Executive Summary: Trust Zones – Your Key to Zero Trust, Visibility, and GRC
In today's dynamic threat landscape, securing your enterprise goes beyond simple "allow" or "block" decisions for applications. It demands nuanced, risk-adaptive controls. Trust Zones provide a structured framework to categorize applications based on their inherent risk, management oversight, and data criticality. This approach is fundamental to a mature Zero Trust strategy and critical for robust Governance, Risk, and Compliance (GRC).
Netskope dramatically simplifies and empowers this process:
-
Centralized Risk Intelligence: Our App Catalog (over 84,000 cloud apps!) provides deep risk insights and enables custom tagging, allowing you to align apps with your organizational Trust Zones.
-
Dynamic Policy Enforcement: These App Tags feed directly into real-time policies, enabling dynamic, granular controls that adapt without constant policy change control.
-
Unified Risk Orchestration: Risk Exchange integrates App Catalog insights with third-party risk data (from tools like BitSight, Viso Trust, ServiceNow), providing a holistic view of user/device risk that informs application access.
-
Automation & Integration: Comprehensive REST API v2 endpoints allow you to programmatically access and manage App Catalog data, automating classification and integrating with your existing GRC/TPRM platforms.
This post will guide you through understanding, defining, and leveraging Trust Zones, highlighting how Netskope's capabilities facilitate a seamless, secure, and compliant environment.
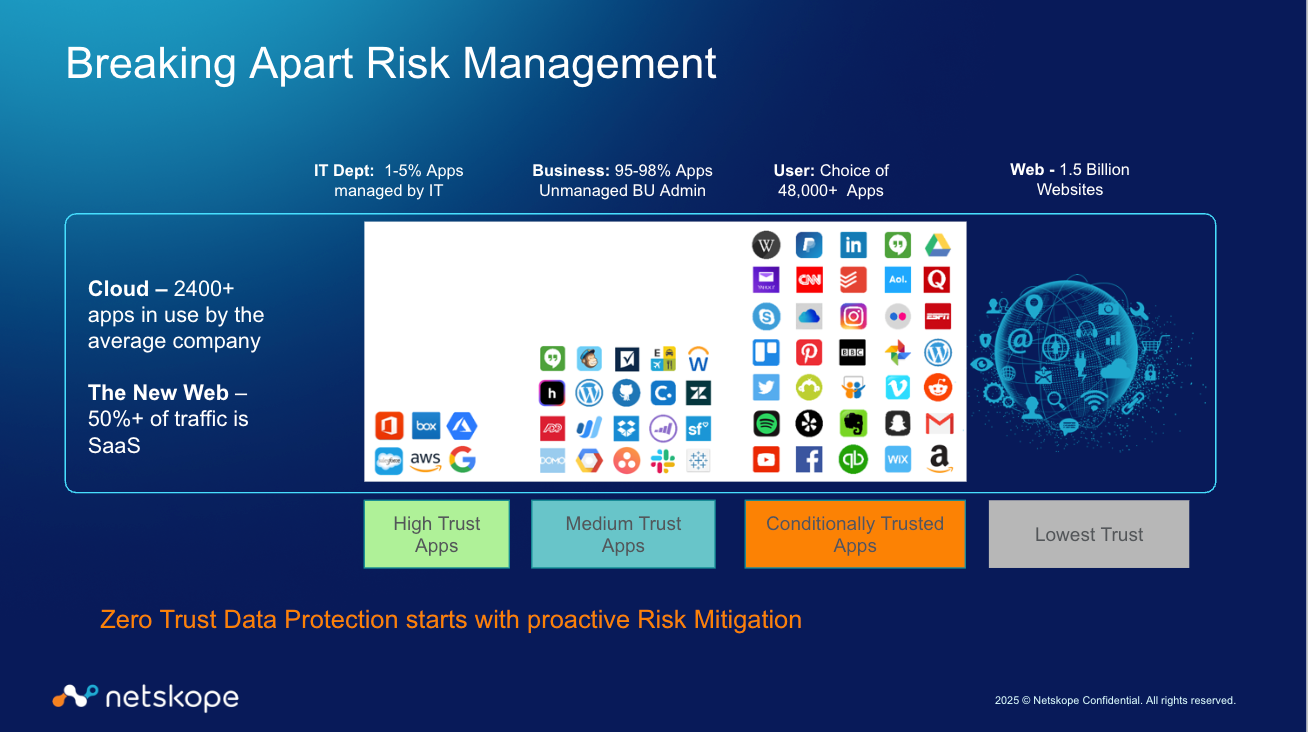
Understanding "Trust Zones" Across Personas
While we refer to them as "Trust Zones" within the context of Netskope's SASE and Zero Trust architecture, security and IT professionals often use related terms that serve a similar purpose, each resonating with specific roles:
-
Trust Zones: This term is commonly embraced by Security Architects and Zero Trust practitioners. It directly speaks to the core Zero Trust principle of explicitly defining and verifying trust levels for applications, irrespective of network location.
