Note: I understand that traffic to Zoom is generally recommended to be bypassed.
If I want to prohibit the use of Zoom's camera and microphone features, what kind of policy should I write?
I was under the impression that writing a blocking policy in CFW would be sufficient to block usage, but the traffic does not seem to be getting blocked.
Here is the configuration I applied:
Under Settings > Security Cloud Platform > App Definition > Cloud & Firewall Apps, I added the following configuration.
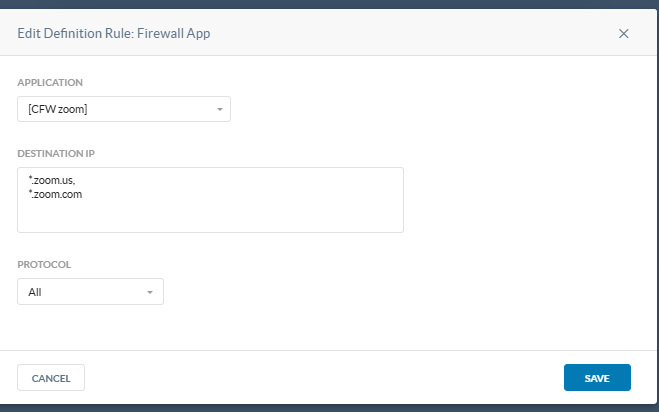
After that, I created a block policy under Real-time Protection.
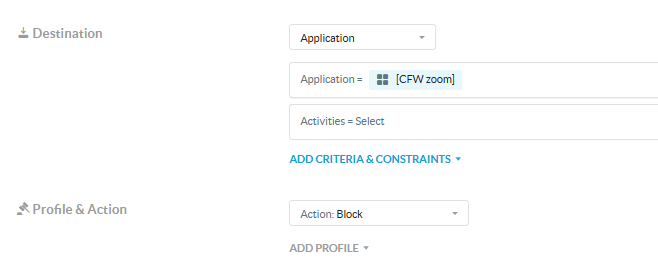
I expected that Zoom’s camera and microphone functionalities would be disabled as a result of the policy.
However, users are still able to use those features.
I would appreciate it if you could point out any mistakes or misconfigurations in my setup.








