
Netskope Global Technical Success (GTS)
Workaround - Microsoft 365 Copilot (Corporate) - Allow Only Corporate Instance
Netskope Cloud Version - 130
Objective
This article aims to assist with a workaround to achieve the use case of allowing only Corporate Instance of Microsoft 365 Copilot until the release of ‘Websocket for Non-DLP Activities’ feature. Please refer the Author Notes & Workaround section of the article
Prerequisite
Netskope Next-Gen SWG license is required
Context
Microsoft suite customers want their end-user to access Microsoft Copilot but only their instance. All other Microsoft Copilot instances should be blocked.
Do You Know?
Microsoft Copilot is available for Personal and Corporate. Netskope has 2 predefined cloud app connectors for Microsoft Copilot.
- Microsoft Copilot for Personal Instances
- Microsoft 365 Copilot for Corporate Instances.
Author Notes
- Microsoft is integrating Copilot capabilities at the operating system level, within Office apps, the Edge browser, and many other applications. This article focuses specifically on browser-based traffic directed to Microsoft 365 Copilot, and highlights the types of traffic where SSL decryption is possible.
- It is recommended to review the foundation parent article first.
| Parent Article |
- Since this article is about Microsoft 365 Copilot, a few details need to be better understood.
- Microsoft 365 Copilot cloud app connector
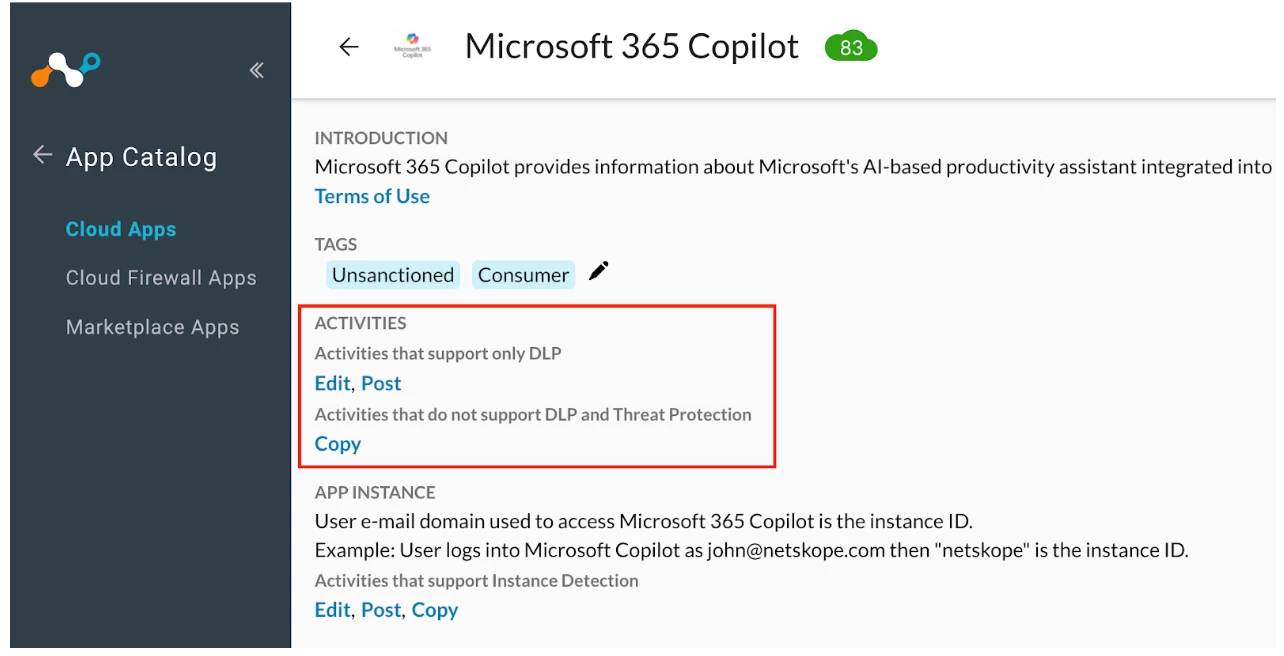
- With the current Microsoft 365 Copilot cloud app connector, the ‘Post’ activity is supported only for DLP (Data Loss Prevention) use cases. It will not be detected in non-DLP scenarios.
- To enable detection of non-DLP ‘Post’ activities in Microsoft 365 Copilot, the ‘WebSocket for Non-DLP Activities’ feature flag must be enabled for each individual tenant.
- Kindly note: The current ETA for the availability of the above-mentioned feature for the customer is R131 i.e. October’2025.
- If the feature is business-critical and can't wait for release, please see the 'Workaround' section of this article for a temporary solution
Note - Post the release of R131, Raise a support case with Case Type - How-to-Question with Netskope GTS to enable ‘WebSocket for Non-DLP Activities’ feature flag.
Configuration
To implement this use case, Four distinct policy sets are required:
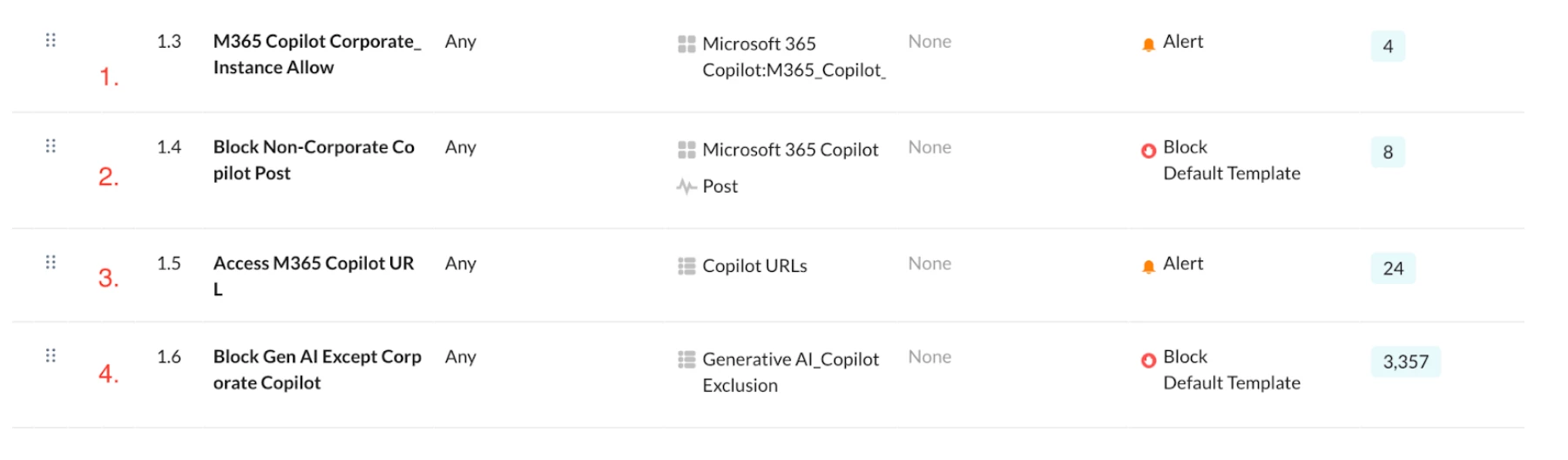
Given that Netskope enforces policies in a top-down order, the policies should be configured in the following sequence:
- Policy 1: Allow or monitor activity specific to the corporate instance of Microsoft Accounts.
- Policy 2: Block Post activity on Non-Corporate Instance of Microsoft 365 Copilot.
- Policy 3: Allow user traffic going to Microsoft 365 Copilot URLs, based on specific HTTP referrer headers.
