In this article we’ll demonstrate how you can implement automatic remediation for security posture violation findings discovered by Netskope Cloud Security Posture Management (CSPM).
Netskope CSPM continuously assess public cloud deployments to mitigate risk, detect threats, scan and protect sensitive data and monitor for regulatory compliance. Netskope simplifies the discovery of security misconfigurations across your clouds. Netskope Auto-Remediation framework for AWS enables you to automatically mitigate the risk associated with these misconfigurations in your AWS cloud environment.
Netskope CSPM security assessment results for such security benchmark standards as NIST, CIS, PCI DSS, as well as for your custom rules are available via the View Security Assessment Violations Netskope API.
Netskope auto-Remediation solution for AWS deploys the set of AWS Lambda functions that query the above Netskope API on the scheduled intervals and mitigates supported violations automatically.
You can deploy the framework as is or customize it to mitigate other security violations and to meet your specific organization’s security requirements.
The source code and deployment instructions are available at GitHub repository.
Note, that you need to deploy this solution in each AWS region you opted in for. It’s recommended to deploy the remediation functions on the delegated security management account. You can choose to deploy them on the same account that’s been used as delegated administrator for Amazon GuardDuty, AWS Security Hub, or another delegated AWS account. Following AWS best security practices, it’s not recommended to deploy the solution on the AWS Organization Management account. Deployment of the remediation functions done using AWS-autoremediation CloudFormation template.
