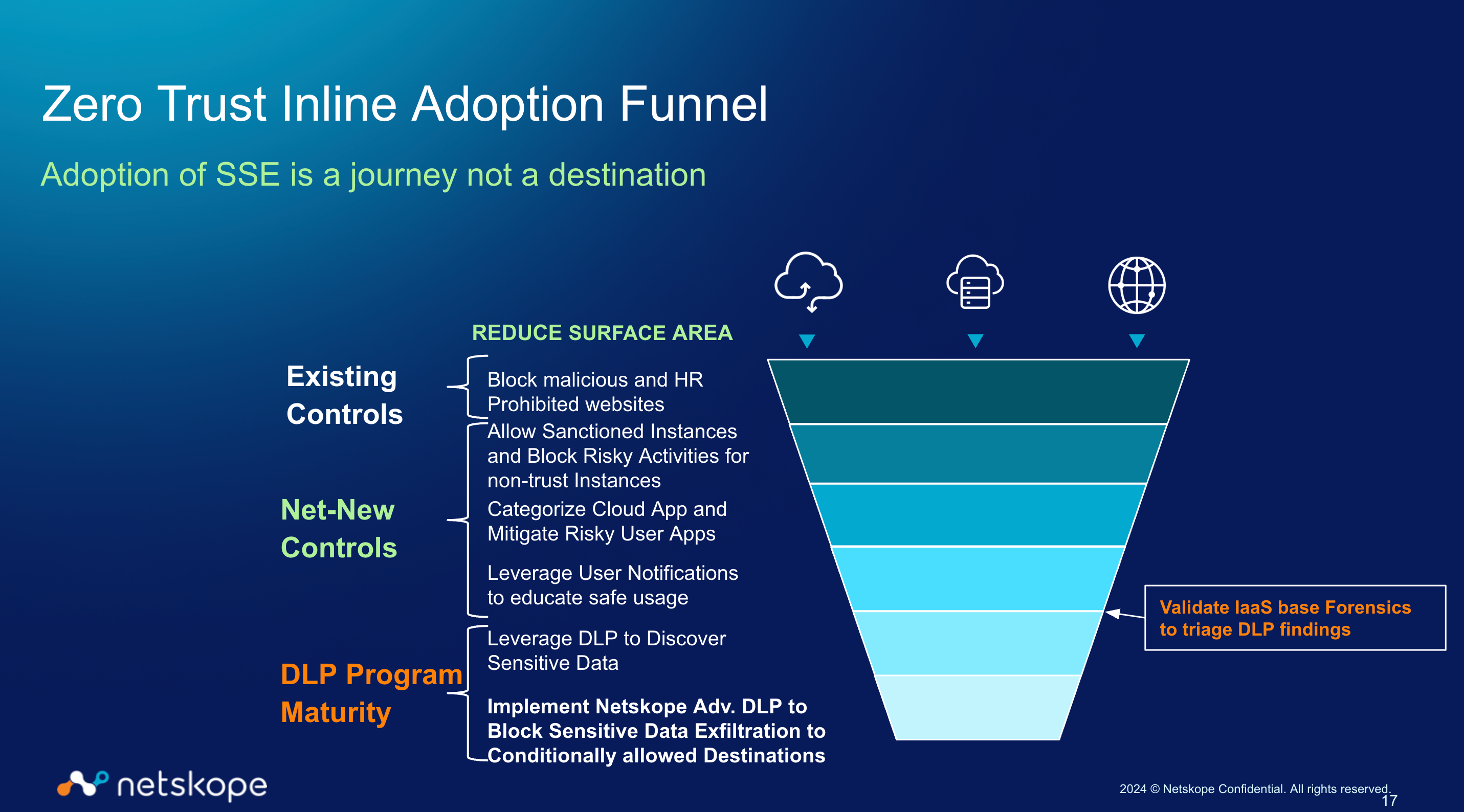
Implementing Zero Trust is a journey, not a single destination. The Netskope Zero Trust Inline Adoption Funnel provides a structured, progressive approach to gradually implementing Netskope's powerful security capabilities. This strategy is typically broken into the following key pillars or stages, building complexity and control as you gain confidence and visibility, while clearly defining roles and supporting compliance:
Successful security programs, and the adoption of advanced models like Zero Trust, fundamentally rely on the harmonious interplay of people, process, and tooling. When one or more of these critical components is missing or misaligned – whether it's a lack of skilled personnel, undefined workflows, or unoptimized technology – the efficacy of your security initiatives, and thus the successful adoption of this vital Zero Trust model, will be severely hampered. This funnel, therefore, emphasizes the comprehensive engagement required across your organization.
