Every company uses tagging and resource labeling in their own way. Among other uses, mature labeling practices are a great way to identify resources to their cost centers, keep track of their purpose and contents for compliance requirements and for naming ownership and maintenance responsibilities. Netskope Security Posture Management can help enforce good labeling practices with a few simple custom rules suited to your needs.
How to ensure that every resource of a given type is labeled properly
Most common use case for label policy enforcement is to ensure that resources are labeled at all. For example, if we want to ensure that every EC2 instance in our AWS Cloud carries a label named "org-unit", we can write the following rule for AWS monitoring:
EC2Instance should have Tags with [ Name eq "orgunit" ]
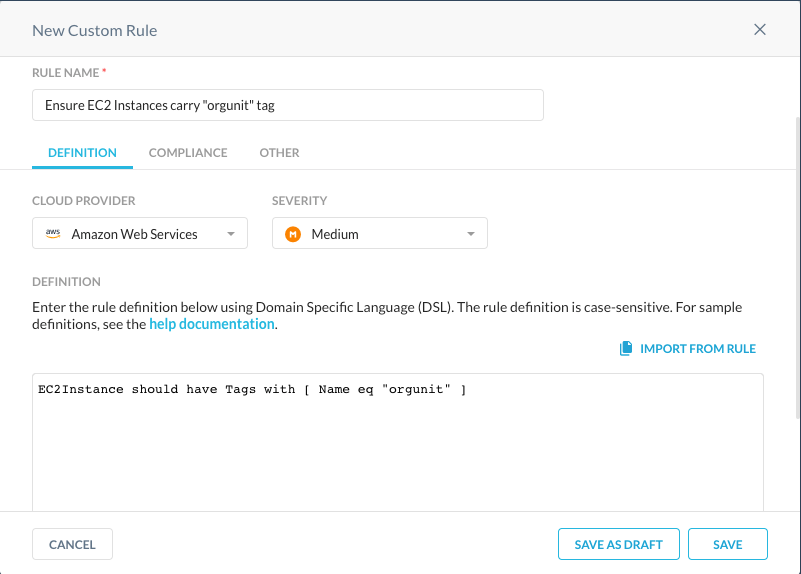
Once added to a compliance profile and being monitored by a Security Posture Policy, this rule should show in the Security Posture view with findings like this:
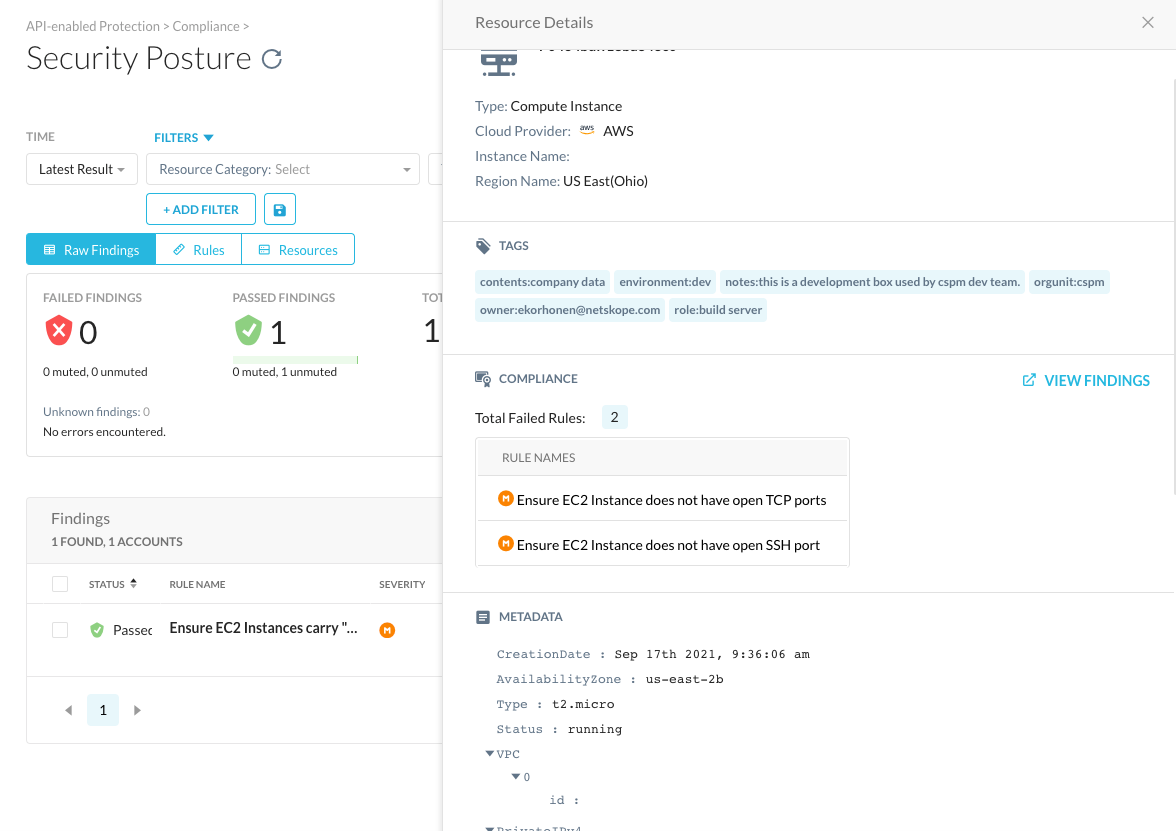
Likewise, We can use a single rule to detect violations of multiple tagging practices. E.g. rule
EC2Instance should have Tags with [ Name eq "orgunit" ] and Tags with [ Name eq "owner" ]
would alert if either of the "orgunit" or "owner" tags would be missing.
You can also add more complex logic for tag enforcement. You might want to ensure that no resources carrying a certain label contain severe misconfigurations. To illustrate, we describe multiple rules for detecting public storage buckets that have been labeled to contain Personal Identifiable Information (PII) here.







