Hi,
Not sure if there's already a similar question posted somewhere,
In the Administration > Audit Log section:
When clicking on the gear, the options to select are "User, Severity, Activity" . There is no option to show comments/notes entered for a specific activity logged.
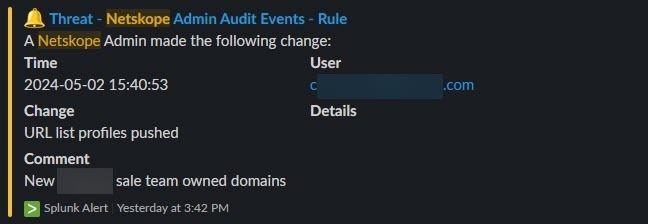
Is there a way to add another column in the Audit Log that can show the comments that were entered when adding/modifying a policy/persona/rule?
It seems odd that while add/changing/modify/removing a rule/policy, you're prompted to add (which is optional) a comment/note before saving/applying a change to an activity performed but never can locate or view the comments in the Audit log.
Are the comments details located in another section of Netskope? Are they retrievable? if yes, will the notes/comments still be linked to the very activity event that was performed at the time when the comments were entered?
or
If not, could this be a consideration as an additional enhancement in the next release/upgrade/patch to the console platform to view this data in the view in the audit log section?