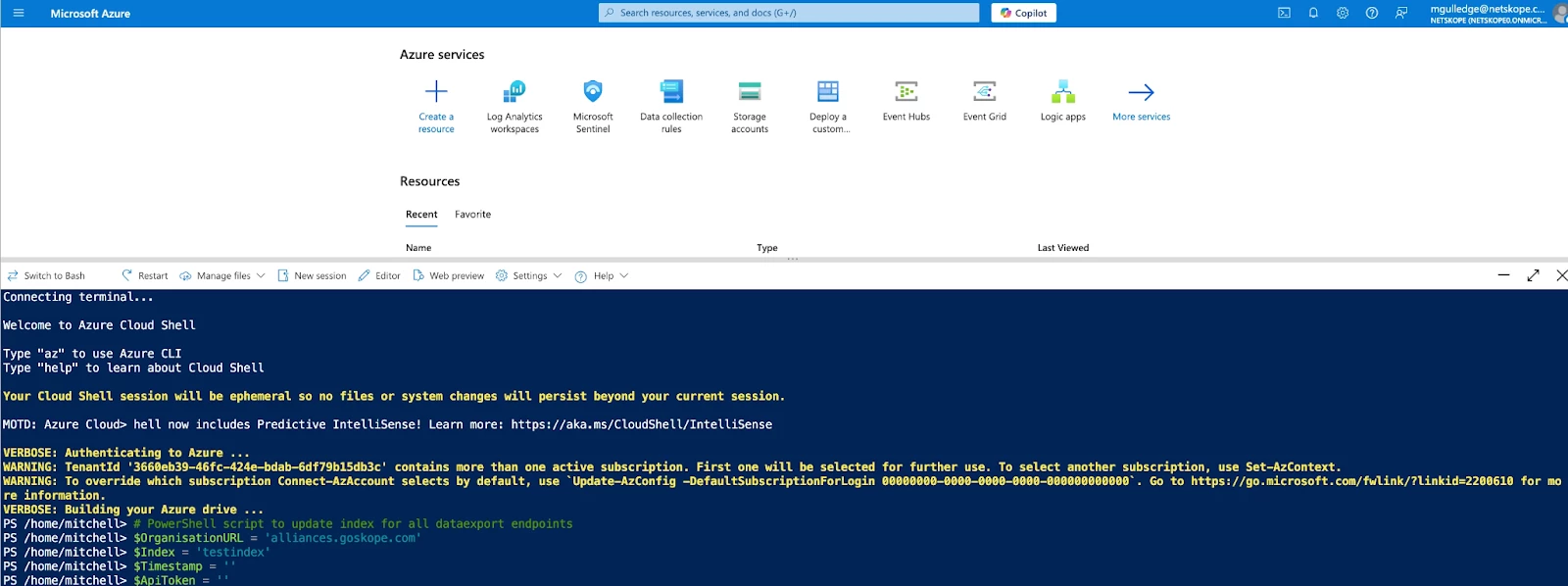
Now that you have the index at the desired starting point you can follow the steps below to deploy the CCF connector in your Azure tenant.
How to Create Netskope RBACv3 Token
These steps are performed in the administration interface of your Netskope SSE instance. For more detailed info, see the Netskope documentation.