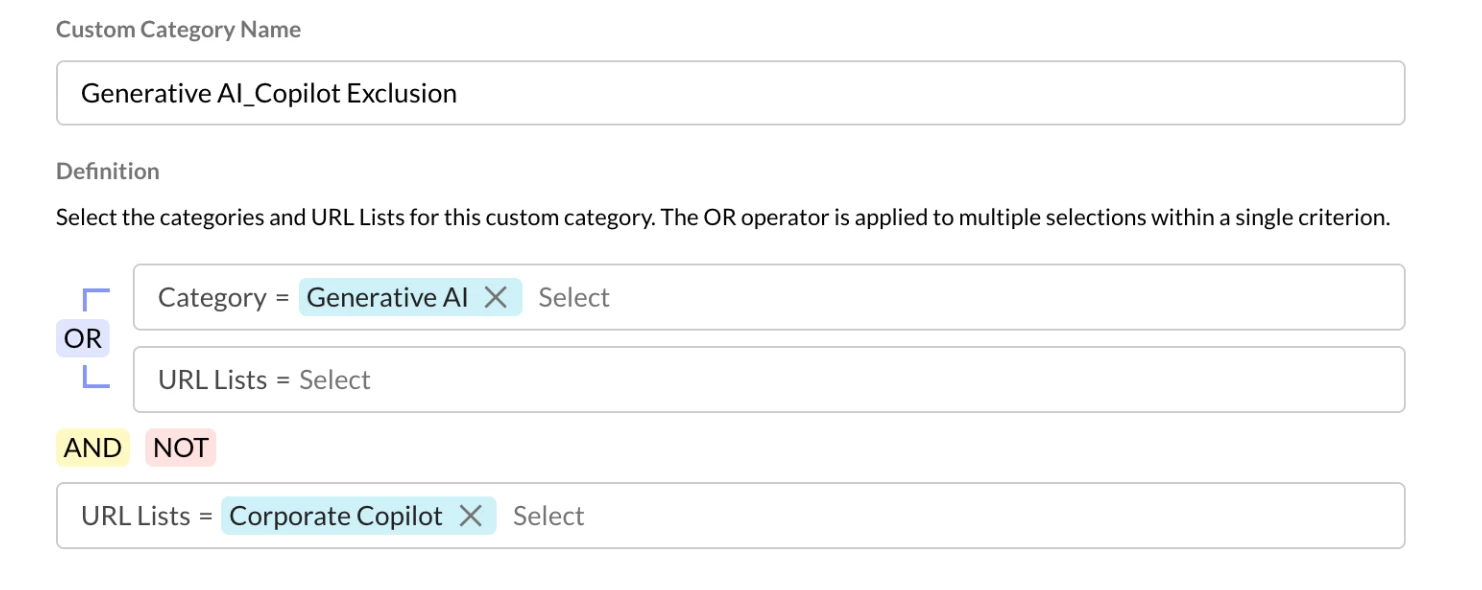
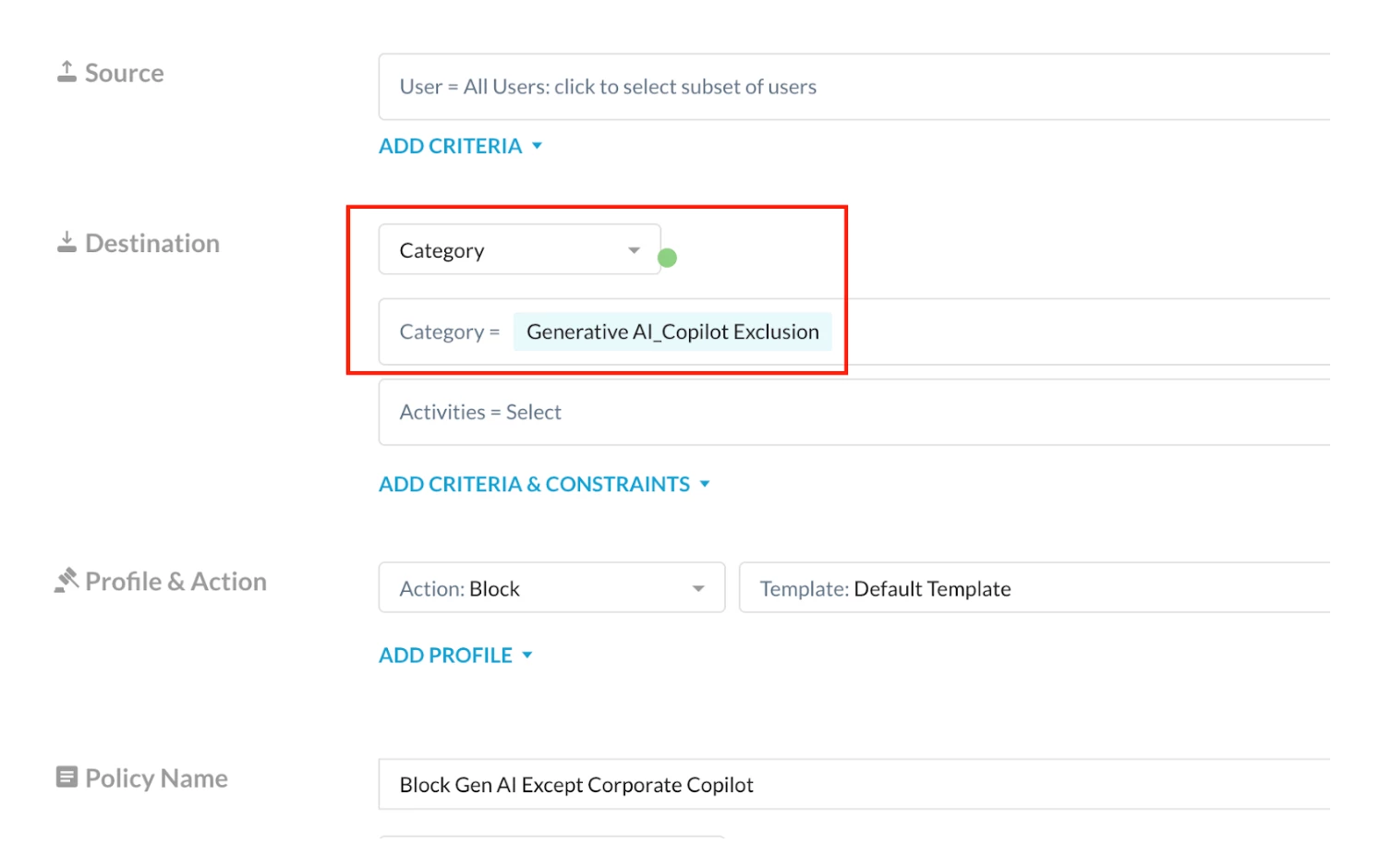
- Policy 4: Block access to the broader Generative AI category, while making an exception for the corporate Microsoft 365 Copilot URLs (copilot.cloud.microsoft and m365.cloud.microsoft/chat).
Let’s start Configuring Real Time Policies
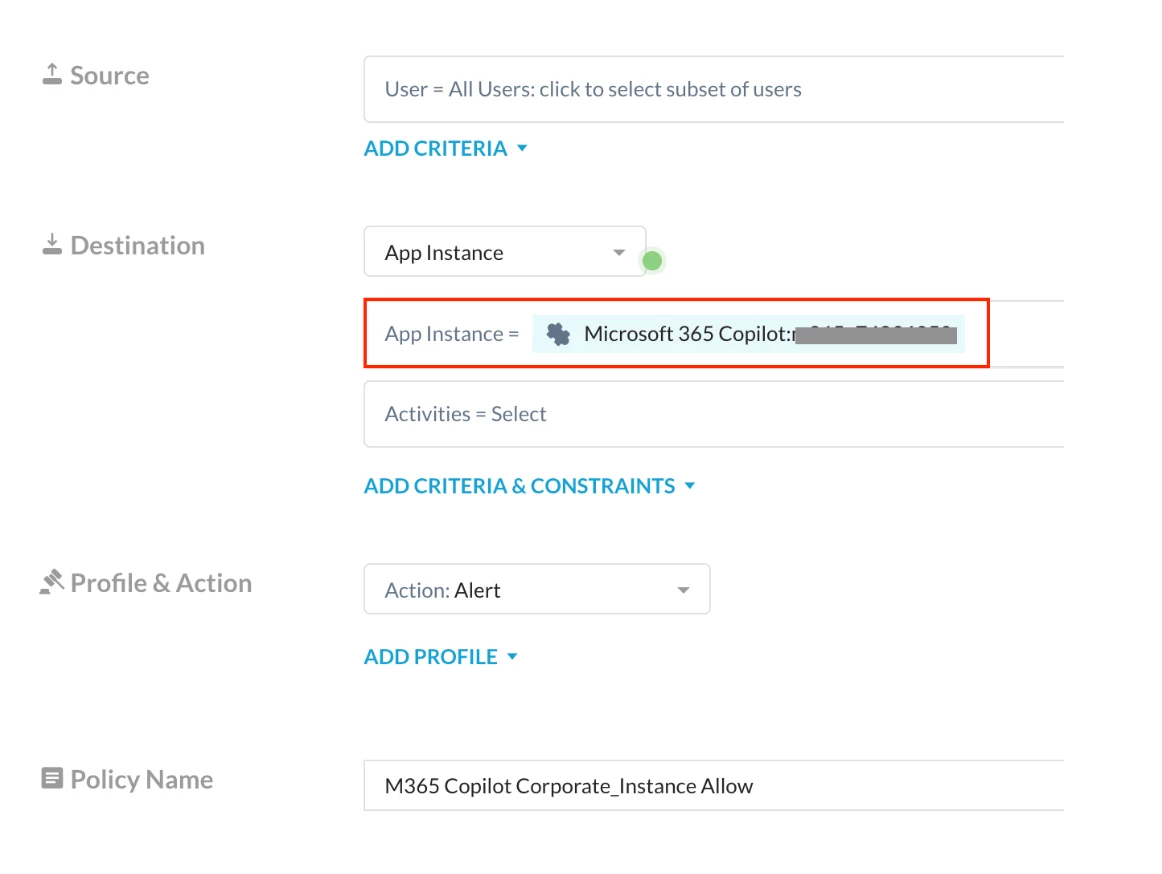
Policy 1: Allow activity specific to the corporate instance of Microsoft Accounts.
Step 1 - Instance Mapping for Microsoft 365 Copilot (Corporate) Organization account.
