Netskope Adoption Welcome Pack
Thank you for your investment and welcome to Netskope! Your customer experience team is here to ensure you have everything you need to make your Netskope journey a success.
Attention ! Don’t miss these crucial resources.
While you get started with Netskope, please ensure to use the below links to access various Netskope portals and resources. Brownie : Don’t forget to bookmark these links for future reference.
| Task | Link |
| Request your first support account through your Netskope representative | |
| Create a Netskope Academy Customer Learning portal account | |
| Create a support portal account and “Follow the sections shown below” for important announcements. | |
| Subscribe to the Trust Portal to get live Maintenance and Incident updates | |
| Check out our Knowledge Base articles | |
| Join the Netskope Community | |
| Subscribe to receive the latest Product Updates | |
| Stay current on Netskope's Events including Webinars, Workshops, User Groups | |
| Stay up to date on Release Notes and research knowledge base articles | |
| Measuring your success using Netskope Reporting dashboards | |
| Learn about all the tools available to accelerate your Adoption Journey |
Following important sections from the support portal
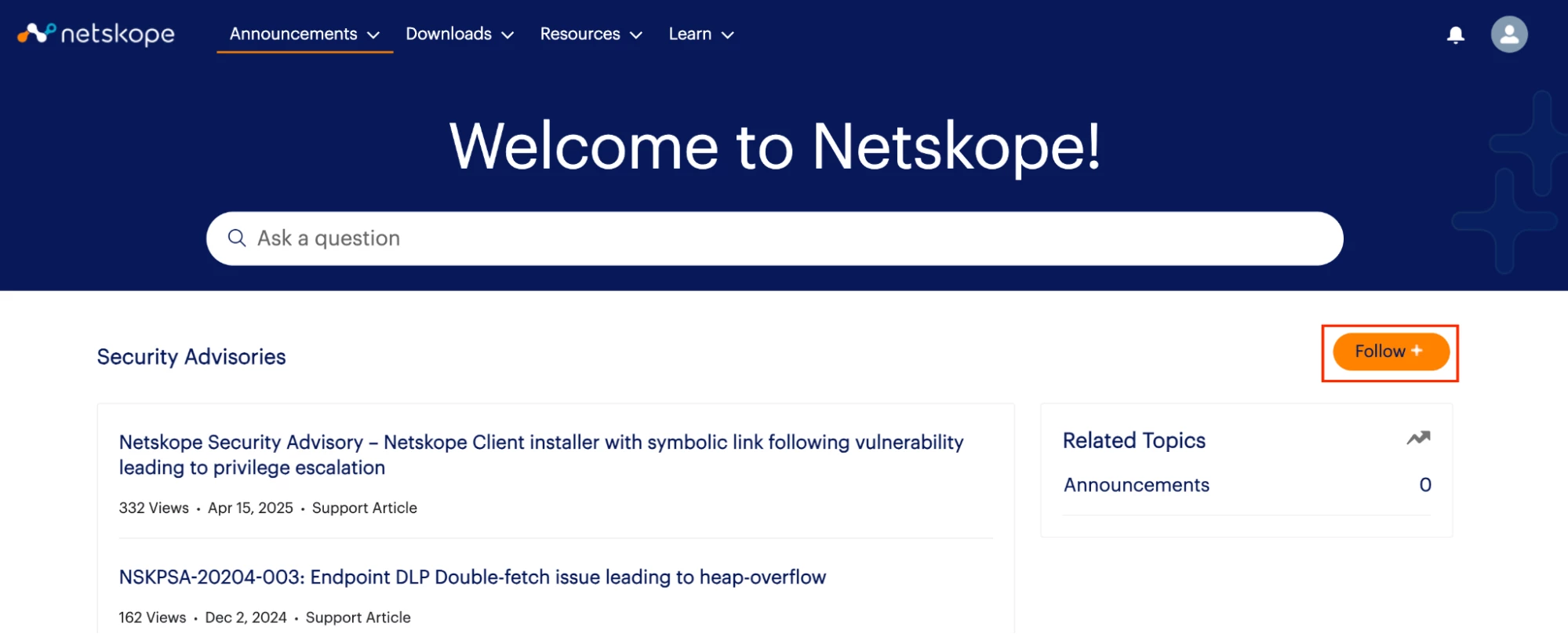
Once you have created your support portal account, it is crucial that you follow on to the below highlighted sections to receive notifications within your email inbox related to Service Notifications, Scheduled Netskope Data Center Maintenance, Threat Advisories, Security Advisories etc.
