I am very excited to introduce a community-based beta plugin for Cloud Exchange. This Network Access Control (NAC) plugin is designed to enhance Cloud Exchange by integrating Netskope telemetry with enterprise networks. It effectively enforces security measures and bridges the gap between customer network locations utilizing NAC solutions and the Netskope SSE Platform.
Purpose and Context:
- The NAC plugin enables sharing Netscope telemetry with enterprise networks, allowing appropriate enforcement actions based on detected threats or compromises.
- It allows to send information about managed users whether they are on the on-premise network (SDWAN or Client-Tunnel) or remote.
Functionality:
- The plugin leverages the SSE solution to detect high threats or indicators of compromise and shares this information with the enterprise network.
- It facilitates actions such as VLAN changes, quarantine roles, or group tag assignments based on detected incidents.
User and Device Management:
- The plugin targets managed users with Netscope clients or those using an SD-WAN tunnel.
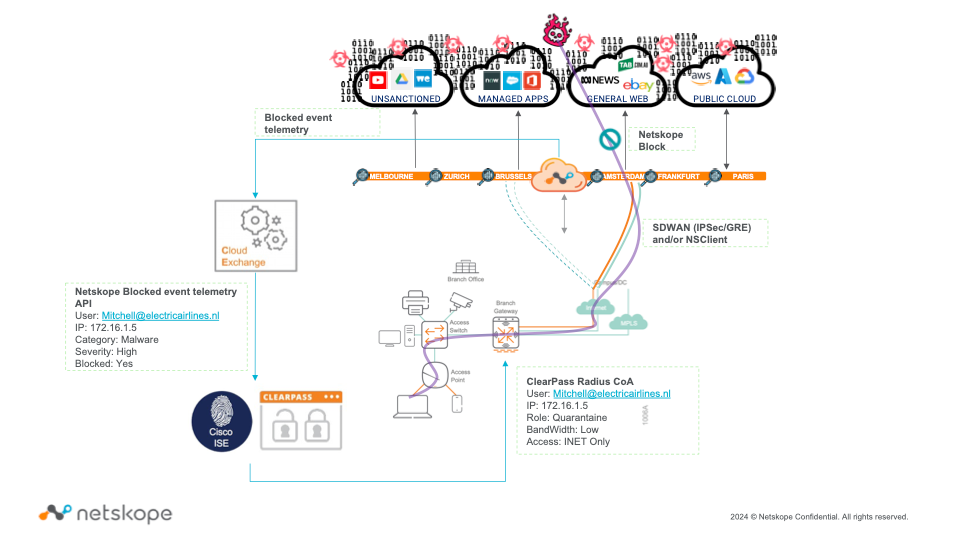
- When threats like phishing or malware are detected, telemetry is sent to Cloud Exchange, and the NAC plugin shares the event details (device information, incident specifics) with the network access control device.
Supported Solutions:
- Currently supports ClearPass and Cisco Identity Service Engine (ISE) for enforcing network access control.
- Can be extended to support other network solutions (FortiNAC, ForcePoint).
User-Based Operational Workflow:
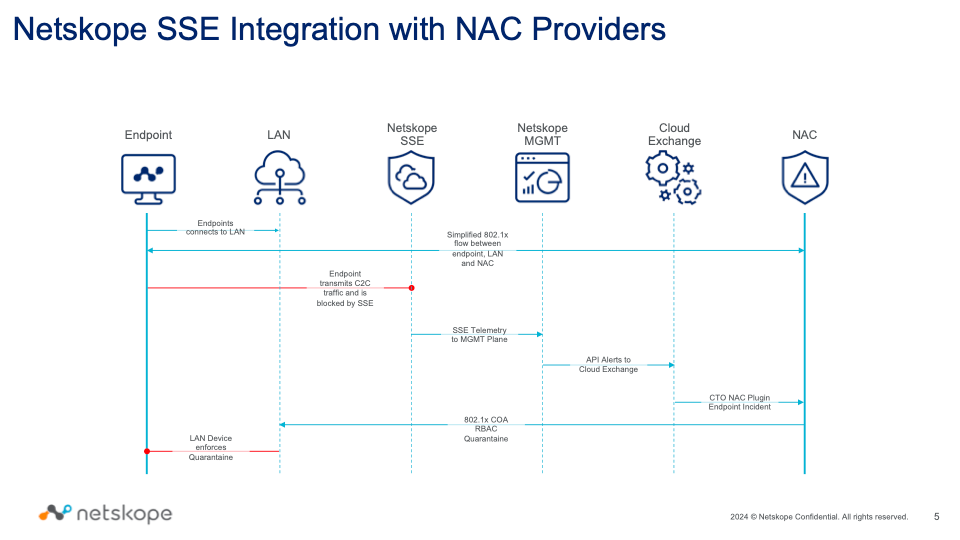
- The process begins with user authentication on the LAN network using 802.1x radius authentication.
