Netskope Global Technical Success (GTS)
UrbanVPN: How to Block with Netskope Effectively
Netskope Cloud Version - 129
Objective
How to restrict UrbanVPN access via Netskope
Prerequisite
Netskope SWG/Next-Gen SWG & Netskope Cloud Firewall license is required
Context
UrbanVPN is a free P2P and proxy application. End-users at customer end may install the UrbanVPN extension on their Google Chrome or other browsers to bypass Netskope’s controls. This document explains how to block UrbanVPN using Netskope.
Do You Know?
-
As of Aug 26, 2025, Netskope recognizes UrbanVPN as a Cloud Application, but no pre-defined cloud app connector is available.
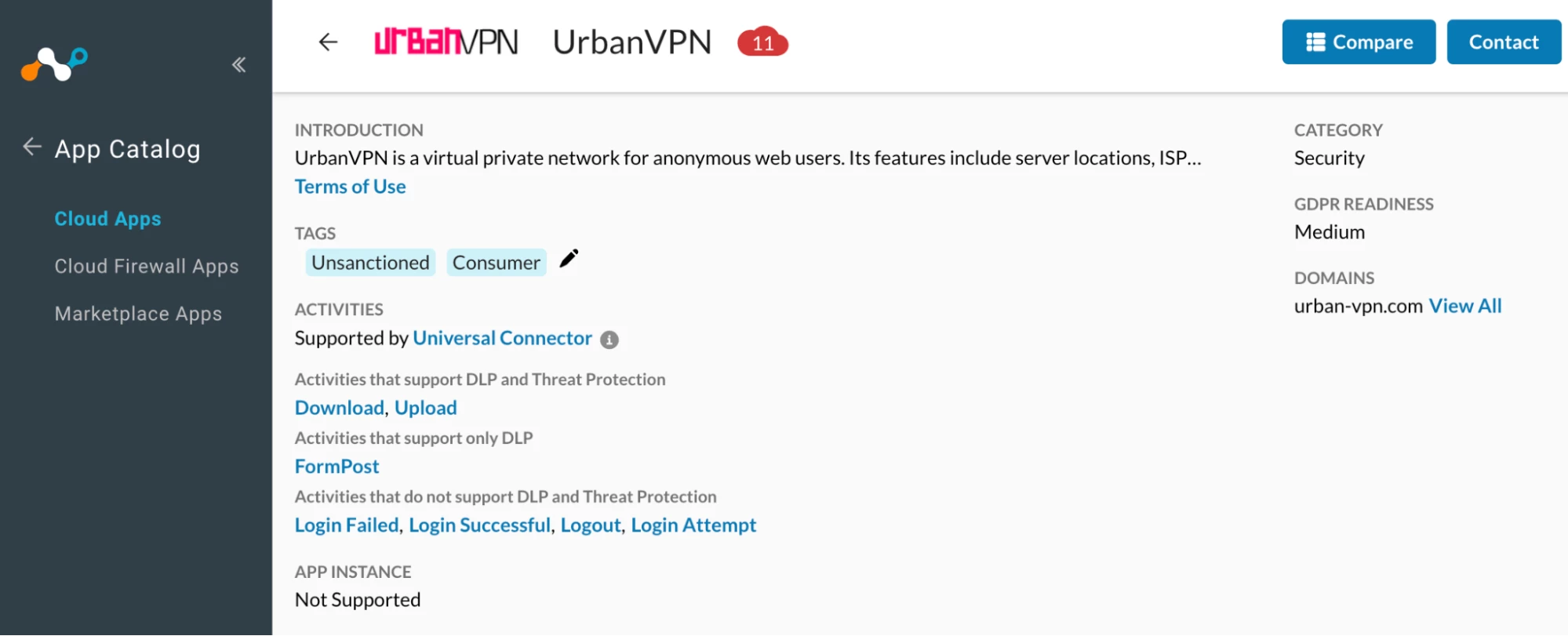
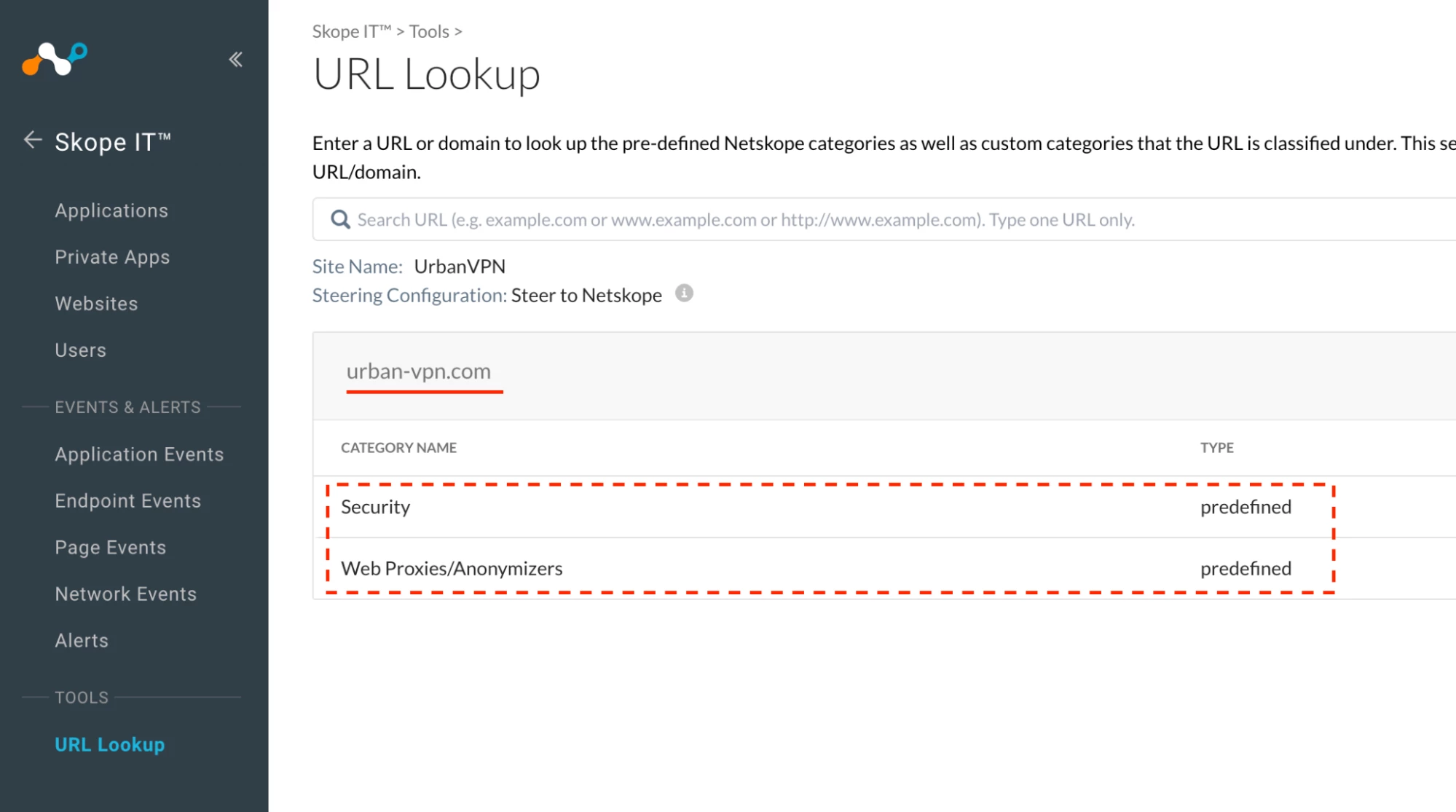
It is important to note that the pre-defined cloud app is with Universal Connector support.
