GitHub is a web-based platform that provides hosting for software development projects utilizing the Git version control system. It serves as a collaborative platform for developers to work together on code, track changes, manage projects, and host their code repositories.
GitHub allows developers to create and maintain repositories, which are containers for code and related resources. These repositories can be either public, allowing anyone to view and contribute to the code, or private, restricting access to a selected group of individuals or organizations.
There are some security challenges that we as the Customer Zero team are trying to address for Github. The premise behind the security posture is considering sensitive data movement, malicious repositories, code injection and leakage, ensuring appropriate access controls and permissions. We are currently monitoring and securing access to Github internally with a breadth of products that are developed and maintained by the development and QA teams at Netskope. These capabilities include areas such as inline protection, API-enabled protection, SaaS security posture management (SSPM), and Cloud Firewall, to name a few. In this guide, we will provide a perspective of how Netskope’s products and capabilities are used internally for securing enterprise data.
Real-time Protection
- Traffic originating from managed endpoints [Windows, Mac, and Linux OS], is currently being steered via the Netskope Client to the cloud, where deep inspection takes place, in the form of policies.
- This gives us the capability to manage the traffic to Github in a granular manner.
- Netskope’s Cloud Confidence Index (CCI) has analyzed and classified Github as an enterprise application, and provides an overview of the activities that are identified by the Netskope proxy for inline traffic. These activities include:
- Delete ,
- Login Failed ,
- Login Successful ,
- Logout ,
- Share ,
- View ,
- Invite ,
- Login Attempt
Policy capabilities currently in place:
For Github, some of the real-time policies in place:
- Threat protection (Cloud Threat Exchange) to block upload and download activities based on Development Tools and Technology categories.
- Netskope Cloud Exchange (CE) provides customers with powerful integration tools to leverage investments across their security posture. CE consumes valuable Netskope telemetry and external threat intelligence and risk scores, enabling improved policy implementation, automated service ticket creation, and exportation of log events from the Netskope Security Cloud.
- This protects users from uploading and downloading malicious files and data.
- Monitor upload, download and formpost activities within the Development Tools and Technology category for users who are about to end their employment with Netskope.
- DLP policy which checks for certificate files in the Development Tools category.
- DLP policy which checks for sensitive data (PII, PCI, PHI, SSN, passwords, API security keys) in Github.
API Protection
Netskope API Data Protection works by directly connecting to a cloud app using the APIs published by the app, and uses OAuth to gain delegated access to the app.
Netskope's API Data Protection provides a complementary deployment model to provide cloud visibility, policy, and data security services by directly connecting to a cloud service using the APIs published by the cloud services. The API Connector works in conjunction with the Netskope cloud proxy to provide defense-in-depth security services.
For Github, we currently have an API protection policy similar to that of the realtime policy which checks for sensitive data ((PII, PCI, PHI, SSN, passwords, API security keys) in Github.
This ensures data is protected in Github instances at all times.
SaaS Security Posture Management (SSPM)
SaaS Security Posture Management (SSPM) is a service that provides an organization insight into the security posture of their SaaS applications. According to Gartner, SSPM is defined as “tools that continuously assess the security risk and manage the security posture of SaaS applications. Core capabilities include reporting native SaaS security settings' configuration and offering suggestions for improved configuration to reduce risk."
Some of the benefits of SSPM include:
- Continuous security assessment into policy violations of SaaS apps.
- Guided remediation of misconfigurations.
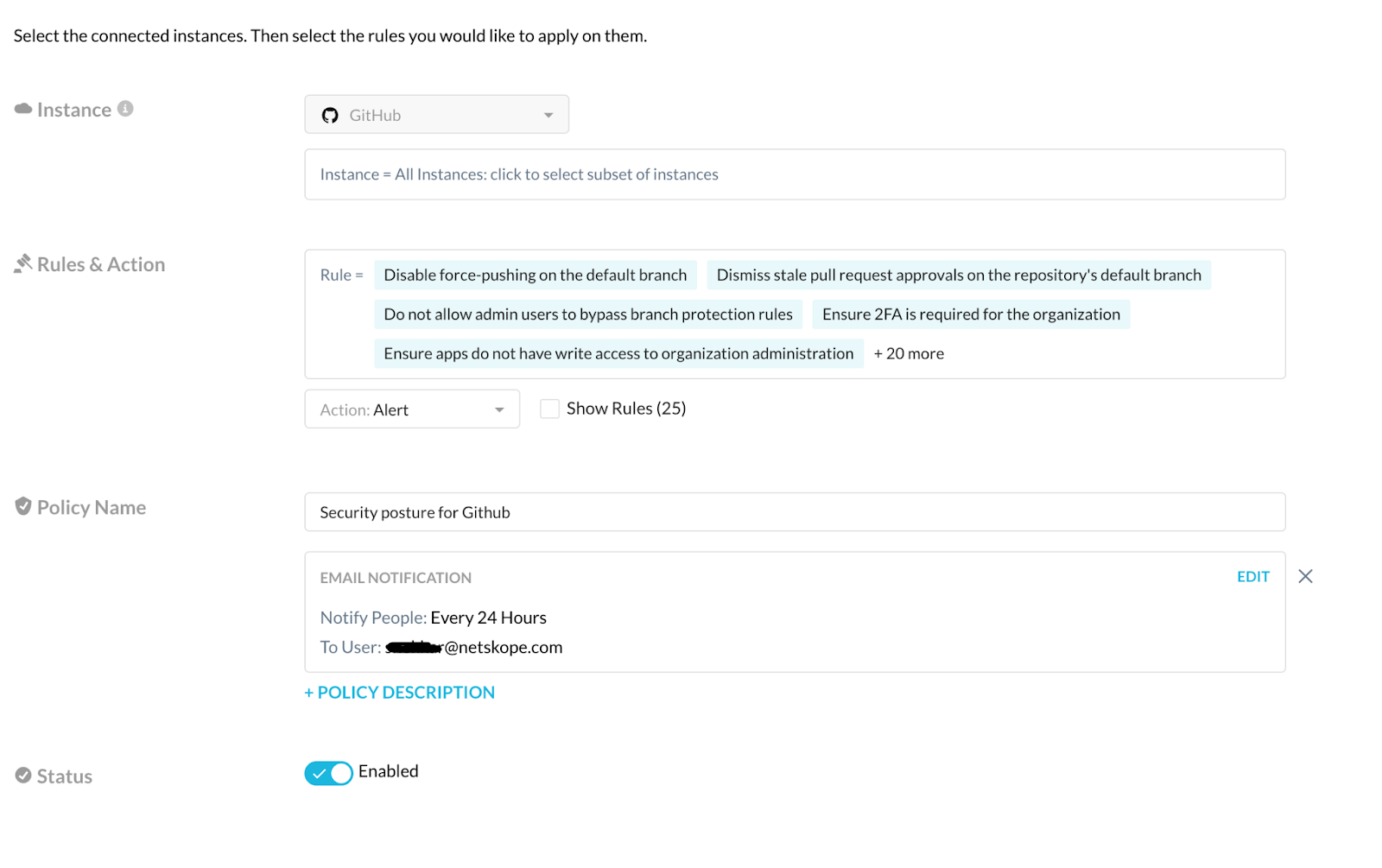
Each of these rules satisfy the following compliance standards:
- CSA-CCM-4.0
- GDPR-2016-679
- HIPAA-1996
- ISO-27002-2013
- NIST-CSF-1.1
- NIST-800-53-4
- PCI-DSS-3.0
- AICPA-SOC-TSC-2017
Nextgen SSPM version supports enhanced features for Github security posture management. This provides some new features such as:
- Visibility to SaaS apps and sub resources (in Inventory page)
- Powerful Netskope Governance Language (NGL) which is a lot easier to use and also helps hunt down details such as:
- The name of all users who have access to any connected apps on Github.
- Names of users having access to a particular connected app installed on Github.
- A list of all connected apps a particular user has with access to on Github.
- Ability to create custom rules quickly based on NGL queries
- Revamped simplified Policies page (doing away with ‘Profiles’)
- Support for cross-application rule
- There is also a findings history visualization available with the next gen feature. This shows the status of compliance findings for Salesforce over the last seven days visually.
- In the policy, we also have an option of sending SSPM rule violation notifications to the concerned SaaS app admin, so they can start working on remediating the alerts accordingly.

