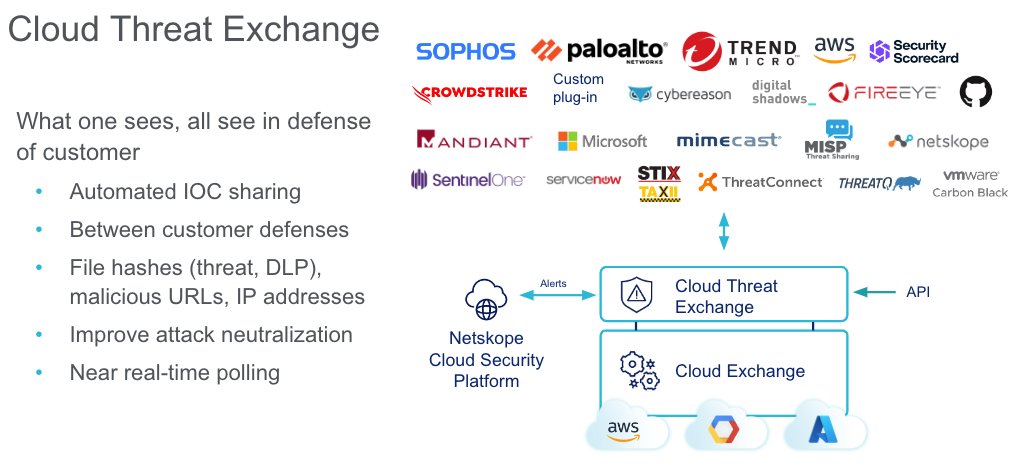
One of the most important lines of defense in the Netskope Platform is the Threat Protection Engine. In the coming weeks, we will take a closer look under the hood and explore together how Netskope makes life difficult for attackers. One piece of the advanced multilayered threat protection is a module, based on classic threat intel feeds.
But which feeds are used and can customers customize or enrich them themselves?
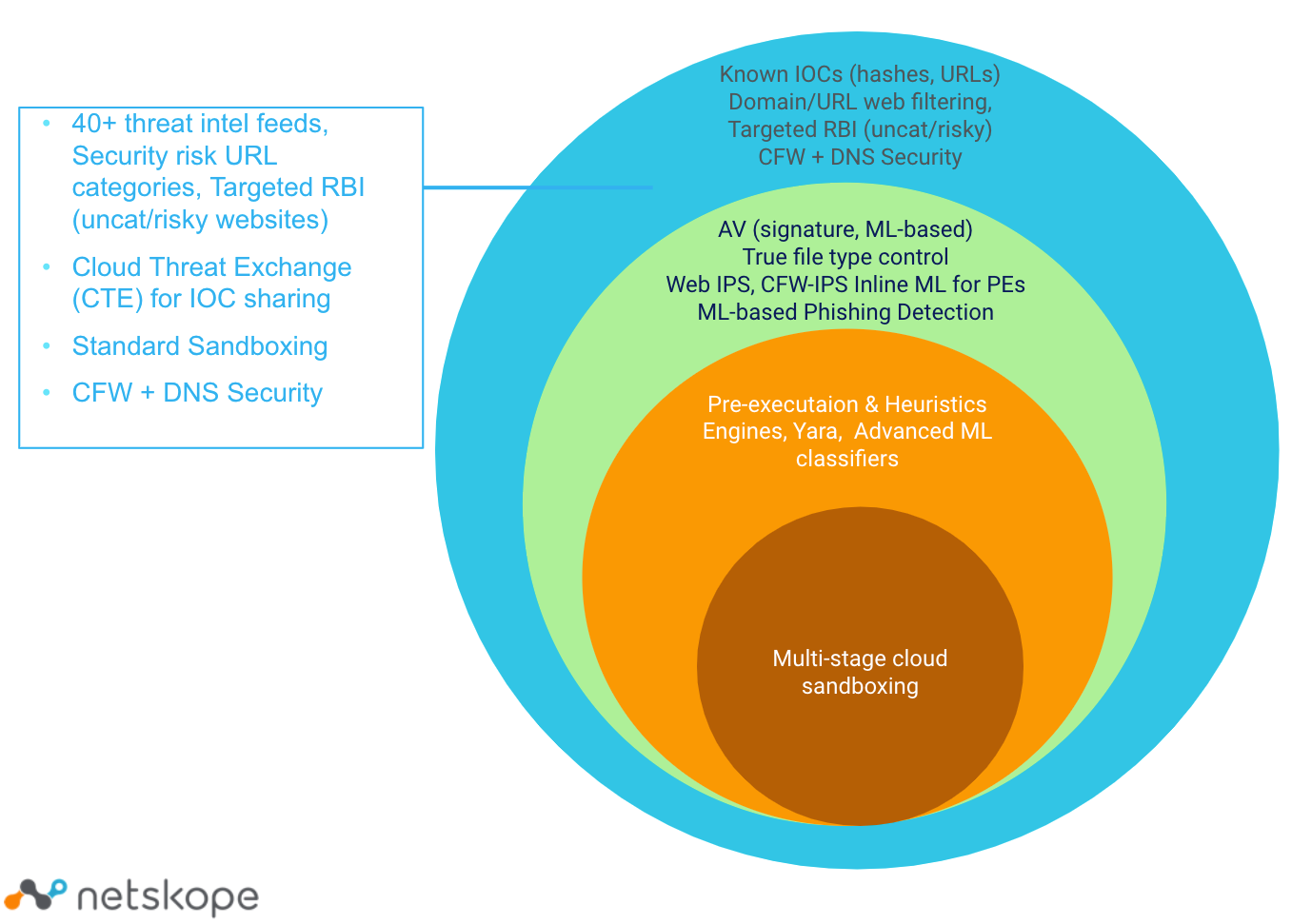
Netskope uses a wide range of threat intelligence feeds, both open source and commercial throughout our products. These include various forms ranging from network and file indicators, to rules and signatures. Since our sources may change frequently, we don't publish a publicly available list.
Netskope uses several own, best-of-breed open-source and paid threat feeds including MalwarePatrol (multiple feeds including phishing, C2, NRD, DGA), VirusTotal (multiple feeds), Webroot, Cisco Talos, Bitdefender, Reversing Labs, OpenPhish, PhishTank, VxVault, AIS/CISA, and many others.
Netskope regularly evaluates and adds new intel feeds for the areas of malware, phishing, C2, and ransomware.
In addition, Netskope partners with Mimecast, FireEye, CrowdStrike, Cybereason, SentinelOne, VMware Carbon Black, ThreatQuotient, and many more to leverage their customer-specific threat intelligence via the Netskope Cloud Threat Exchange (CTE). CTE is extensible, so customers and partners can easily add own feeds, additional threat intelligence partner feeds or integrate with a threat intelligence platform like MISP as needed.
More details are found in the Netskope Cloud Threat Exchange Documentation .