-
It is essential to understand the behavior and traffic patterns of Urban VPN. For this testing, I am using Google Chrome as the test browser.
i. Access Chrome Web Store - Link
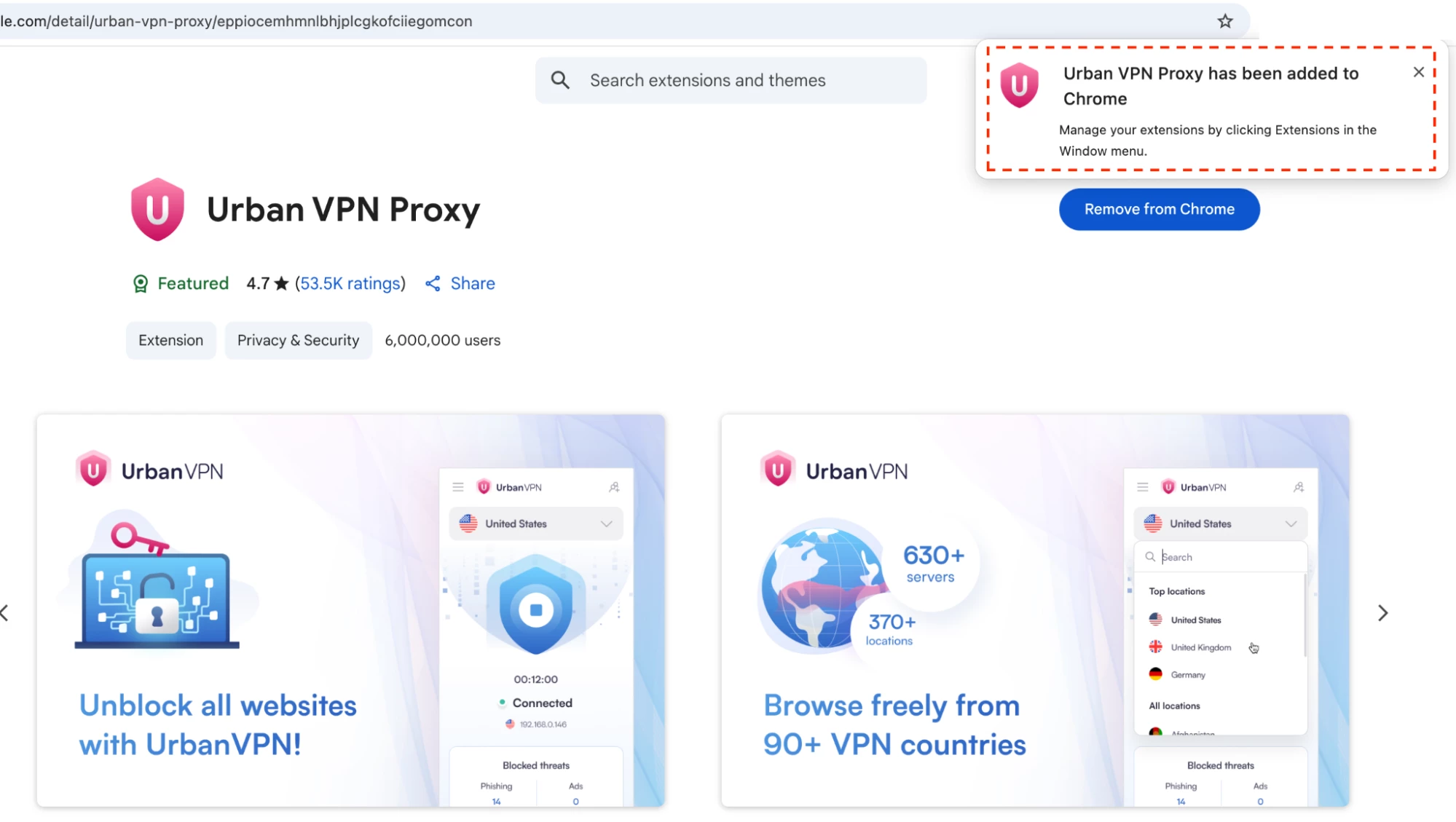
ii. Search for UrbanVPN and then click on ‘Add to Chrome’
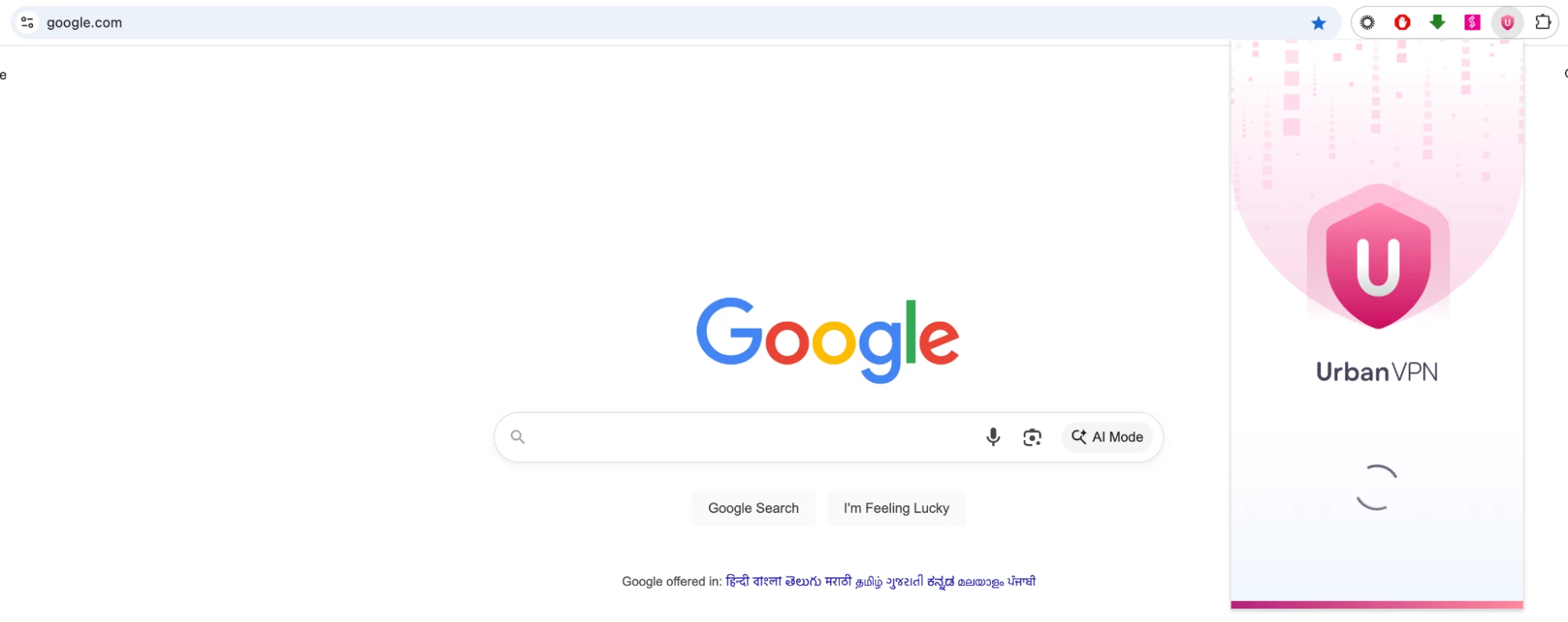
iii. Launch UrbanVPN
