
Netskope Global Technical Success (GTS)
Grok xAI - Block Activity 'Upload'
Netskope Cloud Version - 129
Objective
The objective is to restrict upload activity on Grok xAI
Prerequisite
Netskope SWG or Next-Gen SWG license is required
Context
The customer aims to restrict their end-users from uploading files on xAI. This knowledge base article explains how to achieve this use case via Netskope Realtime Policies
Do You Know?
- As of Aug 26, 2025, Netskope recognizes Grok xAI as a Cloud Application, but no pre-defined cloud app connector is available.
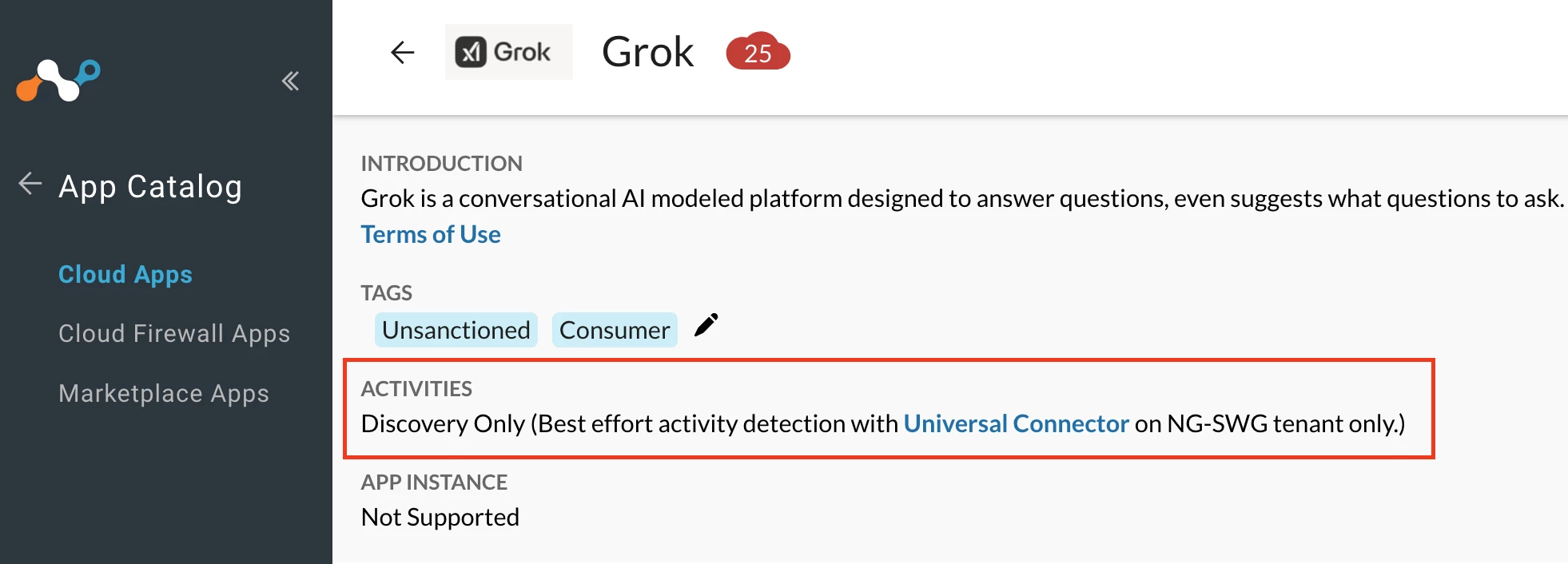
- Netskope Product Management is currently working on a product enhancement request that addresses the need for a predefined cloud app connector for Grok AI. At this time, there are no confirmed release timelines.
- In the interim, customers can utilize custom URL/Web category to restrict ‘Upload’ activity.
- To create a Custom URL/Web category, it is essential to understand the behavior and traffic patterns of Grok AI. The following details outline the observed interactions and activities performed by the application -
i. End-users must be logged in to Grok AI before they can upload a file.
ii When initiating an interaction with Grok AI (specifically a file upload), the traffic is first redirected to https://grok.com/rest/app-chat/upload-file
iii. This initial interaction is labeled as ‘Upload-file’.