- In the Netskope console, go to Settings > Administration > Administrators & Roles
- Go to Roles
- Add the below Function scope while creating the Role
- Infrastructure
- Infrastructure Log: View
- Skope IT
- Alerts: View
- Application Events: View
- Endpoint Events: View
- Network Events: View
- Page Events: View
- Administration
- Audit Log: View
- DLP
- Incidents: View
- Infrastructure
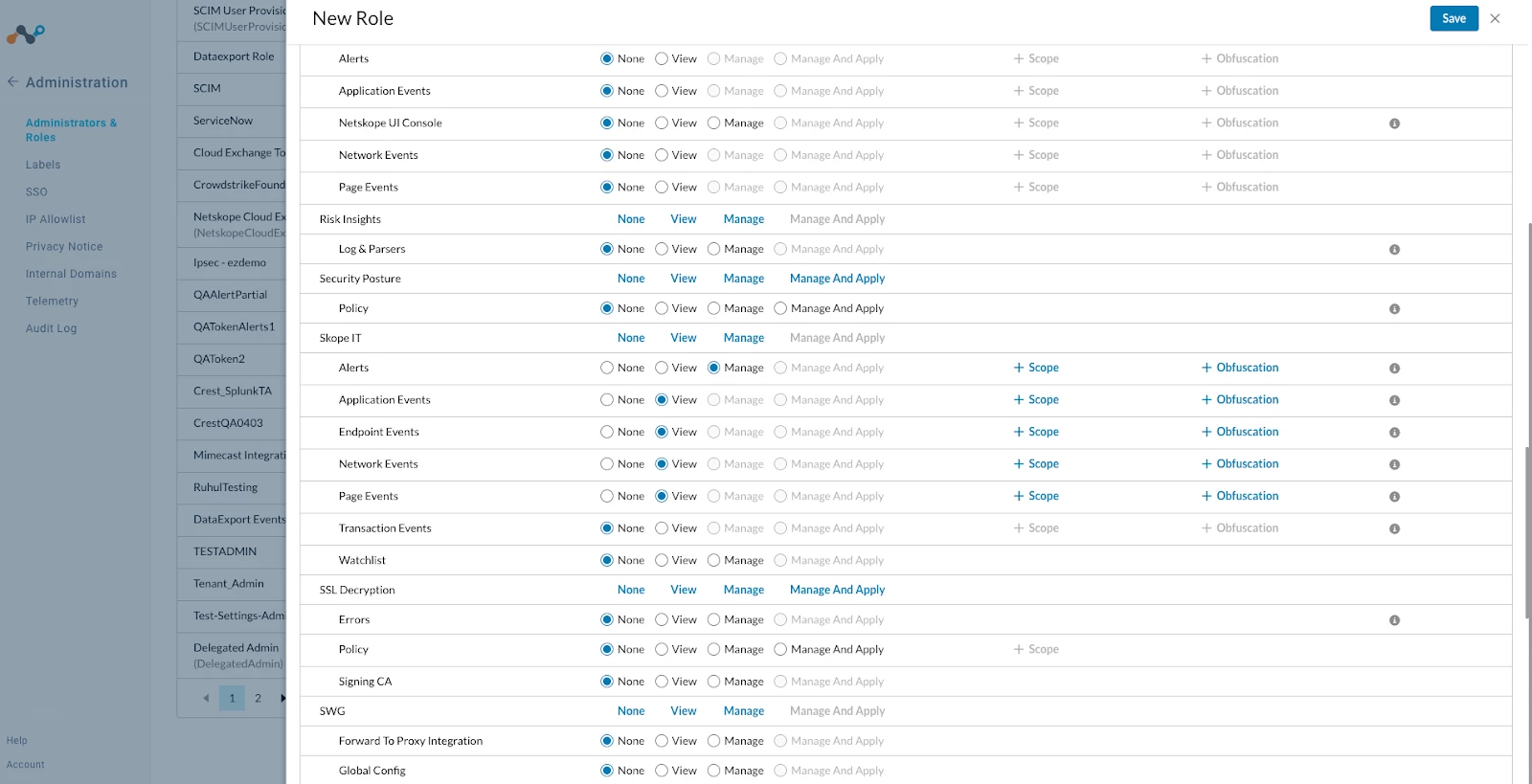
- Click Save.
- Click on Administrators and click on Service Account
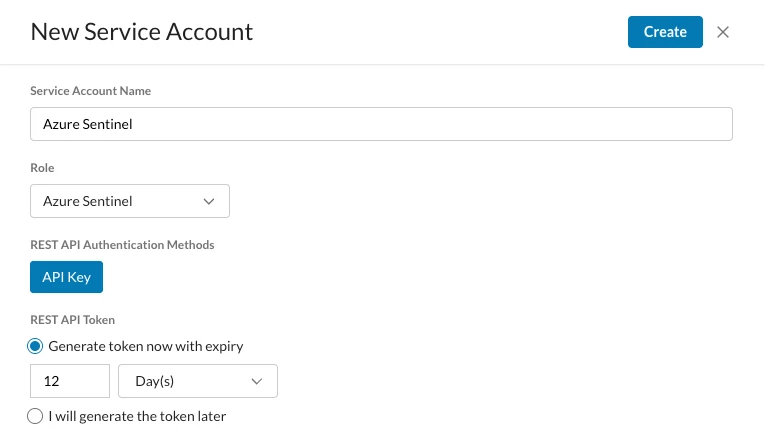
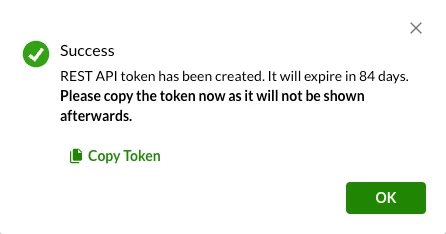
- Copy this token to be used later in the Netskope Data Connector tile.