-
Vendor Tiers / Risk Tiers / Risk Classifications: These terms are frequently used by GRC Analysts, Third-Party Risk Management (TPRM) teams, and CISOs overseeing overall enterprise risk. They provide a standardized way to assess and categorize external applications (and their associated vendors) based on their inherent security risk, data access, and potential impact.
-
Criticality Classifications: This resonates strongly with IT Operations, Business Unit Leaders, and those involved in Business Continuity/Disaster Recovery (BCDR). It focuses on the impact of an application's compromise or unavailability on business operations, guiding resource allocation and risk prioritization.
Regardless of the terminology used, the underlying goal is the same: to move from a binary "allow/block" decision to a nuanced, risk-adaptive security model that aligns technology controls with business priorities and regulatory obligations.
Defining Trust Zones
Trust Zones represent a risk-based segmentation of applications based on their origin, management oversight, data criticality, and the level of organizational control. They allow for a differentiated approach to security due diligence, policy enforcement, and continuous monitoring, moving beyond a flat "allow or block" stance to a more nuanced, risk-adaptive security model.
Why Trust Zones Matter: Strategic Imperatives & Stakeholder Engagement
Implementing a trust zone approach is not just a technical exercise; it's a strategic imperative that provides significant benefits across the organization, requiring cross-functional collaboration for effective adoption and continuous improvement.
-
The "Why" – Key Benefits:
-
Strategic Alignment: Directly links security policies and resource allocation to the organization's overarching business objectives and risk appetite.
-
Enhanced Efficiency & Resource Optimization: Avoids over-securing low-risk applications and under-securing high-risk ones, directing security spend and effort where it matters most.
-
Robust Compliance & Auditability: Provides clear, documented rationale for security controls, simplifying audits and demonstrating adherence to various regulatory frameworks.
-
Improved User Experience: Balances stringent security with business enablement by applying proportionate controls, reducing friction for legitimate, low-risk activities.
-
Scalability & Agility: Offers a flexible framework to manage the ever-growing sprawl of cloud applications, enabling faster, safer adoption of new technologies.
-
Clearer Communication: Establishes a common language for discussing application risk across technical and non-technical teams.
-
-
Engaging Different Personas in the Process:
-
CISO / Security Leadership:
-
Engagement: Lead the overall strategy, define risk appetite, approve framework and high-level policies. Review comprehensive risk reports and compliance posture.
-
Compliance Relevance: Responsible for overall adherence to frameworks like NIST CSF (Govern, Identify, Protect), ISO 27001 (Overall ISMS), and high-level GDPR/HIPAA/PCI DSS program compliance.
-
-
GRC / Compliance Teams:
-
Engagement: Map trust zones to specific regulatory requirements, assist in documenting controls, conduct risk assessments, and gather audit evidence. Ensure policies satisfy legal and contractual obligations.
-
Compliance Relevance: Directly involved in ISO 27001 (Compliance clause A.18), GDPR (Accountability, Data Protection by Design), HIPAA (Administrative Safeguards), PCI DSS (Control Validation).
-
-
IT Operations / Application Owners:
-
Engagement: Provide deep insights into application functionality, dependencies, and data flows. Actively participate in categorizing applications, testing policies, and defining operational procedures for new app onboarding based on their assigned zone.