Hit the follow button at the right as shown below
Netskope Resources
We are here to guide you on your self-paced path to success, however, should you need help along the way, you can use these resources.
| Resource | Type of Request | Contact Methods |
| Technical Support |
|
Note: additional support accounts can be requested through a support case. Global Support Numbers:
|
| Technical Support |
|
Note: Select case type of: How To Question |
Getting Started
Netskope has developed foundational learning modules focused on enabling administrators with best practice knowledge on core components of the SASE platform.
We have broken these up into essential and recommended modules for easy, self-paced learning. The following Jump Start series provides you with the fundamentals to get started with Netskope and are essential to know at the beginning of your journey.
| Netskope Component | Essential Learning Modules |
| Jump Start: Getting started with Netskope |
Expanding on the Jump Start series, we recommend you progress your knowledge by understanding some of the Administrative processes.
| Netskope Component | Recommended Learning Modules |
| Client Configuration & Troubleshooting | |
| Working with Netskope Technical Support | |
| Role Based Access Control | |
| Netskope Integrations | |
| Netskope Insights |
Self-Serve: Operationalization & Adoption Checklist (Also increases your Tenant Health Score!)
Now that you have completed the fundamental knowledge phase, we move into the Operationalization & Adoption phase, where you use that knowledge to configure policies using the best practices and increase your Tenant Health score.
Match the Netskope component you are subscribed to and mark off the tasks when completed in the checklist below at your end.
Instructions
The Netskope Component describes a tenant configuration, client configuration, product configuration or a process that is recommended by Netskope to ensure you are aligned with the foundational best practices.
Go through each line item and continue to align your tenant as per the recommendations defined below.
| Netskope Component | Task Checklist | Reference | |
| Client Configuration | Client Auto Upgrade Configuration | Client Auto Upgrade Configuration : Ensure the client versions are set to Auto upgrade to Latest Golden release | |
| Client Configuration Settings | DTLS : Ensure DTLS protocol is enabled in all client configurations | ||
| Advanced Debug : Ensure that the debug level is set to "info" or disabled in all client configurations | |||
| Allow disabling of all client services together : Ensure the option to disable the Netskope client services is not allowed in client configuration | |||
| Hide client icon on system tray :Verify that the system tray icon is visible in all client configurations | |||
| Password protection for client uninstallation : Ensure password protection is enabled for client uninstallation in all configurations | |||
| Protect client configuration and resources : Verify that client self-protection is enabled to prevent tampering with client processes and files | |||
| Number of Client Configurations | Number of Client Configurations : Ensure that there are multiple client configurations created apart from default configuration | ||
| Client Version Distribution | Client version Distribution Maturity : Ensure that Netskope clients are upgraded to Latest Golden release across the environment | ||
| DLP Policies and Configuration | Forensics Profile Configuration | Ensure that Forensics profile is configured : Netskope recommends using a public cloud storage (like Azure Blob, Amazon S3) as a forensic destination over a SaaS storage app, because a SaaS storage app cannot scale for high frequency forensic write workloads. | |
| DLP policies Configuration specific to Industry needs | Ensure to create Data protection policies specific to your compliance, industry regulations to ensure there are essential safeguards in place to protect your sensitive data. | ||
| General Tenant Configuration | Basic Security Settings | Privacy Notice : Privacy Notice should be enabled | |
| Idle Timeout : This should be set to automatically log out inactive users | |||