How It Works: A Seamless Process for Log Management
Netskope’s native integration allows for rapid log shipping without any additional deployment overhead. Here’s how you can enable the integration today:
- Navigate to the Content Hub of your Microsoft Sentinel Workspace. Select Netskope Data Connector:
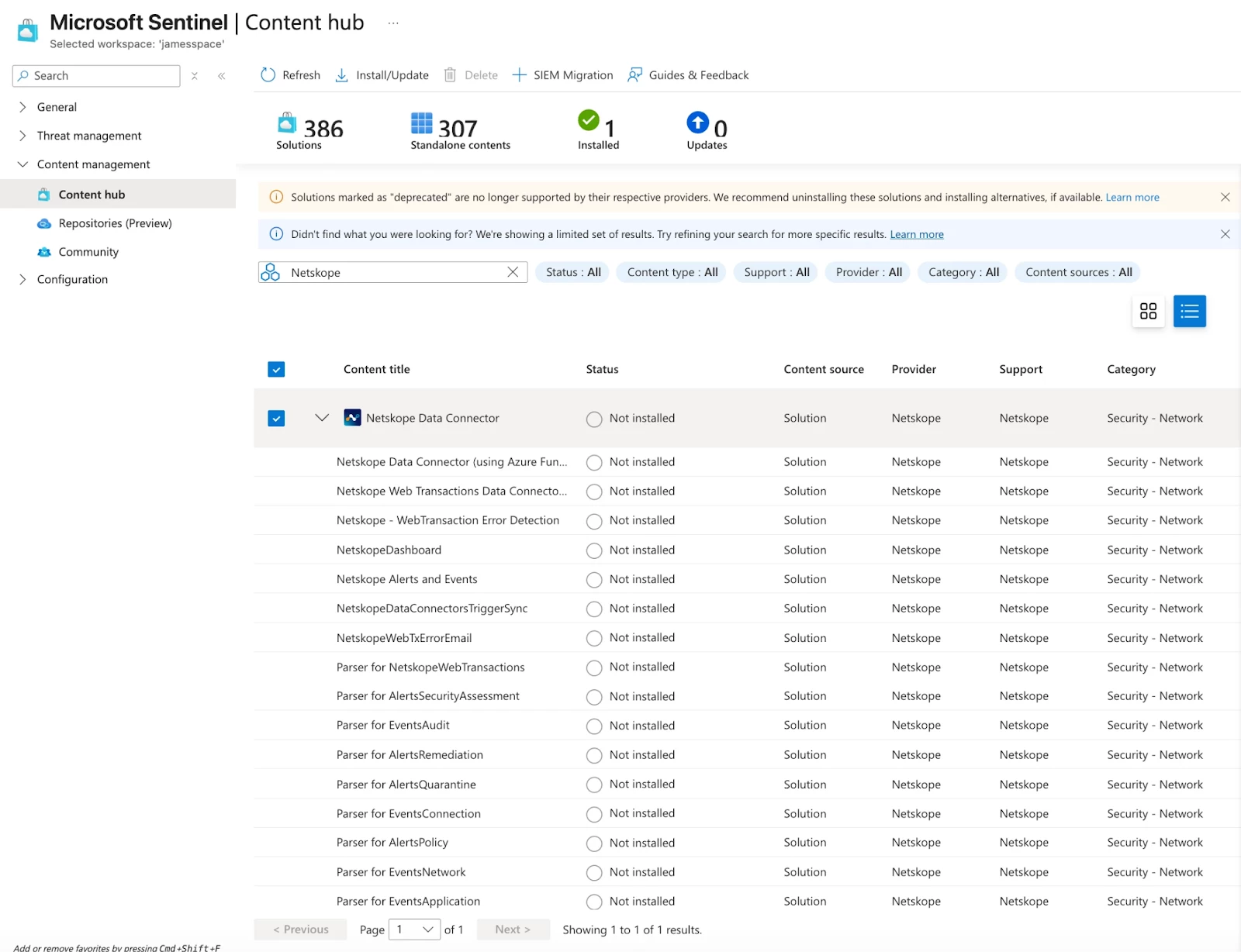
- Select Install:
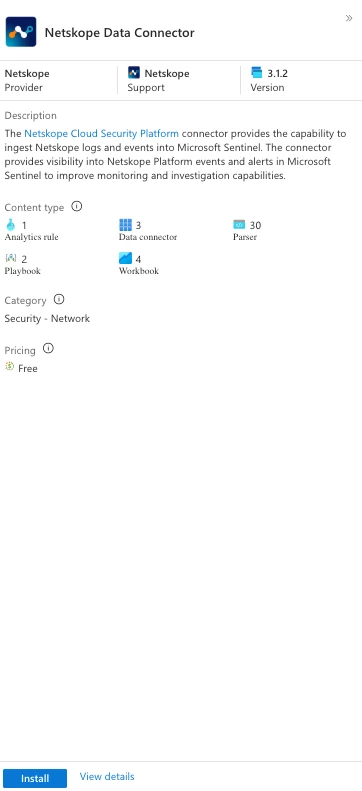
3. After clicking review and create you will need to navigate to your sentinel instance under Data Connectors where you will see Netskope Alerts and Events and we would need to configure the same.