To remediate security violations findings across all your organization’s accounts, you need to deploy the cross-account AWS IAM roles on all accounts, including the delegated security management account. Cross-account roles deployed using AWS-autoremediation-target CloudFormation template. You can deploy it using AWS CloudFormation StackSet or using your cloud orchestration tools.
As a pre-requisite, you need to enable AWS Systems Manager (AWS SSM) on all your accounts and AWS regions. AWS SSM Automation used to remediate violations for such compliance rules as rule 4.1 of the CIS AWS Foundations standard “Ensure no security groups allow ingress from 0.0.0.0/0 to port 22“.
While this framework can be used to mitigate multiple violations, we’ll show you how to automatically mitigate violation 2.9 of the CIS AWS Foundations standard – Ensure VPC flow logging is enabled in all VPCs.
Below we assume you already configured Netskope CSPM Continuous Security Assessment for Amazon Web Services for your AWS accounts and included AWS CIS Foundations Benchmark in your Security Assessment Policy
Setting Up
Follow the deployment steps in the GitHub repository and deploy the solution in your AWS delegated security management account and deploy cross-account AWS IAM roles on all AWS accounts.
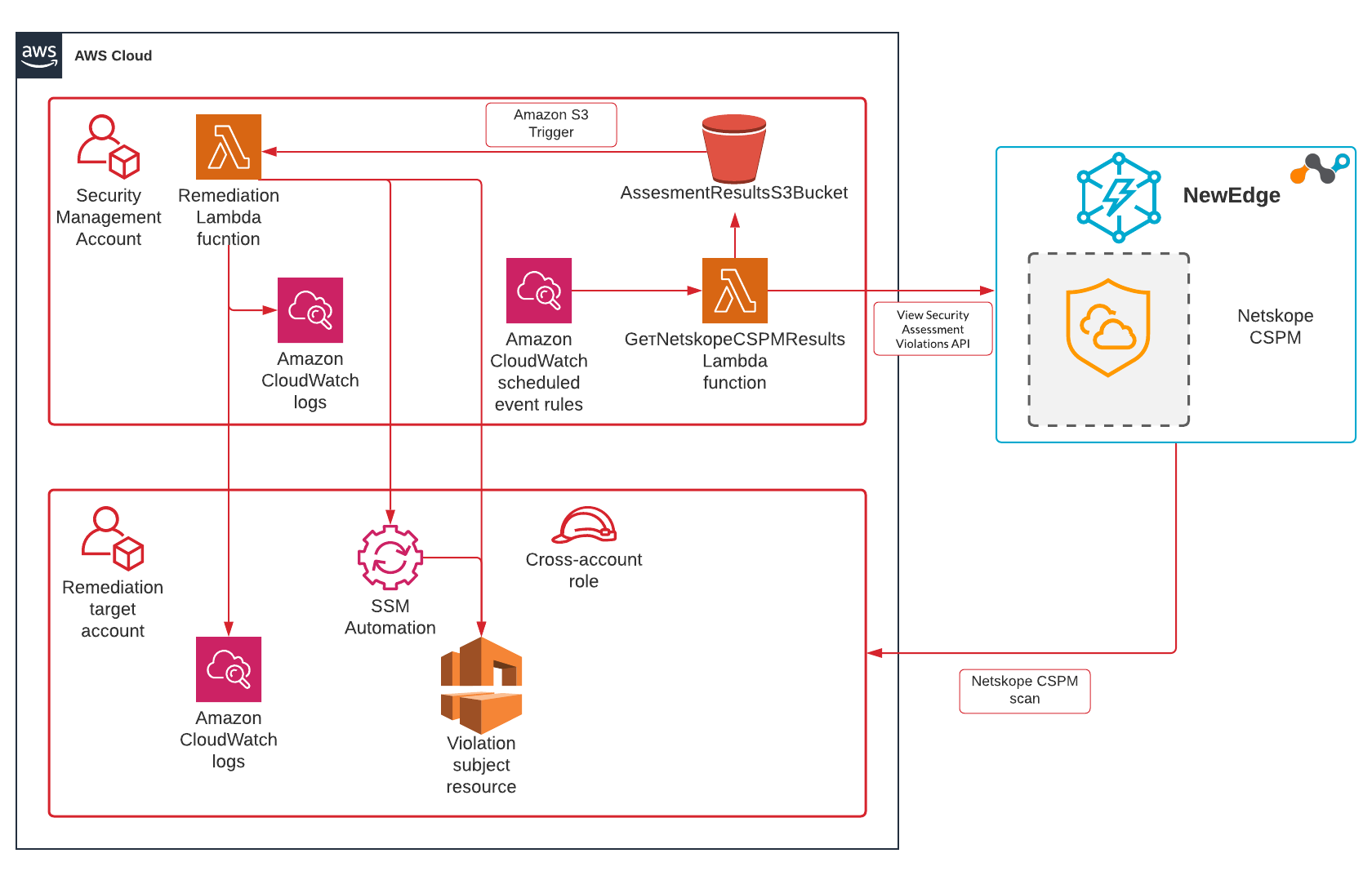
The solution deploys GetNetskopeCSPMResults Lambda function and corresponding AWS CloudWatch scheduled rule to query Netskope View Security Assessment Violations Netskope API.
When violations of the CIS rule 2.9 in the current AWS region found in the API response, GetNetskopeCSPMResults Lambda function stores them in the AssesmentResultsS3Bucket, which has Amazon S3 Trigger configured to call CIS12029VPCFlowLogsLambda Lambda function. This Lambda function reads the violations from the file, verifies if the resource is still not compliant and configures VPC flow logs if required. Cross-account IAM roles used to remediate violations across the organizations’ accounts.
See it in action.