| Password expiry : Password expiry should be configured to enforce regular password changes | |||
| Multiple concurrent logins : Multiple concurrent logins should be disabled for Security reasons | |||
| IP Allowlist : This should be enabled to restrict access from unauthorized IP addresses | |||
| SSO Enablement | SSO should be enabled and properly configured in order to mitigate security risks associated with console (Web UI) access. | ||
| MFA for local admin users | Enable MFA for all local administrator accounts Consider implementing a policy requiring MFA setup before granting administrative privileges Regularly audit administrator accounts to ensure MFA remains enabled | ||
| Administrator provisioning | Ensure RBAC is provisioned as per roles within the organization | ||
| Netskope personnel access | Netskope recommends tenants to enable SSO in order to allow Netskope personnel access to the tenant. | ||
| SSL Policies | SSL DnD policies | SSL DnD policies limit Netskope’s ability to have visibility on the traffic. Ensure that SSL DnD is only configured for required traffic | |
| SSL DnD Policy for Microsoft 365 | Check if there is a SSL DnD (Do Not Decrypt) policy set for Microsoft365 (Office 365) related web traffic. Following Netskope recommendations, such a policy should not be enabled. | ||
| SWG Policies | Ads Block Policy | Ensure that there is a policy that blocks web advertisement content | |
| DoH Block Policy | Ensure that DoH (DNS over HTTPS) is being blocked. | ||
| Safe Search Enablement | Ensure that Safe Search is being enabled on the tenant. | ||
| Real time policy Blocking AUP categories | Ensure that all categories identified as inappropriate or risky are being blocked. | ||
| Dynamic URL Classification | Ensure that Dynamic URL Classification is enabled on the tenant | ||
| Policy to Block Risky Destination Countries | Ensure that web traffic to high-risk countries is properly blocked through web security policies. | ||
| Steering Configuration | Bypassed Traffic Logging | Ensure that Bypass Traffic logging is set | |
| Steering Configuration Best practices | Ensure that there are Multiple steering configurations leaving default at the bottom, Test steering configuration applied to subset of users, Review Exceptions in different configurations, Ensure that Steering mode is set as per entitlement
| ||
| Threat Protection Policies | Real Time Policy Blocking Security Risk Categories | Ensure that there is a policy blocking Security Risk categories. | |
| Real Time Policy with Threat Protection Profile | Ensure that there is a policy to block Malicious payloads | ||
| IPS Enablement | Ensure that IPS is enabled |
Real-Time Protection Policies - Best Practices
Below are the best practice inline policies for Netskope. Ensure to have these policies configured in the structure as shown below for your tenant.
A deep understanding of each of these policies can be obtained from this link
| Policy group | Policy | Reference Link | Sr No |
| Threat | Block DNS over HTTPs | 1.1 | |
| Block security risk categories | 1.2 | ||
| Block traffic destined to High risk destination countries | 1.3 | ||
| Block upload/download of malicious files | 1.4 | ||
| Utility | Policy Sync test | 2.1 | |
| RBI | Steering all RBI categories with action set to isolate | 3.1 | |
| CASB (Activity Oriented) | Allow Sanctioned apps | 4.1 | |
| Cloud firewall | Block Apps - L7 based policies | 5.1 | |
| Block Apps - L3 based policies | 5.2 | ||
| Web (Category based) | Block online Ads | 6.1 | |
| Block all acceptable use categories | 6.2 | ||
| NPA | Allow access to Private apps | 7.1 |
If you need assistance in understanding these best practise checklist or aligning your tenant in accordance with the best practices, you can raise a ticket at support.netskope.com by using the “Case Type - How to Questions”
Done Already? Congratulations! Your Level 1 Tenant Health score is 100/100. To move further in your adoption journey, review the additional resources available here
You can also access product learning paths for various platform offerings available here
Warm Regards,
Netskope Customer Experience Team