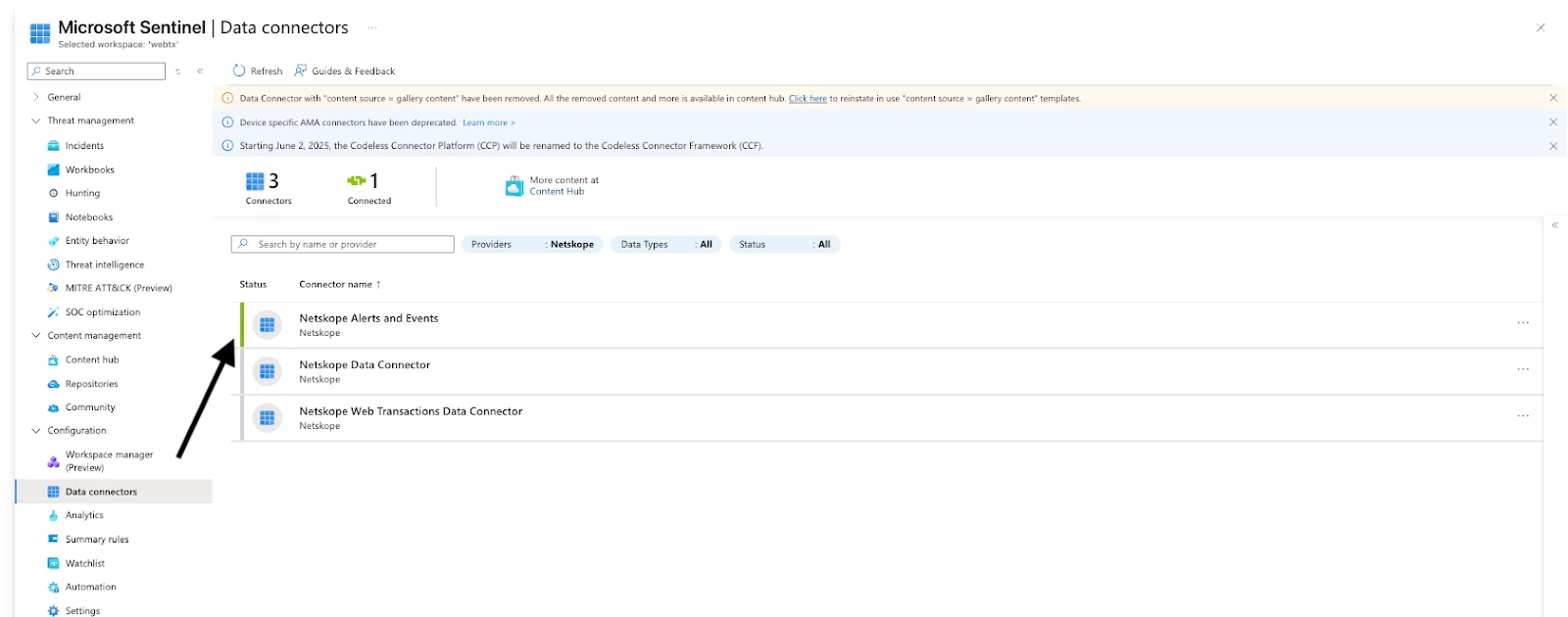
4. Select Open connector page and you will need to fill out your organization url (if you have ex: alliances.goskope.com your org name is alliances) and API key. Additionally with the version 3.1.2 you can also select/deselect the different endpoint for which you want the data to be ingested. Also if the value is empty with no value as yes or no it will take yes by default.