The 1st 443 transaction goes to authentication.urban-vpn.com/.......
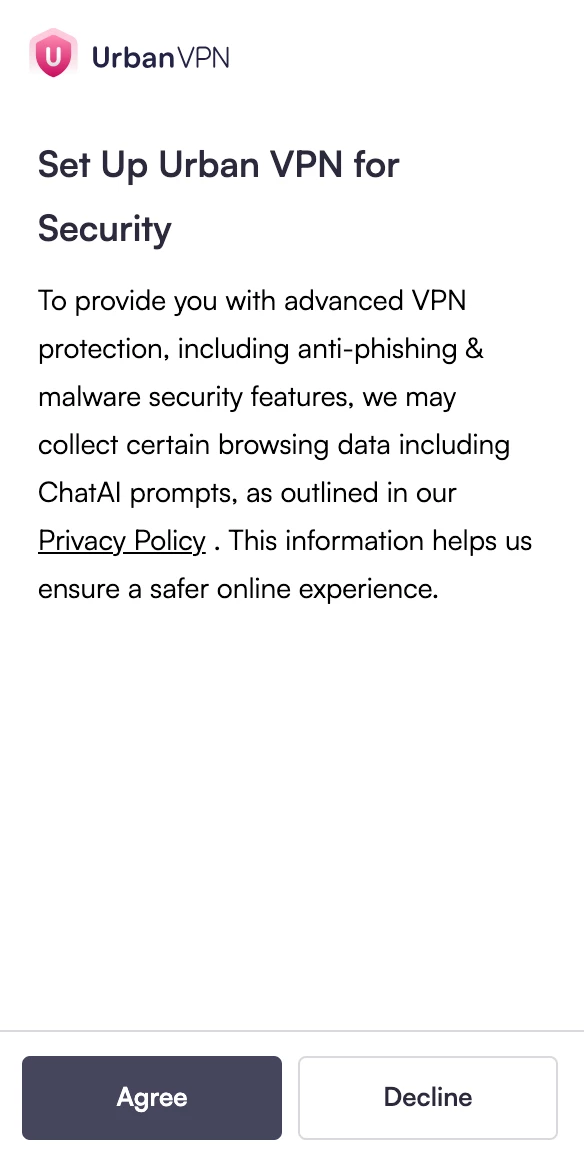
iv. If authentication.urban-vpn.com/....... is accessible then the following message will appear
v. Ready to connect

vi. Connected

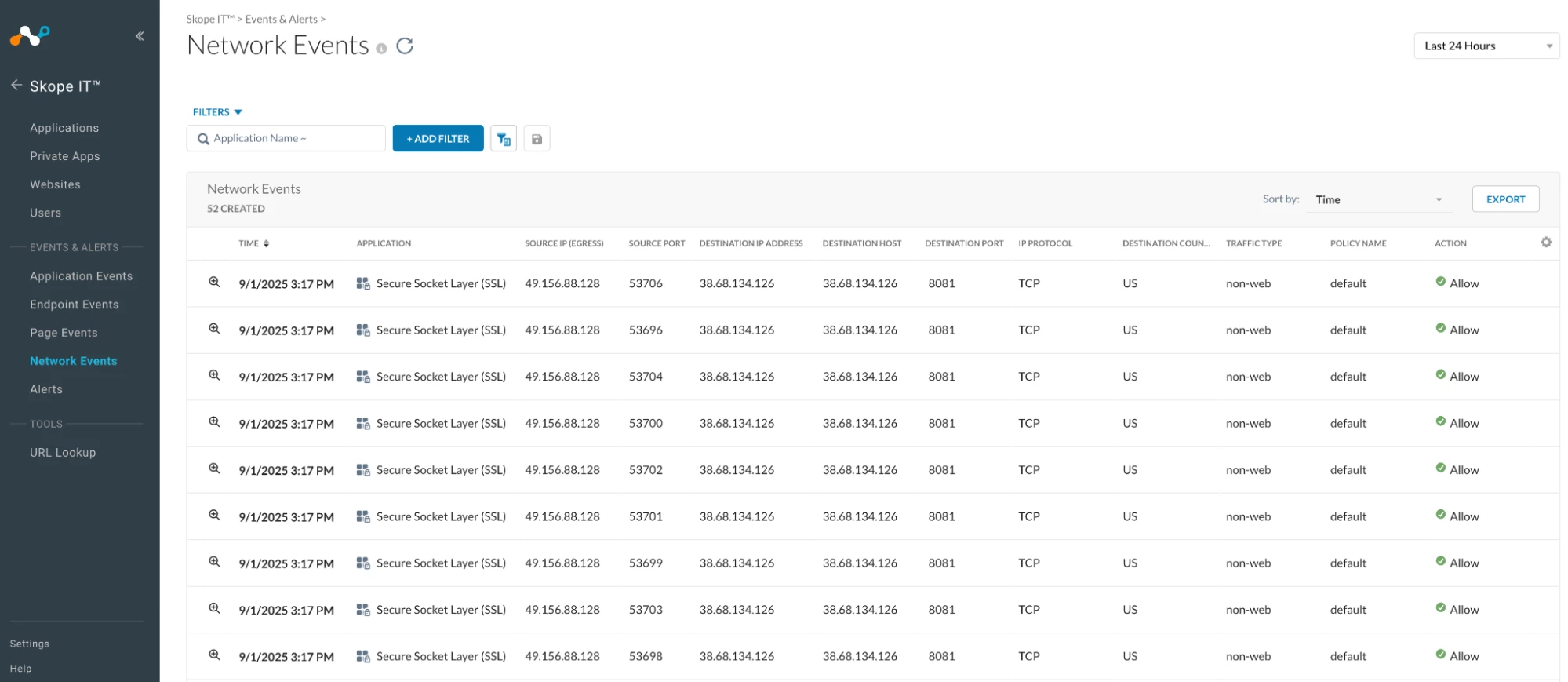
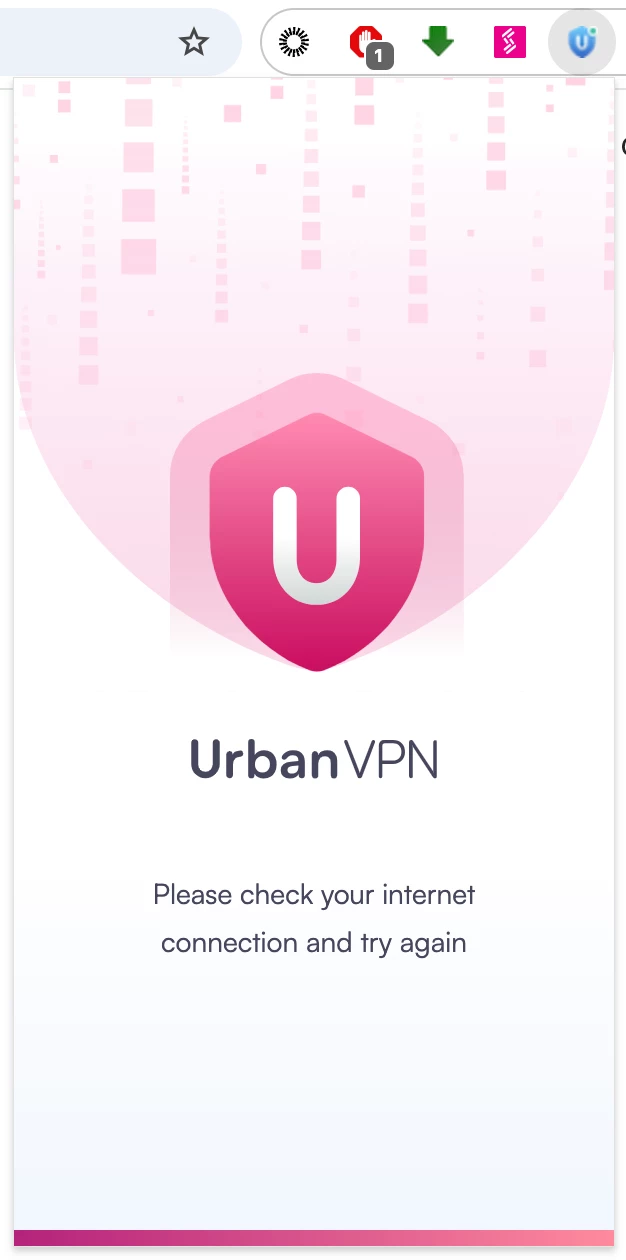
vii. Once connected, all your traffic is tunnelled through Urban VPN to their servers. Urban VPN establishes an SSL connection over a TCP port, and this traffic is non-HTTP.
Ref.
-
Check the ‘Application, Destination IP address, Destination Host, Destination Port, Traffic Type’
-
Destination Port is 8081.
Note: Urban VPN does not publicly disclose all technical details about which ports it uses.