1. Threat Pillar: Your Foundational Defense This is the initial, often primary, focus for organizations adopting the Zero Trust model with Netskope. It's about establishing baseline protection against the most immediate and well-understood risks, a fundamental step in building explicit trust.
-
Core Focus: Implementation of robust threat policies to protect against known malicious content, malware, phishing, and sophisticated attacks. This includes enforcing HR policies related to data handling and system usage, and applying acceptable use policies governing how network and application resources can be utilized.
-
Zero Trust Connection: This pillar establishes the "never trust, always verify" mindset at the most fundamental level, preventing known bad actors or activities from gaining any implicit trust, and reducing the attack surface.
-
Supporting Compliance Requirements:
-
NIST Cybersecurity Framework (CSF): Directly supports the "Protect" (PR) and "Detect" (DE) functions, particularly PR.AT (Protective Technology) and DE.CM (Continuous Monitoring).
-
ISO 27001/27002: Aligns with controls like A.12.2 (Protection from malware), A.12.6 (Vulnerability management), and A.13 (Secure development).
-
PCI DSS: Contributes to requirements like 5 (Protect all systems from malware) and 11 (Regularly test security systems).
-
-
Well-Recognized Program Adoption Strategies:
-
Low-hanging fruit approach: Start with easily definable and universally accepted blocks (e.g., malware, known bad IPs/domains).
-
Default-deny mindset: While not fully implemented at this stage, the principle of blocking what is clearly harmful aligns with this.
-
Phased rollout: Begin with a pilot group, then expand, monitoring impact.
-
-
Key Stakeholders/Functions Involved:
-
CISO/Head of Security: Sets strategy, approves policy risk.
-
Security Operations (SecOps) Team: Implements, monitors, and responds to alerts.
-
Network Team: Ensures proper traffic steering and connectivity.
-
HR/Legal: Provides input on acceptable use and policy enforcement.
-
2. Risk Management Pillar: Shaping Behavior & Controlling Applications As more traffic is successfully steered into the Netskope cloud and SSL decryption becomes active, this pillar concentrates on actively managing application-related risks and shaping user behavior based on deeper visibility. This moves beyond simple blocking to intelligent, context-aware control.
-
Core Focus: Implementing policies to prevent unauthorized exfiltration of sensitive data, whether it's intellectual property, personally identifiable information (PII), or financial data. This involves discovering where sensitive data resides, identifying patterns, and applying controls.
-
Key Activities and Progressive Steps:
-
Sanctioning Instances: As traffic reveals specific instances of applications (e.g., corporate vs. personal instances of a cloud storage service), it's crucial to tag these. This enables the creation of explicit "allow" policies for corporate-sanctioned applications, especially for top-tier, business-critical services, aligning with Zero Trust's explicit access principles.
-
Proactive Blocking of Risky Activities: Target and prevent access to, or specific activities within, sites and applications known to be unacceptable or high-risk. Netskope's Cloud Confidence Index (CCI) engine (covering tens of thousands of applications) can be leveraged for this, allowing risk-based access decisions.
-
Maturing Risk Posture with User Notifications: Educate users in real-time about safe and compliant application usage, reinforcing corporate policies. For example, if an employee attempts to upload corporate data to a personal cloud account, a customizable notification can prompt them to use the sanctioned corporate application, offering education while maintaining control. This fosters a security-aware culture, crucial for a mature Zero Trust approach.
-
-
Zero Trust Connection: This pillar moves beyond basic threat blocking to apply adaptive, context-aware policies based on application risk and user behavior, refining the "verify, then trust" continuous assessment for every access request.
-
Supporting Compliance Requirements:
-
NIST CSF: Enhances the "Protect" (PR.AC - Access Control) and "Respond" (RS.AN - Analysis) functions by providing granular context.
-
ISO 27001/27002: Supports A.9 (Access Control), A.13 (Communications Security), and A.18 (Compliance with Legal & Contractual Requirements) by controlling cloud app usage.