-
Compliance Relevance: Focus on NIST SP 800-53 (e.g., AC-3 Access Enforcement, CM-2 Baseline Configuration), ISO 27001 (A.14 System Acquisition, Development & Maintenance) for ensuring applications are secured according to their classification.
-
-
Business Unit Leaders:
-
Engagement: Advocate for business-critical applications, define acceptable use scenarios, and provide context on the type of data handled. Understand the implications of trust zone assignments on their operations and innovation. Help balance risk acceptance with security controls.
-
Compliance Relevance: Ensure their processes and application usage align with GDPR (Purpose Limitation, Data Minimization), HIPAA (Use and Disclosure rules), and internal data governance policies.
-
-
Legal Counsel:
-
Engagement: Review policy language, advise on legal implications of data handling within different zones (e.g., cross-border data transfer, privacy concerns), and ensure contractual agreements with third-party app providers reflect the determined trust level and associated security requirements.
-
Compliance Relevance: Critical for interpreting and applying GDPR (Articles 5, 6, 32), CCPA, and industry-specific regulations related to data protection and contractual terms.
-
-
By engaging these diverse stakeholders collaboratively, organizations can define and manage their application trust zones effectively, leading to a more secure, compliant, and operationally efficient environment.
Netskope's Core Enablers for Trust Zones: Centralizing Risk Intelligence & Orchestration
Netskope provides the intelligence and control plane necessary to implement and manage your application Trust Zones effectively.
Application Risk (App Catalog - formerly Cloud Confidence Index - CCI)
Netskope's App Catalog is a critical capability that empowers security and GRC personas to effectively implement and manage these Trust Zones. It provides a vast, continuously updated intelligence repository that serves as your central source of truth for application risk.
-
What can be reviewed in the App Catalog: For over 84,000 cloud applications, you can review detailed attributes including:
-
Risk Score: A quantitative assessment of the application's security posture.
-
Categories: The App Catalog provides a 1:1 app to category mapping, with both primary and secondary classifications (e.g., "Collaboration," "Cloud Storage").
-
View Specific App Details: Clicking on any app opens a dedicated page for in-depth research, displaying app-specific information such as:
-
Certificates and Standards: Understand the cloud service’s compliance and data center certifications. This helps comply with regulations and industry guidance.
-
Data Protection: Details on data classification, encryption, security headers, file sharing, and public key pinning. Ensures policies on content, data protection standards, sharing restrictions, and guards against attacks.
-
Access Control: Information on role-based controls, IP filtering, password best practices, SSO/AD hooks, MFA, and supported devices. Allows comparison and confirmation of access control levels.
-
Auditability: Details about Admin audit logs, user audit logs, and data access logs, indicating their availability for traceability, investigations, or regulatory compliance.
-
Disaster Recovery and Business Continuity: Capabilities like status/change/upgrade notifications, availability, and hosting providers. Provides confidence in business continuity and helps determine recovery steps in case of service disruption.
-
Legal and Privacy: How the cloud service handles data ownership and privacy via browser or mobile. Identifies weak spots that could lead to potential data breaches by understanding employee privacy handling.
-
Attack Surface Management: Indicates if a cloud service has been found vulnerable to over 60 different vulnerabilities including OWASP Top 10. This ensures your organization is not susceptible to attacks that could lead to a data breach, brand damage, or loss of trust. (Note: OWASP ZAP is used for passive vulnerability scans.)
-
-
-
Quick Access to Event Data: Relevant event data and user activity logs for each application are available for analysis within Netskope's analytics capabilities, providing crucial insights for monitoring and reporting.
-
Value of App Tagging for Classification: The App Catalog provides powerful App Tagging capabilities. This allows GRC Analysts, Security Architects, and Business Unit Leaders to classify the applications in use within their organization by applying custom tags that align directly with their defined organizational Trust Zones (e.g., "Corp-High-Trust," "BU-Conditional," "Monitor-Only"). These tags are invaluable for formalizing internal risk postures and policies.
-
Usability of App Tags in Real-time Policy: The true power of App Tagging lies in its seamless usability within Netskope's real-time policy engine. Policies are created by administrators, and once these policies are in place, changes to App Tags for different applications are dynamically applied without requiring policy change control. This allows for agile, continuous classification as your third-party risk function or other personas work through the process of app classification, ensuring policies always reflect the latest risk assessments without operational friction.
