"Netskope NewEdge is the world’s largest, highest-performing security private cloud and powers the inline and API-driven security services of the Netskope Security Cloud. NewEdge provides customers with unparalleled service coverage, performance and resilience. Today NewEdge is powered by data centers in 70 regions with new data centers being added every month. By taking full control over routing, peering and data center location decisions, NewEdge achieves the lowest possible latency and round trip times for web, cloud & software-as-a-service (SaaS) access."
“Will the business-critical enterprise app traffic also be treated as regular internet traffic, leading to traffic delays and poor user experience?” is a concern that most security practitioners have when evaluating SASE. This technical brief will address this concern by analyzing the use of SASE, with the benefits of underlying internet peering to deliver the prominently used enterprise application in Cloud.
For example, Today Office 365 contributes more than 25% of enterprise traffic, and is growing at a high rate. Legacy office 365 applications were designed for on-premise data centers designed with specific network hops , Time to Live (TTLs) settings , and guaranteed Round Trip Time (RTT) or Latency. These apps are very chatty and traffic-intensive. To give you a context of the traffic volume, a typical user of Office 365 generates more than a dozen persistent connections. As these applications are delivered from Cloud , the traffic goes over the public internet that is made of interconnections of many Internet Service Providers introducing many network hops, congestion points, and no guarantee of RTT. Additional latency is introduced by enterprise security appliances used for Proxying and SSL inspection. This increase in network latency impacted adoption of Cloud Based Office 365. To address this issue Microsoft has been making two recommendations to enterprises:
a.) Clear connection without SSL inspection
b.) Reduce the number of hops. Options:
- Connect from enterprise egress IP - increases MPLS cost
- ExpressRoute to Office 365 edge - high deployment cost & complex to manage
- Direct connection from user/device - the best as per Microsoft recommendation
Now it is very important to note that while the example above is of the most prevalent enterprise app, Office 365, the need for a high performance and low latency network applies to all business apps used frequently by the users (e.g. payment applications and others)
PoPs or edges of Private Clouds:
The most common way to deliver apps to the global user community is through CDN (Content Delivery Network). CDN refers to a geographically distributed group of servers and caching infrastructure working together to provide fast delivery of cloud based applications. CDN providers host its edge infrastructure in Internet exchange point (IxP) co-location (COLO) facilities. These facilities are large data centers housing edges of multiple Internet Service Providers (ISP) and CDNs. SASE providers host their edges in these data centers to improve network performance. The commonly used term POP (Point-of-Presence) refers to the edges of ISP, CDN, and SASE.
Strive to minimize round-trip-time (RTT):
For faster network and application performance, it is essential to reduce RTT by avoiding the regular internet path, which may have many hops across multiple ISPs. BGP (Border gateway protocol) peering is used between the edges in the co-location facilities described above to provide a dedicated bandwidth. Such peering also reduces the distance as these edges are physically located in the same data centers connected by 10G or 100G shared fabric, achieving 1-2 ms of RTT between the edges.
A short note on BGP:
The Internet is a network of hundreds of thousands of smaller networks known as autonomous systems (AS). Each of these networks is a large pool of routers run by a single organization, such as various ISPs, technology vendors, and government agencies, etc. Every AS is identified with a unique AS Number (ASN) governed by the Internet Assigned Numbers Authority (IANA). BGP is the routing protocol that exchanges routing information between two AS. The routing information consists of known networks and number of hops to reach that network. Autonomous systems connect with other AS by peering with their edge routers so that hop count is one (1) to each other network.
The path of enterprise app traffic:
The path of any internet traffic starts from the user/device at any location. In SASE network architecture, the first leg is a direct connection from the user/device to the SASE edge gateway, the traffic entry point. Internet peering applies to the last path, which starts from the SASE edge at the exit. Without internet peering, the path will traverse regular internet, leading to multiple hops across various ISP before reaching the CDN edge of the enterprise cloud app provider. Suppose the SASE provider has a partnership with the app provider. In that case, it can accomplish internet peering with its CDN edge and reach the service in one or two hops.
