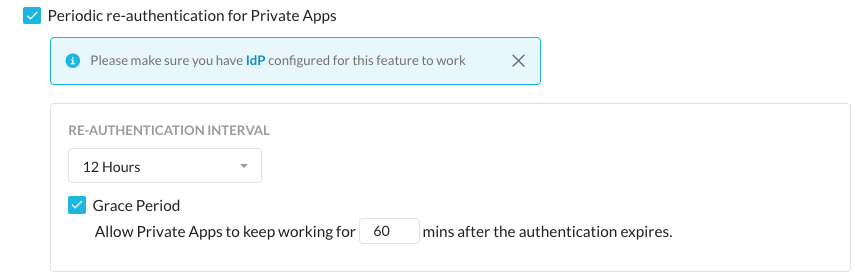
Netskope Private Access (NPA) is a Zero-Trust Network Access solution that provides seamless access for users accessing applications. One of the Zero-trust capabilities within NPA, Periodic Reauthentication, is based on an integration with your enterprise Identity Provider (IDP) such as Azure AD or Okta. This capability allows the Netskope client to challenge the user via your Identity Provider for credentials and MFA to maintain or activate access to internal applications. Administrators configure intervals for groups or OUs based on the security posture required. For example, the below configuration would require a user to authenticate to my IDP every 12 hours with a 1 hour grace period before access would be revoked:
Depending on your enterprise’s security requirements, you may wish to always enforce MFA or specific access requirements. This becomes a challenge if your Identity Provider caches sessions for a period of time which is increasingly common. The mini browser used by the Netskope client varies by operating system (Edge for Windows, Safari for Mac, etc). If your user has a cached session for the IDP within one of these browsers, it may transparently reauthenticate the user. If you’d like to change this behavior, many IDPs support app specific configurations that enforce MFA or other controls every time regardless of cached sessions. Below are instructions for two of the most common Identity Providers, AzureAD and Okta. These settings may also impact your SAML forward proxy authentication if you are using IPSEC or GRE steering to Netskope.
AzureAD
AzureAD will typically cache user sessions by default so periodic reauth will use this cached session by default as well. Administrators can configure a Conditional Access policy scoped to the Netskope User Enrollment and Authentication app. This Conditional Access Policy will require authentication to the Netskope app every time the user accesses this application which occurs when Periodic Reauth is triggered. Example configuration steps for this policy are below. Consult with your AzureAD or Microsoft 365 admin to ensure these policies will not conflict with other Conditional Access Policies.
- Navigate to portal.azure.com.
- Open Conditional Access Policies by entering Conditional in the search bar.
- Click Create new policy.
- Enter a descriptive name in the Name field.

- Click No target resources selected.
- Check the Select apps option.
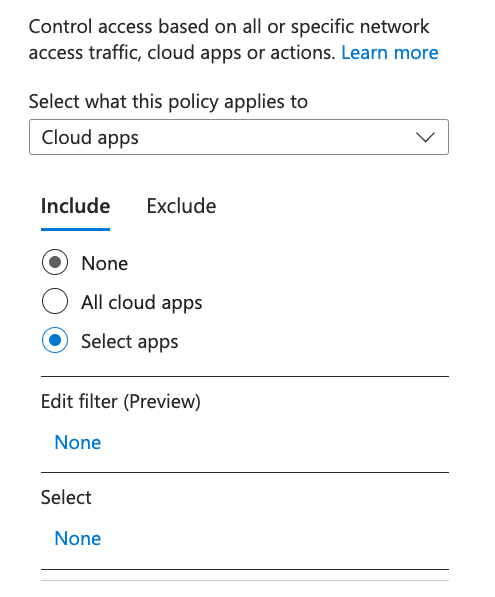
- Click None under the Select option.
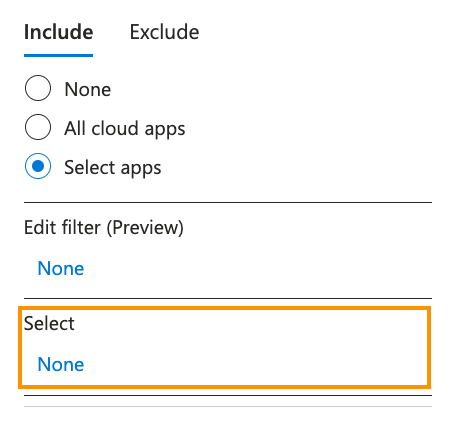
- Search for and check the box next to your Netskope authentication app.
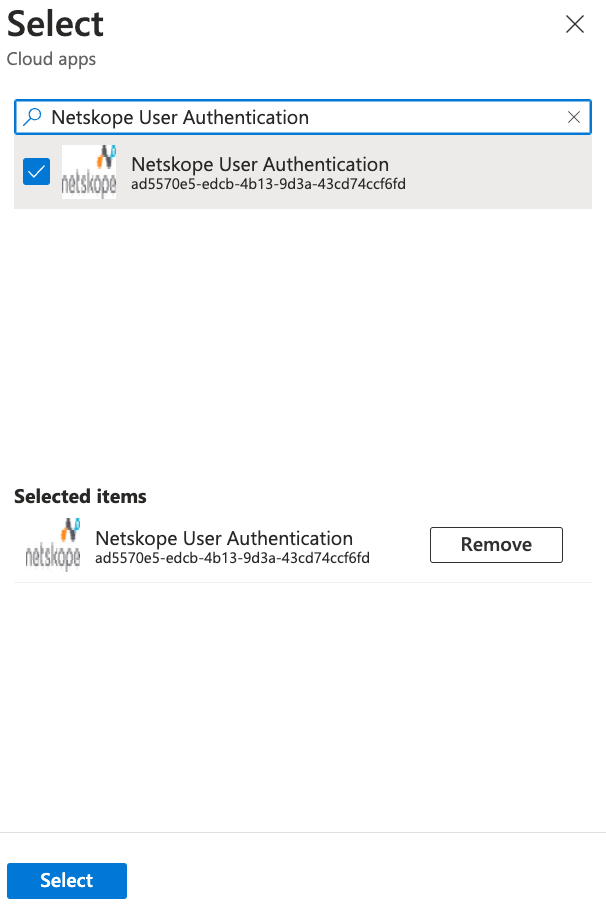
- Click Select.
- Click 0 controls selected under the Session section.

