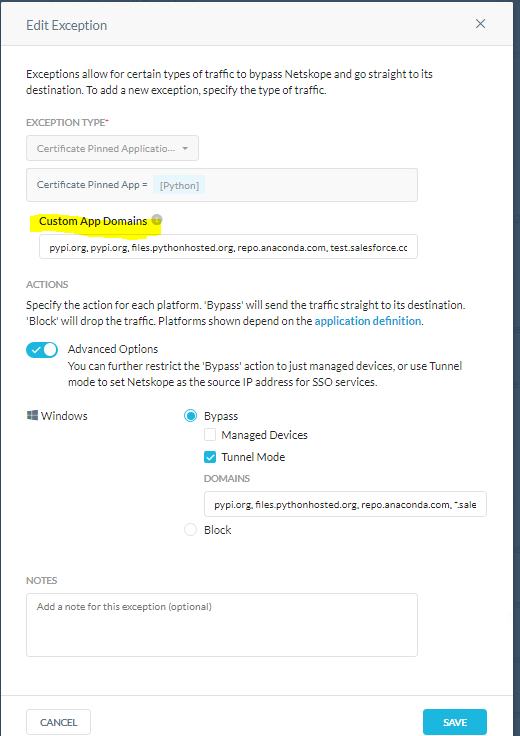
Since the upgrade to version 85, I started to notice it doesn't look as if cert pinned application exceptions recognize or apply tunnel exclusions any more. I'm opening a case with Support but I wanted to reach out here to see if anyone else experienced anything similar first. There is a exception for python.exe and if i use the tunnel settings it'll bypass any connections made to those domains but attempt to intercept everything else.
For Example:
Python.exe > Tunnel Mode: pypi.org and Pythonhosted.org