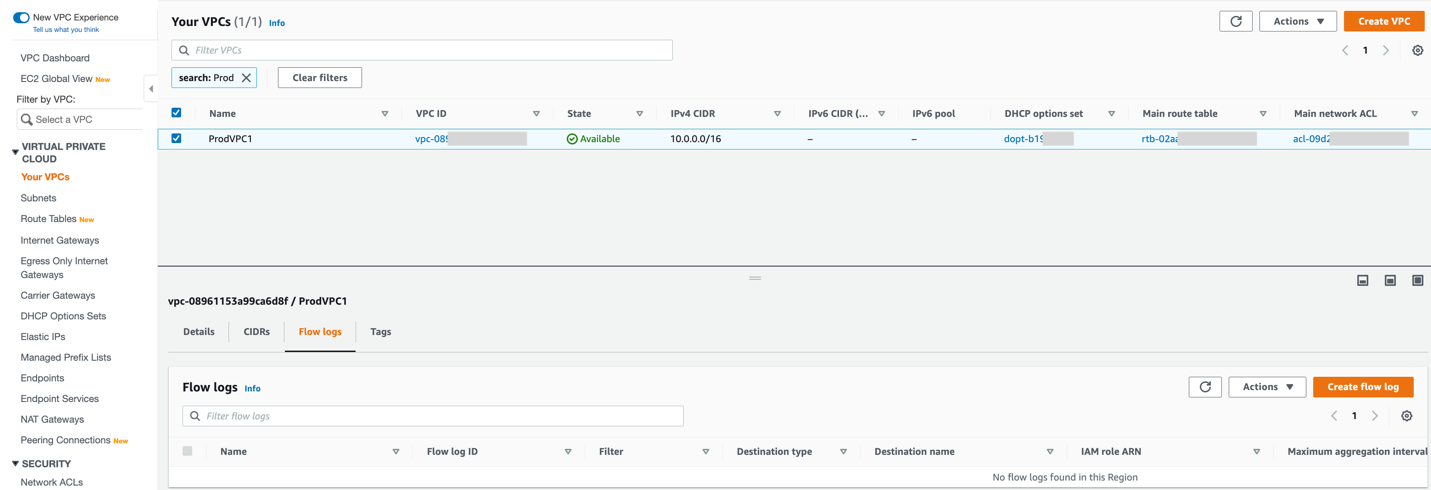
Let’s take a look at the non-compliant AWS VPC that doesn’t have VPC Flow Logs provisioned:
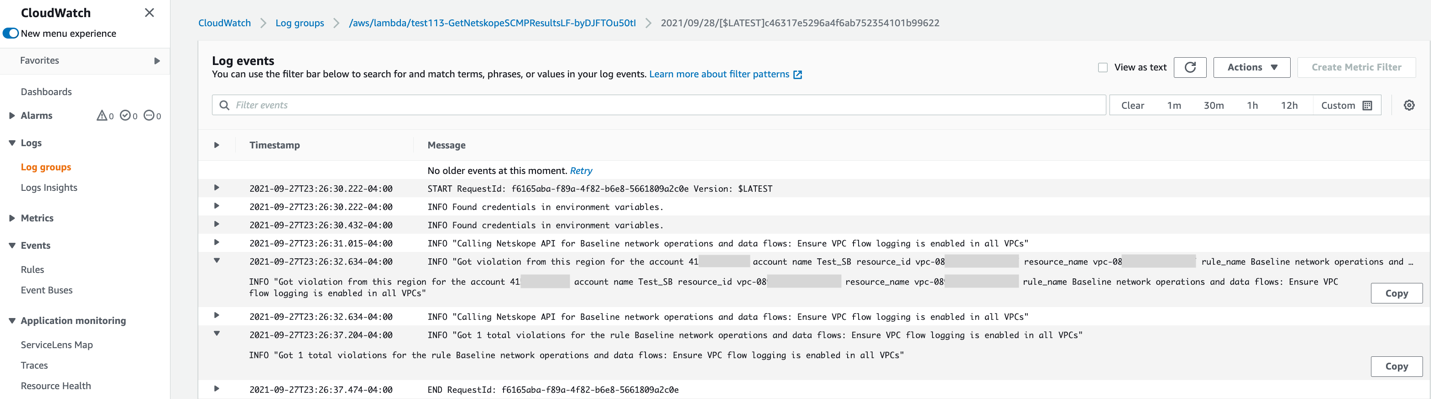
GetNetskopeCSPMResults Lambda function has been triggered by the CloudWatch scheduled rule and retrieved corresponding violation from the Netskope API:
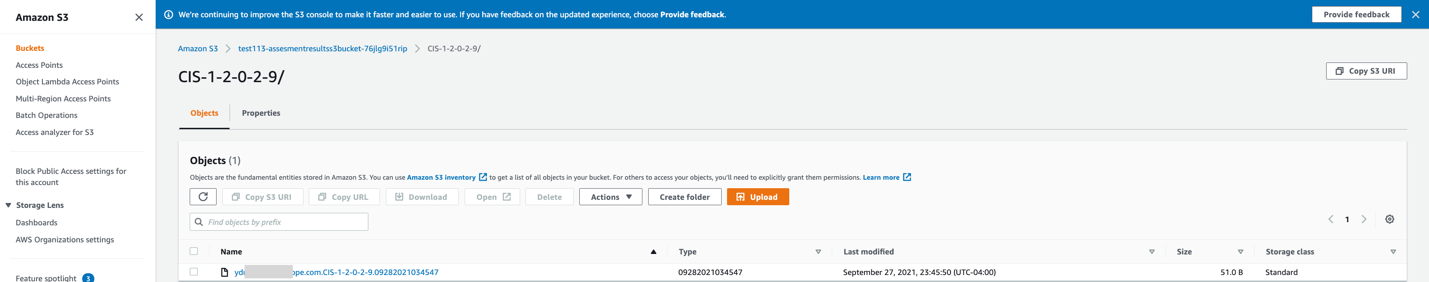
GetNetskopeCSPMResults saves the violation file in the S3 bucket:
Which triggers CIS12029VPCFlowLogsLambda Lambda function that provisions VPC Flow Logs for the corresponding VPC:
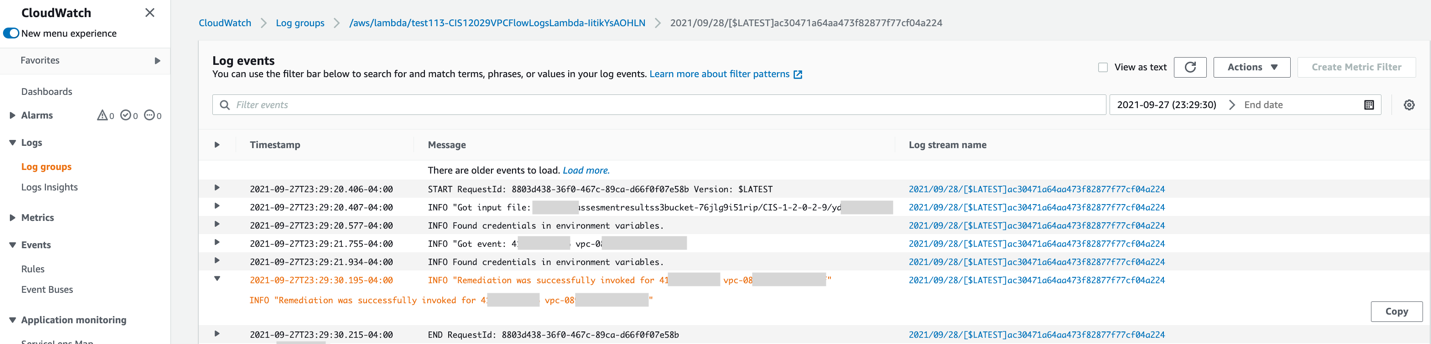
Now let’s take a look at the VPC and you can see that now VPC has Flow Logs provisioned:
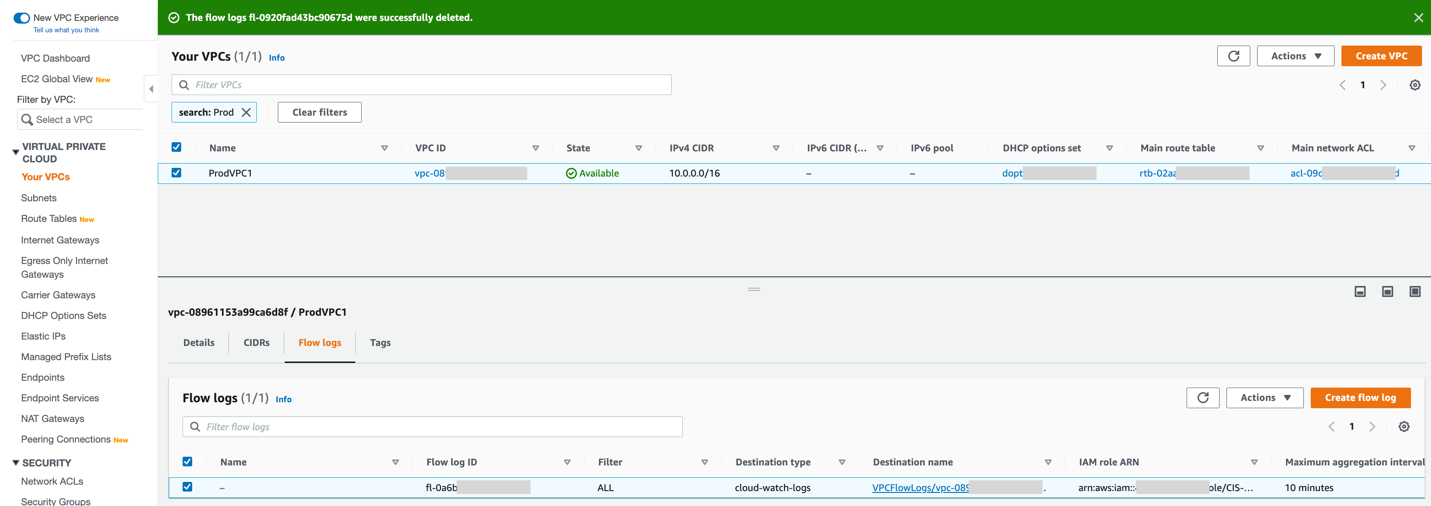
You’ve just seen how you can use Netskope Auto-Remediation Framework to automatically mitigate security violations findings discovered by Netskope SCPM. You can easily deploy other supported remediations or to develop your own remediation functions based on this example.