The following diagrams show the comparison of two scenarios:
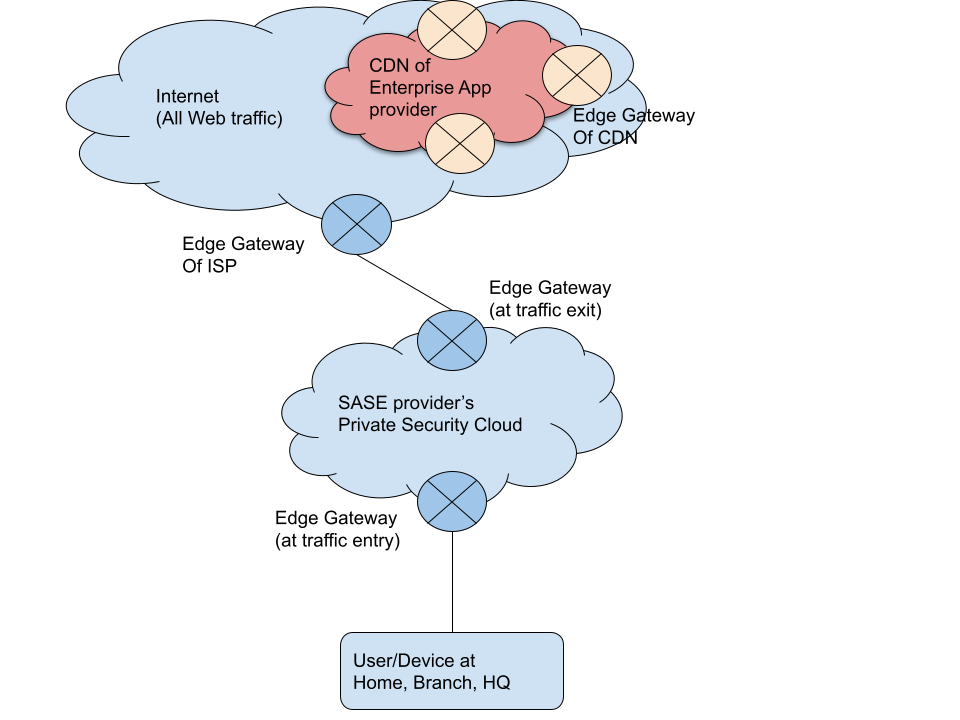
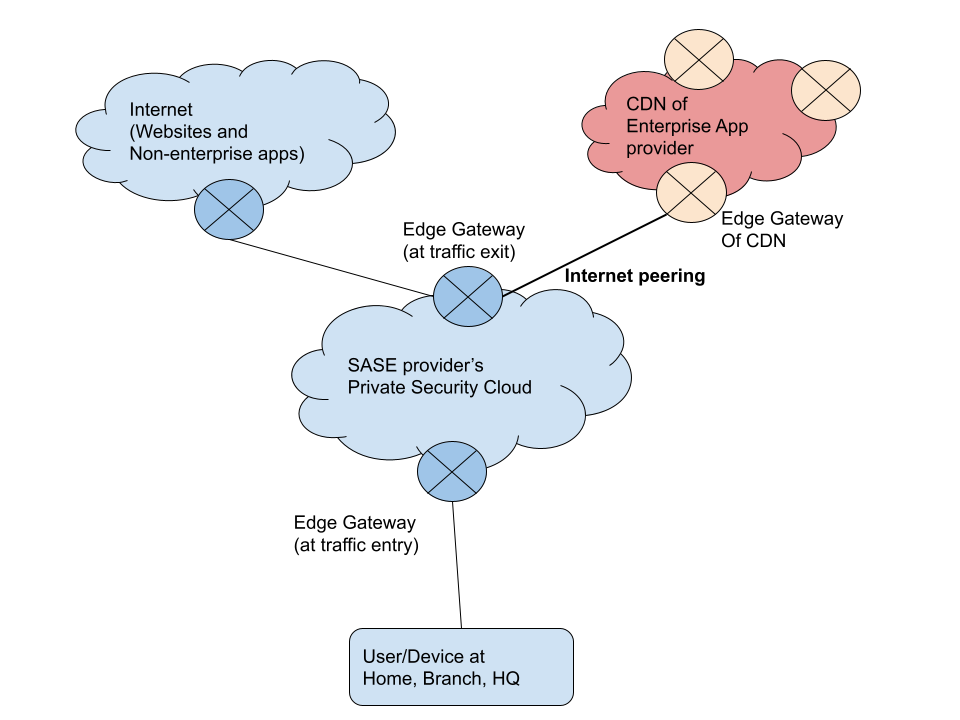
Internet peering:
Internet peering enables high performance for a specific enterprise cloud app. The provider of this app should enter into a partnership agreement with the SASE provider to allow peering between co-located edges of both parties. The internet peering partnership is for the mutual benefit of both parties, and it can be accomplished in two ways:
a.) Private peering is the direct peering relationship between these two private clouds, identified by two different autonomous system numbers (ASN) in the BGP world. Private peering is implemented in a private facility by two methods - private network interconnect (PNI) across layer-1 of 100G or private exchange across layer-2 of 10G or 100G.
