Netskope has various built-in (aka predefined) DLP identifiers to detect passwords, public keys, private keys and base64 encoded data.
While you can write a regex to detect passwords in your environment, I have highlighted some of the challenges here:
- Regexes can cause DoS and False positives (at a customer site who has a dedicated team to write regex their complain was email in a string being detected as passwords).
- There is no single password standard that would work for all the environments.
- The key sizes are varied length.
Best approach for a credential detection policy
- Use Exact Match capability to identify username of AD account exfiltration
- Use Netskope's built-in identifiers rather than writing complex regex.
- Use Custom Entity validator to validate your test data with a corresponding Netskope predefined identifier.
Note: You do not have to create a custom entity. Just for the validation purpose call a predefined identifier under a custom entity.
Netskope can detect passwords for up to a certain number of finite characters. Feel free to test the length with your test data and see which one fits the best for your environment.
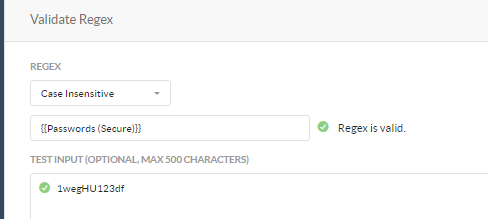
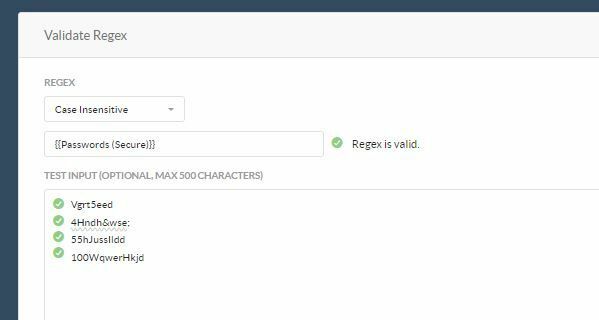
- Passwords: {{Passwords (Secure)}} works for most combination of alphanumeric and special characters combinations.
- Public and private keys: Netskope has following predefined identifiers for the public and private keys that works for private and public key standards such as RSA, OpenSSH, ECDSA PGP.
Note: Netskope cannot identify the encrypted text as we are privy to the actual keys but using these key related identifiers you can detect that keys are being exfiltrated.
Steps to validate predefined identifiers with test data:
- Login to Netskope tenant and go to
Policies > Profiles > DLP > Entities > New Entity
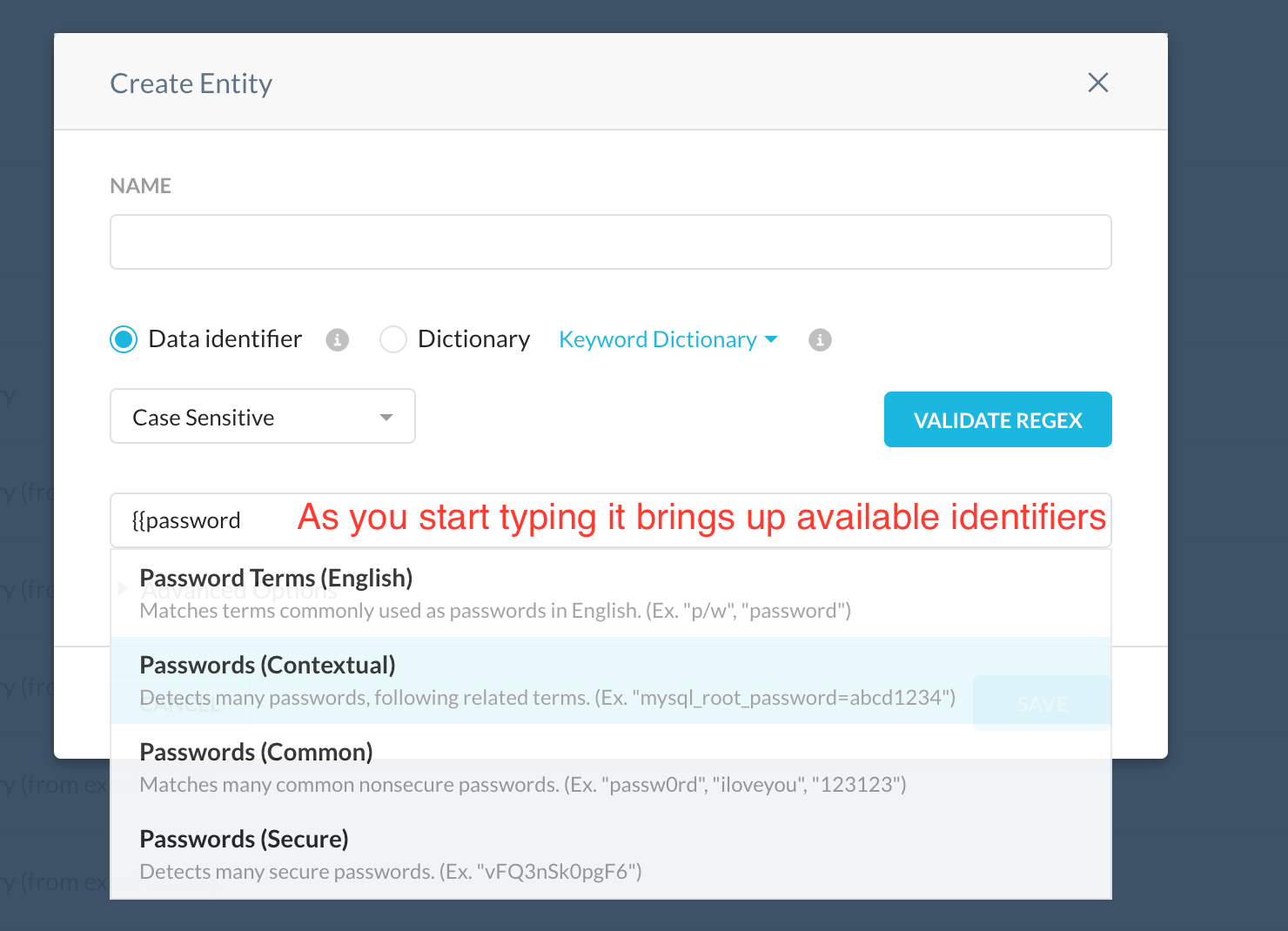
(Based on the listed entities page 230 onwards in the doc referenced above. As you type after entering two open curly brackets “{{“the wizard auto completes with one of the supported entities. E.g. type generic for all the generic keys supported.)