Supported Auto-Remediation Functions
|
Profile |
Service |
Rule Name |
Action |
|
CIS-FNDAWS-1.2.0 |
CloudTrail |
Secure audit trails so they cannot be altered: CloudTrail Log Files Lack Integrity Validation |
The auto-remediation lambda function invokes the SSM runbook: AWSConfigRemediation-EnableCloudTrailLogFileValidation which enables log file validation for AWS CloudTrail. |
|
CIS-FNDAWS-1.2.0 |
EC2 |
Communications and control network protection: Ensure no security groups allow ingress from 0.0.0.0/0 to port 22
|
The auto-remediation lambda function invokes the SSM runbook: AWS-DisablePublicAccessForSecurityGroup which removes the inbound rule entry of Source ‘0.0.0.0/0’ with port 22 and port 3389 from security groups |
|
CIS-FNDAWS-1.2.0 |
EC2 |
Communications and control network protection: Ensure no security groups allow ingress from 0.0.0.0/0 to port 3389 |
The auto-remediation lambda function invokes the SSM runbook: AWS-DisablePublicAccessForSecurityGroup which removes the inbound rule entry of Source ‘0.0.0.0/0’ with port 22 and port 3389 from security groups |
|
CIS-FNDAWS-1.2.0 |
EC2 |
Baseline network operations and data flows: Ensure VPC flow logging is enabled in all VPCs |
The auto-remediation lambda function creates the flow logging for Amazon VPC if not exist. |
|
BPR-AWS-1.0.0 |
EC2 |
Communications and control network protection: Ensure no rule exists which allows all ingress traffic in default Network ACL |
The auto-remediation AWS Lambda function removes the rule entry from the Default Network ACL that allows all traffic ingress for all the protocols |
|
BPR-AWS-1.0.0 |
EC2 |
Communications and control network protection: Ensure no rule exists which allows all ingress traffic in Network ACL which is associated with a subnet |
The auto-remediation AWS Lambda function removes the rule entry from the specified Network ACL that allows all traffic ingress for all protocols |
|
CIS-FNDAWS-1.2.0 |
IAM |
Remote access: Ensure access keys are rotated every 90 days or less. |
The auto-remediation AWS Lambda function inactivates the access key which is older than 90 days for the user |
|
BPR-AWS |
RDS |
Access permissions and authorizations: Ensure RDS Instances do not have Publicly Accessible Snapshots |
The auto-remediation AWS Lambda function disables public access of all snapshots of given database instances |
|
BPR-AWS |
Redshift |
Access permissions and authorizations: Ensure Redshift Clusters are not Publicly accessible |
The auto-remediation AWS Lambda function invokes the SSM runbook: AWSConfigRemediation-DisablePublicAccessToRedshiftCluster which disables public accessibility for Amazon Redshift cluster. |
|
BPR-AWS-1.0.0 |
S3 |
Ensure S3 Bucket is not publicly accessible. |
The auto-remediation lambda function enables IgnorePublicAcls and RestrictPublicBuckets public block access settings, which blocks the public access to the Amazon S3 buckets |