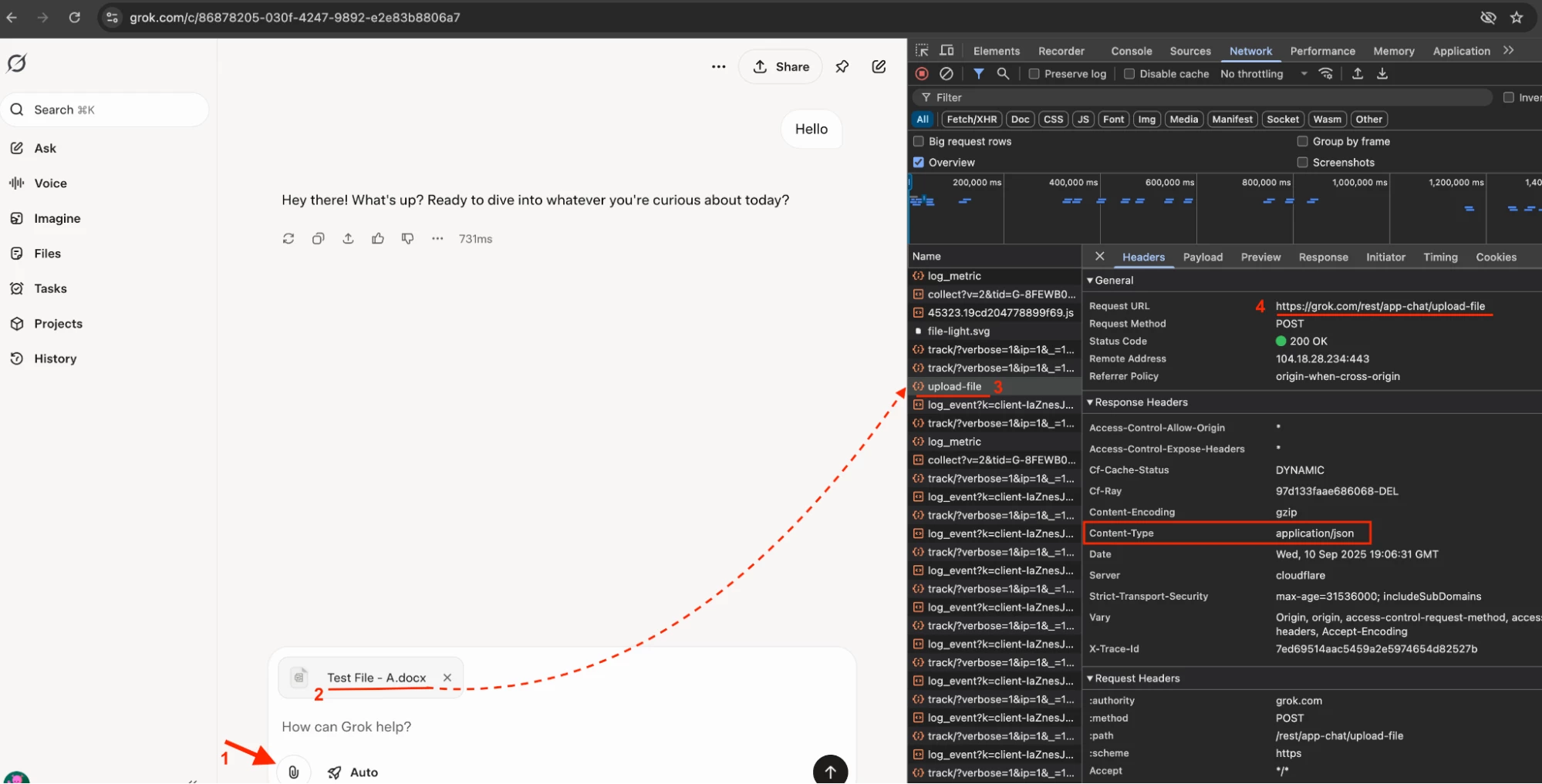
iv. The Content-Type is set to application/json, which indicates that the backend requires the data in JSON format.
v. Binary data (like a .docx, .jpg, .pdf) can’t be directly represented in JSON. So, if the backend requires JSON, the file’s binary data is usually Base64-encoded before being placed in the JSON.