b.) Public peering is the most common method of peering using layer-2. It is brokered at IxP where one private cloud peers with one or more private clouds through a single layer-1 connection to IxP’s shared fabric of 10G or 100G.
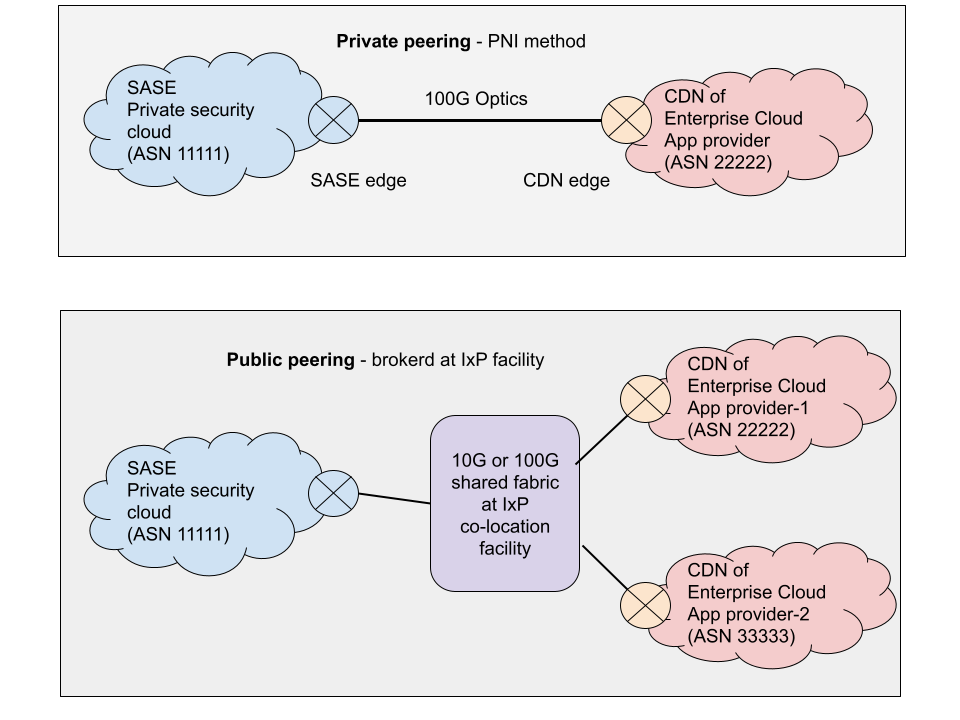
Therefore, when evaluating SASE vendors, security practitioners must exercise all due diligence. Identifying and differentiating the enterprise app traffic and providing it preferential treatment by all efforts to reduce RTT is an essential criterion for SASE provider selection. It is highly recommended to do research about the internet peering readiness of SASE providers with major enterprise app providers.
View numbers of Netskope peering exchange points at https://www.peeringdb.com/net/10670. Now, compare with the number of peering exchange points of other SASE vendors. You will be surprised to see that one of the top vendor completely lack private backbone, and its SASE platform fully rely on public internet.
NewEdge: Netskope’s Security Private Cloud
Behind the scenes, NewEdge is the infrastructure that powers the Netskope's security private cloud.
We conducted this special session for both security and networking professionals for an overview of the NewEdge architecture, key design principles critical updates and key insights.
Netskope Performance: Advanced Troubleshooting
Sometimes it becomes very difficult to troubleshoot end-to-end network performance for a complex & interdependent network architecture like SASE. We conducted this special session as part of our ongoing weekly technical workshops.
Review the community post to watch these workshops on Academy:
Recordings of workshops for Customers
Recordings of workshops for Partners
References:
https://www.netskope.com/platform/newedge
https://support.netskope.com/s/article/Netskope-Performance-Troubleshooting-Guide