- Check the box next to Sign-in frequency.
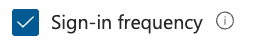
- Configure the interval for periodic reauthentication. The example below uses 1 hour for a shorter demo interval. You can select a longer interval but the interval must be shorter than the reauthentication interval configured in Netskope. For example, if Netskope is configured to reauth every 12 hours, ensure this value is 11 hours or lower.
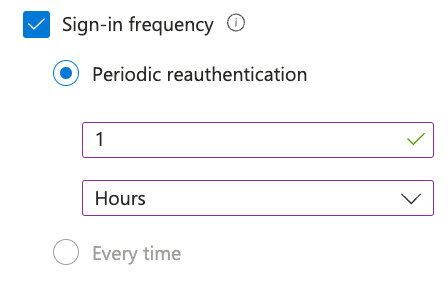
NOTE: You can also now select the every time option which will force the user to enter their password and MFA every reauth. This may behave differently depending on your other Conditional Access policies and Azure AD configurations.
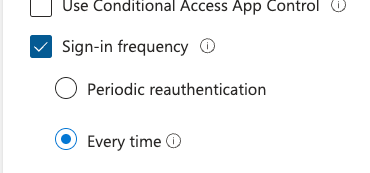
- Click Select.

- Enable the policy and click Create.
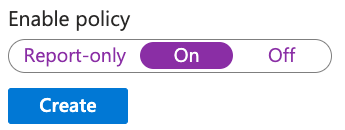
With this enabled, your users should be prompted to authenticate and perform any other checks (Device Compliance, MFA, location based policies, etc) every time Netskope reauth is triggered.
Okta
Okta supports more frequent authentication policies to specific apps via app sign-on policies. Follow the steps below to configure a more frequent reauthentication policy. The steps below are a sample configuration. Consult with your Okta administrator to ensure this does not conflict with existing sign on policies.
- Navigate to your Okta admin console.
- Click Applications to expand the menu.

- Click Applications.
- Select your Netskope application. The name may vary.

- Click Sign On.

- Scroll down to Sign On Policy and click Add Rule.
- Enter a name for your rule under Rule Name.

- Scroll down to Actions and check the box next to Prompt for factor. Leave Every sign on checked.
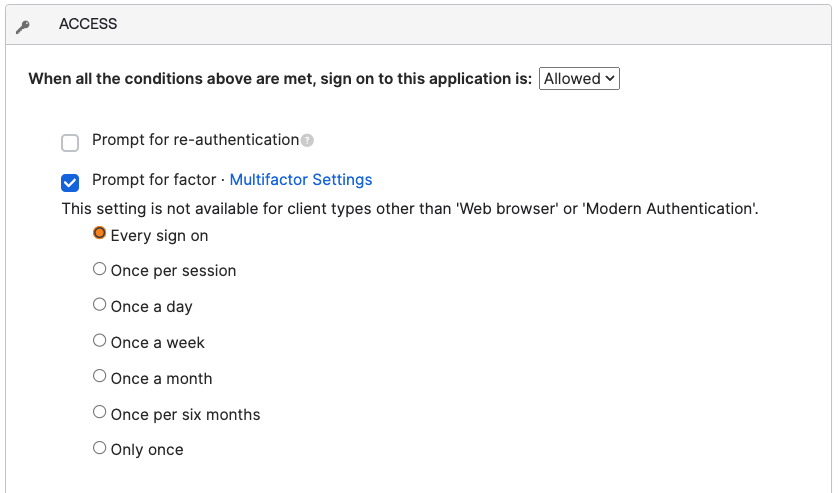
- Click Save.

Users should now be prompted for MFA every time they attempt to reauth, regardless of cached sessions. You can optionally alter this policy to require MFA on an interval or to prompt for credentials and to prompt for MFA.