- Netscope detects threats and sends telemetry to the management plane, which is then shared with Cloud Exchange.
- The NAC plugin processes this data and updates the network access control device to enforce appropriate actions.
Cloud-Exchange Operational Workflow:
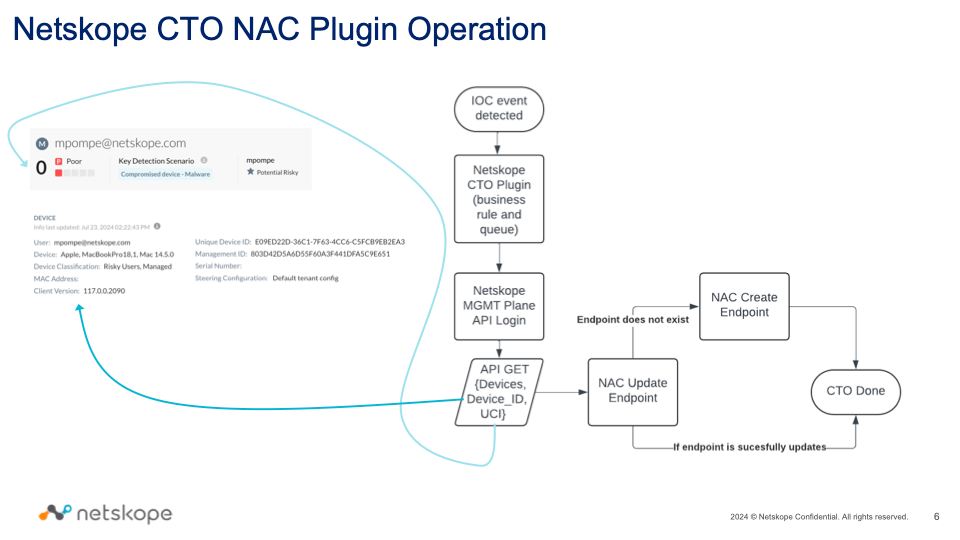
- Netskope Cloud Exchange (CE) retrieves and ingests alerts destined for the ticket orchestrator module (key information: hostname, UPN, alert details)
- CE processes the alerts based on a Business Rule:
- Hostname NOT empty
- Alert Type is equal to Malware
- Policy (name) contains Malware
- Deduplication based on: ‘Request Id’ and ‘Incident Id’
- CE Queue is the link between tenant->business rule-> NAC Notifier Plugin
- NAC Plugin retrieves additional information from Netskope Tenant:
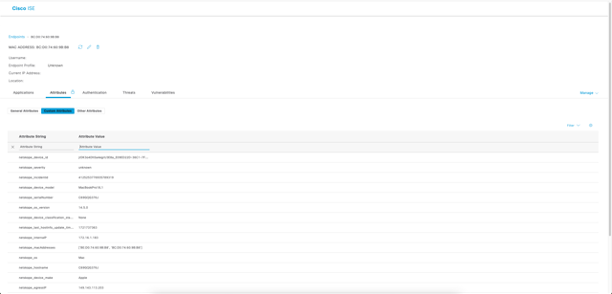
- Device details (MAC Address, compliance information)
- UEBA User Confidence Score (if licensed)
- NAC Plugin tries to update or else create the endpoint with the Netskope Incident and endpoint details.
Technical Details:
- The plugin uses the Web Use Interface API to fetch device details and operates through the Cloud Exchange Ticket Orchestrator module.
- The workflow includes synchronizing APIs, creating incidents, and updating endpoints with appropriate actions based on business rules.
The NAC plugin offers a robust mechanism to integrate Netscope telemetry with enterprise networks, ensuring enhanced security through dynamic and automated enforcement actions based on detected threats. This is a true differentiator against other SSE-vendors as it provides a clean and efficient solution for informing network access solutions based on real-time threat detection in the Netskope SSE-Platform.
