Hello,
I have a file containing records in this format:
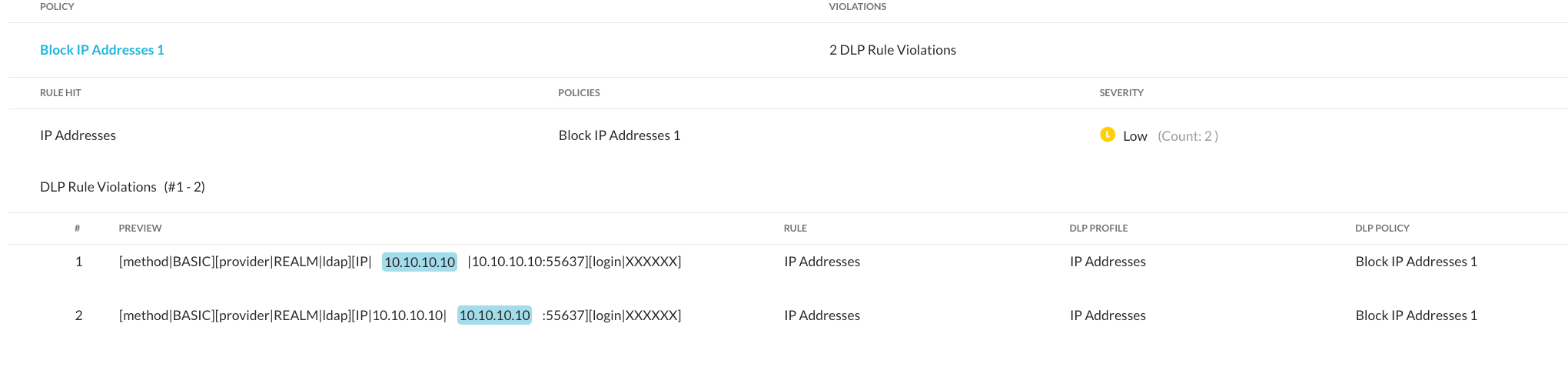
2022.03.18 11:46:45 DEBUG web[XXXXXXXX][auth.event] login success [method|BASIC][provider|REALM|ldap][IP|10.10.10.10|10.10.10.10:55637][login|XXXXXX]
I used this regular expression to detect private IP addresses:
(10\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3})|(172\.1[6-9]{1}[0-9]{0,1}\.[0-9]{1,3}\.[0-9]{1,3})|(172\.2[0-9]{1}[0-9]{0,1}\.[0-9]{1,3}\.[0-9]{1,3})|(172\.3[0-1]{1}[0-9]{0,1}\.[0-9]{1,3}\.[0-9]{1,3})|(192\.168\.[0-9]{1,3}\.[0-9]{1,3})
Using this regular expression, I can't detect any IP addresses in the file sent through netskope. What can I do and where is the problem?
Solved
DLP - Detect IP addresses in a log file
Best answer by sshiflett
Hello
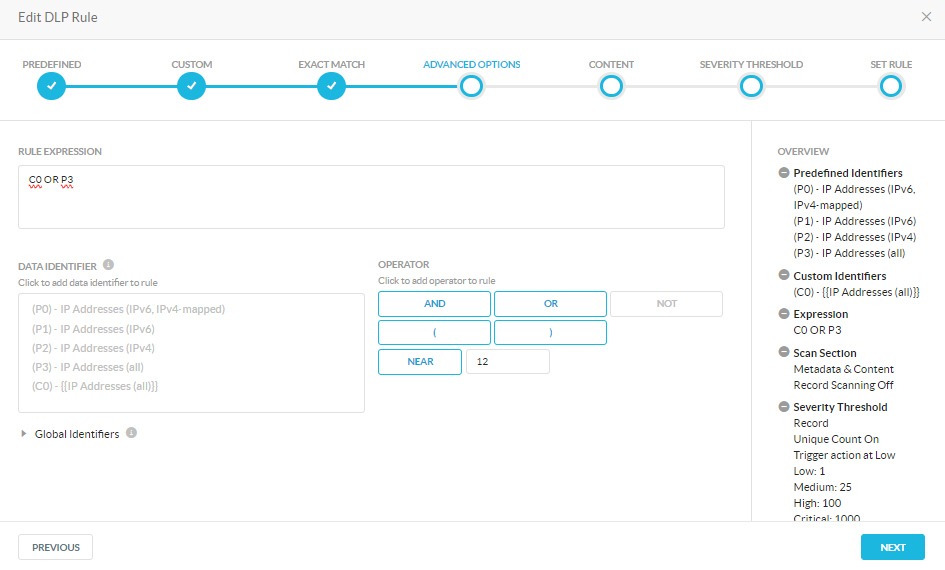
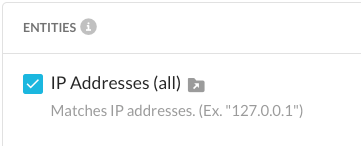
I grabbed your snippet and was able to trigger using the predefined identifier for IP addresses:
Without getting into the weeds, it’s almost always better to use predefined identifiers instead of regexes when possible due to how the Netskope engine handles word boundaries. My rule just leverages the predefined identifier.
Additionally, searching for just an IP address is likely to create a lot of noise and false positives so I would suggest adding additional identifiers or thresholds to ensure you’re capturing just the log files and data you’re looking for.
This topic has been closed for replies.
Sign up
Already have an account? Login
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Login to the community
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.