- When checking the rules that failed, we can see the NGL definition the rule is based on:
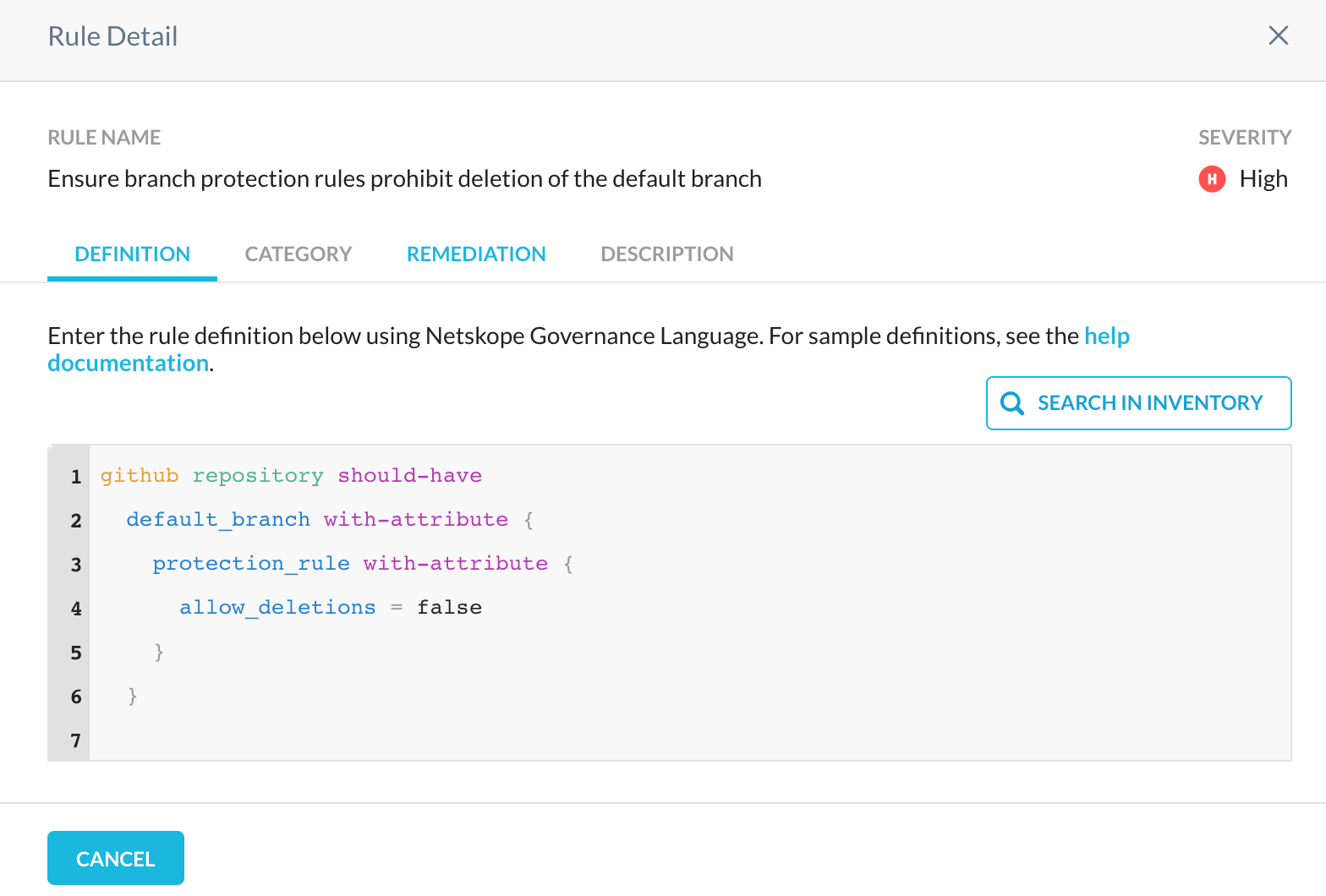
- The definition associated with each rule gives a good reference for searching the inventory for finding resources that don’t satisfy the criteria the rule is checking.