What is does not do:
It only synchronizes information based on a managed identity, with the Netskope Client. Gues/Machine/Explicit Proxy user information is NOT supported.
In addition, this plugin is not intended as a Managed Device sync server.
Trying it out
This post explains how to configure the Beta Netskope NAC Notifier with the Cloud Ticket Orchestrator module of the Netskope Cloud Exchange platform. Please remember that at the current stage it is a beta plugin and should be treated as such. Feedback is most welcome at mpompe@netskope.com.
Prerequisites
To complete this configuration, you need:
- A Netskope Tenant (or multiple, for example, production and development/test instances)
- A dedicated service account with custom admin role in the Netskope environment
- A Netskope Cloud Exchange environment of version 5.x+ with the Ticket Orchestrator module already configured.
- NAC account API/Admin credentials (OR):
- Cisco ISE API admin account (currently a token is not yet supported)
- HPE Aruba ClearPass API Token
- Netskope Cloud Exchange should have network connectivity towards the NAC solution
1. Netskope Tenant Configuration
Creating the custom role:
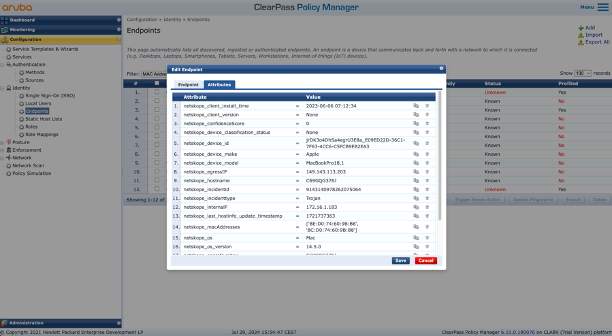
The NAC Plugin utilises the following resources: device, device/{device_id} and /uba/fetchUsersAndStatistics .
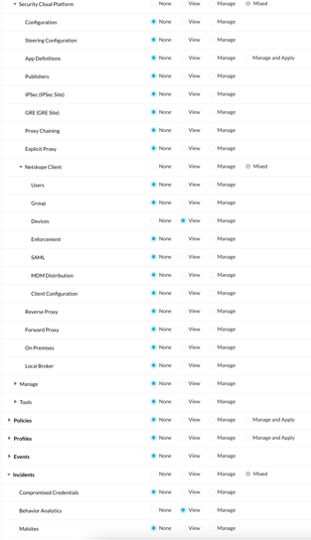
In the Management Interface of Netskope a custom role should be created for this API service account with the following rights.
Functional Areas:
•Access Control (all)
•Behavioral Analytics
Page Permissions – ALL NONE, EXCEPT:
Settings -> Security Cloud Platform -> Netskope Client:
•Devices: View
Incidents:
•Behavior Analytics: View
!*Remember that if a new user account is created, an initial first login is required to change the password.
2. NAC Configuration
2.1 Create the right Admin/API credentials for Cisco ISE or HPE Aruba ClearPass (https://developer.arubanetworks.com/aruba-cppm/docs/clearpass-configuration )
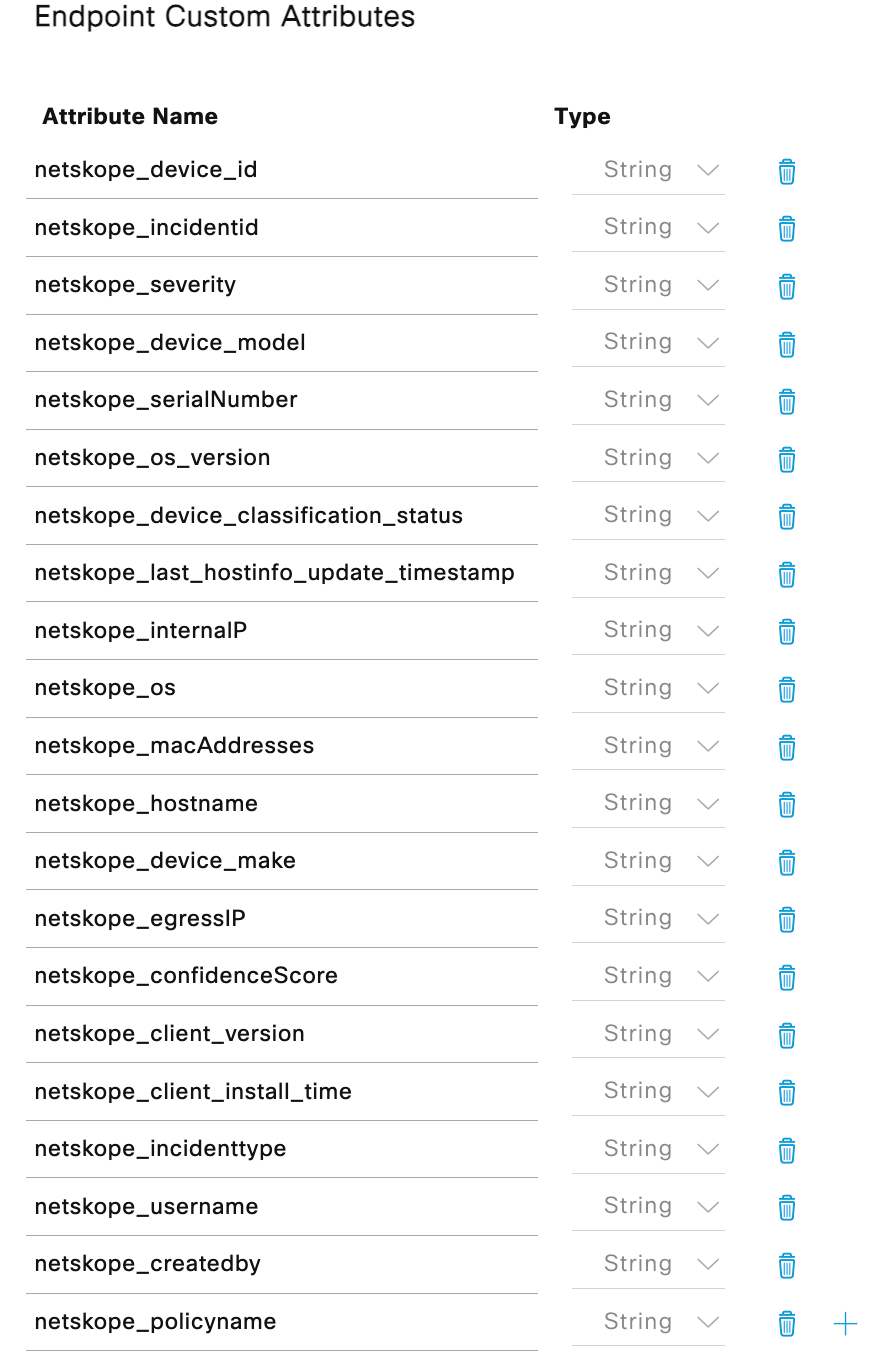
2.2 Create the right Custom endpoint attributes (for Cisco ISE required, HPE Aruba ClearPass dynamically)