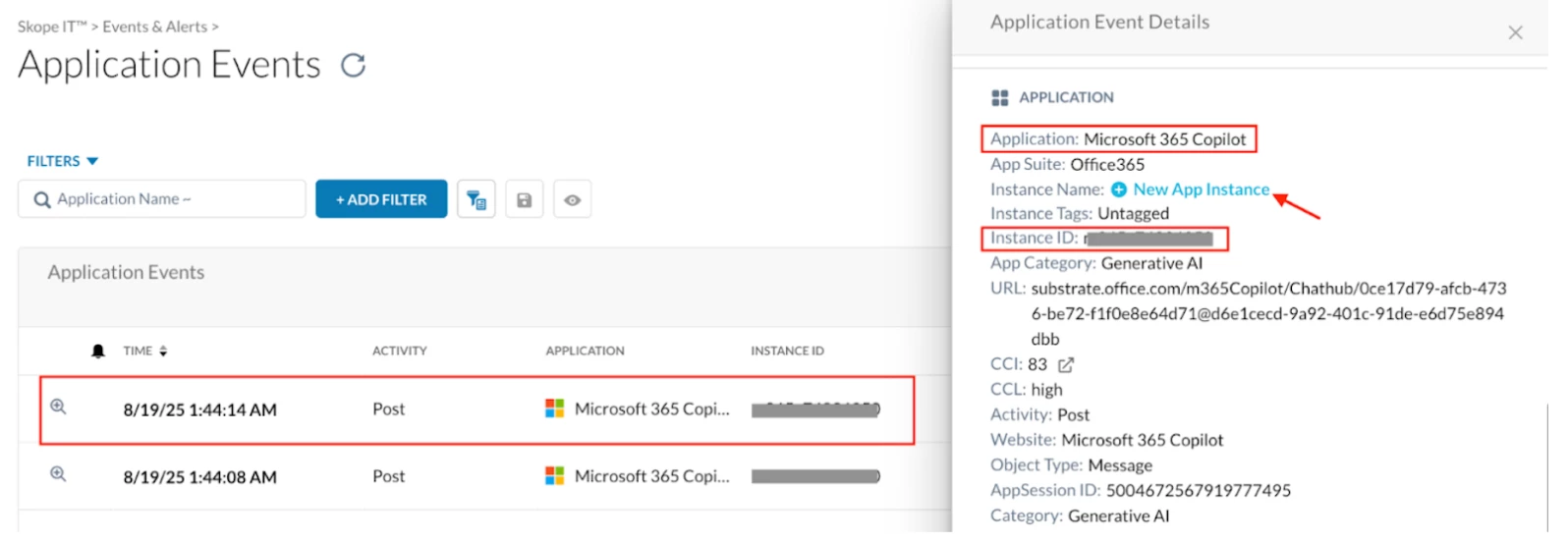
Step 2 - Real-time protection policy
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy
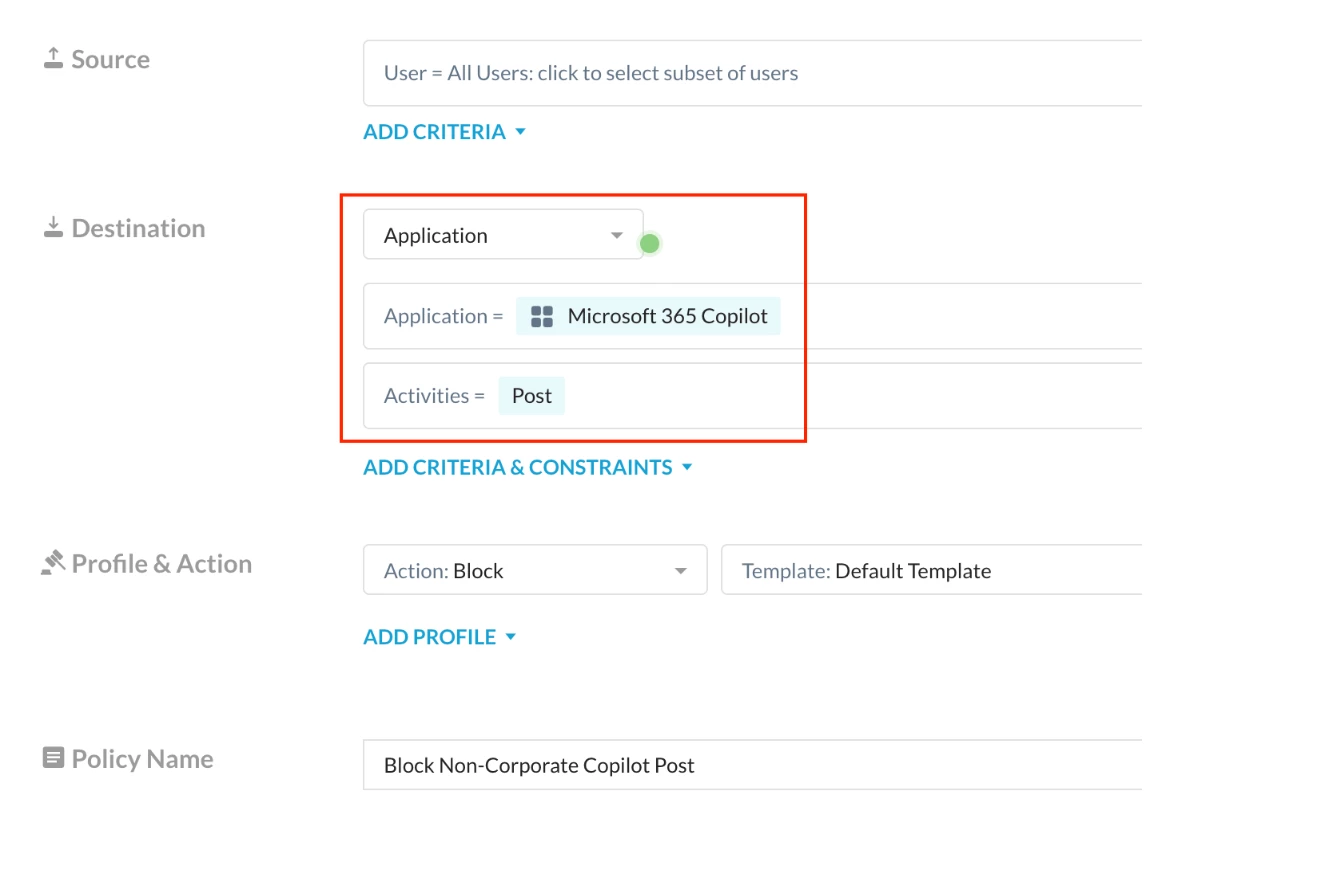
Policy 2: Block Post activity on Non-Corporate Instance of Microsoft 365 Copilot
In addition to Policy 1, this policy will block post activities from all instances of Microsoft 365 Copilot, except the organization’s own instance.
Policy 3: Allow user traffic going to Microsoft 365 Copilot URLs, based on specific HTTP referrer headers.
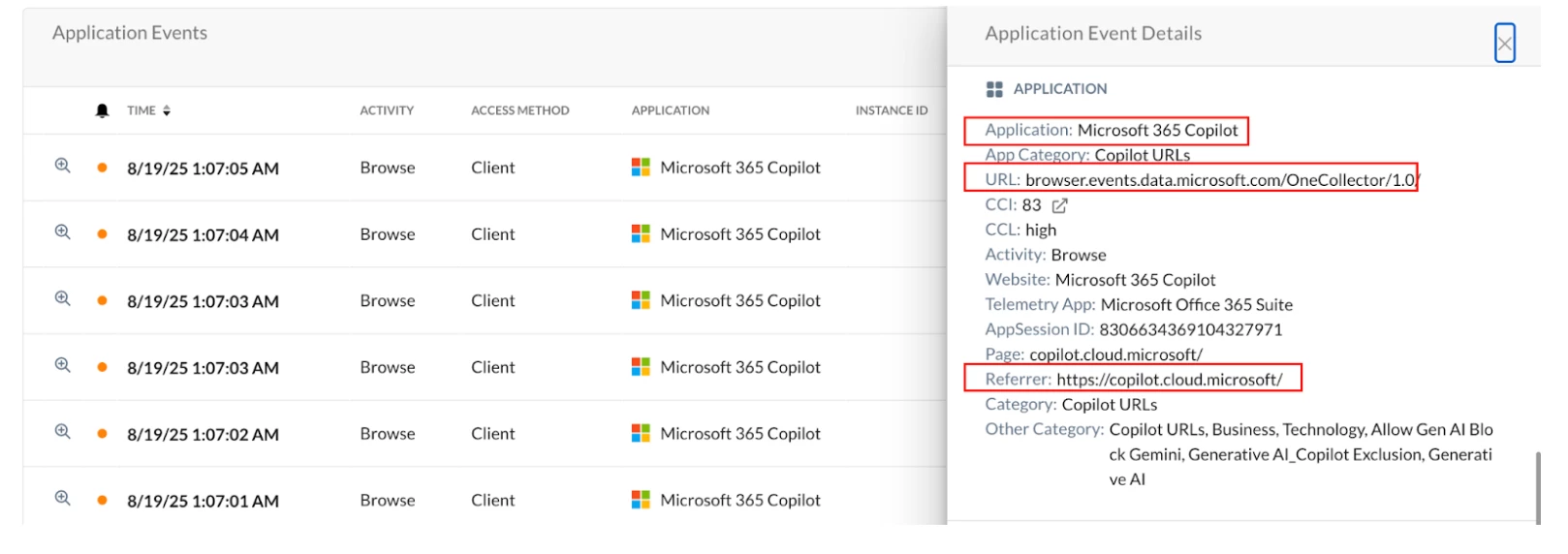
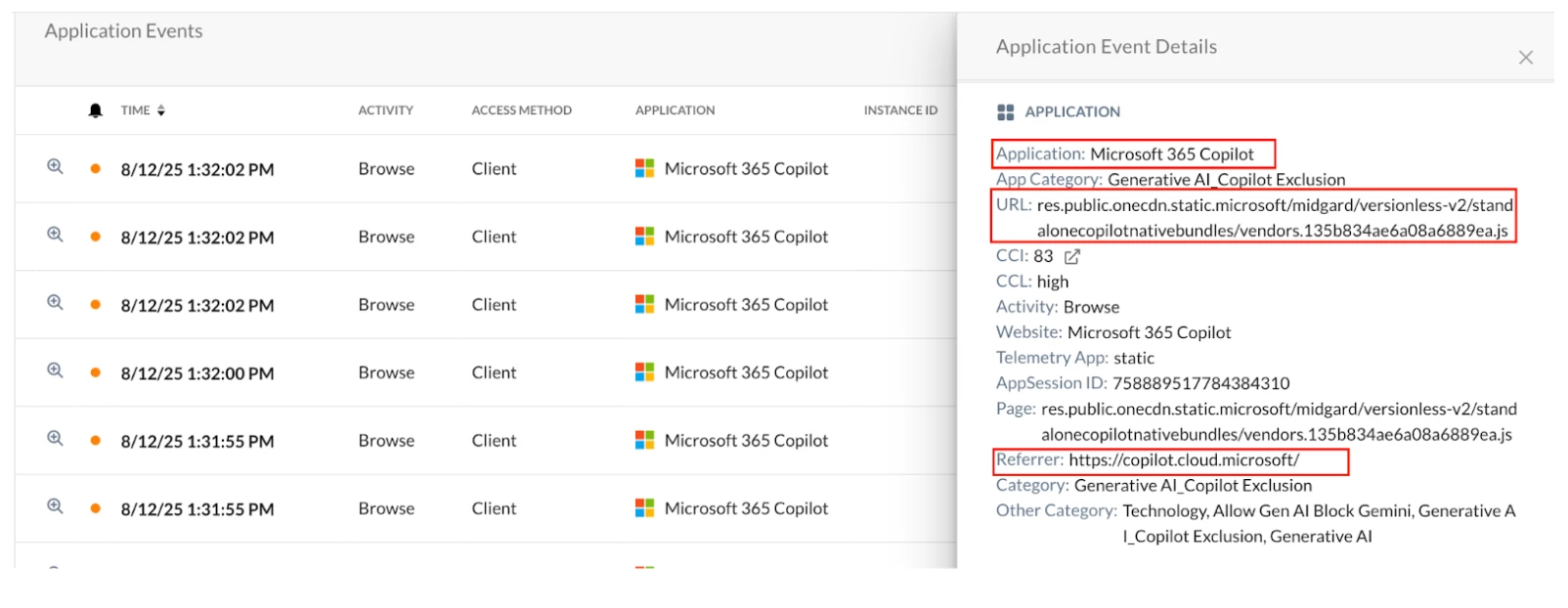
- The M365 Copilot Applications relies on few of the M365 back-end services for log-in and post activity of Copilot. It is not a user facing site instead, Microsoft 365 apps and services communicate with it in the background.