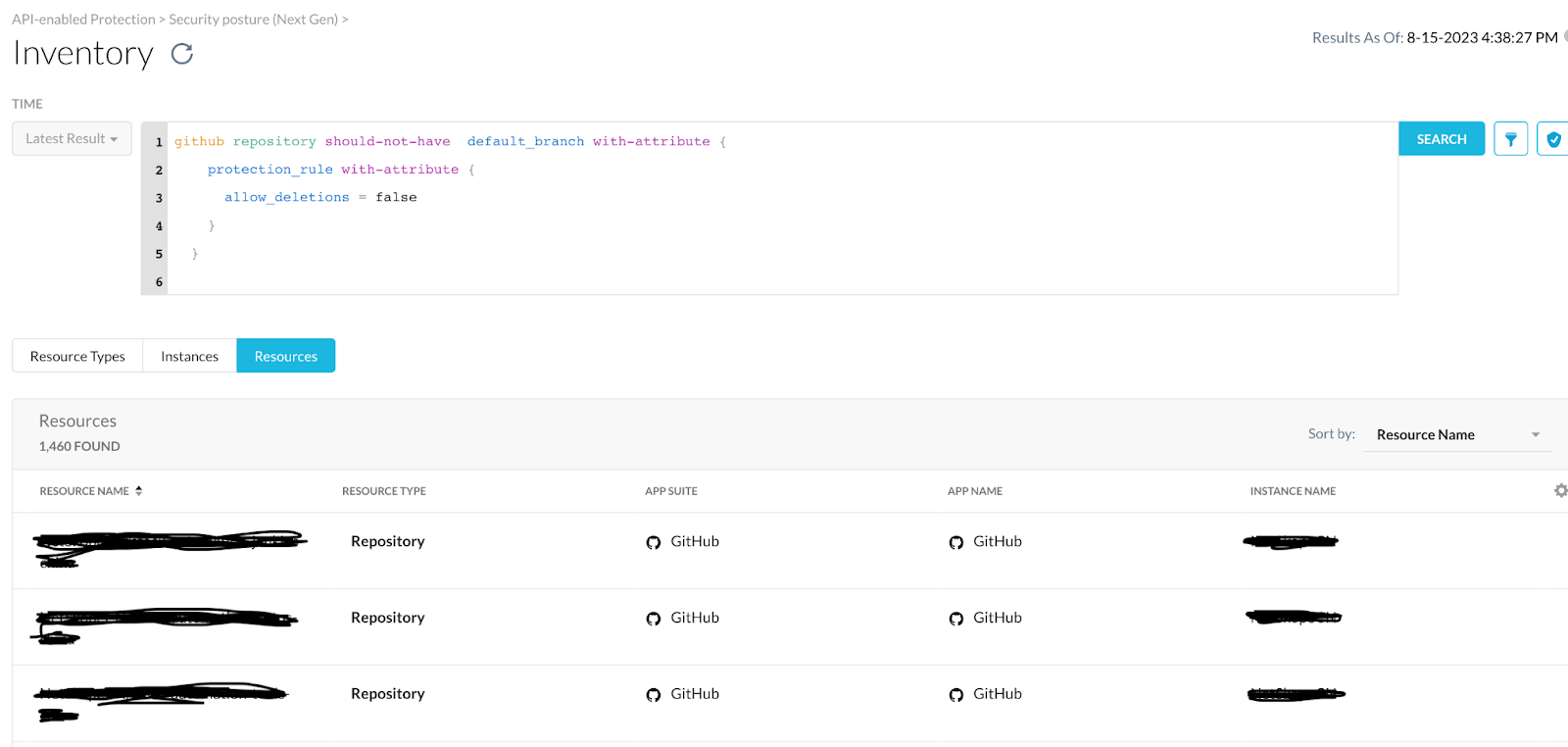
- Netskope begins building an inventory within five minutes of the account configuration. Subsequently, inventory updates are run at the same frequency as the compliance assessments. At the time of the account setup, you can choose to run the compliance assessments every 15 minutes, 30 minutes, 45 minutes, and 60 minutes.
- Reports can also be generated for further analysis of compliance findings.
User Behavior Analytics
For both real-time as well as API-based Github traffic, machine learning algorithms can be used and classified, as part of Netskope Behavior Analytics. Netskope's User Behavior Analytics tool looks at patterns of human behavior, and then applies algorithms and statistical analysis to detect meaningful anomalies from those patterns—anomalies that indicate potential threats. Instead of tracking devices or security events, behavior analytics tracks users. There are a set of predefined Behavior Analytics rules that can be used to create policies for detecting any abnormalities in both real-time, as well as API connector-based Github instances, from a user activity perspective. Few of these are mentioned below:
- A user-based spike in repositories deleted: Deleting code repositories could be an act of sabotage, whereby the malicious actor is attempting to wipe-out the organization's intellectual property or at least disrupt code deployments.
- A user-based spike in sensitive data uploaded to personal apps: Find users that are uploading abnormally large amounts of files/data relative to past behaviour while also raising DLP alerts. The idea is to find a potential malicious insider exfiltrating sensitive corporate data.
- A user-based spike in identities deleted: The user has deleted more identities than usual, which could be an indicator of sabotage. This could be an attempt to disrupt systems or people from their normal access.
- First access from an IP block for the organization: Find users that are coming from /16 IP blocks that have never been seen before for the overall organization. The idea is to find potentially compromised credentials being used outside of the organization.
- A user-based spike in downloads from Corporate applications: Find users that are downloading abnormally large amounts of files/data relative to past behaviour. The idea is to find a potential malicious insider exfiltrating corporate data.
Application Activity Summary dashboard can be used in Advanced Analytics to get some insights of trends for Github.
Hope this blog post helped in providing a brief insight into how Github is protected at Netskope for reference. Please feel free to discuss any concerns or questions that you may have.