-
Validate traffic tunnelling via accessing https://whatismyipaddress.com/
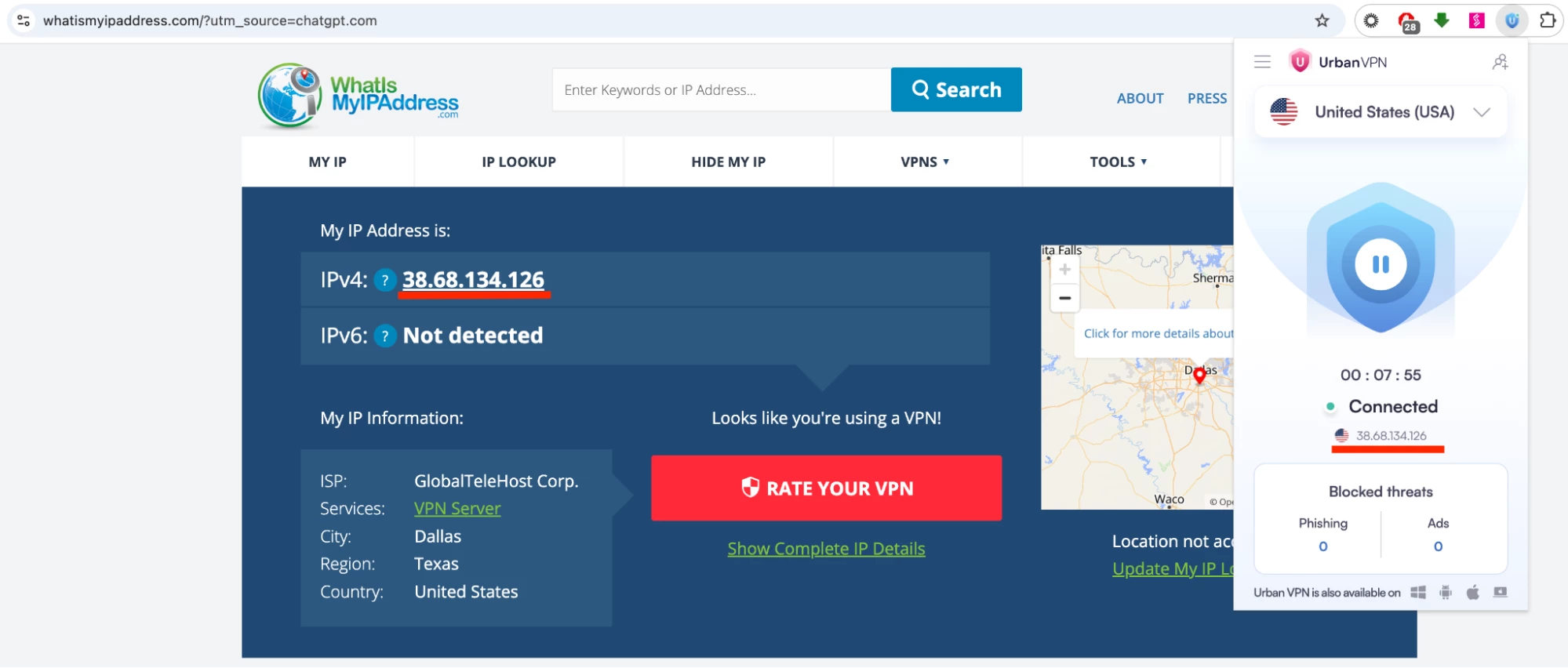
-
When you open an Incognito window, most browser extensions (including Urban VPN) are disabled by default for privacy reasons.
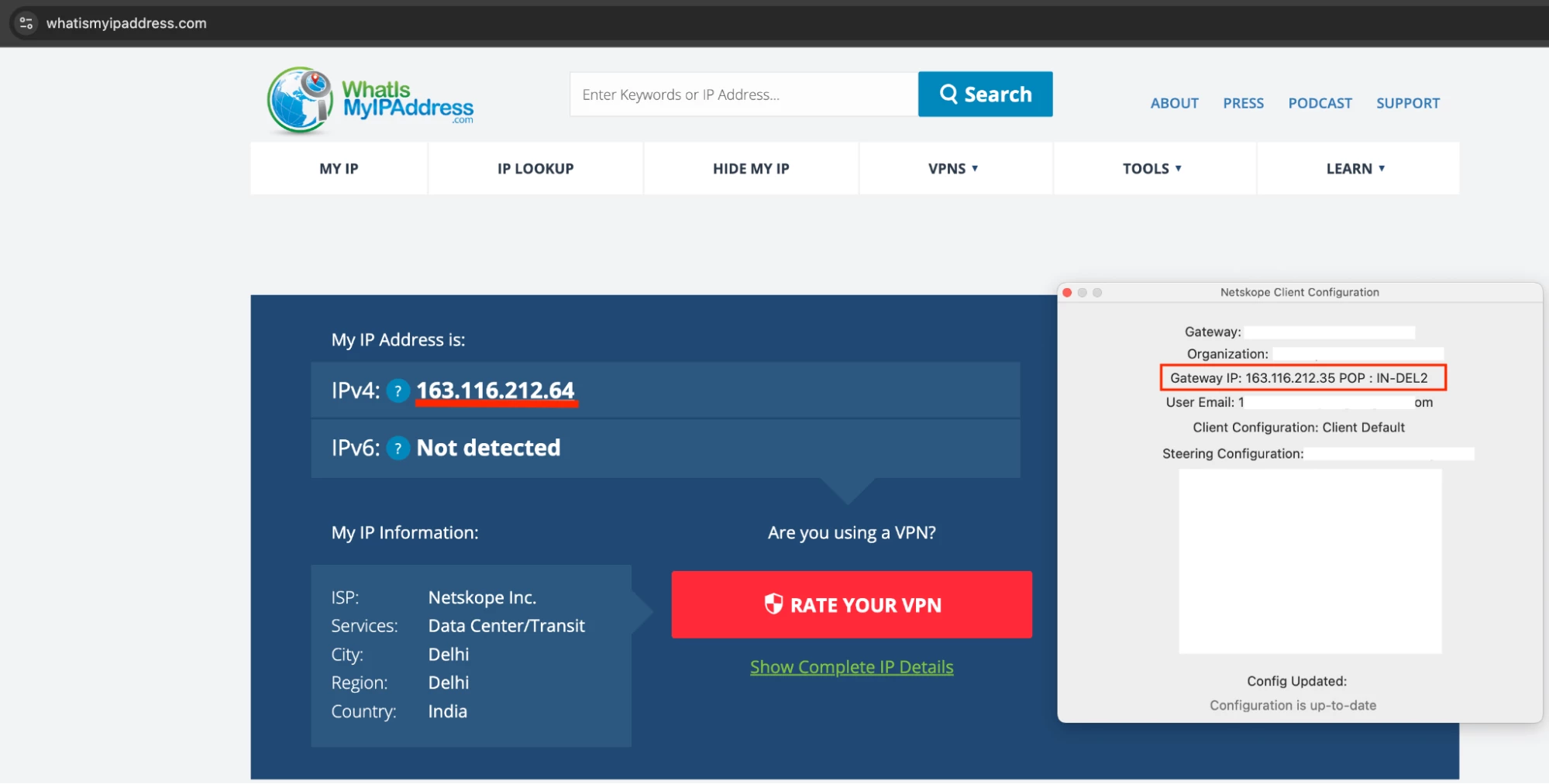
Configuration
-
To block UrbanVPN effectively, we need to implement two configuration components.