- The following URLs also need to be whitelisted when they are referenced by the Microsoft 365 Copilot application during transactions.
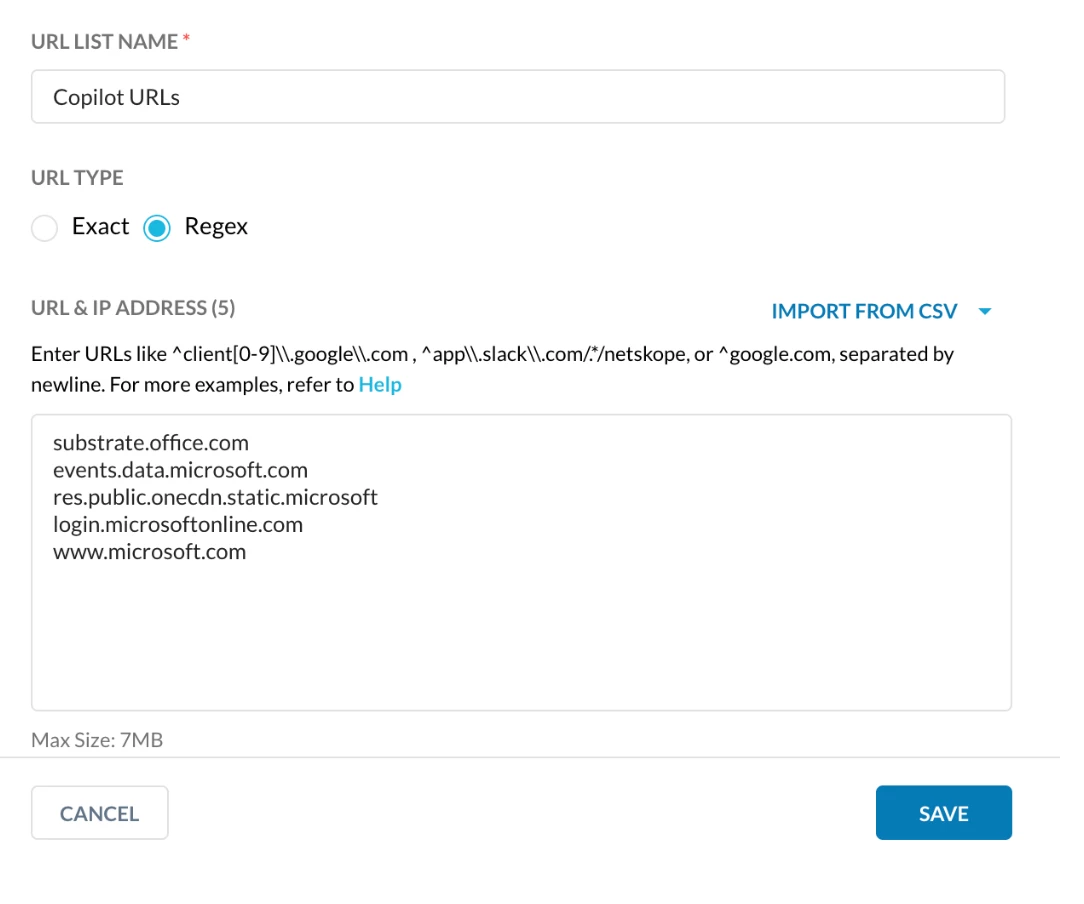
substrate.office.com
events.data.microsoft.com
res.public.onecdn.static.microsoft
login.microsoftonline.com
Application Events reference for few URLs:
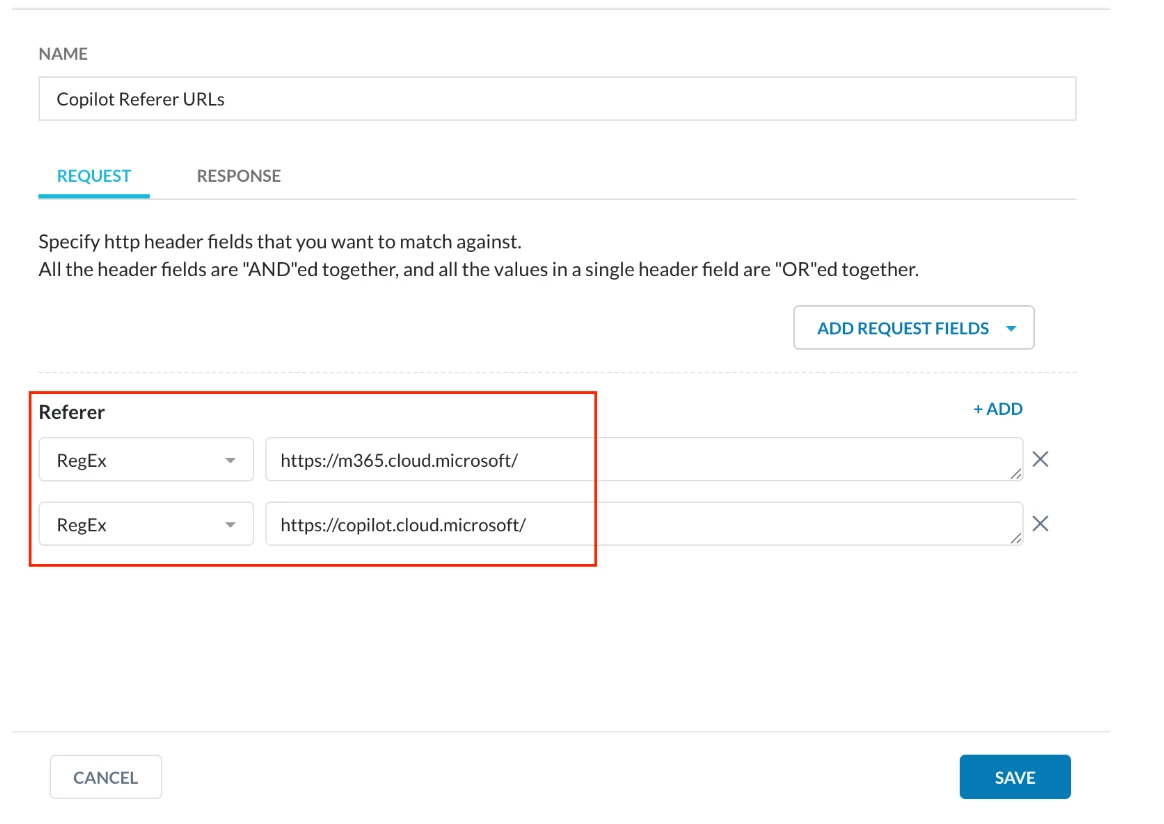
Step 1 - Create an HTTP Header profile for the Microsoft 365 Copilot URLs (copilot.cloud.microsoft and m365.cloud.microsoft)
Path: Netskope Tenant UI >>> Policies >>> HTTP Header
Step 2 - Create Custom URL Category for the above listed URLs
Path: Netskope Tenant UI >>> Profiles >>> URL Lists
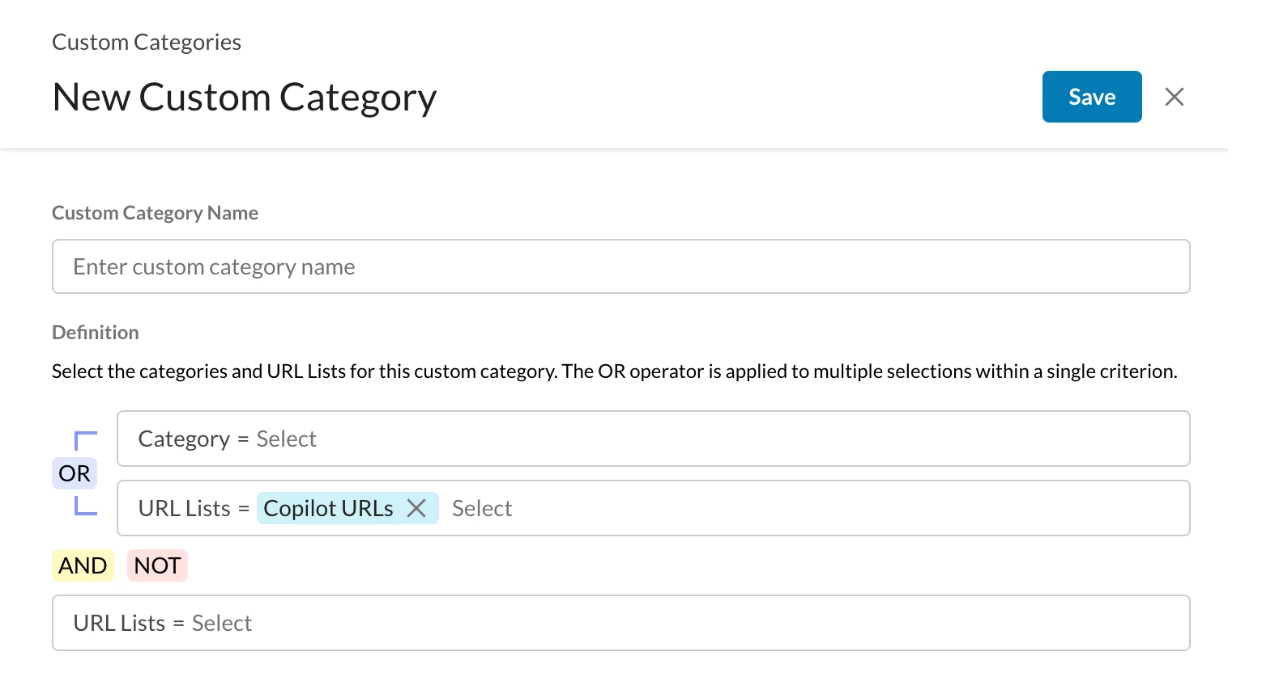
Path: Netskope Tenant UI >>> Profiles >>> Custom Categories
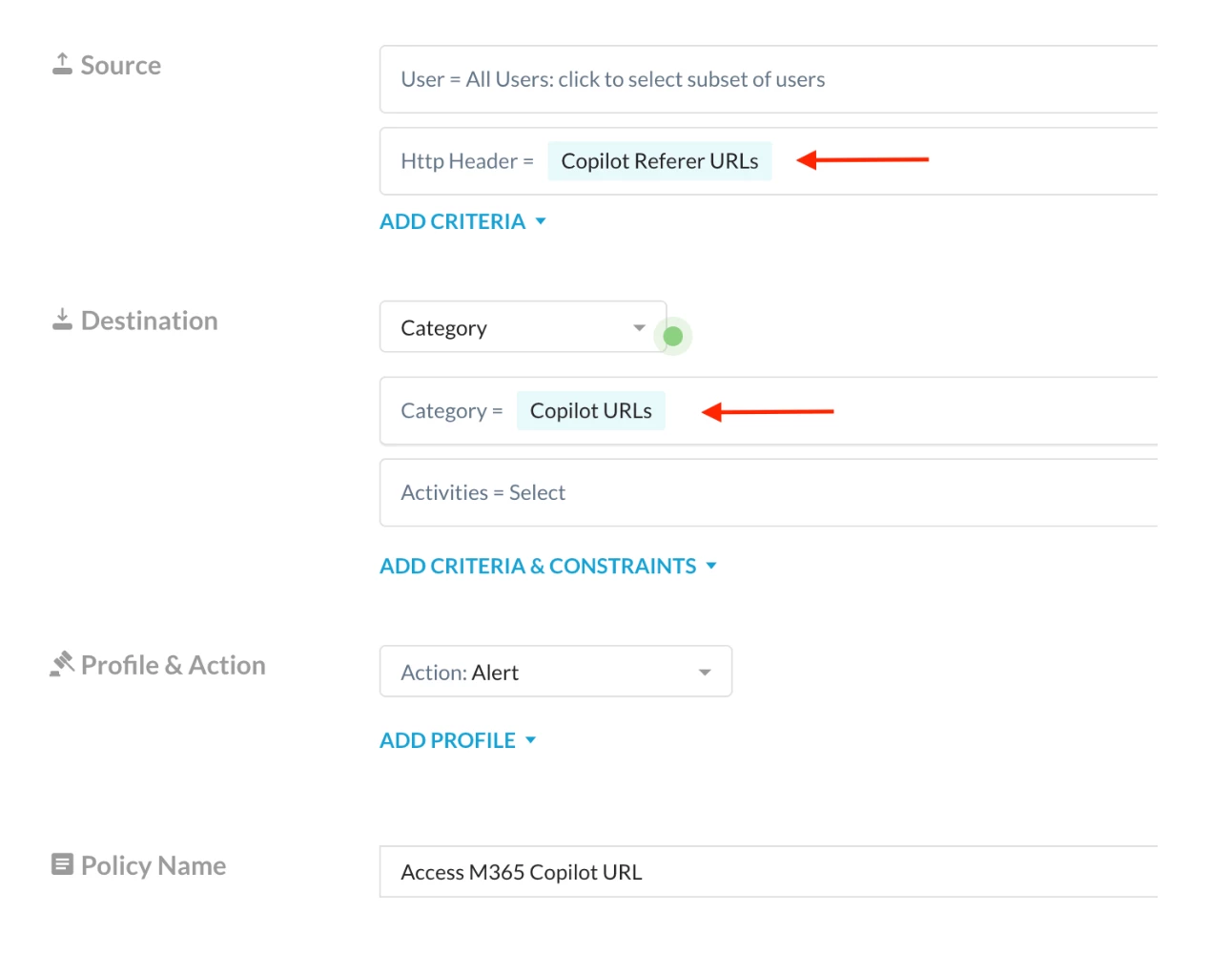
Step 3 - Create a Real-Time Protection Policy
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection
Policy 4: Block access to the broader Generative AI category, while making an exception for the corporate Microsoft 365 Copilot URLs