vi. In the below image ‘content:UEsDBBQACAgIAORmJ1sAAAAAAAAAAAAAAAA’ represents the encoded Base64. However the file name is in plain text format
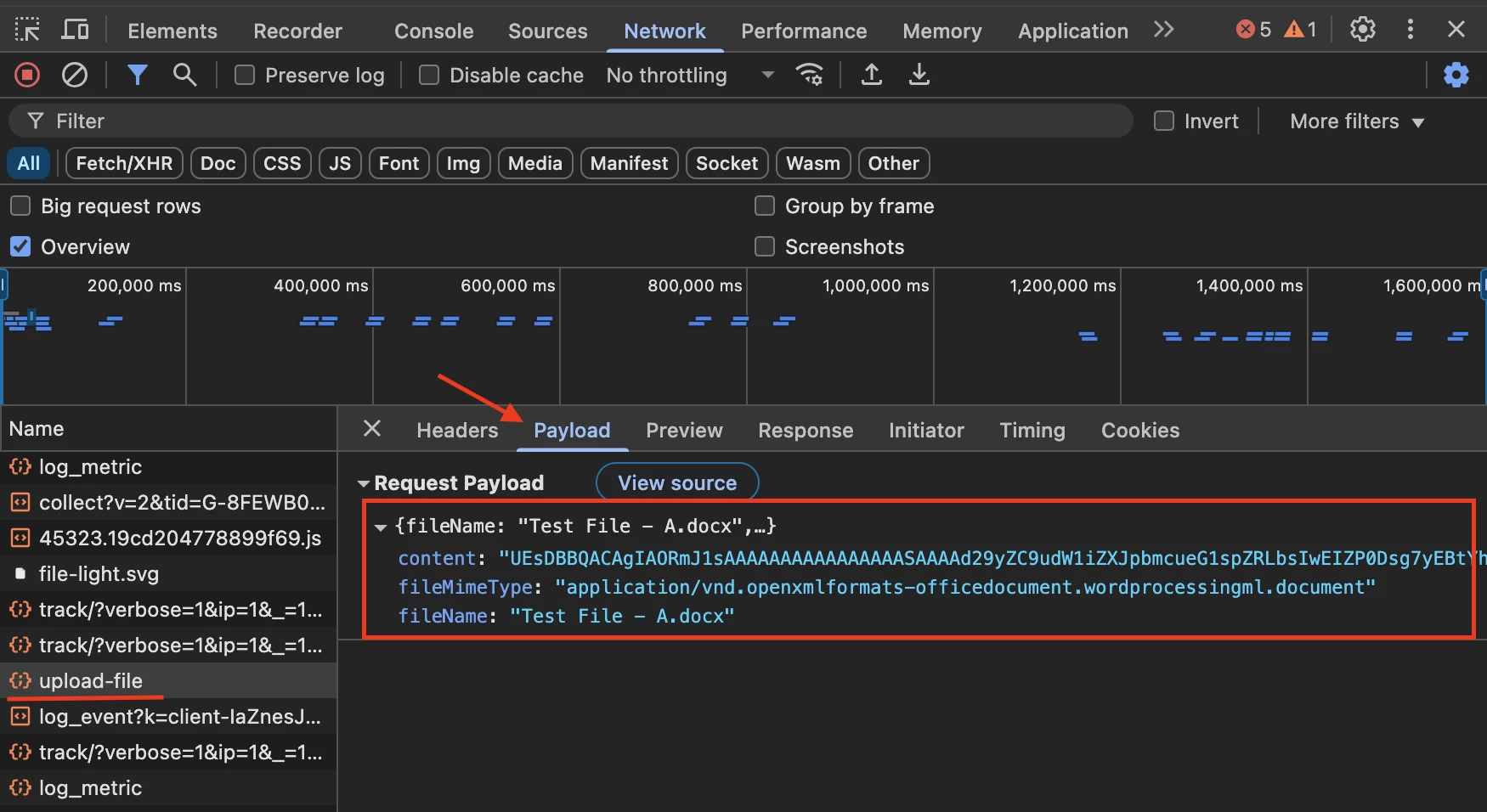
| Upload Conversation | |
| URL Upload-file | |
Author Notes
- Based on the above information, it is clear that the file content cannot be read in the browser. As a result, DLP controls cannot be applied to the Upload activity.
