Web shells are commonly used by threat actors as part of the command and control phase of a cyberattack. These shells can be custom code and used by common C2 frameworks such as Cobalt Strike or be generated as a default payload in exploitation frameworks such as Metasploit. With this comes a challenge to security professionals on how to detect, mitigate, and hunt these shells that may be generated by an adversary during an attack. Netskope’s Advanced Analytics can be used in combination with Netskopes Cloud Firewall to create a dashboard that provides insight into where potential shell traffic is occurring within an organization's environment.
Uploaded with this community post is a Netskope Advance Analytics Dashboard that provides broad insight into where these potential shells may be occurring within an organization's environment.
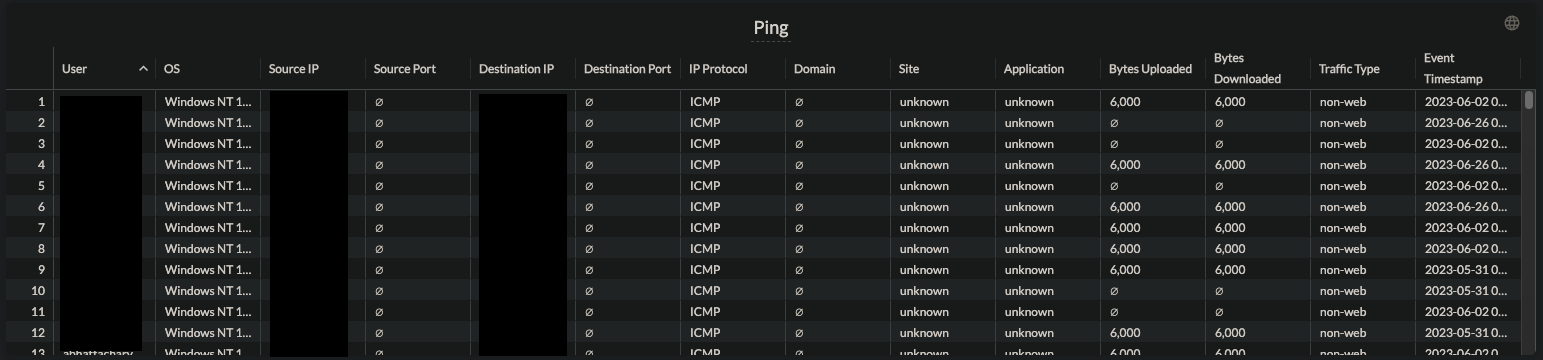
The first Widget in the dashboard is the Ping dashboard. This shows ping traffic within the organization's environment. Depending on environmental variables this may or may not be expected behavior but ping traffic followed by suspected shell traffic could be an indicator of attack.
The second widget is where the suspected shells are displayed. Traffic resembling what is shown in the widget may warrant additional investigation as it shows traffic that resembles what shell traffic looks like.
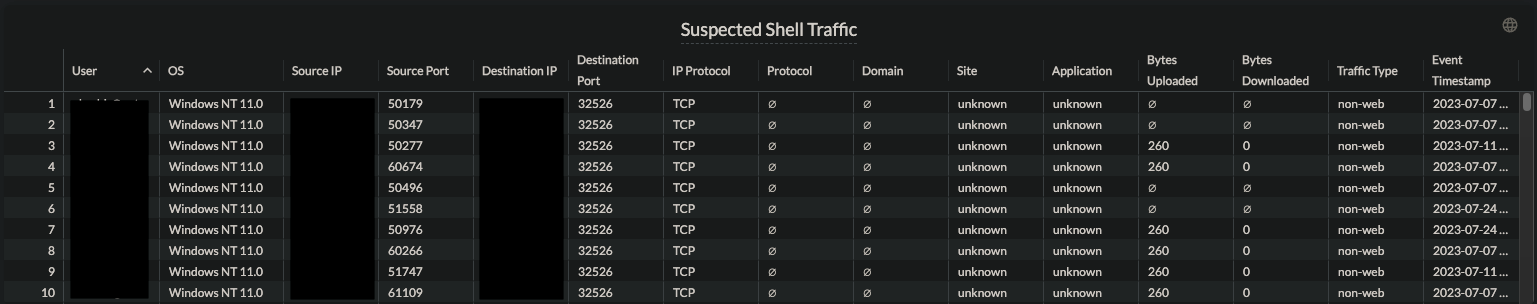
Please Note: Once the dashboard is imported into Advanced Analytics some tuning may need to be done based on the organization's environment and what is considered expected and unexpected behavior by users. Another important factor of this dashboard is by default a condition is that the domain field is null. If an adversary was to use a domain as part of their call back this may not be true so it is worth removing the domain is null condition fro, the dashboard to explore other potential suspected traffic. However this could be excessively noisy and other tuning may be needed on other fields based on what the dashboard is showing.