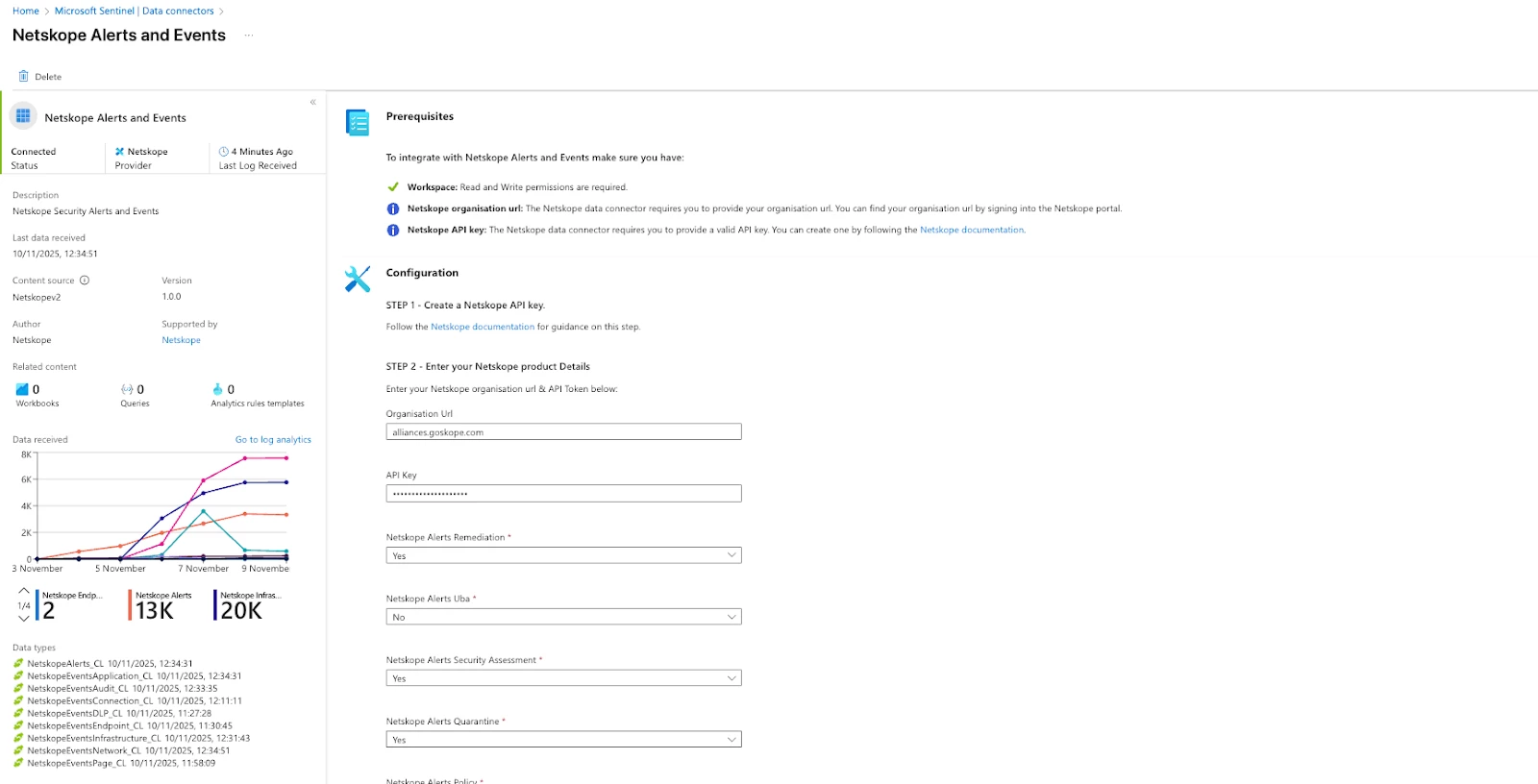
5. Click connect and data should start flowing within 20-30 min
Included Endpoints:
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/page?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/endpoint?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/network?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/infrastructure?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/connection?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/audit?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/application?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/remediation?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/uba?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/securityassessment?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/quarantine?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/policy?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/malware?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/malsite?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/dlp?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/ctep?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/watchlist?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/compromisedcredential?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/content?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/alerts/device?operation=next&index=codeless
https://<insert-tenant-name-here>.goskope.com/api/v2/events/dataexport/events/incident?operation=next&index=codeless
Take Control of Your Security with This Simplified Integration
By leveraging Netskope’s native integration with Microsoft Sentinel, you’ll empower your SOC team with a simple, scalable, and cost-efficient way to gain full visibility over your data. The Codeless Connector Framework removes the friction associated with setting up log shipping pipelines, giving you more time to focus on threat hunting and incident management.
Ready to streamline your security operations? Activate the integration today and unlock the power of Netskope data within Microsoft Sentinel.
Unlock Visibility: Using the Netskope Dashboard to Find Threats Fast
With the Netskope — Azure Sentinel Data Connector, a ready-made Netskope Dashboard is added to your Sentinel workspace, giving you a single pane of glass to explore everything from Events to Alerts and DLP incidents.
Follow the steps below to open the Netskope Dashboard and start investigating activity across users, apps, and data.
- Go to Threat Management > Workbooks > Select the NetskopeCCPDashboard
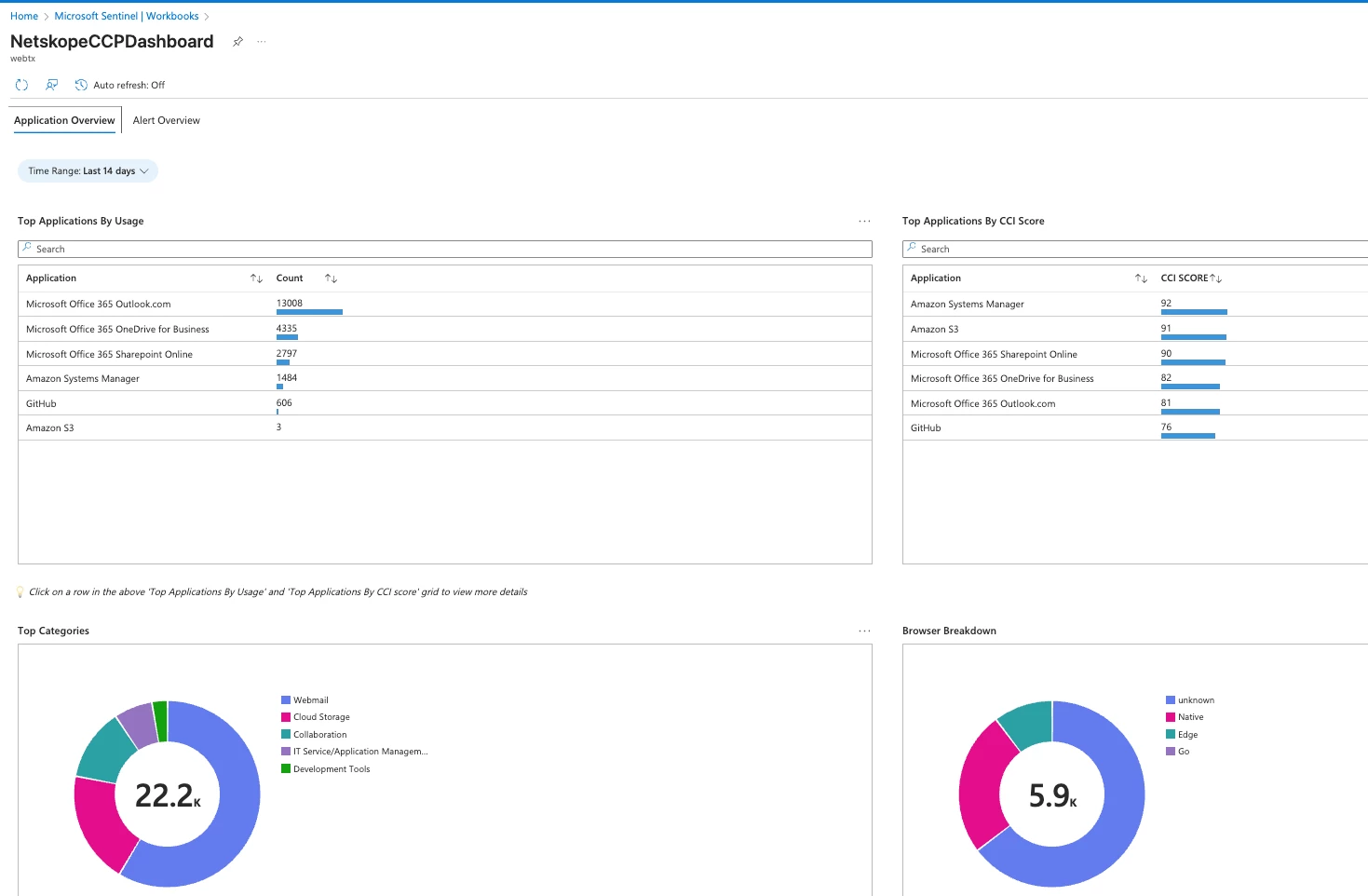
- Application Overview