Cloud Exchange Configuration
Add the following community Beta Github as a repository and add the CTO NAC Plugin:
https://github.com/nskope-MPM/ce_plugins_beta.git
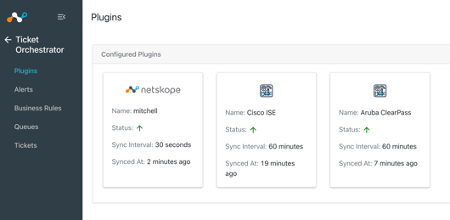
Add and configure the appropriate plugin:
The current plugins require the following credentials:
- NAC: Cisco ISE username/password or ClearPass API key
- Netskope Admin account with a custom role
Business Rule configuration:
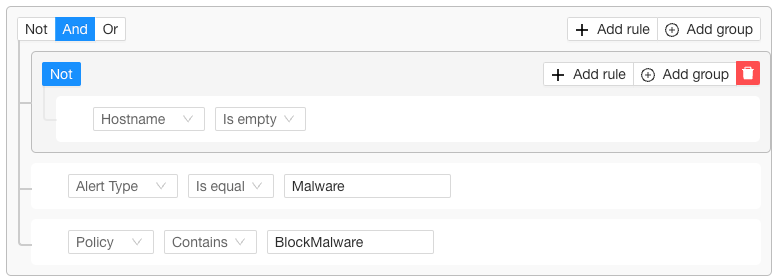
- Hostname NOT empty
- Alert Type is equal to Malware
- Policy (name) contains Malware
- Deduplication based on: ‘Request Id’ and ‘Incident Id’
Queue information required for the ticket:
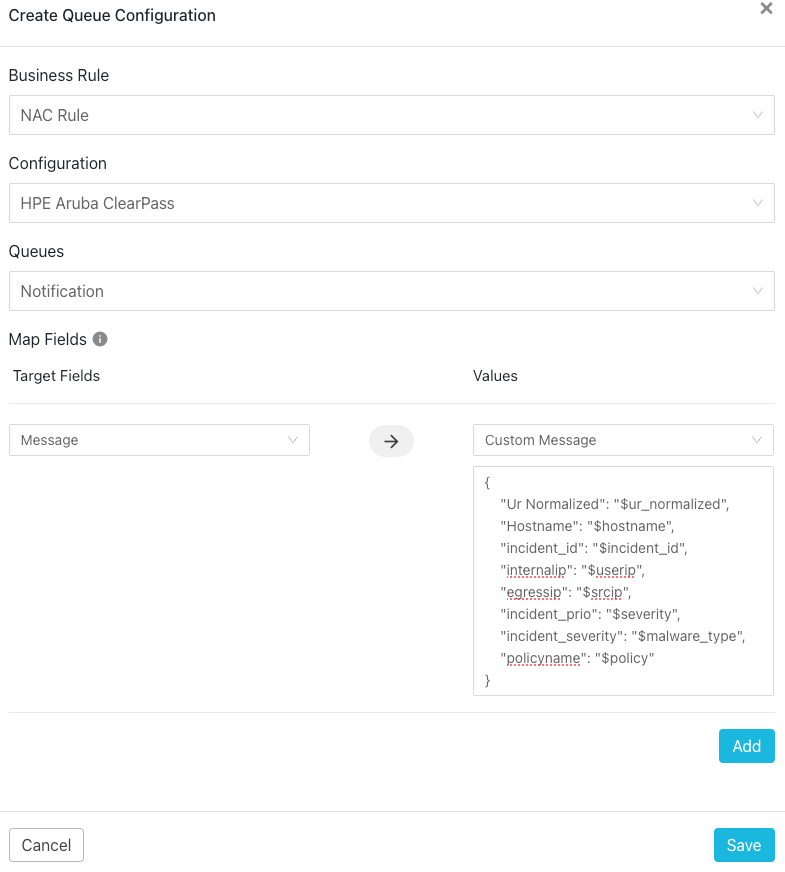
{
"Ur Normalized": "$ur_normalized",
"Hostname": "$hostname",
"incident_id": "$incident_id",
"internalip": "$userip",
"egressip": "$srcip",
"incident_prio": "$severity",
"incident_severity": "$malware_type",
"policyname": "$policy"
}Verify Operation
Verify the operation of the plugin under the CTO Tickets tab:
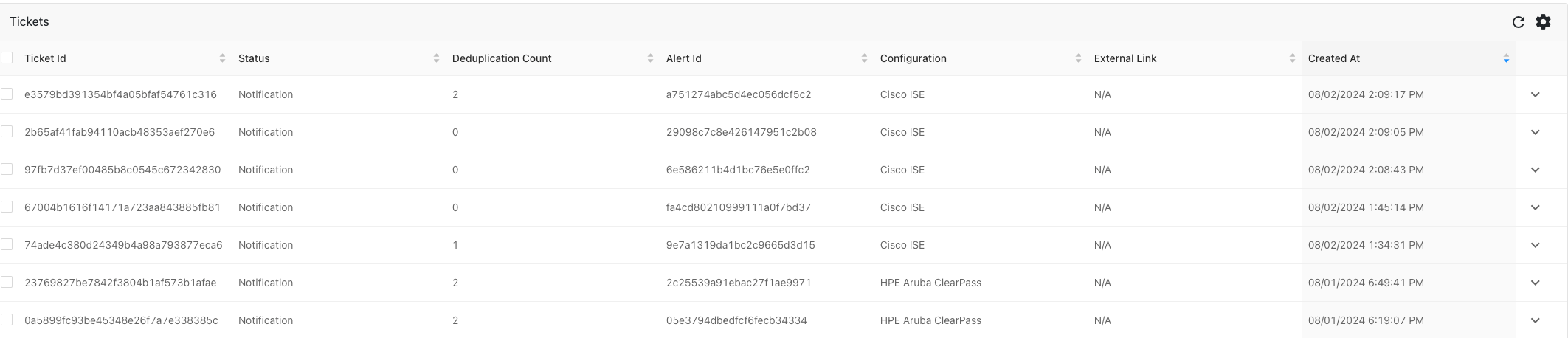
NAC Solution results: