If you work with Security Architects, SOC Engineer, or a SOC Analyst, all of them will tell you one thing “Send me ‘ALL’ the logs!” because their ability to find threats or investigate incidents is reduced without the log data or if the required log data is dispersed in various log data stores. If your chosen partner for cloud is Microsoft, then they will also tell you one more thing “Send it to Microsoft Sentinel!” If you happen to be a person responsible to fetch these logs from Netskope then it’s okay to establish feeling where you think the whole world is working towards making your life difficult. I can tell you one thing – I’m not one of them so let me explain why I think I’m the angel 👼 out there to save you ....!
Let’s get some fundamentals out of our way:
- Cloud Exchange – it’s our integration platform to enable third party partner integrations. Packaged as a multi-container application.
- Modules - Cloud Exchange (CE) comes with four primary modules: Log Shipper, Ticket Orchestrator, Threat Exchange, and Risk Exchange.
- Plug-ins – Cloud Exchange has individual plugins that leverage functionality provided by 3rd-party partners.
- Log Types – Depending on what features are licensed and used by you inside Netskope tenant there are four types of logs we have Network Events, Application Events, Security Alerts, Web Transactions.
- Network Events - Provides insight into cloud firewall and network private access events.
- Application Events - Provides insights into application usage, specifically by devices, users, users and traffic patterns.
- Security Alerts - Provides visibility into security incidents and violations and the ability to identify effects of a breach.
- Web Transactions - Provide granular information about the web sites that users have accessed.
At the high level this is what you will do to send the logs to Microsoft Sentinel:
- Deploy Cloud Exchange
- Add Netskope tenant details and enable log shipper module
- Configure Netskope tenant plugin for Cloud Log shipper
- Configure Microsoft Sentinel plug-in
Okay, so the first thing you want to settle on is to decide where should you deploy Cloud Exchange? You can deploy Cloud Exchange on a Virtual Machine with Docker engine. Your decision for deployment choice will depends on your overall architecture and design, requirements and in house expertise. From the lens of Microsoft Cloud Adoption Framework and Azure Landing Zones – Cloud Exchange belongs to “Management” Subscription. To help you with this deployment, I have created few Infrastructure as Code (IaC) templates using Terraform that are available on Netskope’s public GitHub repositories. Who doesn’t like flexibility or choices? so I have provided quite a few IaC templates for you to pick depending on your situation.
These two templates are using terraform base code and help you with the deployment (i.e., deployment on a VM – each repo comes with readme file with instructions …)
Cloud Exchange (VM) Deployment into an existing Virtual Network
Cloud Exchange (VM) into a new Virtual Network
Here is a video walkthrough of this deployment using one of the templates.
With the deployment of Cloud Exchange done, you are ready to add Netskope tenant details and enable modules and plug-ins? For the “Modules” you will enable Cloud Exchange “Log Shipper” module as the name suggest and for the plug-ins you will use Netskope, Netskope WebTX (only needed if you want them) and Microsoft Azure Sentinel plug-ins – You may have noticed by now that we are very creative when it comes to naming the plugins 😊
For thinking mind, you wonder can’t we not just have one plug-in to do this all? Probably we could have but by decoupling we can use and reference the common plug-ins in multiple ways. I digressed a little … back to the topic, the product documentation provides step by step instructions on these steps so I wouldn’t repeat it – check out these links on how to perform these steps:
- Add Netskope tenant details
- Enable log shipper module
- Configure Netskope tenant plugin for Cloud Log shipper
- Configure Microsoft Sentinel plug-in
This is all what is needed to send the logs from Netskope to Microsoft Sentinel, but as I said earlier, I’m here to make your life easier so let me share another item while we are at the discussing log data. These will give you some “brownie” points with your SOC team members for sure!
Having all the logs available inside your SIEM solution (Microsoft Sentinel) is good but wouldn’t it be nice to have these logs parsed to provide valuable insights and comprehensive monitoring into Netskope log data? This will give you a starting point to know what’s is happening inside your Netskope environment.
Security operations teams love dashboards and visual representation of log data, showing trends over time, and detecting anomalies are essential for their daily work. Microsoft Sentinel has a concept of “Workbooks” which allows you to do all those things. The good news is that I have done the hard work already and have published Netskope workbook as a Microsoft Sentinel Gallery Item – just do a search “Netskope” inside your Microsoft Sentinel under Workbooks Templates to find it.
All you have to do to consume is hit “Save” button and that’s it. Once the logs are start flowing into your Microsoft Sentinel Log Analytics Workspace, Netskope workbook will be able to parse your log data to produce various dashboard – 10 in total. You will be able to get visibility in to your Netskope Security Cloud and quickly identify threats, anomalies, traffic patterns, cloud application usage, blocked URL addresses and more.
Here are all the screenshots from this workbook.
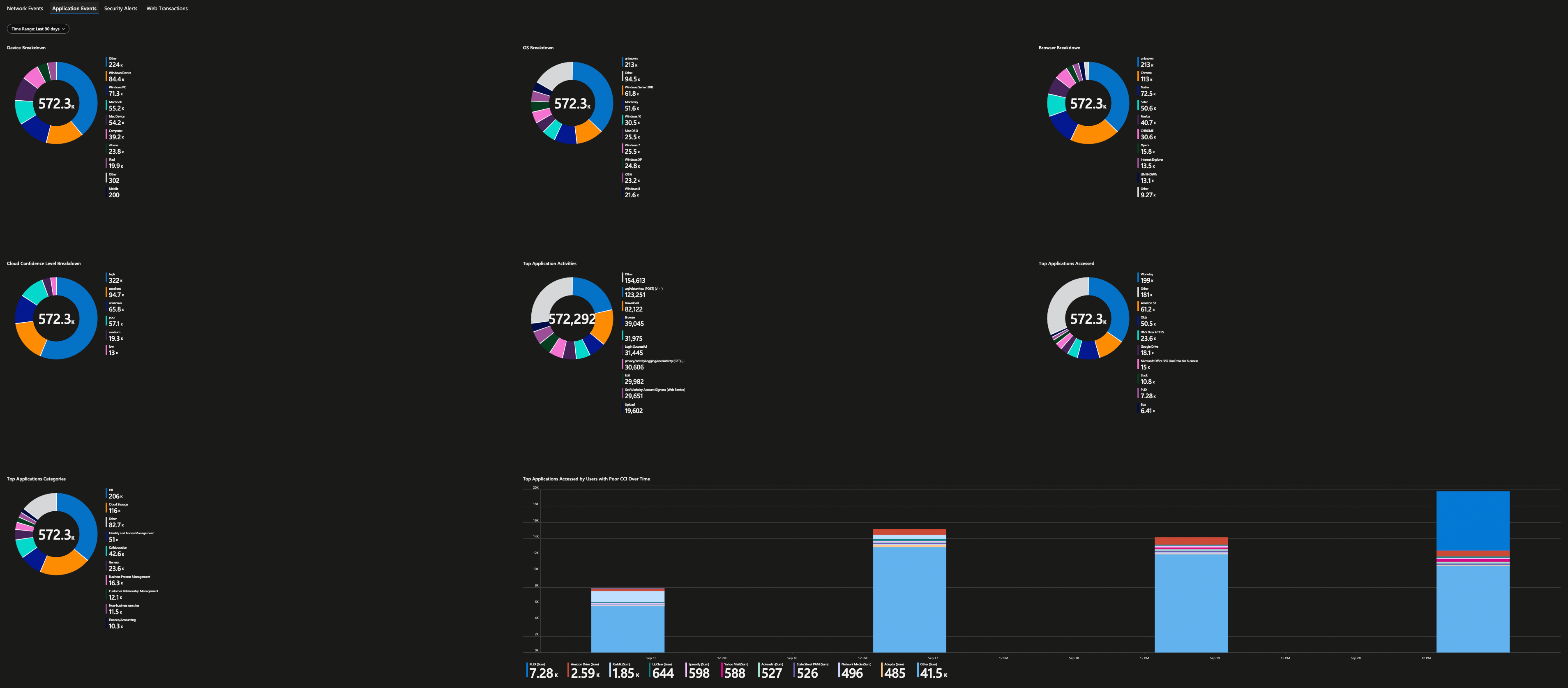
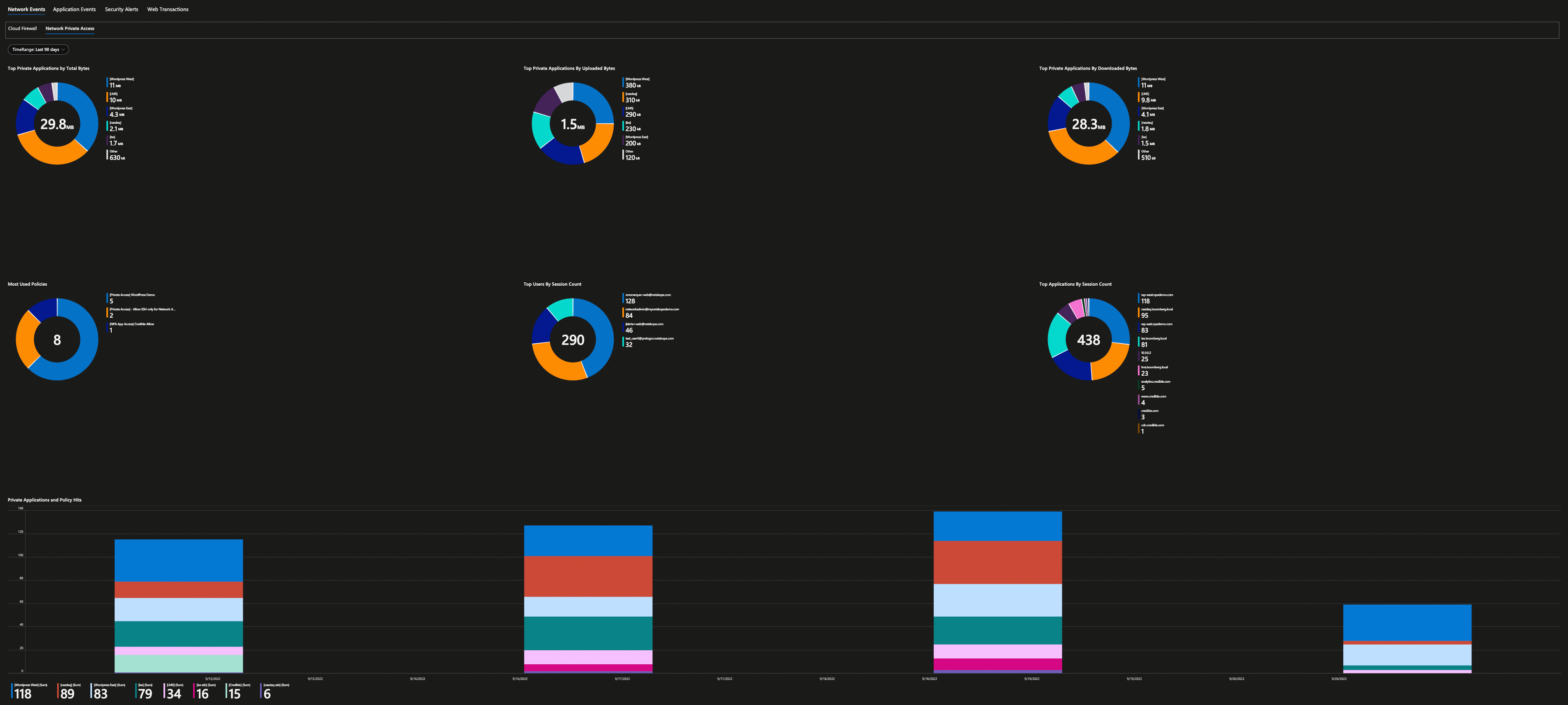
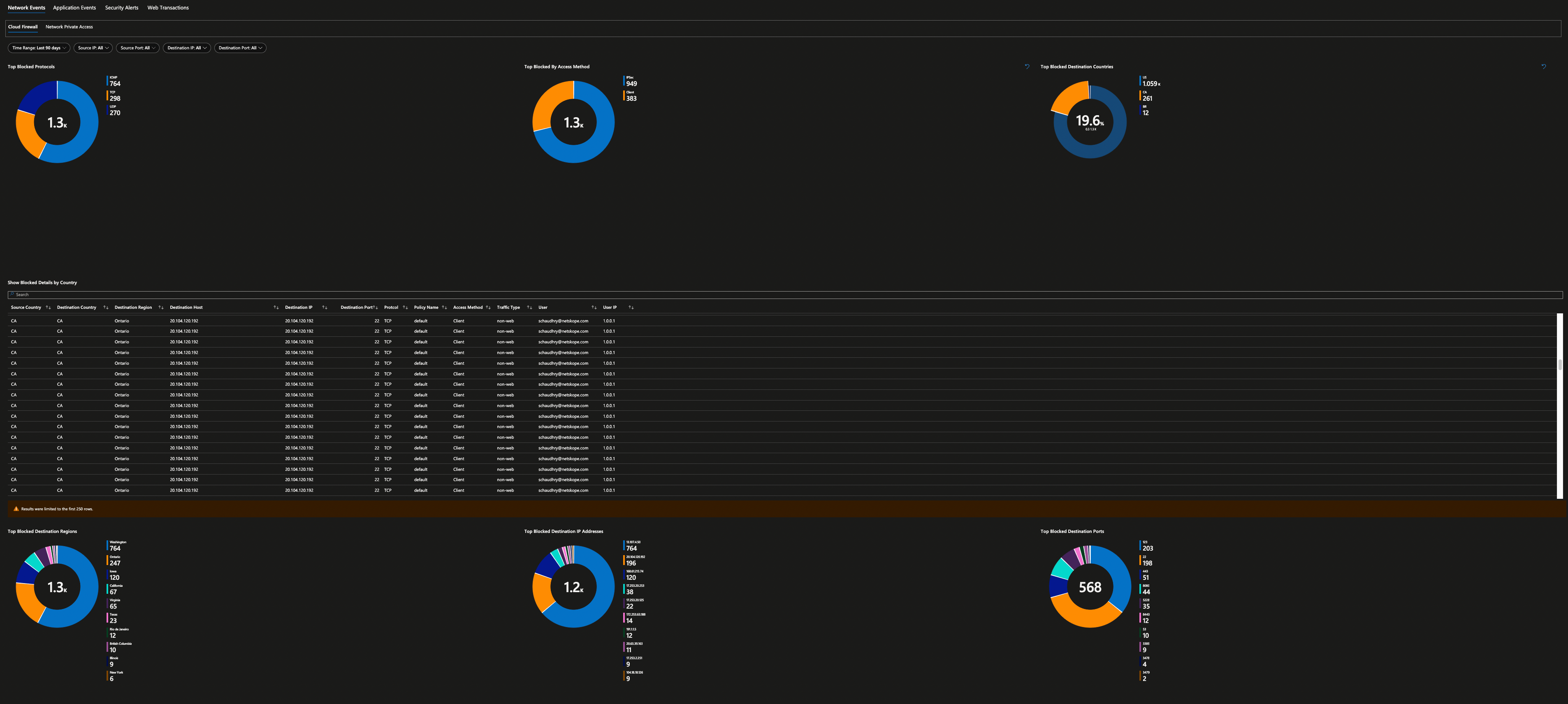
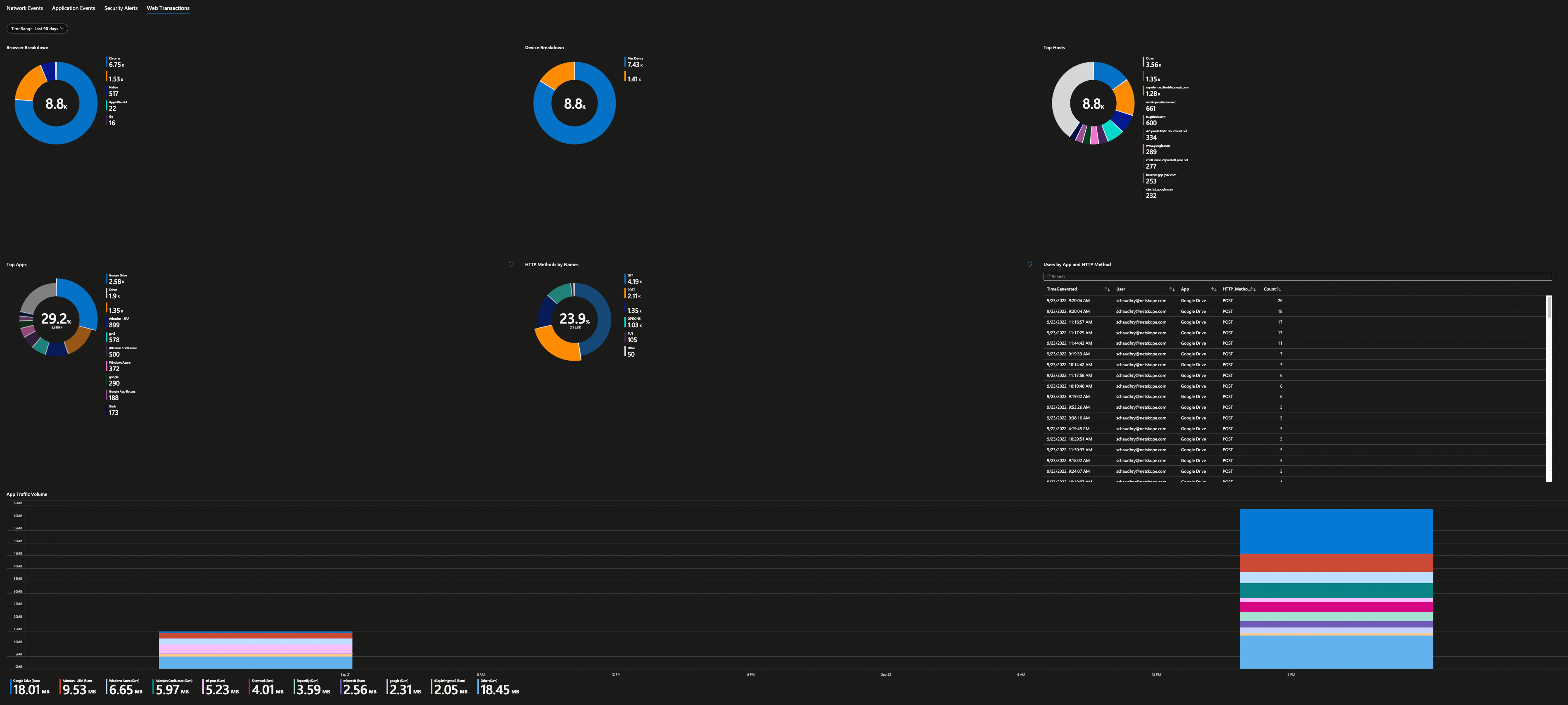
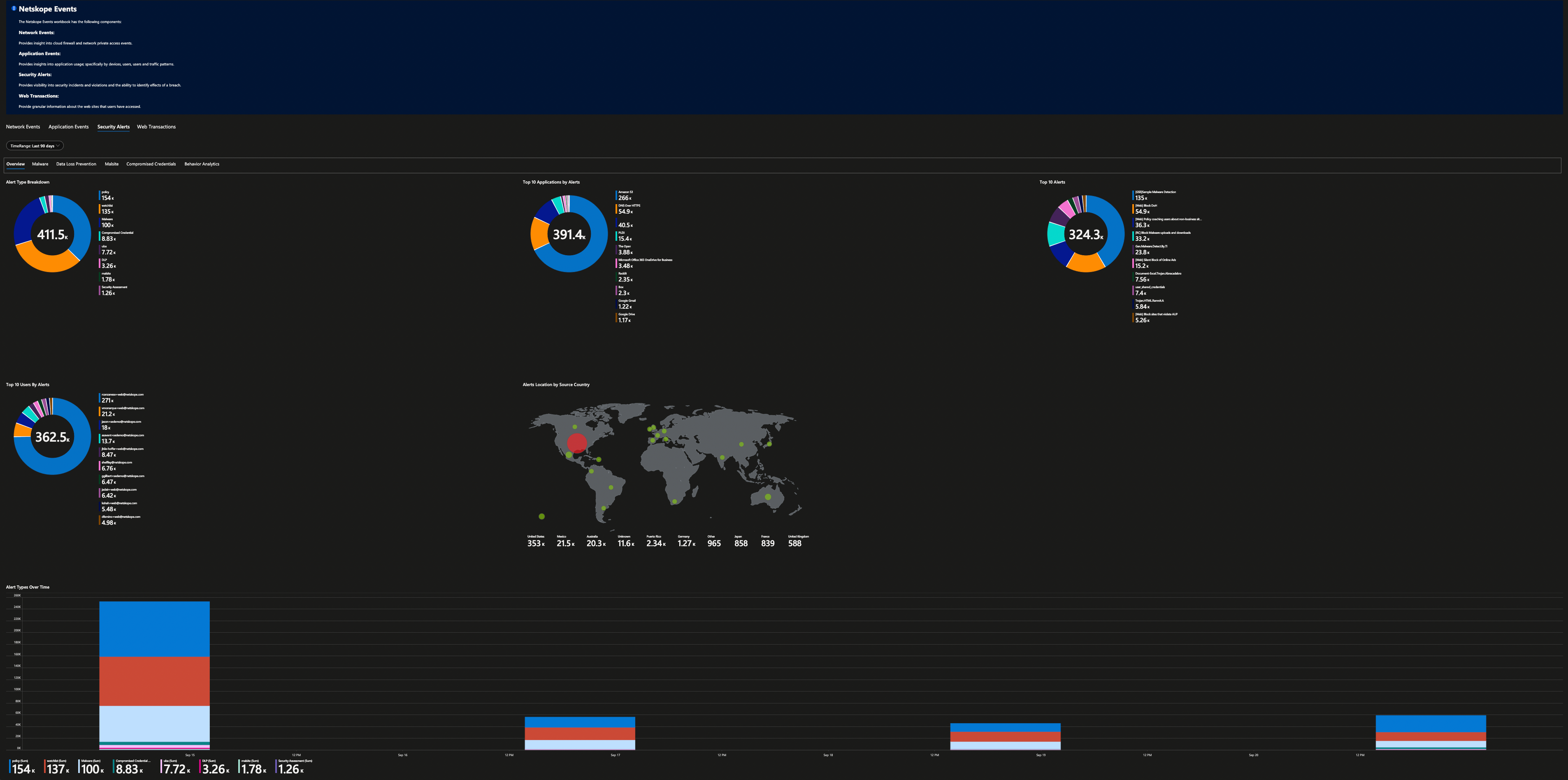
Security Alerts are then further grouped based on their categories.
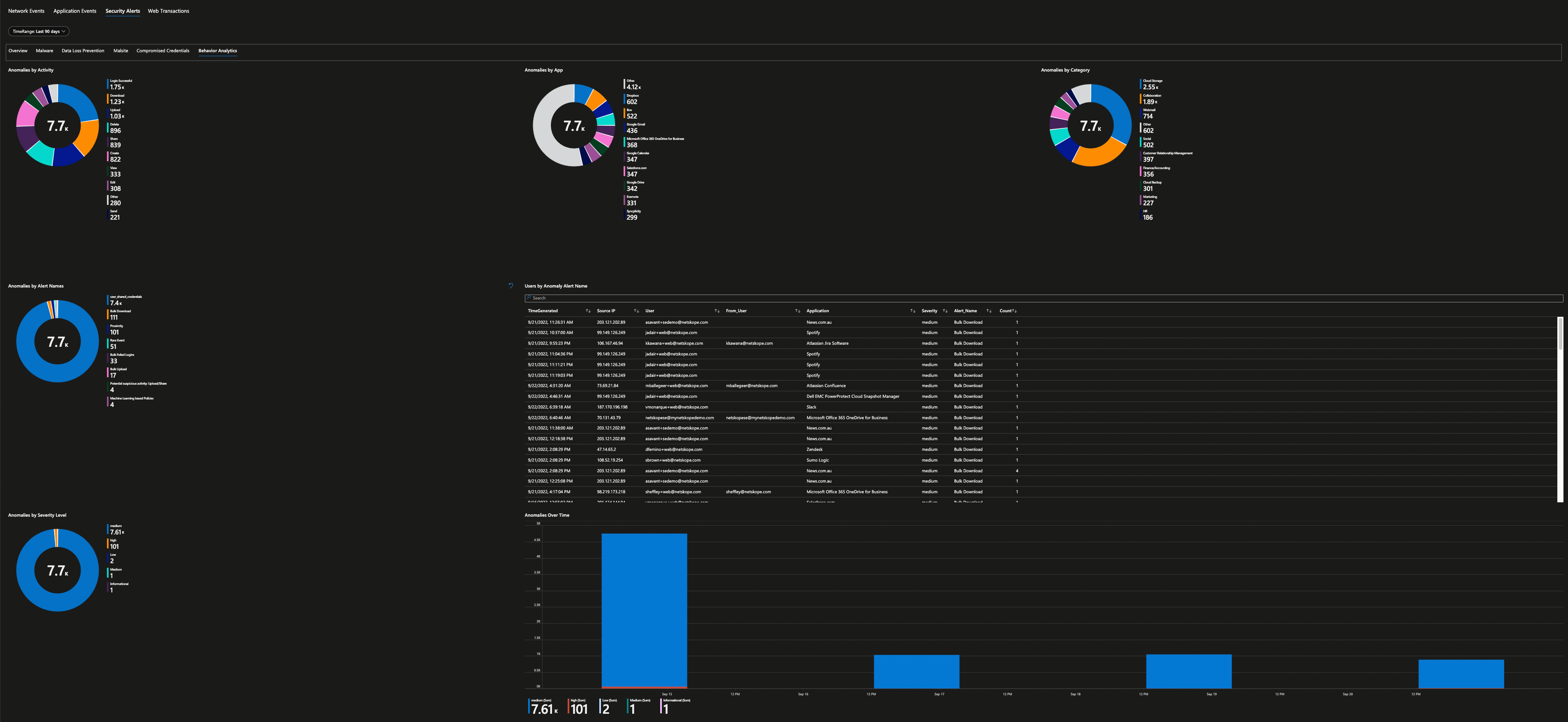
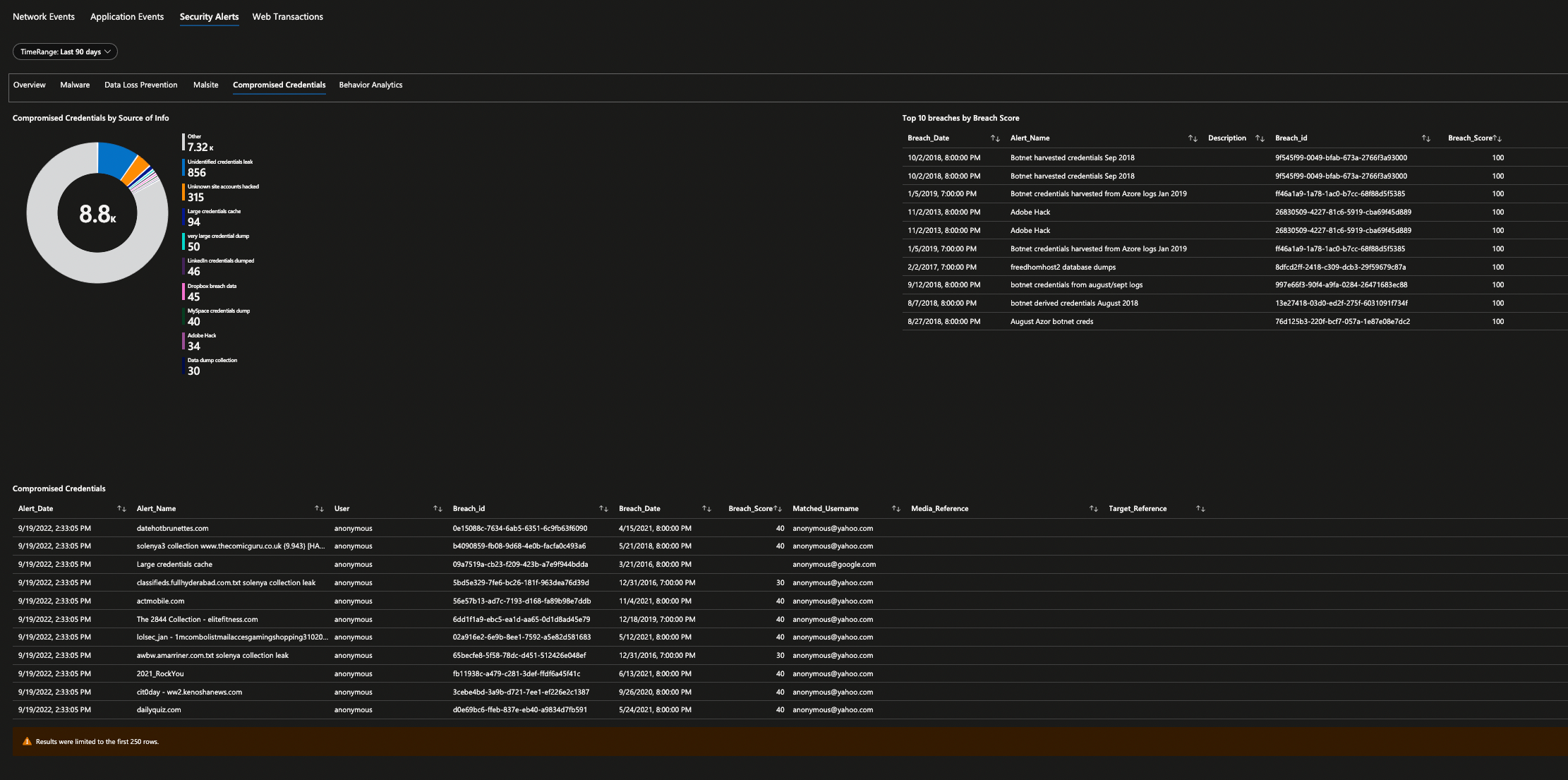
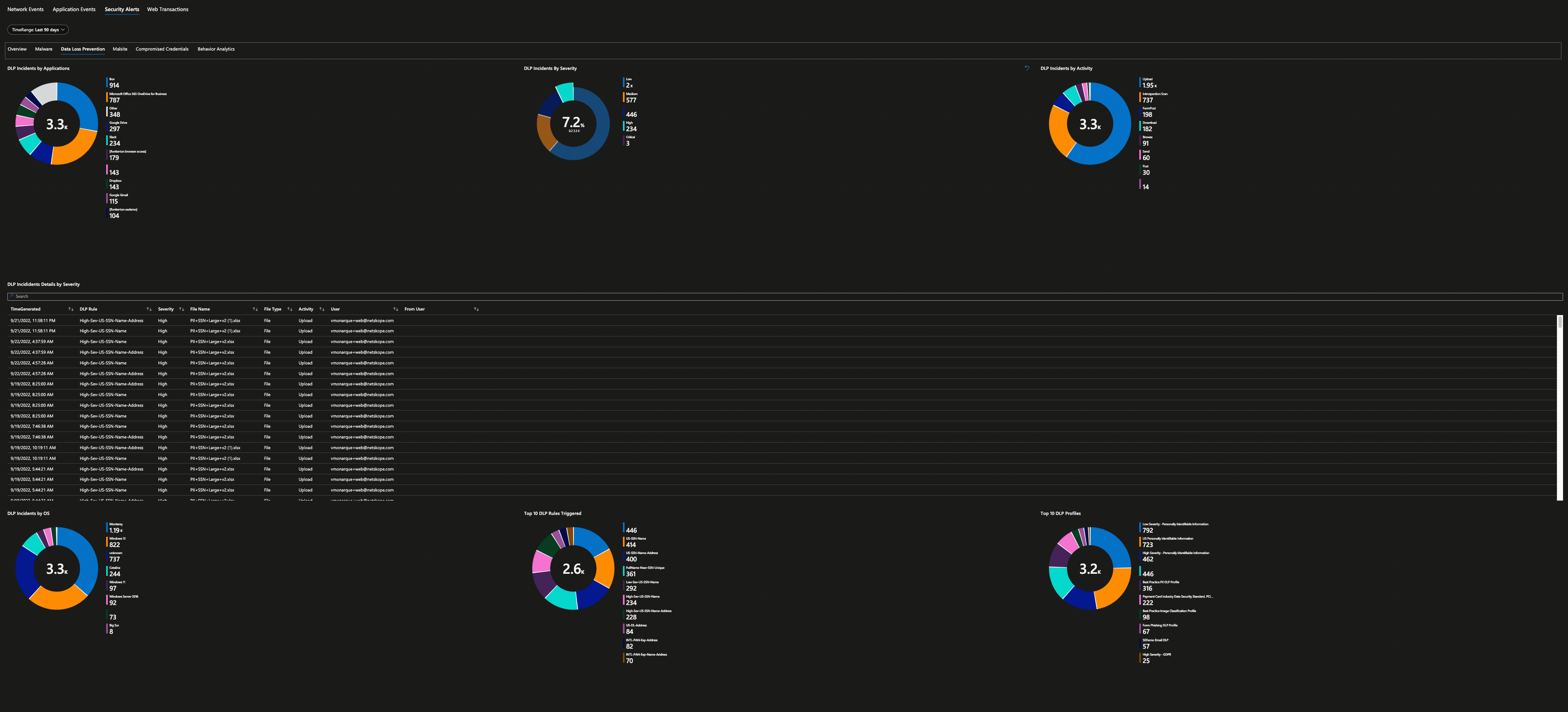
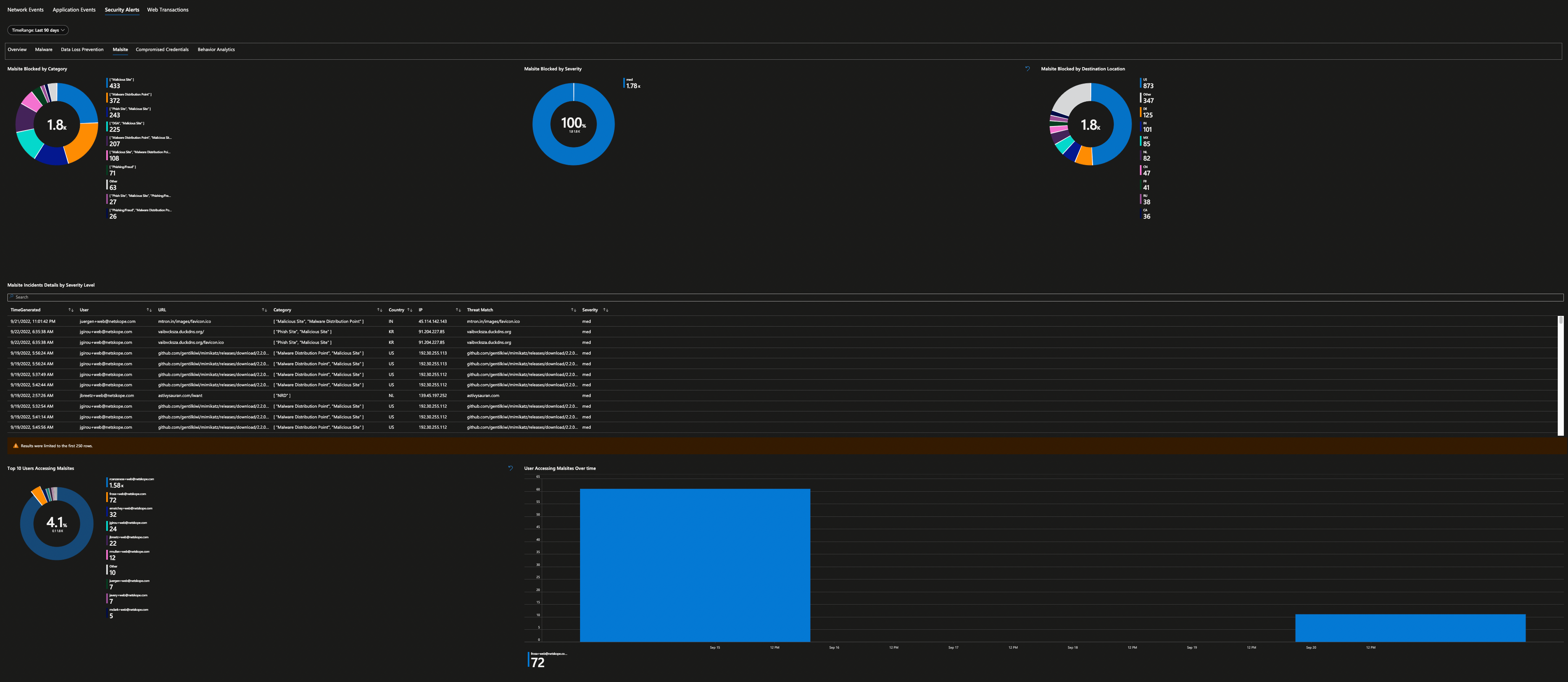
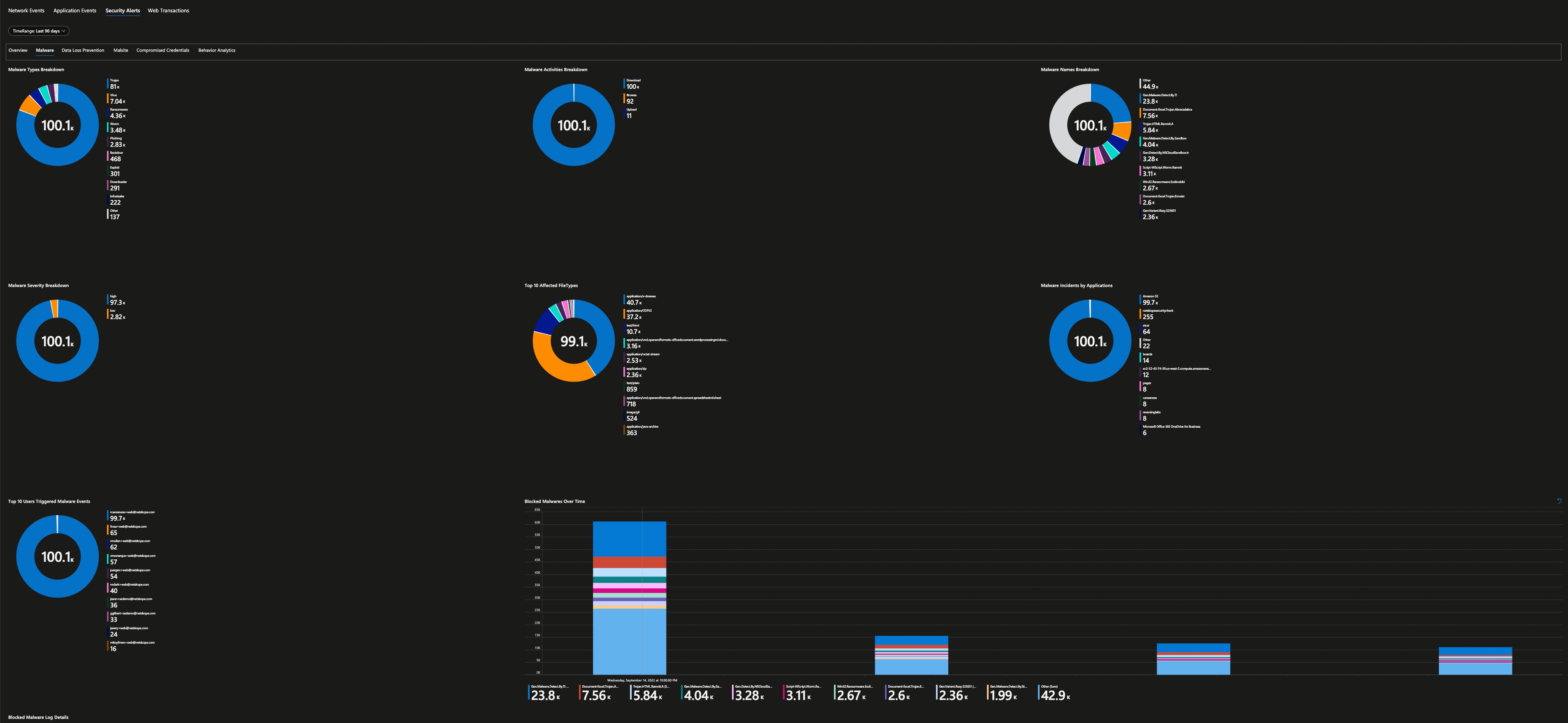
Are you still not convinced even after seeing all the screenshots that it's a good start for any SOC analyst? Well, the workbook is fully customizable so feel free to edits these widgets and produce further insights as you require and do share with Netskope community after all “Sharing is Caring” and I’m sure I can pass the credits to you in our next release of the workbook. Wait, What if I tell you “One More Thing…” to change your mind?

Steve Jobs (May his soul rest in peace) who famously said: "Picasso had a saying 'good artists copy; great artists steal' so it’s my intent to steal the line from Steve’s job keynotes.
As you may be aware, Microsoft Sentinel has a concept of “Playbooks” which are collections of procedures that can be run from Microsoft Sentinel in response to an alert or incident. Playbooks in Microsoft Sentinel are based on workflows built in Azure Logic Apps. Think of it as Security, orchestration, automation and response (SOAR). I have created a Netskope Playbook that provides an integrated solution and allow your SOC to leverage automation to add malicious URL to Netskope as a response to Microsoft Sentinel incidents. You can start automating blocking of these URLs with minimum configurations and effort and this is extremely useful when a Microsoft Sentinel Incident identifies a malicious URL communication, and you want to quickly add it to your Netskope URL block list hence accelerating detection of URLs that should be blacklisted. The playbook is available at Microsoft “GitHub” Repository Here
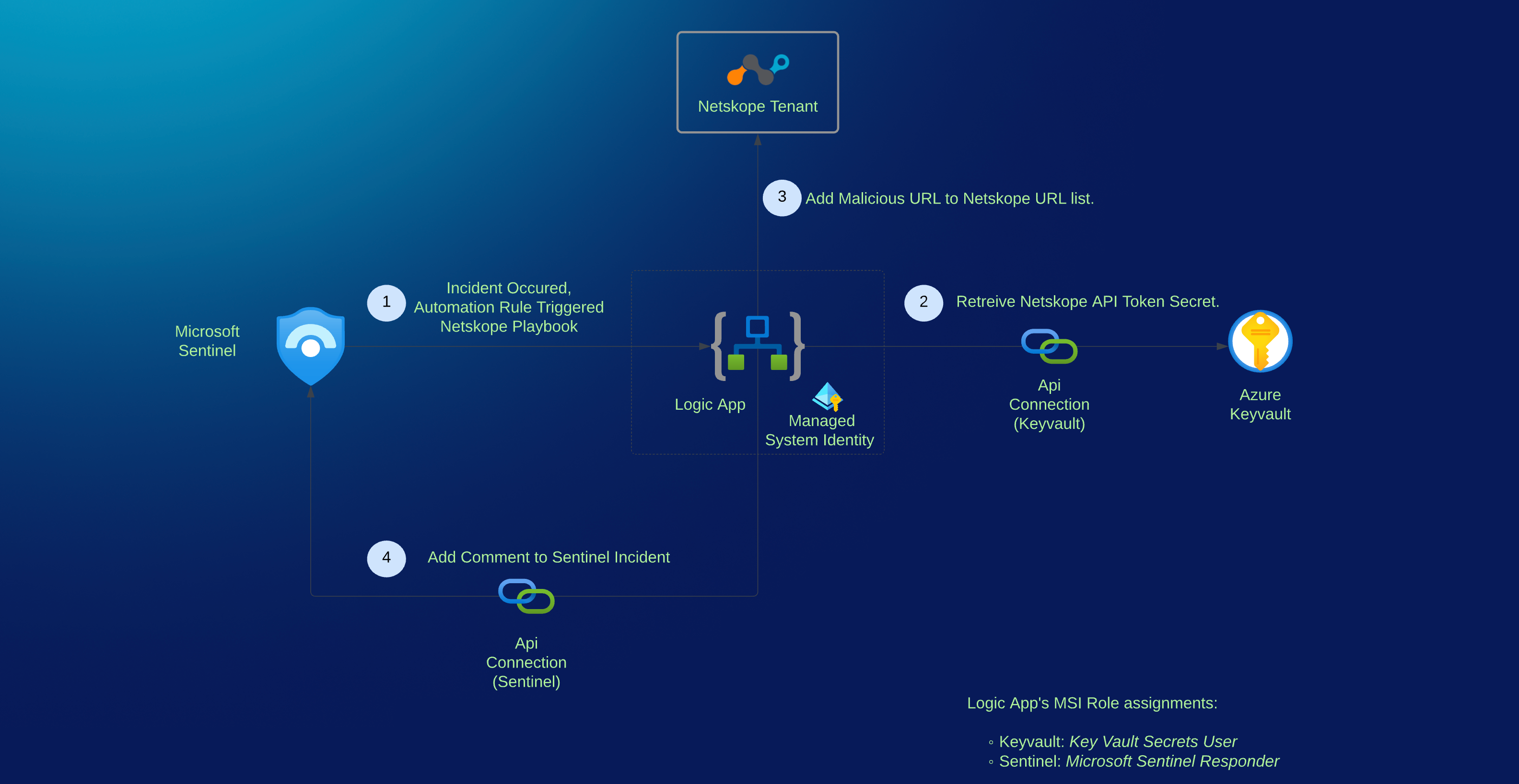
Well, this was a long post folks and I hope you enjoyed reading it as much as I did while writing it, this is all for now ...time to watch Mosquito coast season 2 finale.