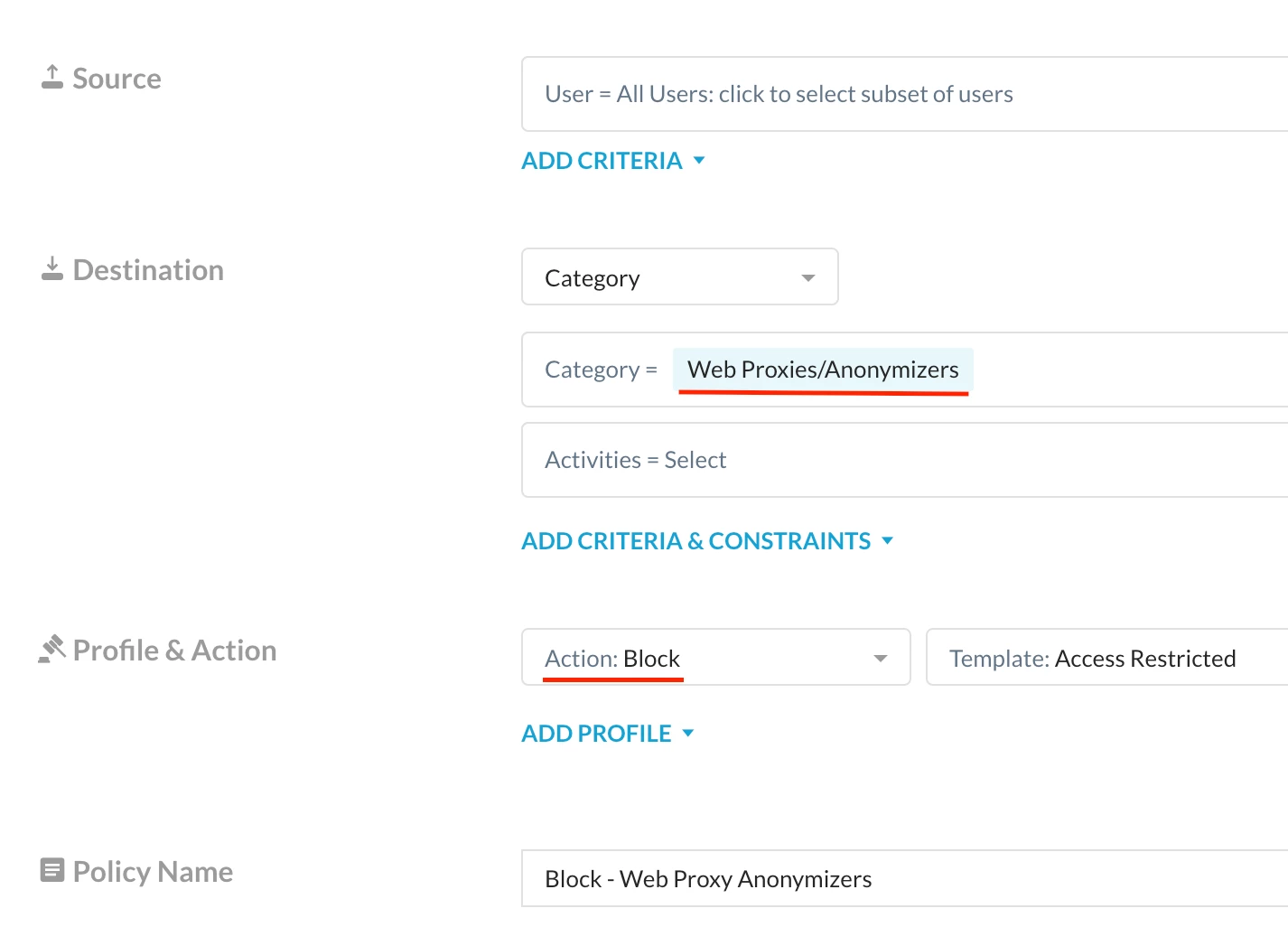
Step 1: Block Web Category ‘Web Proxies/Anonymizers’ via Realtime protection policy
License Required: SWG/Next-Gen SWG
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy
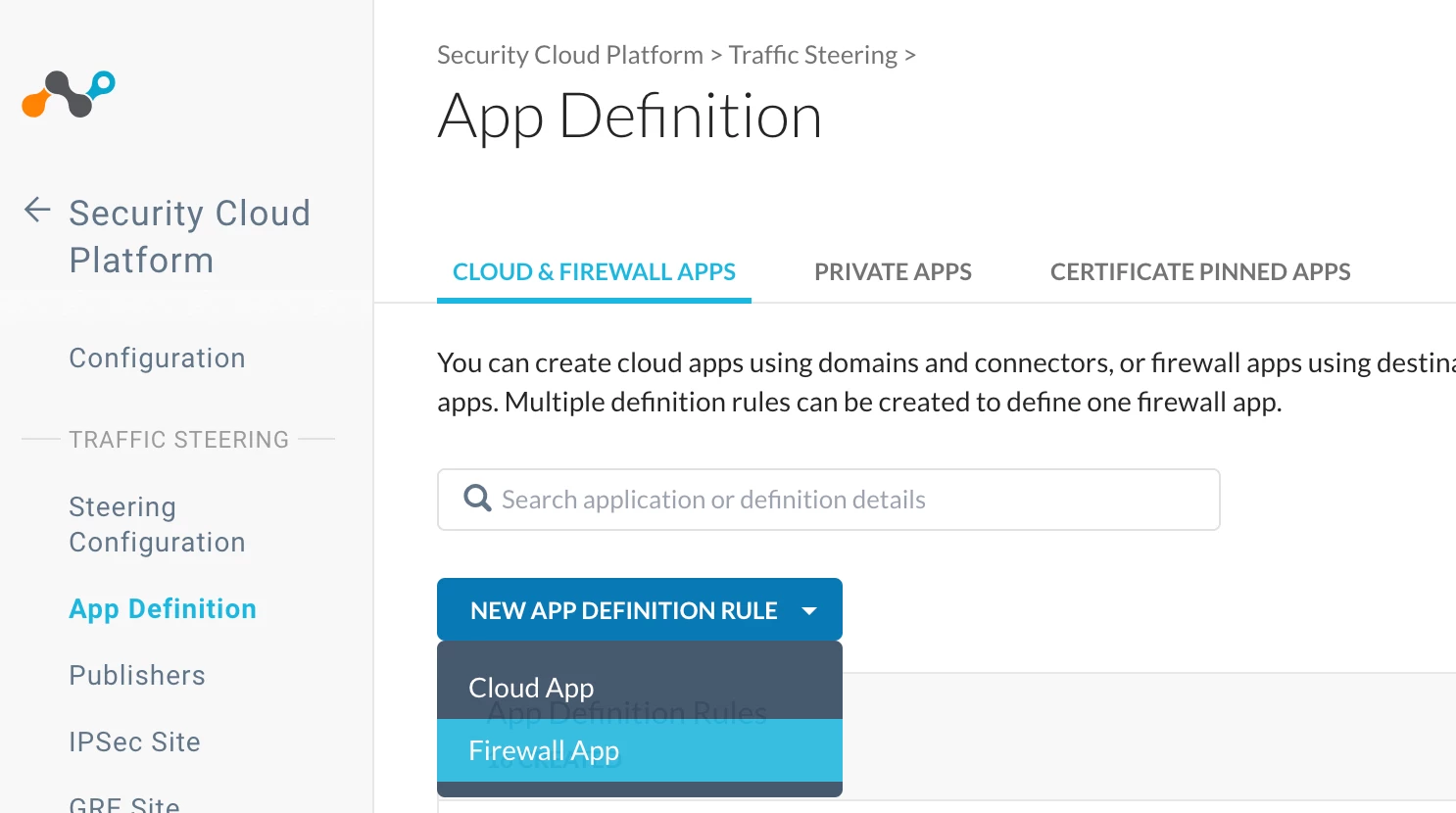
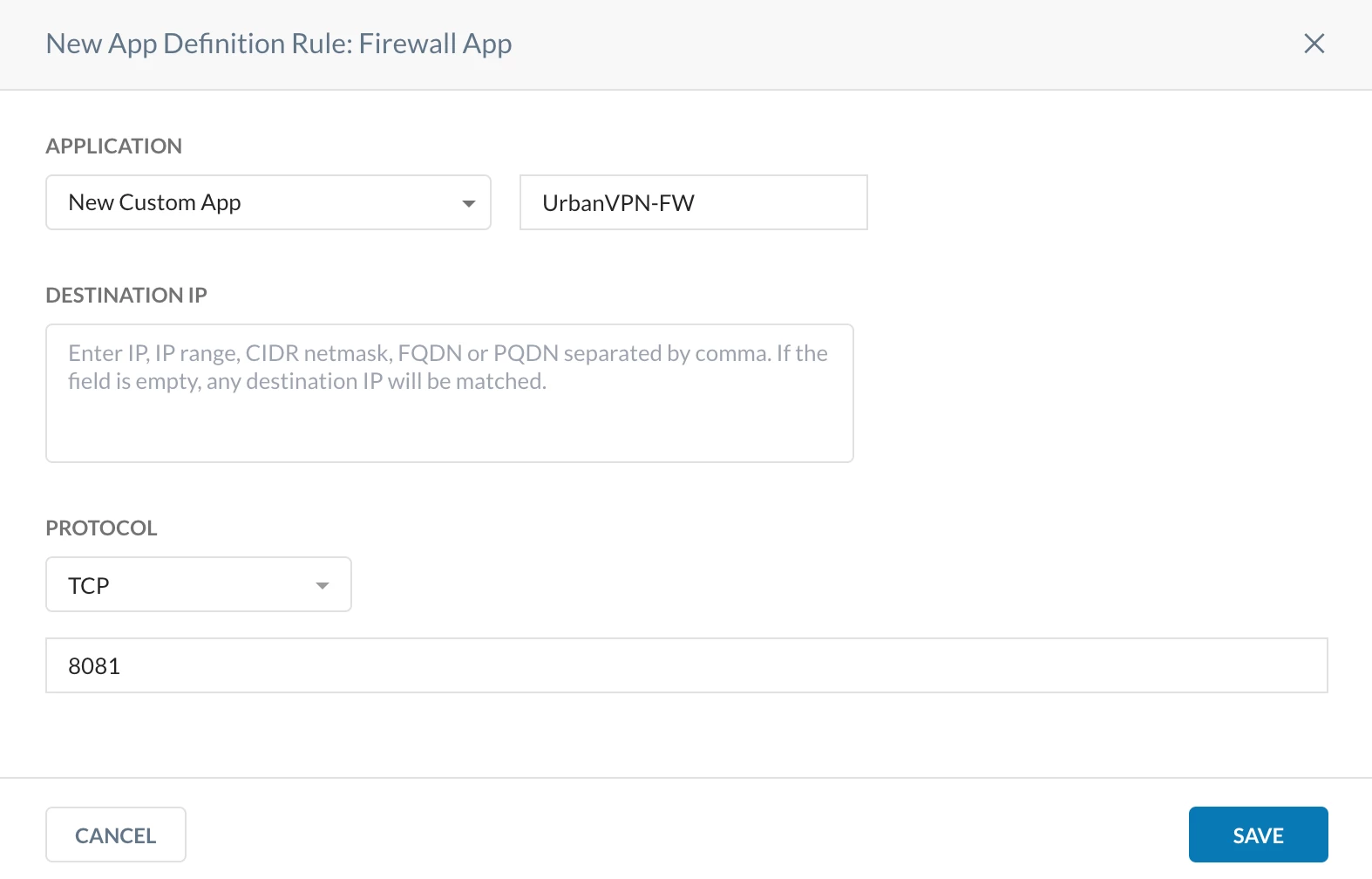
Step 2: Only known and approved TCP/UDP non-HTTP ports should be whitelisted; all other ports should be blocked.