- Customers, however, can choose to block the Upload activity entirely.
- On the other hand, chat conversations are in plain text, which means DLP controls can be applied. For further details, kindly review -
Configuration
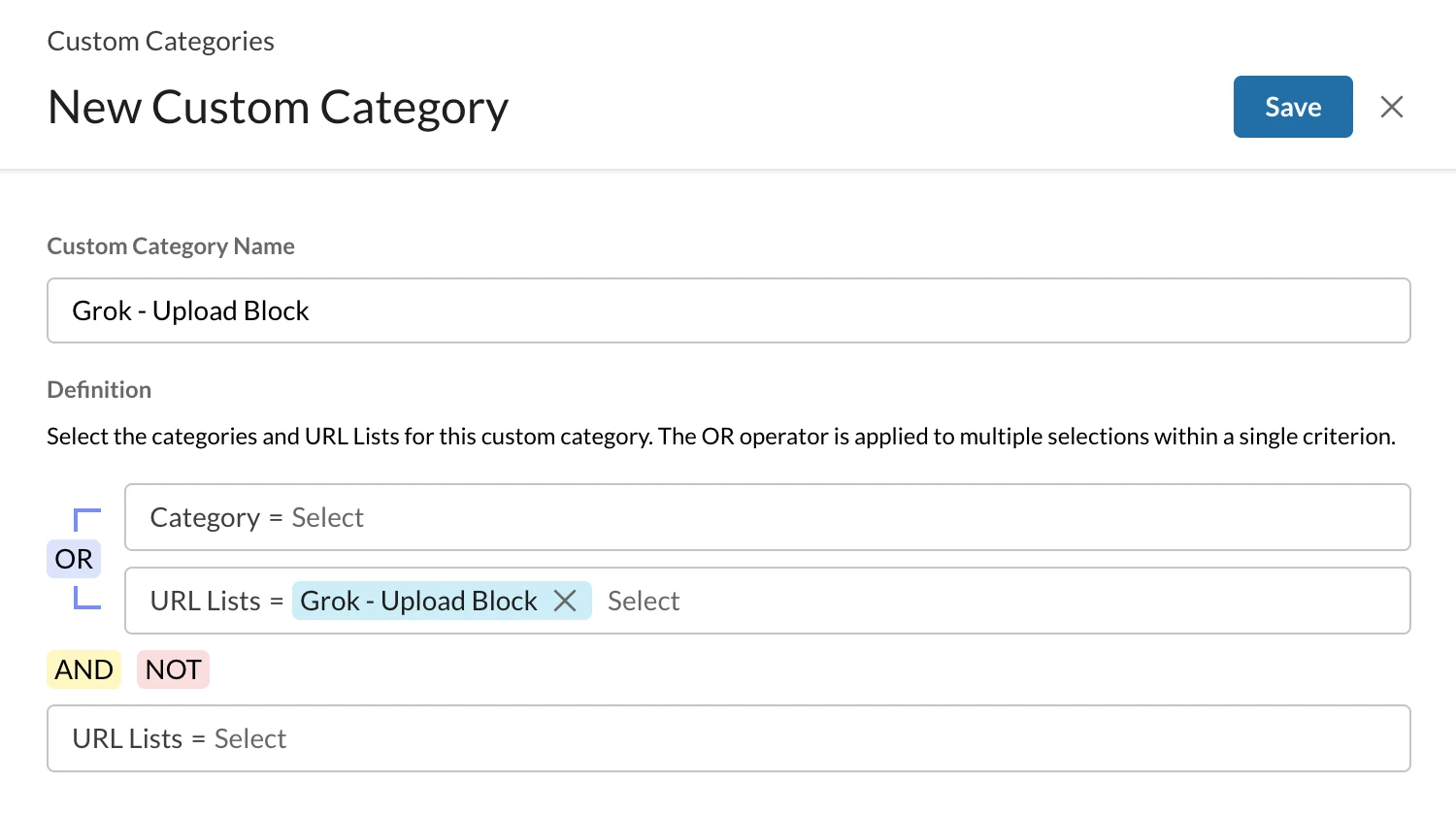
