Netskope’s Secure Web Gateway supports HTTP/S traffic on any port. While Netskope’s Cloud Firewall can control any port and protocol, Secure Web Gateway customers may have use cases to block certain high risk apps that use non-HTTP/S ports and protocols. For example, TeamViewer uses port 5398 for communication but fails over to port 443 if port 5398 is unavailable. By default, the Netskope Web Gateway drops non-HTTP/S traffic so administrators can block TeamViewer in its entirety by following the instructions below:
- Navigate to Settings > Security Cloud Platform > Steering Configuration.
- Select the steering config you wish to apply this to.
- Click EDIT in the top right corner.
- Click the NON-STANDARD PORTS tab.
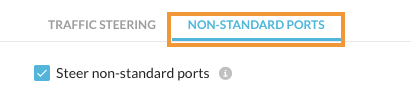
- Check the box next to Steer non-standard ports.
- Create entries and teamviewer.com and *.teamviewer.com with port 5938.
- Click SAVE.
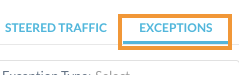
- Change to the EXCEPTIONS tab.
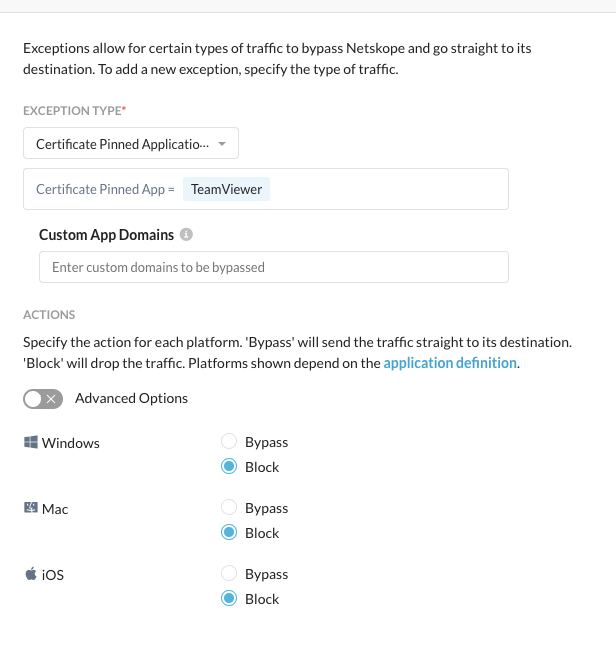
- Add or edit the TeamViewer Certificate Pinned Application and set the action Block.
- Create a Real-time Protection policy to block the Remote Access web category or a custom category that includes both teamviewer.com and *.teamviewer.com. This will also prevent users from accessing the TeamViewer site to download the app.
- To test, update your client configuration and start Teamviewer. You may need to terminate the Teamviewer process and service to ensure a new session is established.
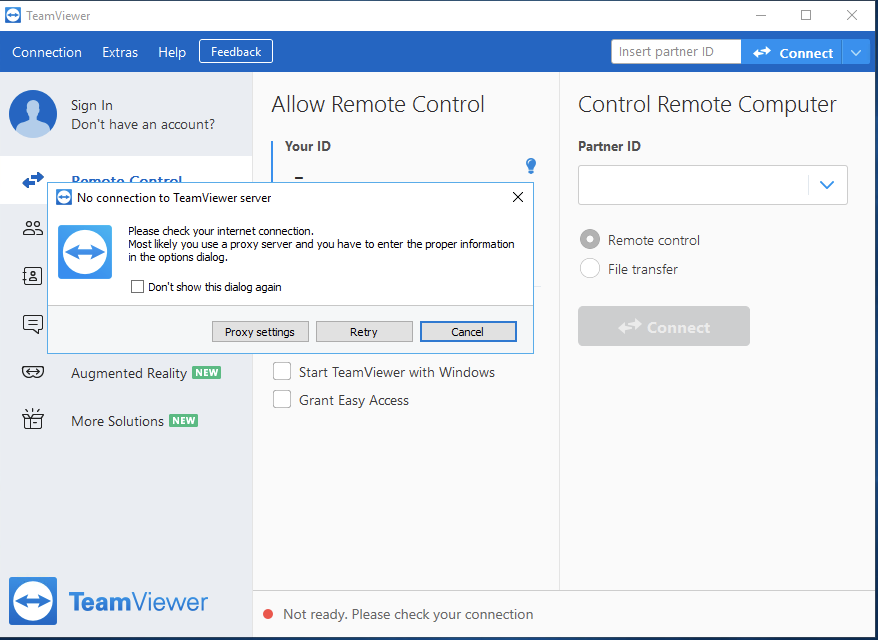
Teamviewer Ports: https://www.teamviewer.com/en-us/trust-center/security/
Steering Configuration: https://docs.netskope.com/en/steering-configuration.html#UUID-eae29f38-85d9-fd13-74c9-077e1ef74513_N1573063388895