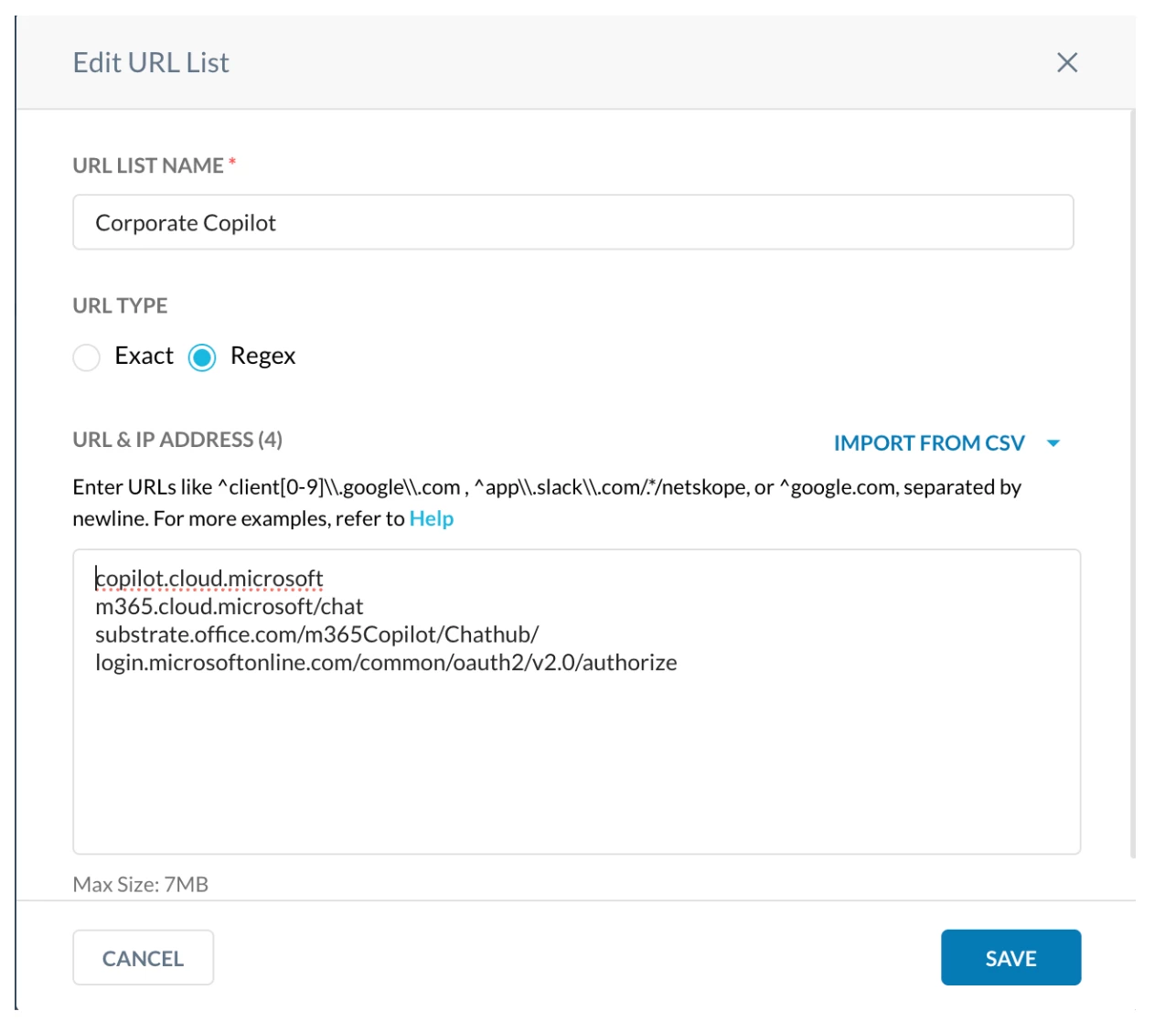
Step 1 - Create a custom URL category to add the below M365 Copilot URLs and their backend URLs as exclusion from Generative AI Category
- copilot.cloud.microsoft
- M365.cloud.microsoft
- substrate.office.com/m365Copilot/Chathub/
- login.microsoftonline.com/common/oauth2/v2.0/authorize
Path: Netskope Tenant UI >>> Policies >>> Profile - - - URL Lists
Path: Netskope Tenant UI >>> Policies >>> Profile - - - Custom Categories
Step 2 - Real-time protection policy
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy
Policy Order:
Workaround (Until the feature release)
To implement the workaround, Policy 1, Policy 3, and Policy 4 in the Configuration section remain unchanged.
Without enabling the feature, Netskope cannot detect M365 Copilot’s Post Activity in a Non-DLP context. Therefore, the approach is to add a random DLP profile to the Real-Time Policy and block all matched and unmatched DLP contexts. This will effectively block any post or upload of text/files by capturing those activities through the DLP profile.
