I have read the Verizon 2022 DBIR and I could not help but noticing that some of the risks outlined in the document can be mitigated by our platform. More in detail:
- At page 8, the report states that "Error continues to be a dominant trend and is responsible for 13% of breaches." This finding is heavily influenced by misconfigured cloud storage. While this is the second year in a row that we have seen a slight leveling out for this pattern, the fallibility of employees should not be discounted.” This is obviously something that we can mitigate with our CSPM.
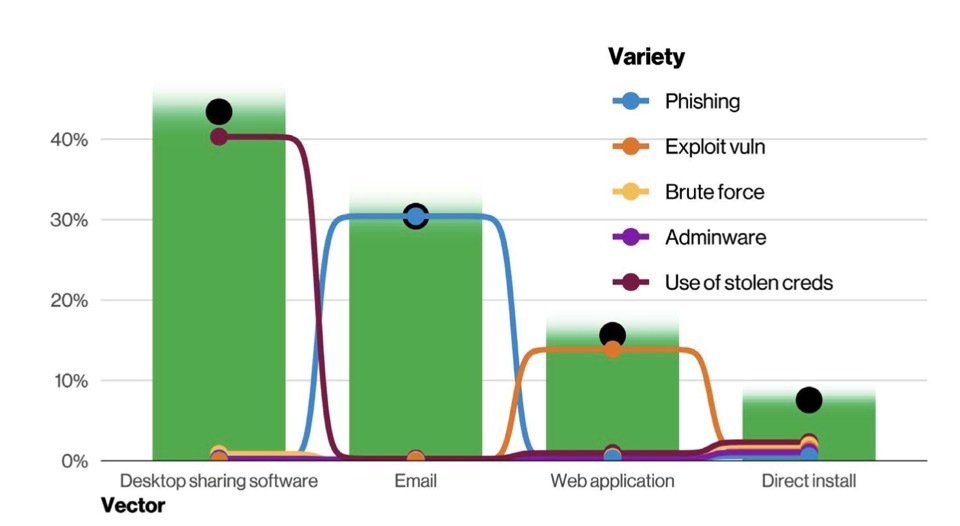
- An additional important message is that remote access plays an important role for attackers. More in detail (page 14) "remote access established by the attacker is important and that there are a slew of ways of creating that persistent access. In terms of vectors, these align well with the notion that the main ways in which your business is exposed to the internet are the main ways that your business is exposed to the bad guys. Web application and Email are the top two vectors for breaches. This is followed by Carelessness, which is associated with Errors such as Misdelivery and Misconfiguration. Next we have Desktop Sharing Software, which captures things like Remote Desktop Protocol (RDP) and third-party software that allows users to remotely access another computer via the Internet. Unfortunately, if you can access the asset directly over the internet simply by entering the credentials, so can the criminals. Please also note that desktop sharing software is one of the main vectors, (page 26). This is a threat that we can mitigate with our NPA.
- It is also interesting the chart at page 28, according to which 40% of Ransomware incidents involved the use of Desktop sharing software, again, something that can be secured with our NPA.
- The process of exploitation of vulnerabilities described at page 31 involves an opportunistic model, meaning that the threat actors start with scanning for IPs and open ports (and then, simplifying things a little bit, they move laterally looking for vulnerabilities to exploit). Even in this case we can use CSPM to find misconfigured (open) services and we can hide them via NPA. This also applies to the mitigation of the risks described in the “Basic Web Application Attacks” section, with the caveats that we can mitigate the risks for services exposed to the organisation (or its partner ecosystem) and not to portals accessed by internet users.
- I would also mention that the UEBA component can mitigate the risk of internal incidents. Despite they accounted for about 20% of breaches (see the chart at page 11), the impact of a single incident is quite significant (see Figure 13 at page 12).
Other elements to note:
- The use of stolen credentials and phishing attacks plays an important role for system intrusions. The most common methods to steal credentials are (1) phishing attacks or (2) the exploitation of vulnerabilities on VPN concentrators or publicly-facing servers. This trend has become so common that you have probably heard about Initial Access Brokers, specific criminal groups who steal credentials and sell or outsource them to other criminal gangs. Our NG SWG can mitigate the risk of phishing attacks via our threat intelligence (and the integrations made possible by Cloud Exchange), and some DLP best practices that we have created. (2) is another threat that can be mitigated switching to a Zero Trust paradigm.
- Similarly, the DBIR outlined a surge of malware delivered via Office docs (Figure 37 at page 27). This is something that we also noted but… The timeframe of analysis ranges from November 1, 2020 to October 31, 2021, and since the beginning of 2022 the percentage of malicious Office docs is constantly decreasing, both because of the takedown of Emotet (which is now testing other distribution mechanisms) and because of additional protection measures applied by both Microsoft and Google for Office Docs. In any case we have specific ML detectors for Office Docs (which are a peculiar characteristic of our advanced threat protection engine that also include advanced heuristics, and a sandbox now able to map the tactics and procedures used by the attackers in the MITRE ATT&CK model.)