-
Criticality for Advanced Analytics & Reporting: Leveraging App Tagging to embed your organizational trust zone classification directly into data streams (logs and events) is critical for advanced analytics. This enables robust reporting with Advanced Analytics capabilities to track and report on managed vs. unmanaged risk, providing clear visibility to CISOs and boards on security coverage aligned with their established risk appetite. It transforms raw data into actionable insights for continuous risk management.
-
Value for Third-Party Risk Management (Risk Exchange Integration): The insights from the App Catalog are significantly amplified through Netskope's Risk Exchange capability. Risk Exchange facilitates crucial data exchange with existing Third-party Risk (TPRM) capabilities within your broader security ecosystem. Only an Admin can configure Application Risk Exchange plugins, which provide the library of supported integrations. This allows for flexible configuration with multiple plugins to the same or different systems for diverse workflows. By ingesting App Catalog risk scores and tags, alongside risk scores from other security tools (e.g., EDR, vulnerability management, identity platforms) from plugins like Viso Trust, BitSight, or ServiceNow, Risk Exchange creates a unified, holistic view of user and device risk. This aggregated risk intelligence can then drive automated, highly-focused orchestration actions (e.g., adjust user access policies for specific apps based on a heightened overall risk score) to rapidly reduce exposure, providing a seamless bridge between application security posture and overall enterprise risk management.
-
Programmatic Access with REST API v2 Endpoints: The App Catalog's comprehensive data and tagging functionality are fully accessible via its REST API v2 endpoints, enabling powerful automation and integration with other enterprise systems. This programmatic access allows organizations to:
-
Retrieve granular application intelligence: Fetch detailed app information, categories, domains, and PDF reports programmatically (e.g.,
GET /api/v2/services/cci/app,GET /api/v2/services/cci/apps/all,GET /api/v2/services/cci/domain,GET /api/v2/services/cci/pdf). -
Automate tag management: Create, update, and delete custom App Tags at scale, even based on attribute rules or dynamic app lists (e.g.,
POST /api/v2/services/cci/tags,PATCH /api/v2/services/cci/tags/{tag},DELETE /api/v2/services/cci/tags). This ensures your Trust Zone classifications remain current and consistent. -
Integrate with GRC/TPRM platforms: Push Netskope's application risk context directly into third-party risk management tools, CMDBs, or GRC platforms for centralized risk assessment and reporting.
-
Build custom dashboards and reports: Leverage the API to pull App Catalog data into business intelligence tools for tailored risk insights. You can also get lists of all tags and supported attributes for rule-based tags (e.g.,
GET /api/v2/services/cci/tags/all,GET /api/v2/services/cci/tags/rules,GET /api/v2/services/cci/tags/supportedattributes).
-
The Four Trust Zones: Applying Contextual Controls
Now, let's explore Netskope's approach to application trust zones in detail:
1. IT High Trust Zone (High Trust Applications)
-
Origin & Governance: These applications are primarily purchased, provisioned, and formally managed directly by your IT department. They undergo rigorous security assessments, due diligence, and vendor risk management processes.
-
Nature: Considered sanctioned, highly trusted, and explicitly allowed applications, forming the backbone of your corporate operations. They are typically subject to comprehensive contractual agreements and service level agreements (SLAs) with security clauses.
-
Purpose: Intended for the majority of users to conduct their primary, mission-critical business activities, often involving the organization's most sensitive or regulated data.
-
Security Implications (GRC Perspective): Policies for these apps are designed for secure, unhindered access, with a focus on deep inspection for data loss prevention, threat detection, and continuous compliance monitoring. The inherent risk is managed down to an acceptable residual risk through robust controls, extensive auditing, and strict change management.
2. Business or Medium Trust Applications
-
Origin & Governance: These applications are typically driven or purchased by individual business units (often through a formalized procurement process, but with less direct IT management than High Trust apps) to address specific operational needs.