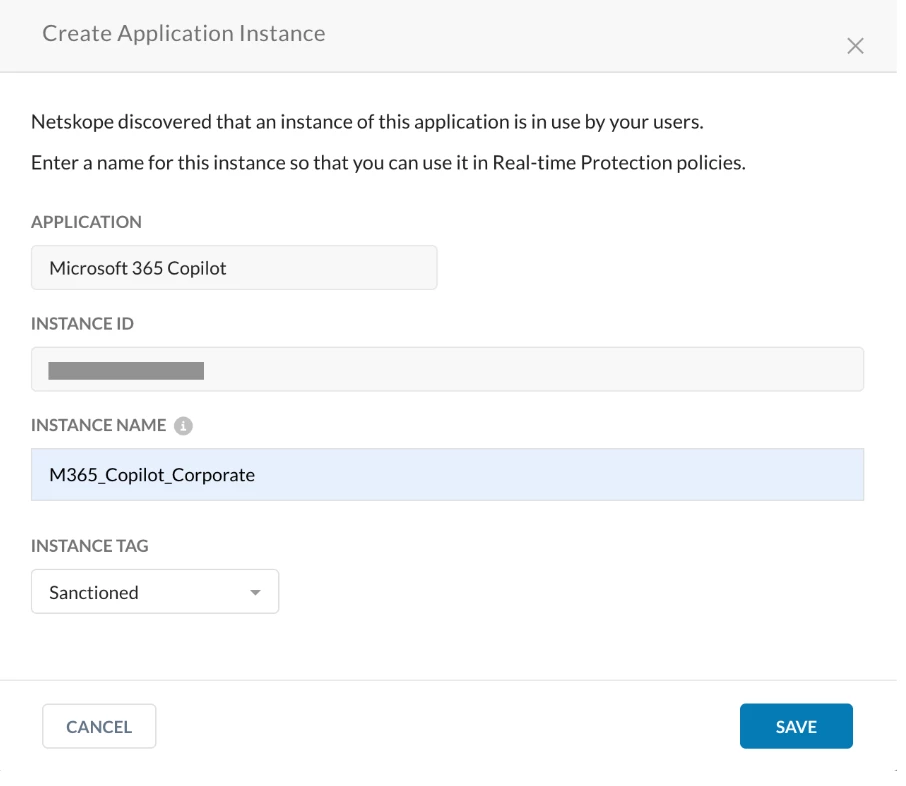
For the Policy 1: As the events are not detected by Netskope SkopeIT, You can create an App Instance Profile for M365 Copilot by navigating to Path: Netskope Tenant UI >>> Policies >>> Profiles - App Instance
If the Corporate domain is (example.com), then ‘example’ is the Instance ID
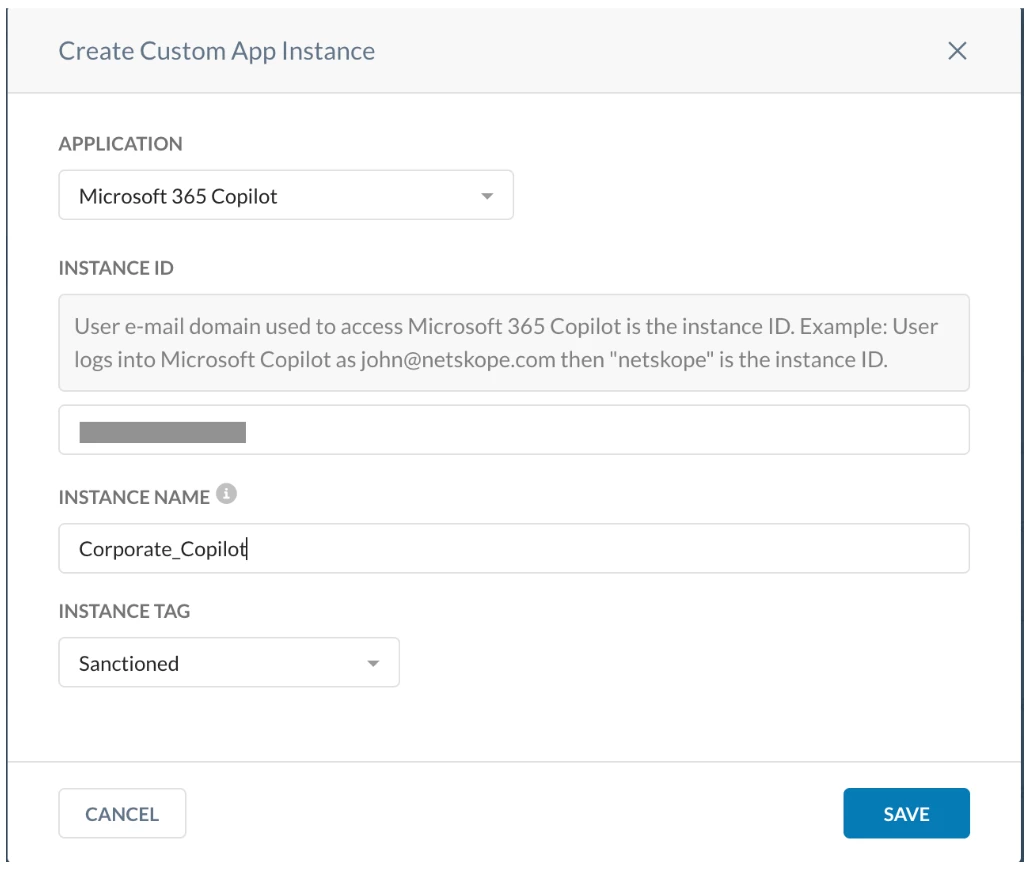
Incorporate the above App Instance Profile to the Real Time Policy as per the Policy 1 (Policy 1: Allow activity specific to the corporate instance of Microsoft Accounts.) mentioned in the Configuration section.
Policy 2: Add a DLP profile to the Real-Time Policy to detect all post/upload activity contexts. I’ve selected a PCI-DSS profile with a block action, and included the condition "If none of the specified profiles match: Block". This ensures that all post/upload activities are blocked, regardless of whether they match the profile.
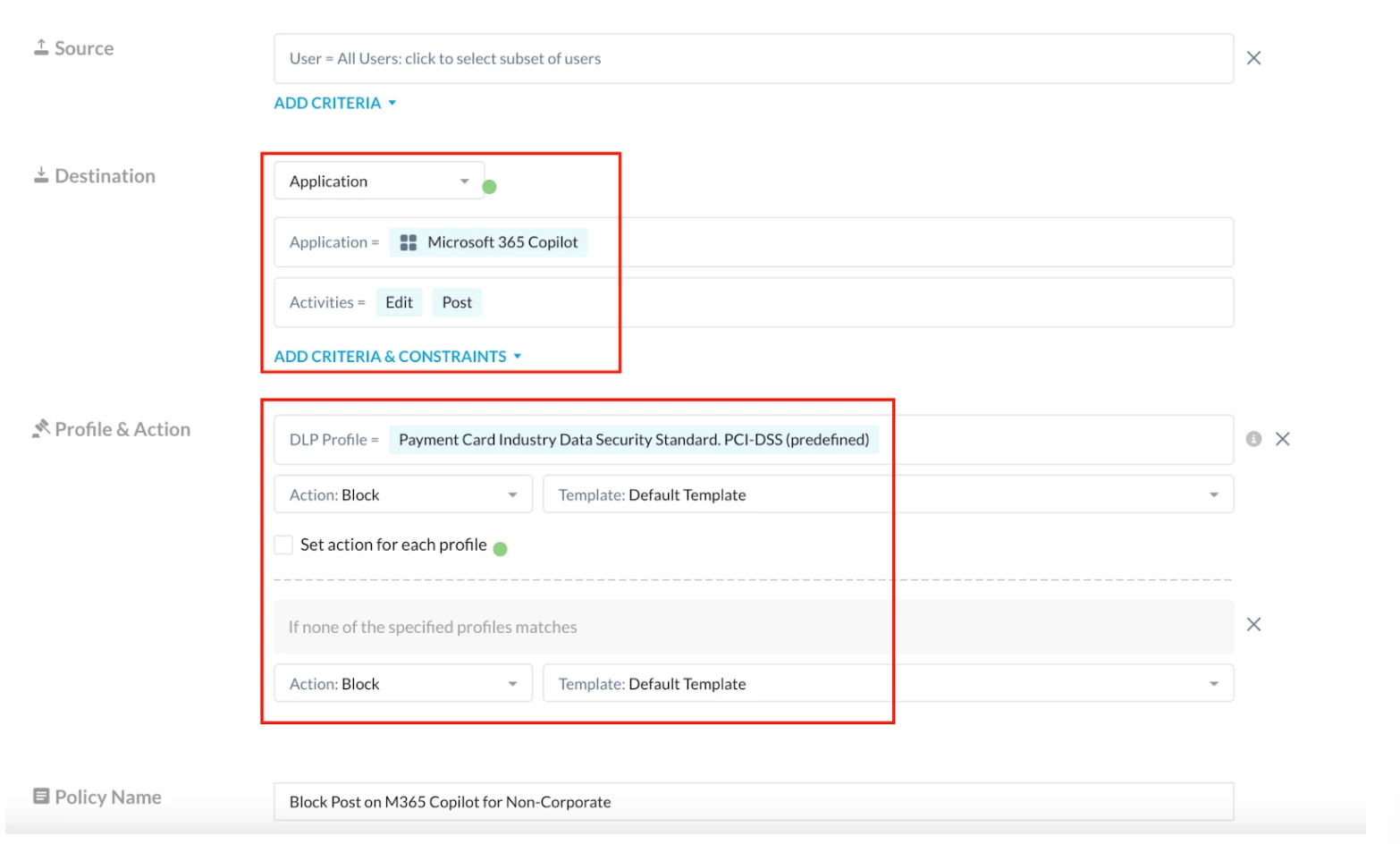
Policy 3 and Policy 4 remain the same.