-
GDPR: Contributes to data protection by design and default, by managing data movement to unsanctioned cloud apps.
-
-
Well-Recognized Program Adoption Strategies:
-
Visibility-first: Initially monitor app usage without blocking to understand organizational behavior.
-
Categorization & Risk Scoring: Use tools like Netskope CCI to classify apps and prioritize risky ones.
-
User education campaigns: Roll out policies with clear communication and notifications, transforming users into an active part of the defense.
-
-
Key Stakeholders/Functions Involved:
-
CISO/Head of Security: Defines risk appetite for cloud apps.
-
Application Owners/Business Units: Provide input on business-critical applications and usage patterns.
-
Security Operations (SecOps) Team: Configures policies, monitors for violations, analyzes user justifications.
-
Internal Communications/HR: Develops and deploys user awareness campaigns.
-
3. Data Loss Prevention (DLP) Pillar: Protecting Your Crown Jewels This pillar represents a more advanced, data-centric stage in the Zero Trust adoption funnel, focusing on the identification and protection of sensitive data across various egress points. It represents the ultimate enforcement of data protection principles within Zero Trust.
-
Core Focus: Implementing policies to prevent unauthorized exfiltration of sensitive data, whether it's intellectual property, personally identifiable information (PII), or financial data. This involves discovering where sensitive data resides, identifying patterns, and applying controls.
-
Typical Sequencing: DLP controls are most effectively implemented after foundational threat prevention and initial risk management policies are well-established, as the app context allows for conditional DLP.
-
Essential Prerequisites for Effectiveness: A clear delineation between non-allowed/prohibited sites and applications and allowed/sanctioned ones is fundamental. This categorization is crucial for determining where and how DLP policies should conditionally scan for, and apply controls to, specific classifications of sensitive data.
-
Key Dependency for Granular DLP: Integration with an IAS (Infrastructure as a Service) based forensics DLP location. Such integration allows for the storage and in-depth, granular analysis of DLP detection events and associated metadata/context. This facilitates accurate determination of whether detected data genuinely constitutes sensitive information that requires protection according to the organization's data governance policies, distinguishing true positives from false positives.
-
Zero Trust Connection: This pillar embodies the Zero Trust principle of protecting the resource (data) directly, applying continuous verification and least privilege to sensitive information regardless of user, device, or location. It represents the explicit enforcement of data access boundaries.
-
Supporting Compliance Requirements:
-
GDPR: Directly supports Article 32 (Security of processing) and principles like data minimization.
-
HIPAA: Essential for protecting Protected Health Information (PHI) against unauthorized disclosure (e.g., 45 CFR § 164.312(c) - Integrity).
-
PCI DSS: Supports Requirement 3 (Protect Stored Cardholder Data) and Requirement 10 (Track and monitor all access to network resources and cardholder data).
-
NIST CSF: Enhances "Protect" (PR.DS - Data Security) and "Detect" (DE.AE - Anomalies and Events) functions.
-
ISO 27001/27002: Aligns with A.13 (Communications Security) and A.18 (Compliance with Legal & Contractual Requirements related to data leakage prevention).
-
-
Well-Recognized Program Adoption Strategies:
-
Data Classification First: You can't protect what you don't identify. A robust data classification scheme is paramount.
-
Phased Policy Rollout: Start with monitor-only policies, then move to block for specific data types or destinations.
-
Collaboration with Data Owners: Critical for defining sensitive data patterns and acceptable use.
-
-
Key Stakeholders/Functions Involved:
-
CISO/Head of Security: Defines data protection strategy and risk tolerance.
-
Data Governance / Privacy Officer: Defines sensitive data, provides legal/compliance guidance.
-
Security Operations (SecOps) / Incident Response Team: Investigates DLP incidents, manages forensics.
-
Business Unit Data Owners: Identifies and classifies sensitive data specific to their operations.
-
Legal & Compliance: Ensures policies meet regulatory requirements.
-
By progressively implementing these pillars, organizations can systematically build a robust Zero Trust security posture with Netskope, ensuring comprehensive protection, proactive risk management, and strong compliance across their entire digital estate.
Next, we'll categorize applications through Trust Zones to further refine risk management!