Step 1 - Create a custom URL/Web category
Path: Netskope Tenant UI >>> Policies >>> Profile - - - URL Lists
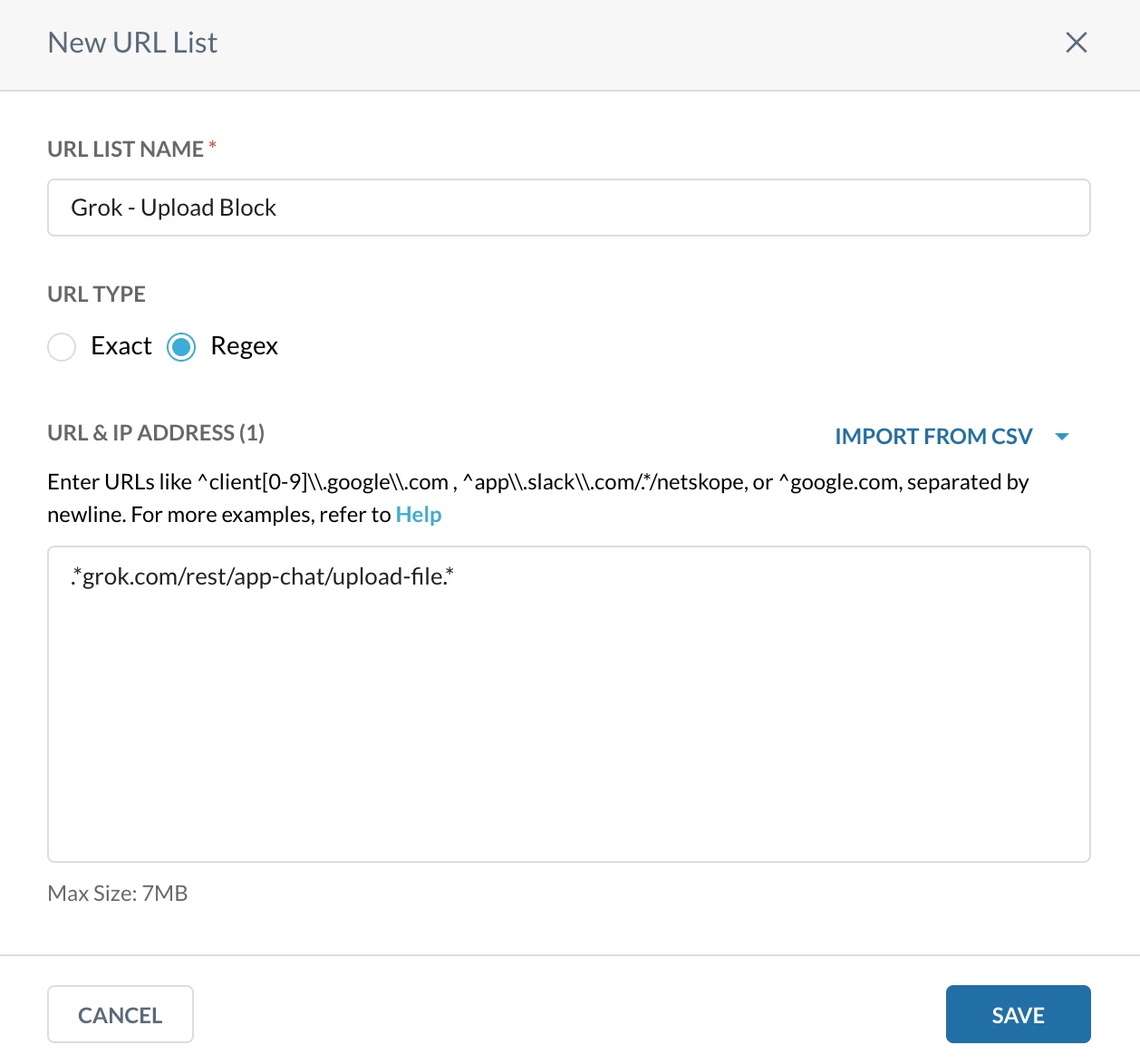
Path: Netskope Tenant UI >>> Policies >>> Profile - - - Custom Categories