Policy Order:
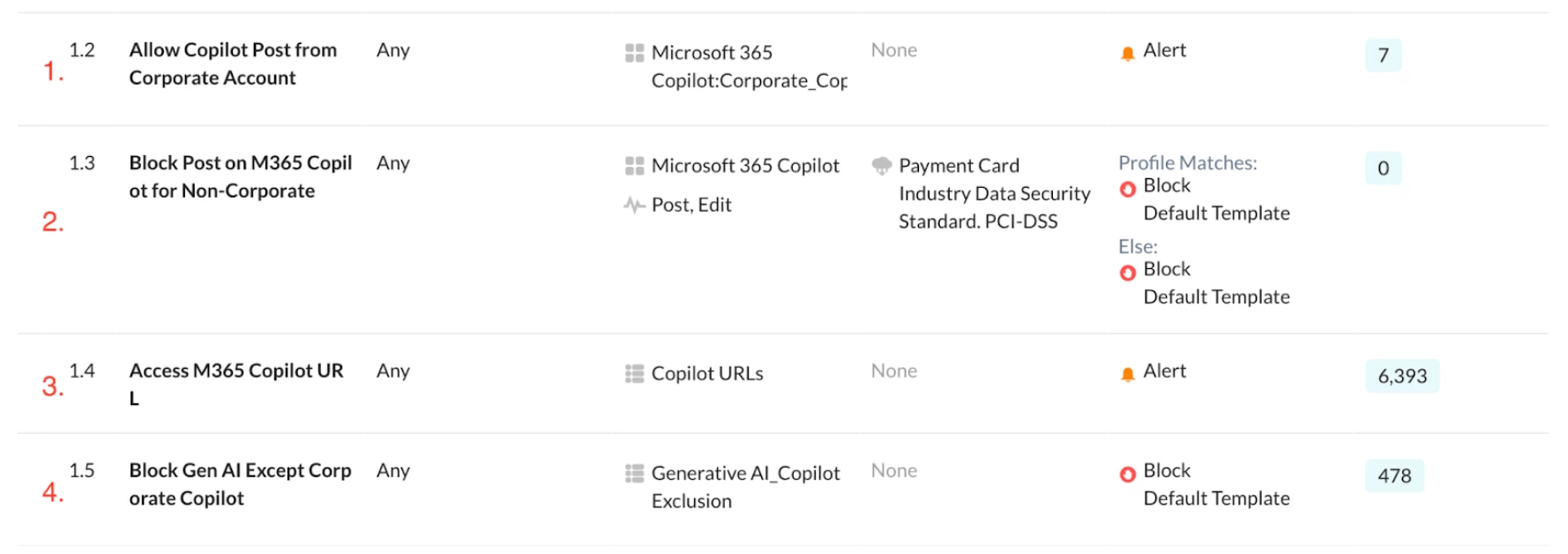
Verification
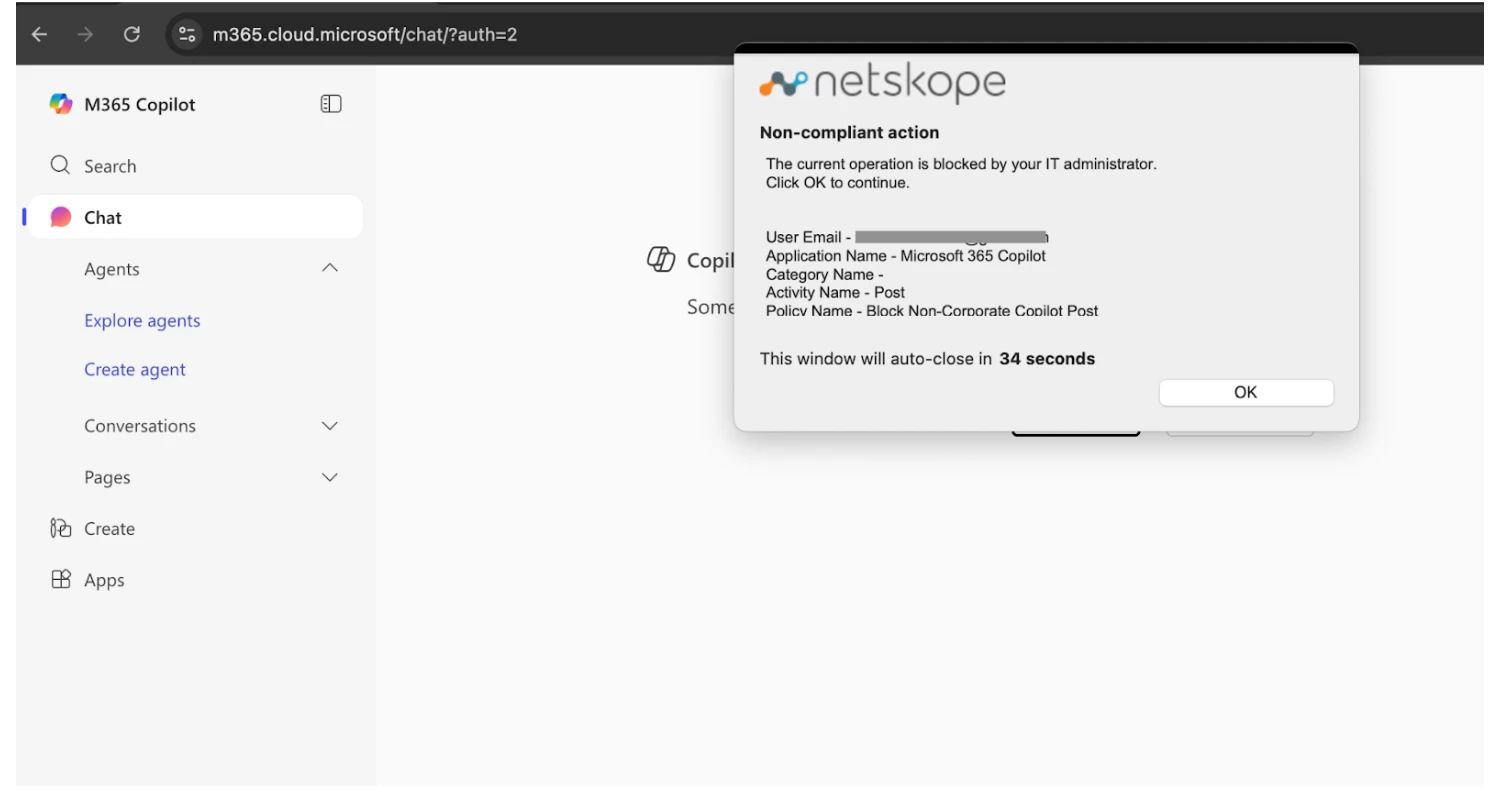
Try posting on Microsoft 365 Copilot using any other Corporate or Personal Account:
Try uploading on Microsoft 365 Copilot using any other Corporate Account:
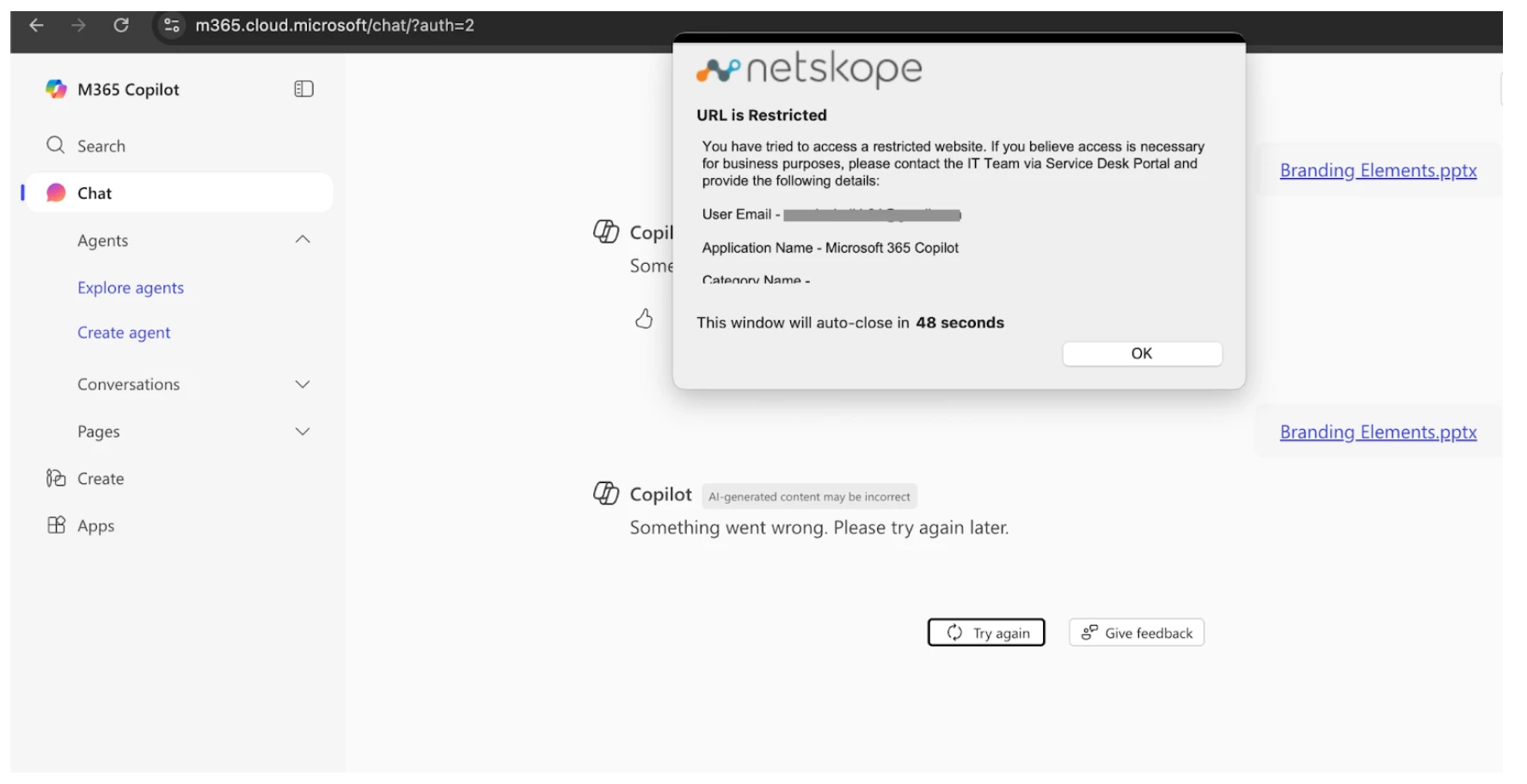
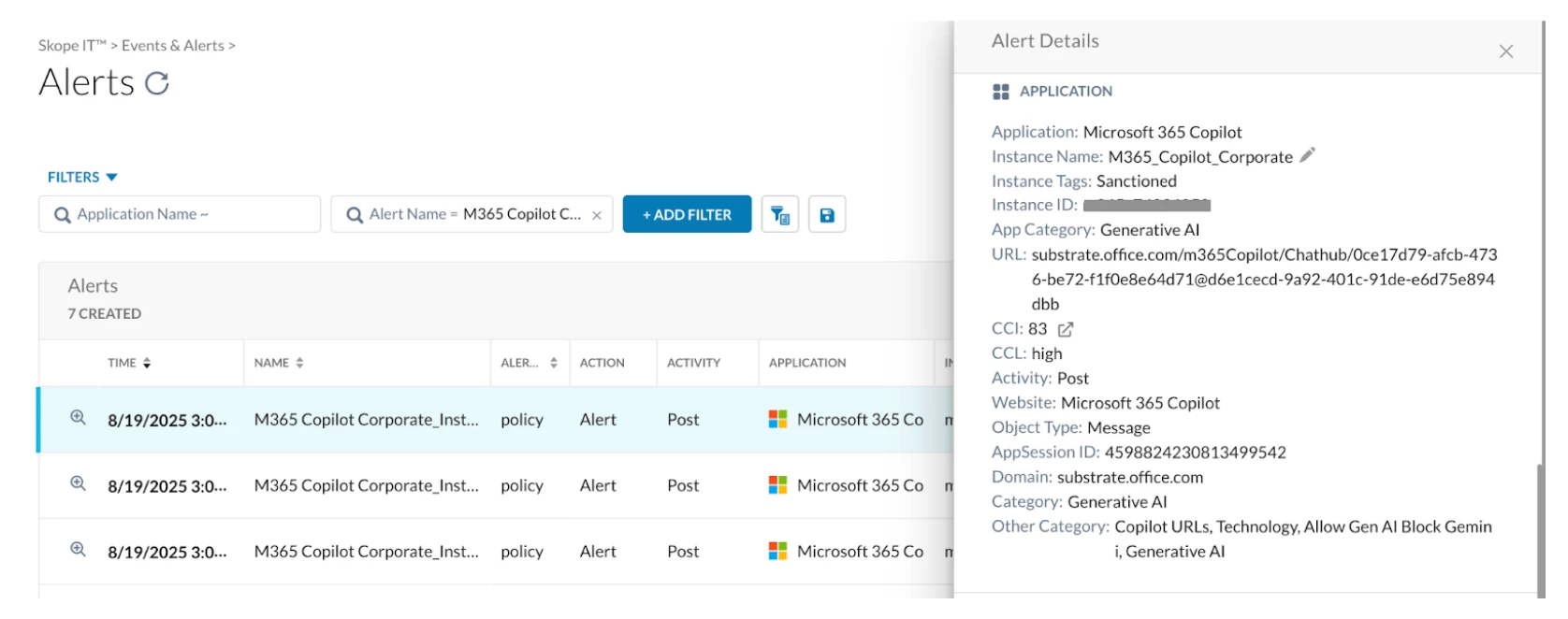
Path: Netskope Tenant UI >>> Skope IT >>> Alerts

