In this article we show how to set up an automatic remediation workflow in Azure, leveraging the APIs available in Netskope’s Cloud Security Posture Management. We’ll show how a security rule can be automatically remediated in Azure, and we’ll show how that remediation can happen either based on a time trigger or a HTTP trigger.
This workflow can be used for many types of violation, in this article we will be considering the use case where we want to remedy a violation where an Azure key Vault does not have purge protection enabled.
The source code is available at https://github.com/netskopeoss/CSPM-Azure-AutoRemediation
Setting Up
Netskope SPM detects violations for key vaults where purge protection is disabled as a part of the rule: Ensure KeyVault is recoverable.
In this solution there are two Azure function apps involved. The first is a FetcherForKeyVaultRecoverableHTTP used for getting a list of violating resources from Netskope SPM. The second is a RemediatorForKeyVaultRecoverable app used for enabling the purge protection in KeyVault (can be custom for other remediation use cases)
The deployment steps for both the function apps are provided in detail in the readme section of the Github Repository.
As part of the setup we create a single storage account that will function as a queue of non-compliant keyvaults to be remediated. Both apps will have the connection string for this storage account as a parameter. Additionally, we enable System Assigned Managed Identity for RemediatorForKeyVaultRecoverable Function App, and provide Contributor RBAC over KeyVault scope for this identity.
Now we are all set to fetch the result from Netskope SPM and trigger remediation for any violation.
Triggering remediation
To test the setup:
- Login to Azure Portal and select the first function app : FetcherForKeyVaultRecoverableHTTP.
- Select the Fetcher Function and copy the function URL.
- The Fetcher function can be triggered either through a HTTP GET request using Postman or a Time Trigger, allowing you to control how and when remediation happens.
- The Fetcher function queries Netskope SPM for any violations. If any violations are present, it will enqueue the violating resource id to a queue under storage account created in Deployment Step 3.
- The second function app RemediatorForKeyVaultRecoverable will automatically dequeue from the queue and enable purge protection for the affected KeyVaults.
The above solution can be extended for other rules and resources by implementing the appropriate remediation logic in additional Azure Function Apps. Queue name for Fetcher and Remediator needs to be the same in both function.json files in the Function.
See it in action!
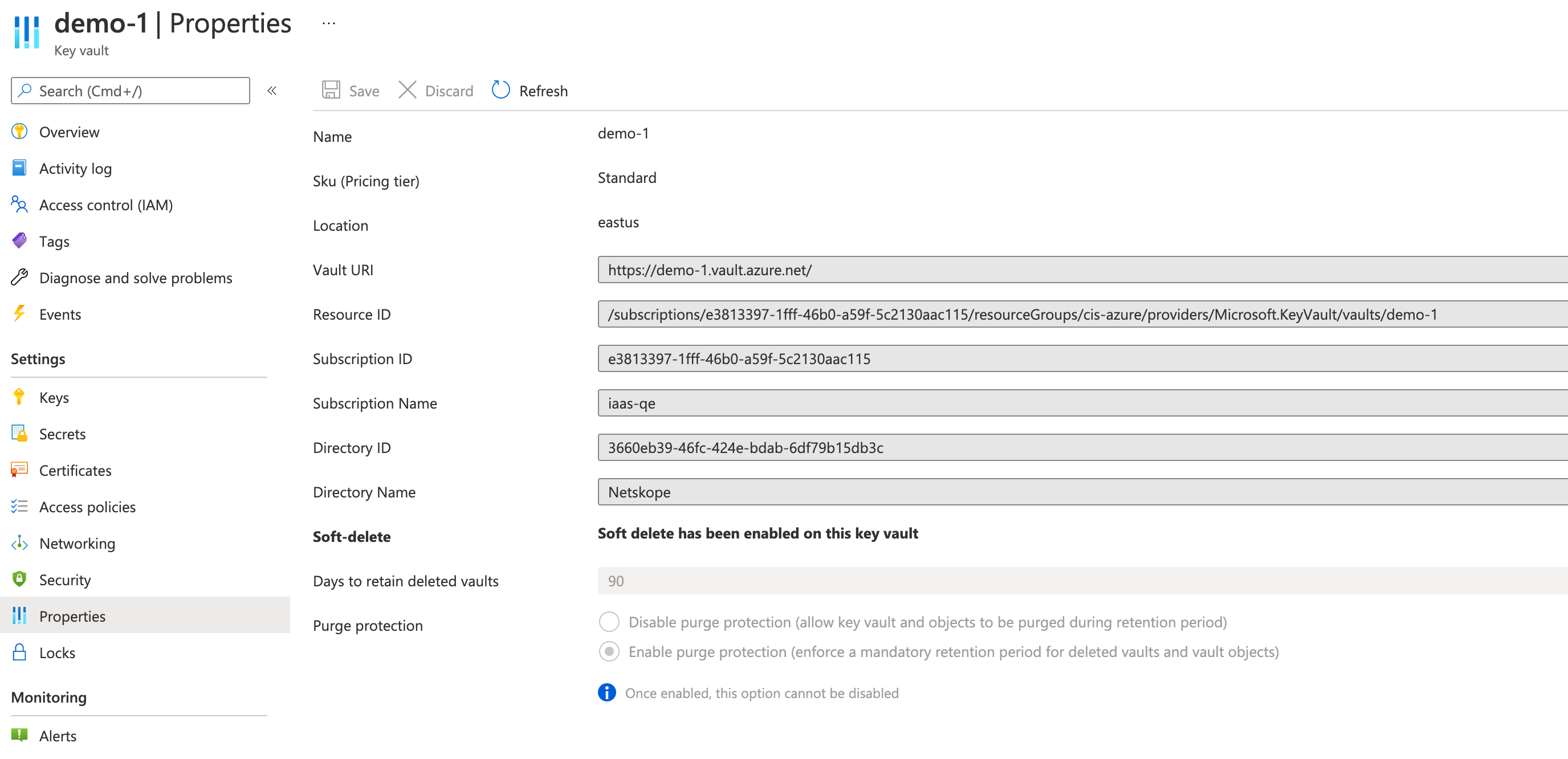
Here we have a non-compliant key vault in Azure: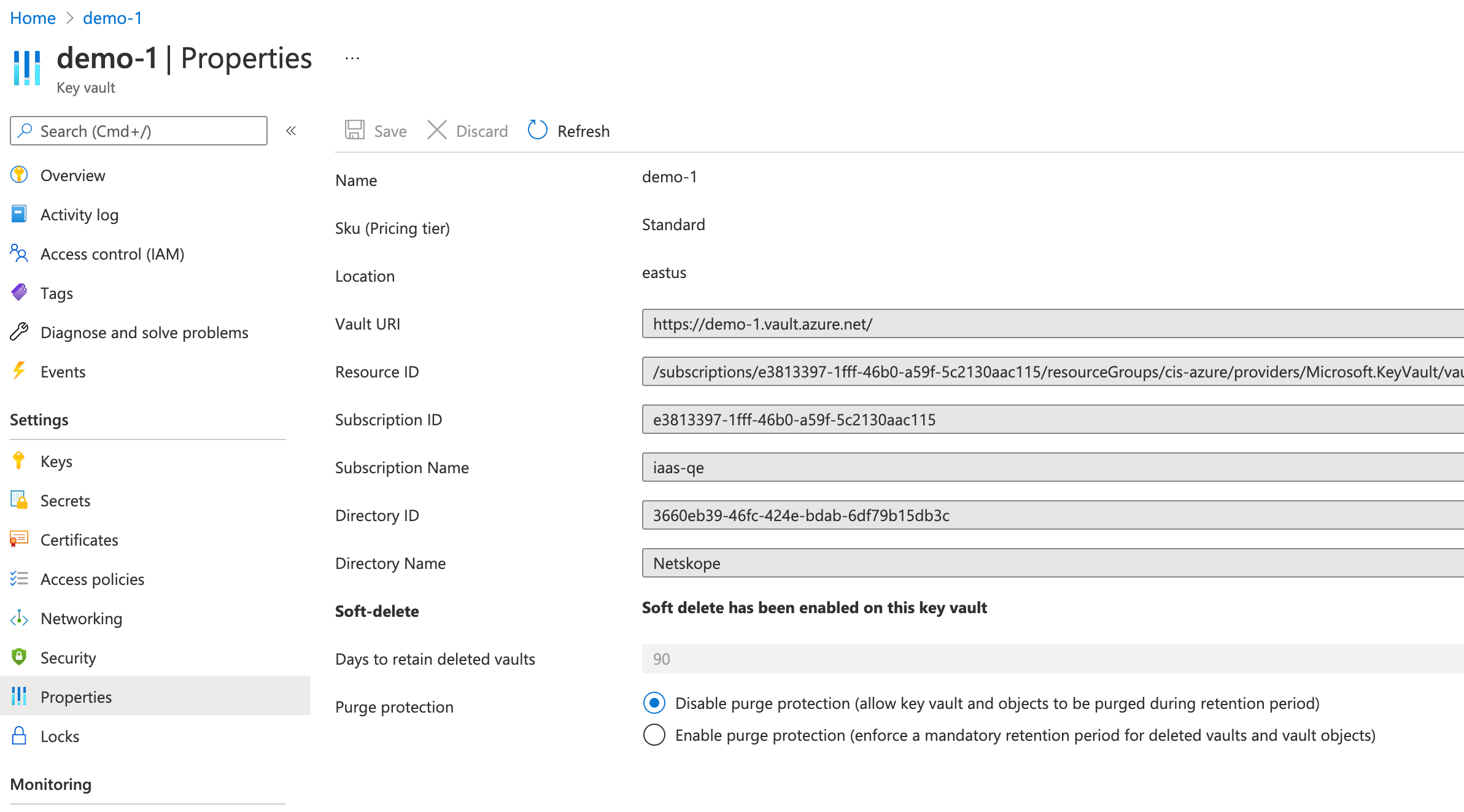
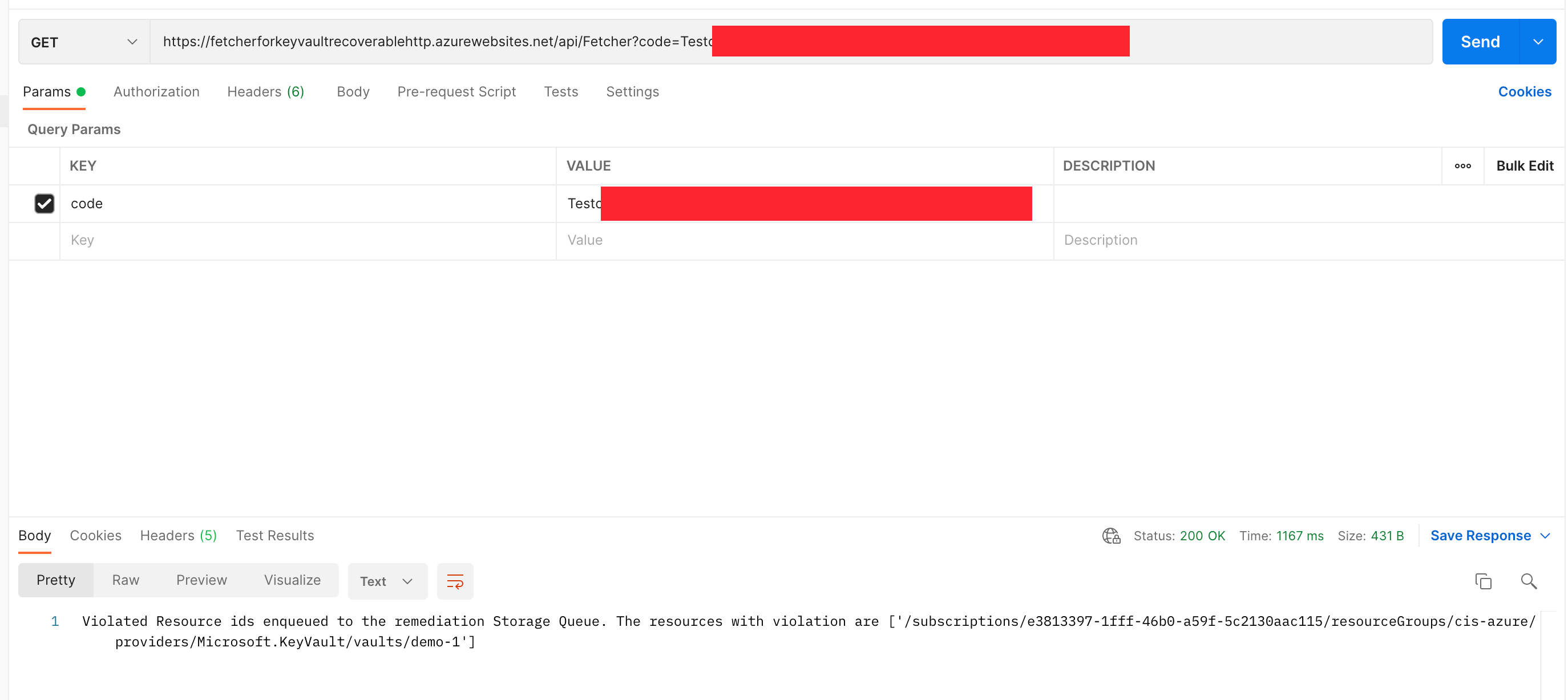
In our test setup, we trigger auto-remediation with postman. In practice, it can run on a schedule or be triggered by other events. Note that the response shows that non-compliant KeyVaults have been found and are now queued for remediation!
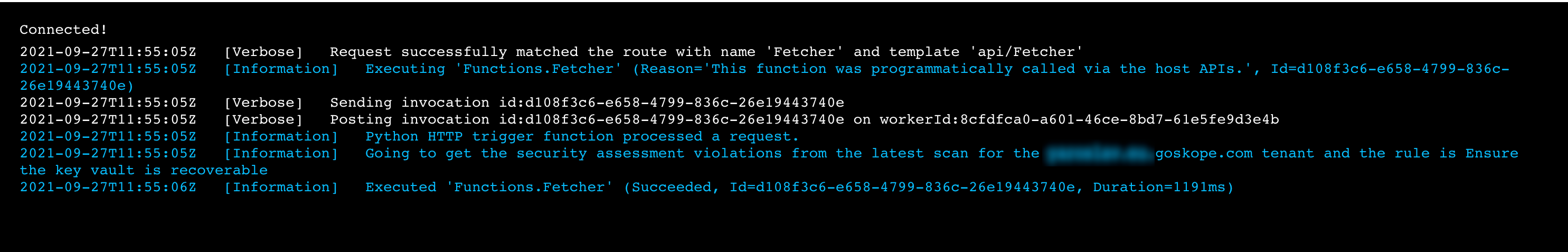
The logs for our first app show that we have found non-compliant KeyVaults in Netskope SPM:
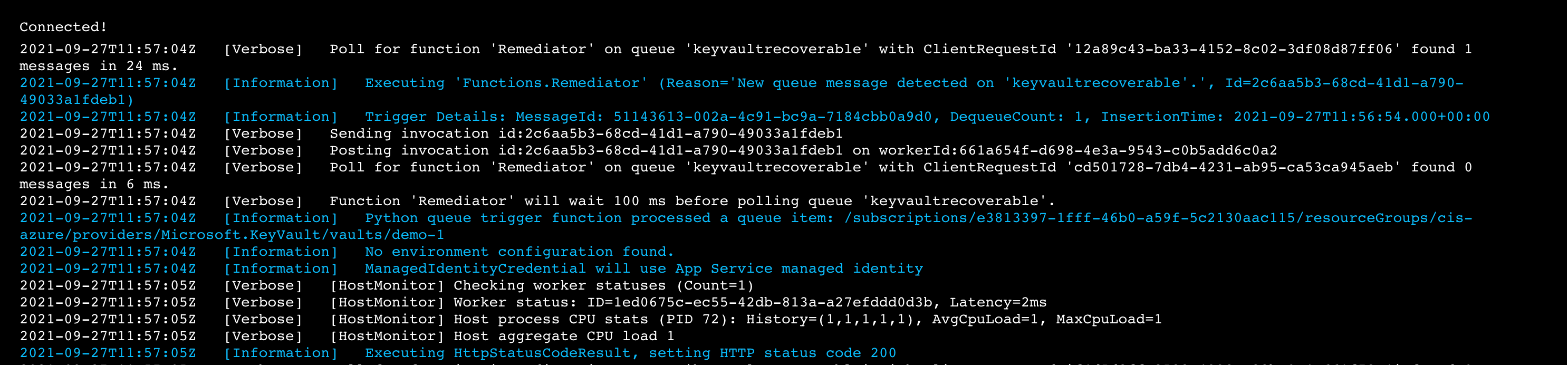
The logs for our second app show it dequeuing non-compliant KeyVaults and applying remediation to them!
Finally, back in Azure we see that our KeyVault is now compliant!