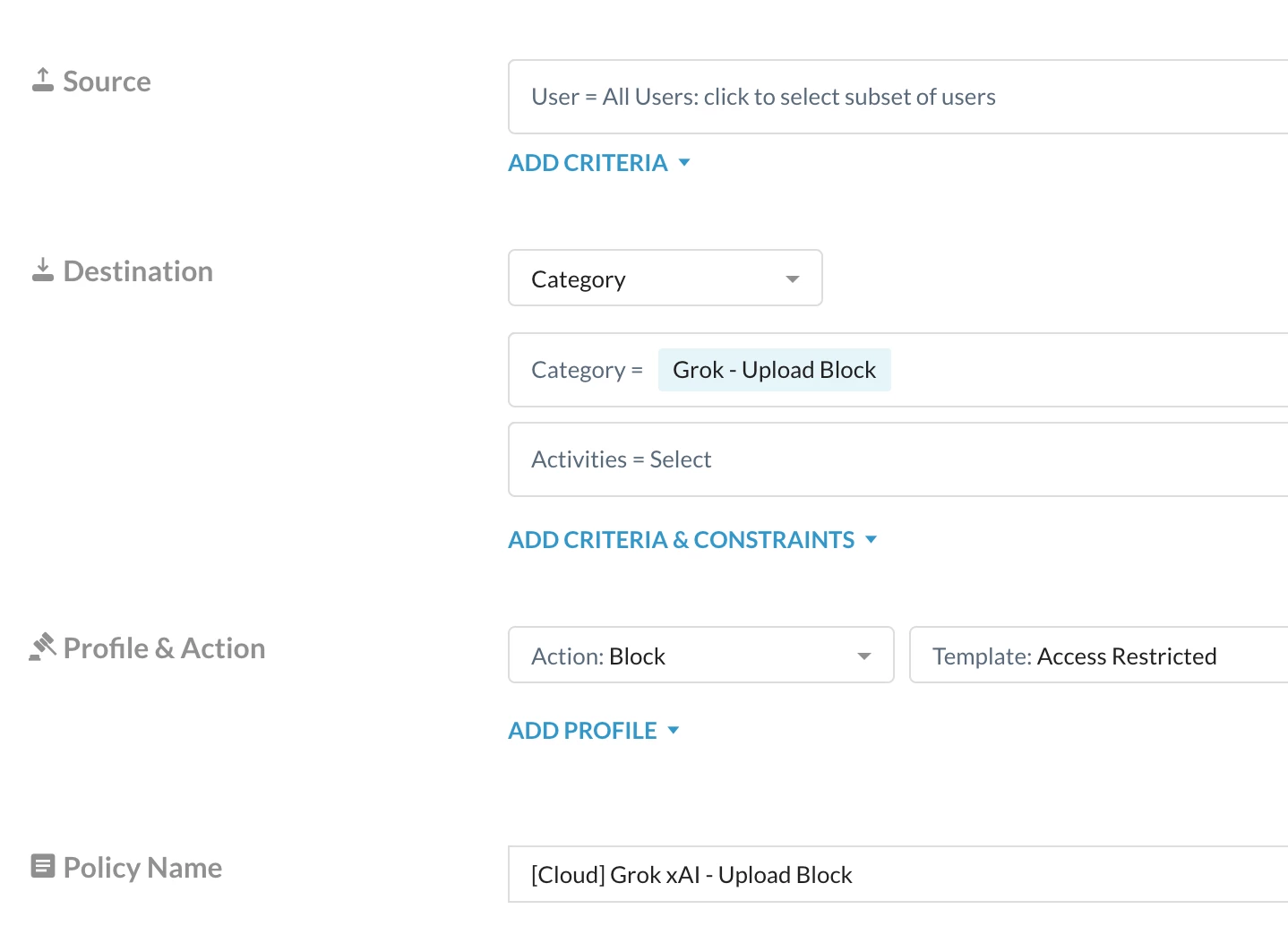
Step 2: Realtime protection policy
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy
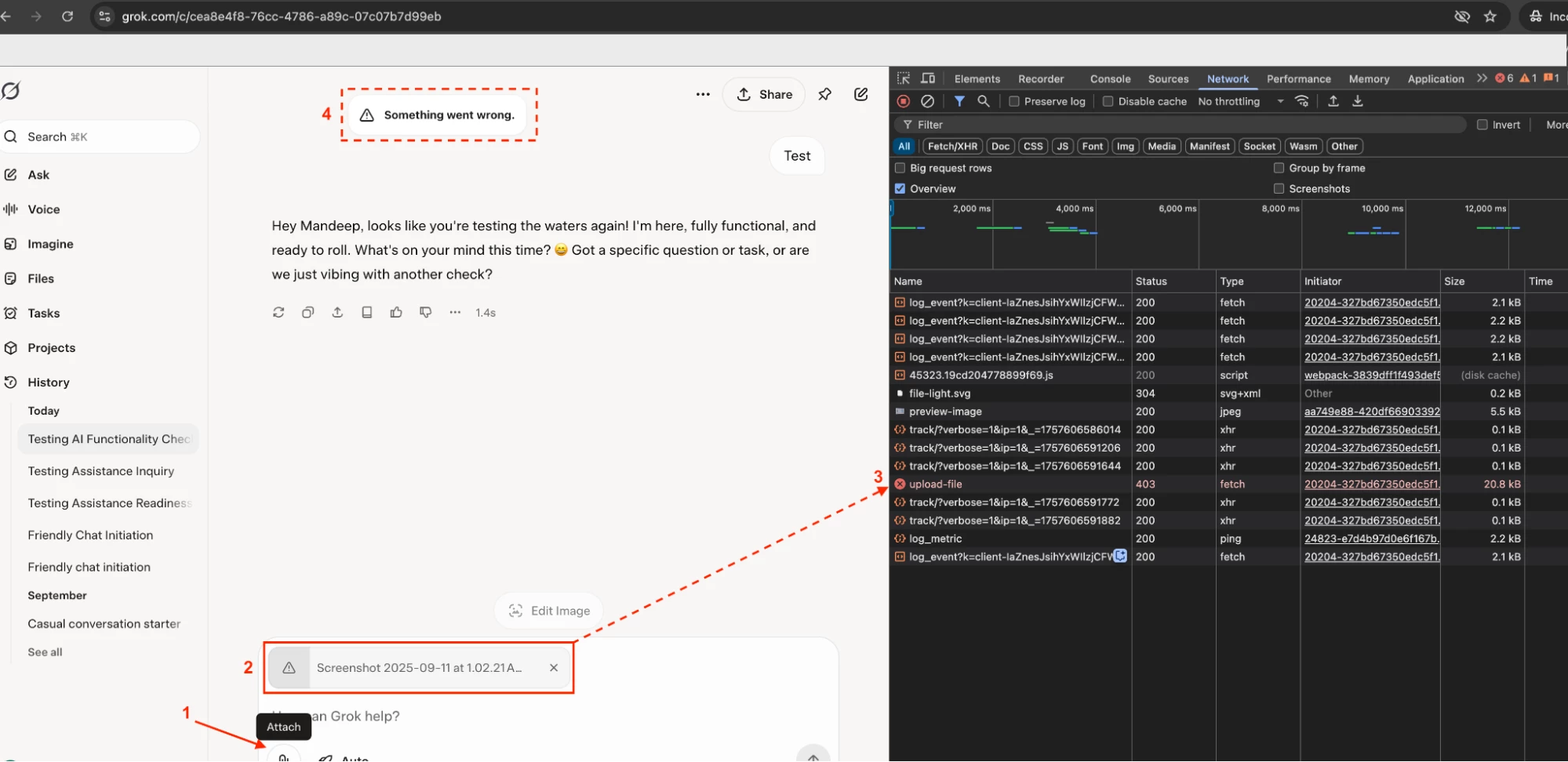
Verification
- Access Grok xAI - Link
- Upload a file
Author Notes
- This document will be revised once Netskope introduces a pre-defined cloud app connector for Grok xAI.
- With the pre-defined cloud app connector, there is no longer a need to create a custom category for Grok xAI.
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.