Try posting on Microsoft 365 Copilot using Sanctioned Organization Account:
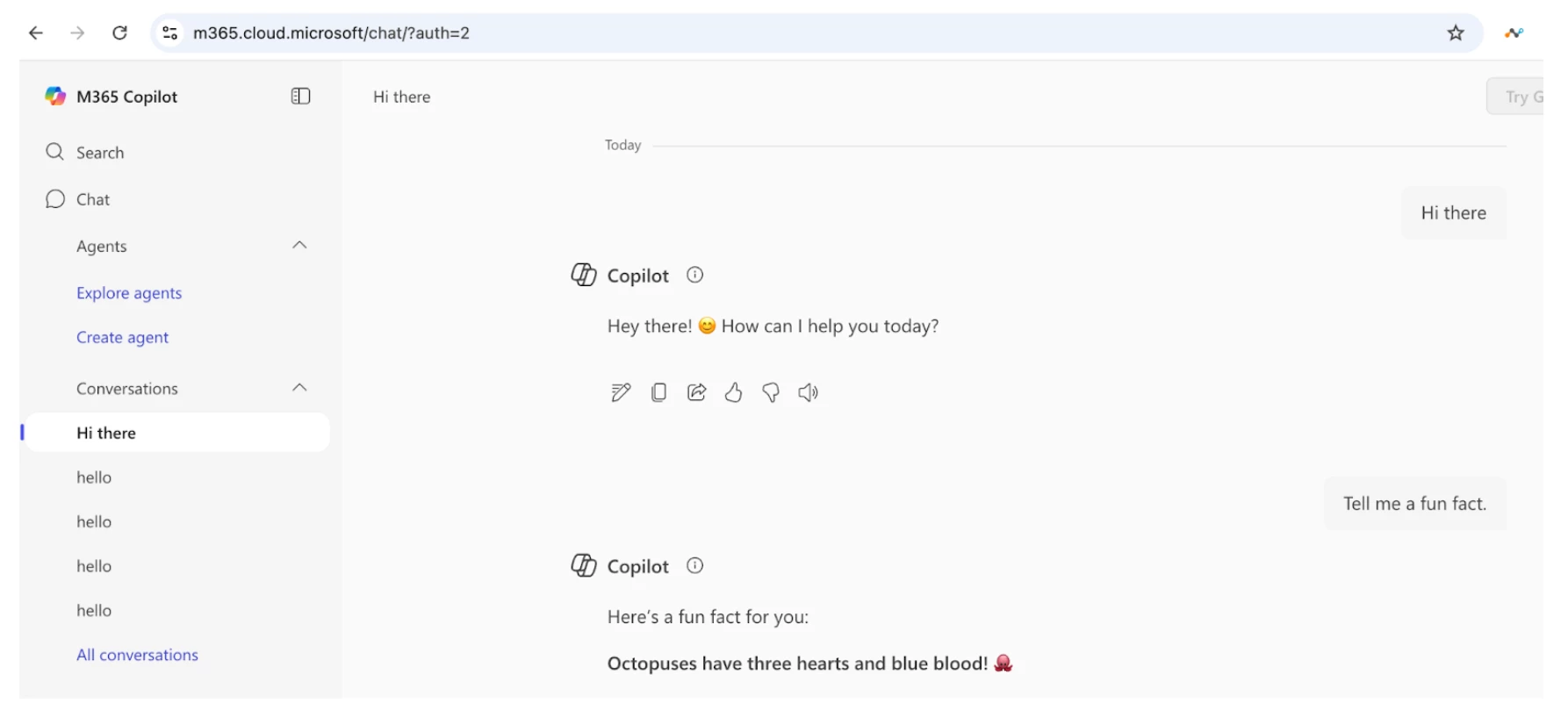
Path: Netskope Tenant UI >>> Skope IT >>> Alerts
Try accessing Microsoft Copilot (Personal) using Personal Account:
The action will be blocked.

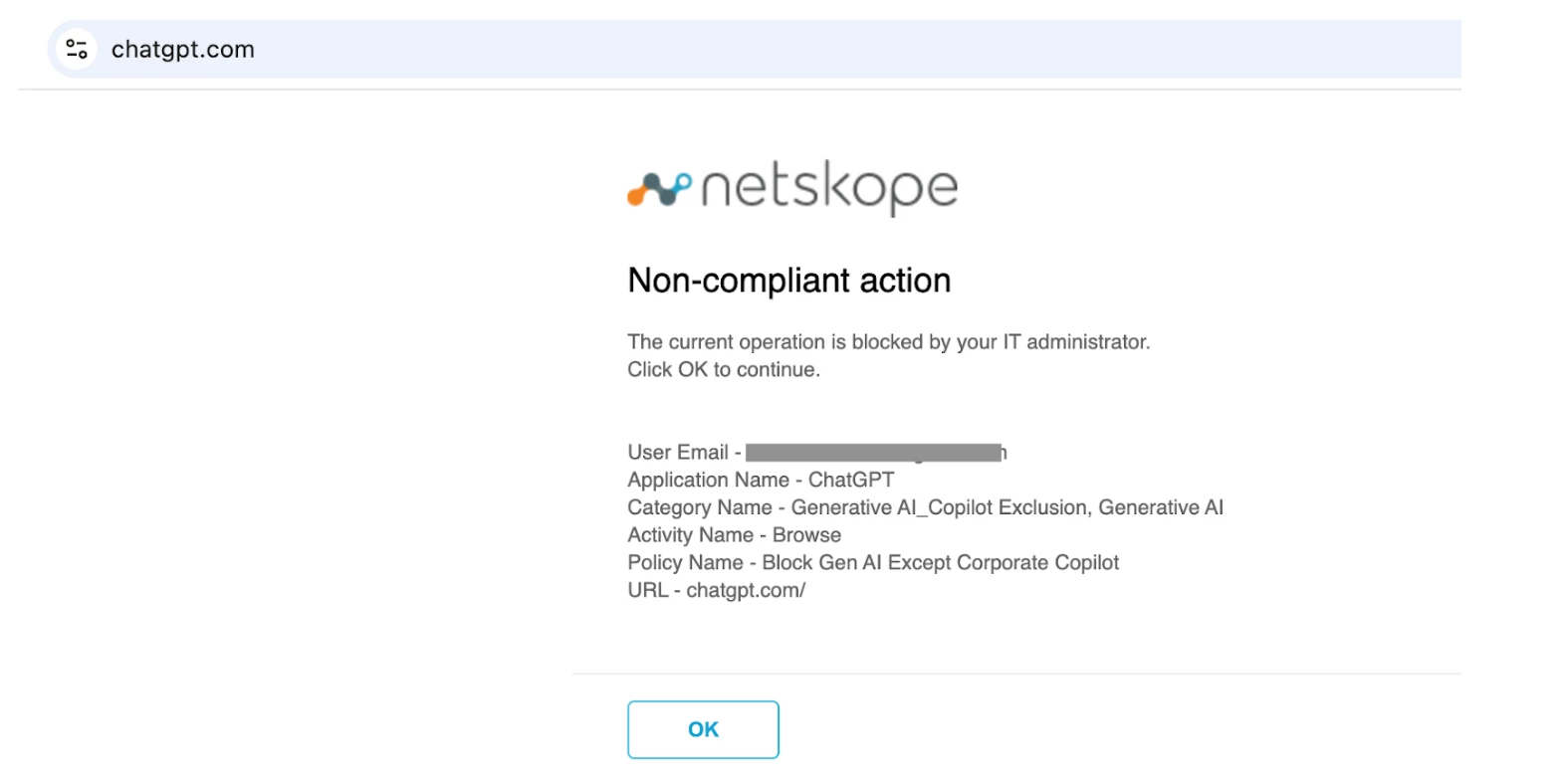
Try accessing any other Generative AI App e.g. ChatGPT
The action will be blocked.
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.