-
Nature: While still sanctioned and allowed, they may have undergone a lighter due diligence process or serve a specific set of users, implying a slightly higher inherent risk profile than IT-managed core applications. Contractual security assurances may vary.
-
Purpose: Acquired for specific use cases relevant to a particular business unit's operations (e.g., specialized marketing automation tools, niche project management software for a specific team).
-
Security Implications (GRC Perspective): Policies are often granular, allowing specific activities while potentially restricting others or requiring additional security scrutiny based on the data they handle and their specific use case. The organization accepts a defined level of risk tolerance for these applications, which is mitigated through targeted controls, ongoing monitoring, and clear ownership by the business unit for security adherence.
3. User or Conditional Trust Applications
-
Origin & Governance: These applications are primarily driven by individual users for personal productivity, collaboration, or convenience, often entering the environment without formal IT procurement. Historically, these might be termed "shadow IT" or personal use applications.
-
Nature: The organization's stance on these applications is crucial and can vary widely (e.g., blocked outright, allowed with restrictions, or monitored). This category often encompasses the largest volume of applications due to diverse user-driven use cases, presenting a higher inherent risk due to lack of direct oversight.
-
Policy Considerations (GRC Perspective): Given their varied nature and origins, policies here are complex and conditional. The focus is on risk acceptance with significant mitigation if allowed, or strict risk avoidance if blocked. This demands robust continuous monitoring and clear incident response processes.
-
Data Loss Prevention (DLP) Impact: If these applications are permitted, it significantly drives the maturity requirements of your Data Loss Prevention (DLP) program. Organizations will need to define specific, context-based identifiers and robust DLP policies to detect and prevent sensitive corporate information from being transferred to these personal or unsanctioned applications. This aligns with Zero Trust's principle of protecting data regardless of its destination and is critical for regulatory compliance where data residency or sharing restrictions apply.
4. The Web (Lowest Trust Zone)
-
Scope & Governance: Encompasses the vast majority of sites on the public internet—everything outside of the explicitly defined applications and instances. It represents the highest inherent risk due to unknown content, constantly evolving threats, and lack of direct control.
-
Nature: This is designated as the lowest trust zone, implying an inherent assumption of risk and necessitating pervasive security controls. No formal due diligence or contractual agreements exist.
-
Policy Application (GRC Perspective): Security for this zone is primarily managed through broad threat policies, acceptable use policies, and basic web filtering. The objective is risk avoidance where possible (blocking known bad/unwanted categories) and risk transfer/mitigation through active threat protection for all allowed Browse.
-
Control Mechanism: Policies are generally coarse-grained, with category-based controls being the primary mechanism for managing access and mitigating general web-borne threats.
Supporting Contextual Layers (Foundational Visibility Reviewed in Post 3)
While the App Catalog and Trust Zones provide application-specific context, remember that these are built upon broader layers of visibility, enabling comprehensive Zero Trust enforcement. These layers, previously detailed, include:
-
User, Group, and Organizational Unit (OU) Information: For Identity-Centric Zero Trust.
-
Device Risk and Device Information: For Conditional Access and Risk-Adaptive Policies.
-
URL Categorization: For Foundational Web Filtering.
-
Application-Based Visibility (App Discovery & Differentiation): Critical for Deep Traffic Inspection (via SSL Decryption).
-
Application Instance Detection: For Data Separation and Control.
-
Application Activity Detection: For Granular Policy Enforcement and Insider Threat Detection.
-
User Risk-Based Visibility (UEBA): For Proactive Threat Detection and Adaptive Trust Decisions.
-
Data Risk (Leveraging Data Loss Prevention - DLP): For Critical Data Protection and Compliance Enforcement.
-
Policy Action Context: For Effective, Adaptive Enforcement.
By systematically building and leveraging these layers of context, organizations achieve a profound understanding of their digital environment, enabling precise security enforcement, meeting critical compliance requirements, and extracting maximum value from their Netskope SASE platform, all within a robust Zero Trust framework.
Further Reading
-
Netskope Cloud Confidence Index (App Catalog) Documentation: Detailed documentation on the App Catalog and its capabilities.
-
Netskope Risk Exchange: Learn more about orchestrating actions based on unified risk scores and integrating with other security tools.