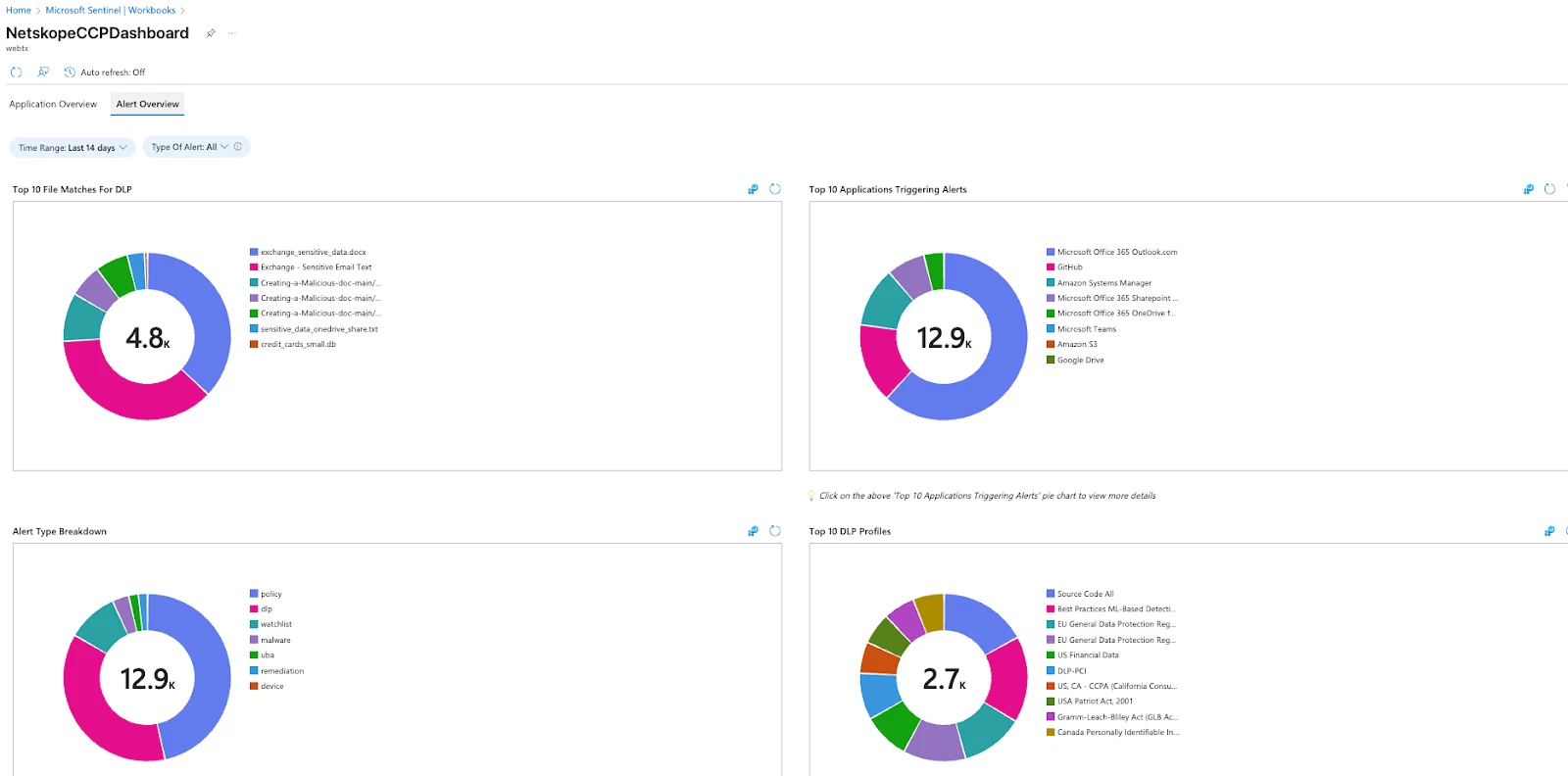
- Alerts Overview
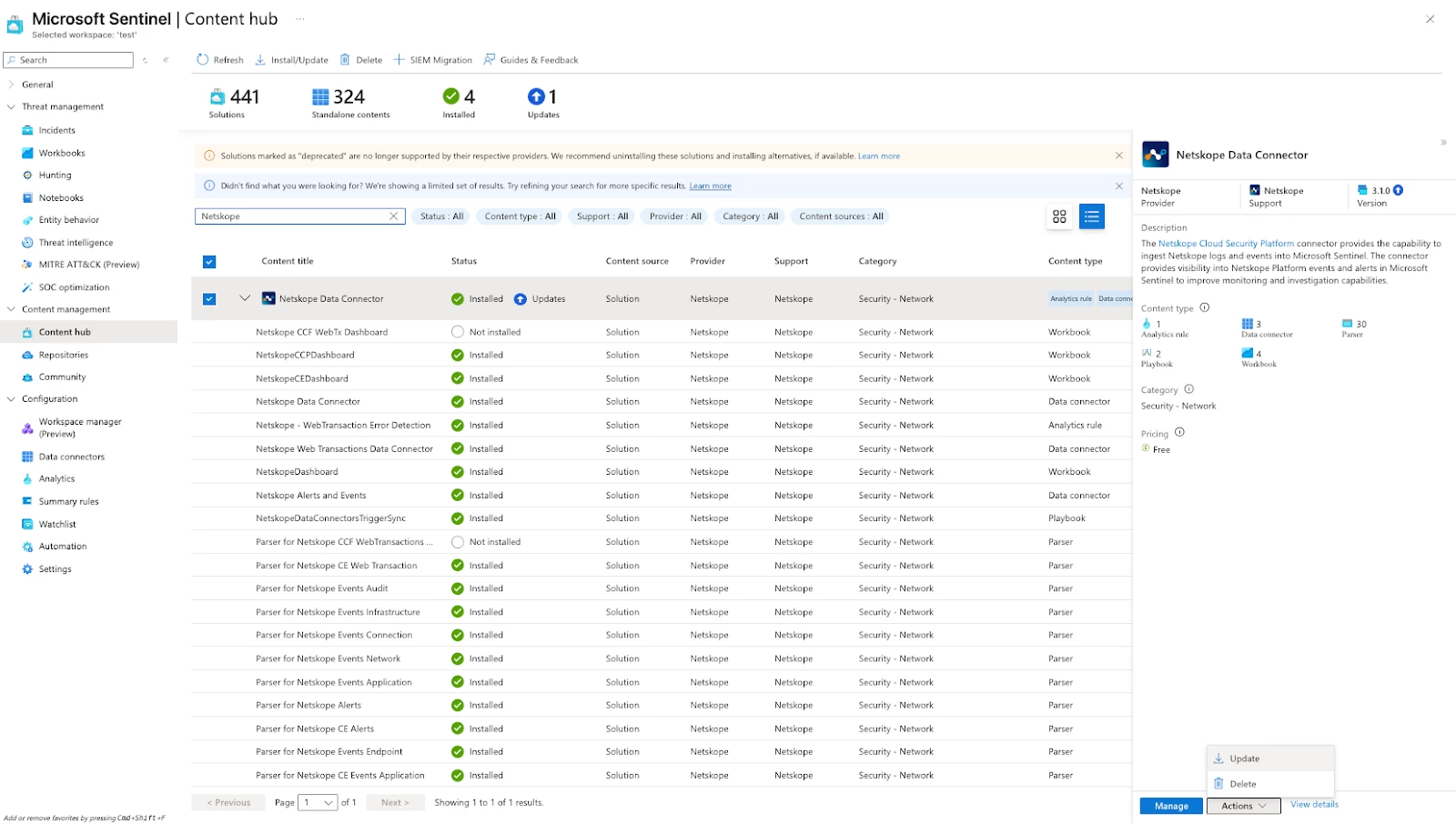
Migrating to the Azure Sentinel — Netskope Data Connector (v3.1.2)
Locate to the content hub and update the Netskope Data connector
Additionally make sure to test out the same in Dev environment first before implementing directly into the production.
FAQs
Q: What does this integration cost?
A: The integration leverages Microsoft’s Codeless Connector Frameworl, which incurs no additional setup cost. However, organizations will need to account for Azure storage costs for the data ingested into Sentinel.
Q: Do I need to deploy Netskope Cloud Exchange?
A: No, the native integration with the Codeless Connector removes the need to deploy Cloud Exchange, saving both time and money.
Q: What types of data can I send to Microsoft Sentinel?
A: You can send all CASB alerts, DLP incidents, threat logs and Netskope Events directly to Sentinel, where they can be easily analyzed and used for incident response.
By integrating Netskope’s powerful security data into Microsoft Sentinel, you’ll give your team the tools they need to protect your organization—efficiently and effectively.
Shoutouts
Also this was made possible by Tim Groothuis at Masero who authored the ARM template and has his own Medium talking about the integration: https://medium.com/@TimGroothuis/announcing-the-netskope-ccp-connector-9470afa8eab3