License Required: Netskope Cloud Firewall (CFW)
Lets block TCP Port 8081
Path: Netskope Tenant UI >>> Security Cloud Platform >>> Traffic Steering >>> App Definition >>> Cloud & Firewall Apps >>> Firewall App
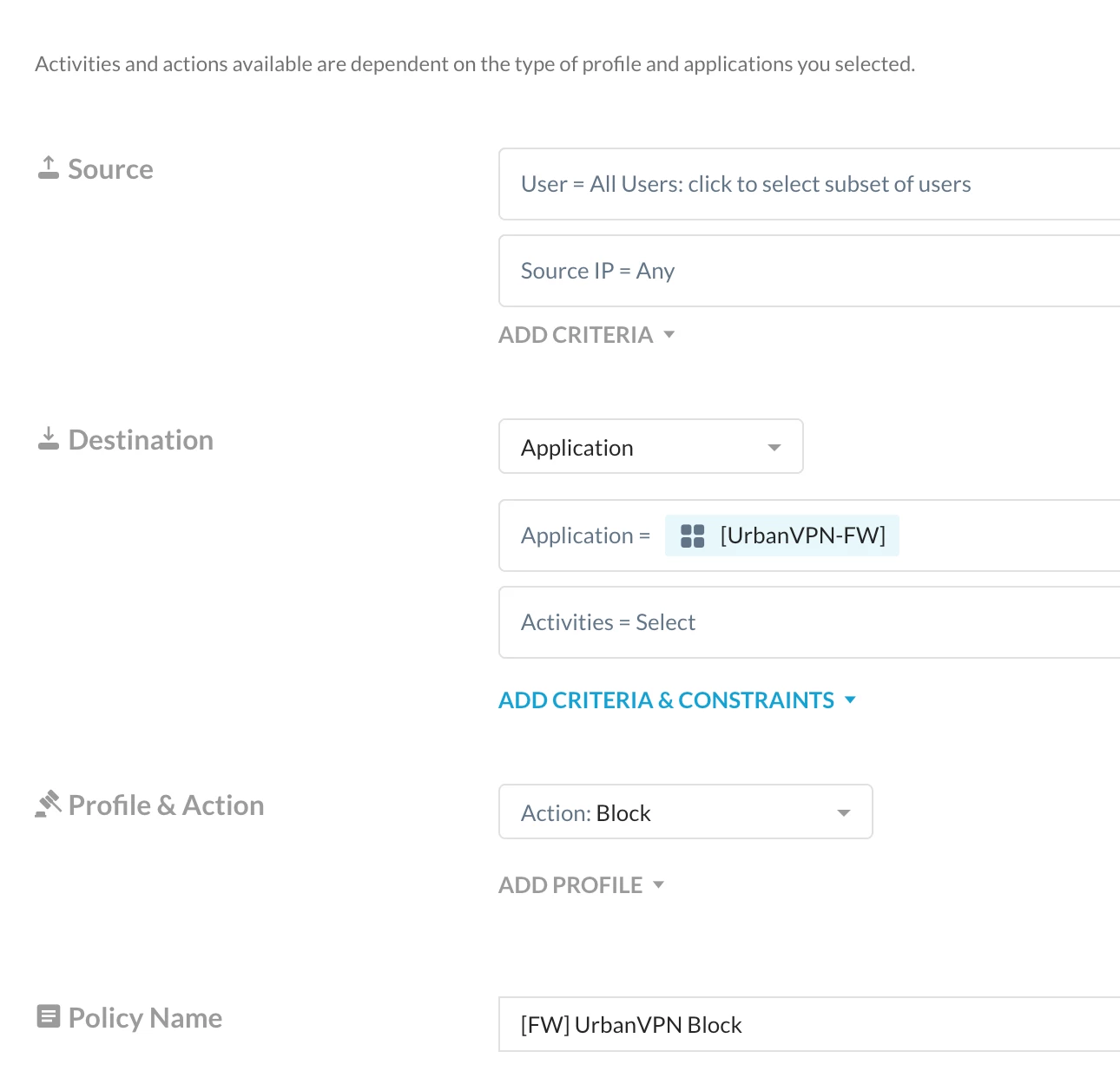
Verification
Author Notes
-
It's important to understand that most proxy applications operate across both web and non-web ports. Without a cloud firewall license, achieving full visibility and control over these applications becomes extremely difficult and unreliable.
Terms and Conditions
-
All documented information undergoes testing and verification to ensure accuracy.
-
In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
-
This article is authored by Netskope Global Technical Success (GTS).
-
For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.