- Search for the predefined identifiers.
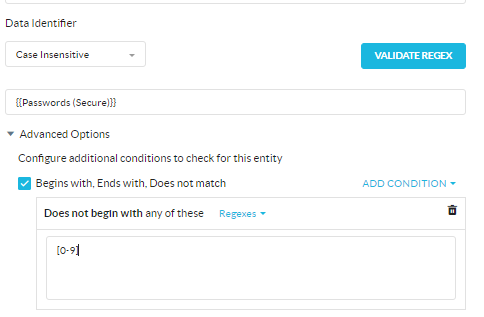
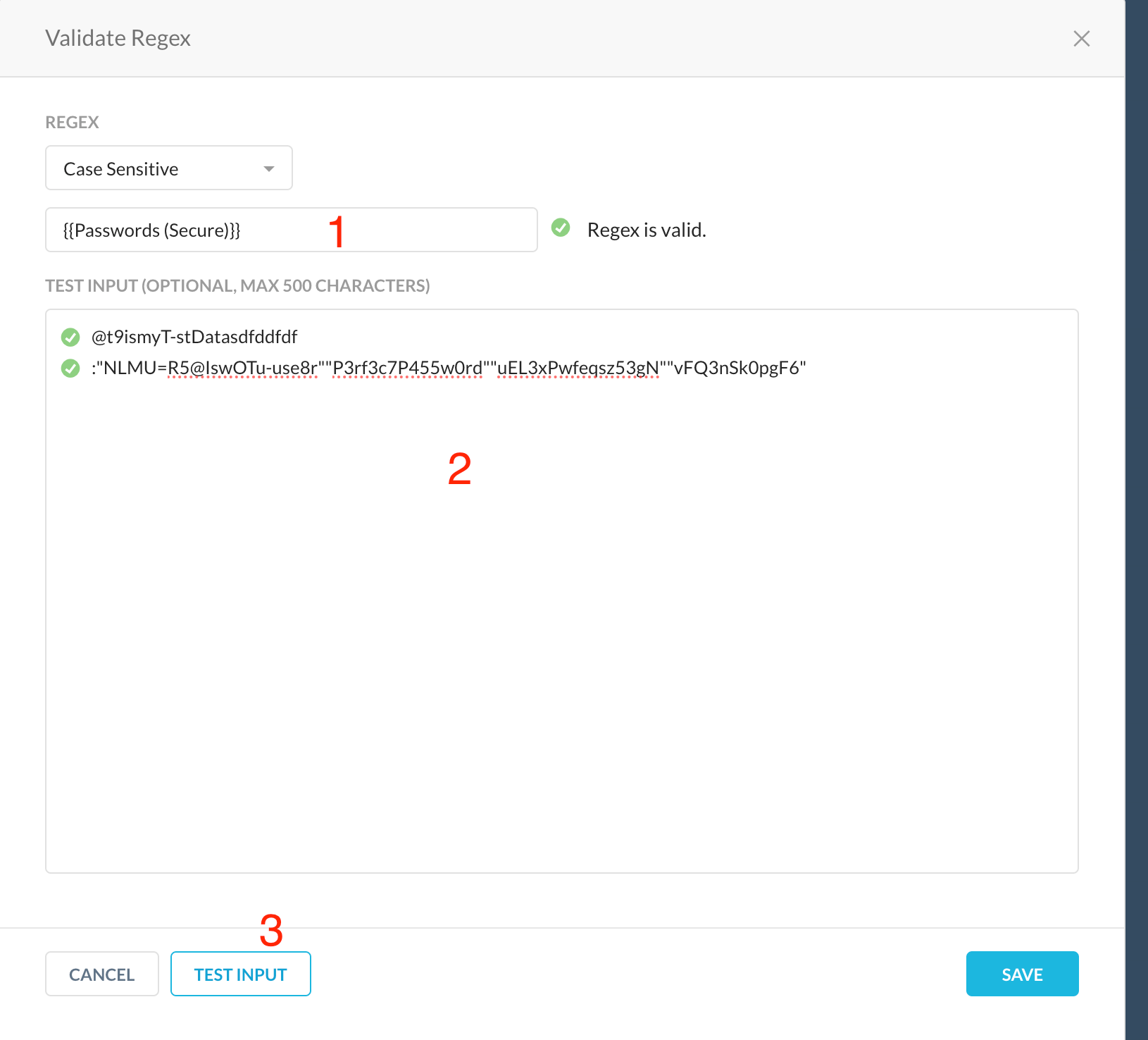
- Click Validate regex and enter sample keys as shown below (each key on separate line)
Netskope publishes Netskope predefined identifier document which is behind support article. It describes all the identifiers with example key sets. For version R106 page 230 onwards you will find credentials related identifiers.
https://support.netskope.com/s/article/DLP-Predefined-Identifiers
Password Terms (English) Matches terms commonly used as passwords in English.
Examples: "p/w", "password", and "pw".
Passwords (Contextual) Detects many passwords, following related terms.
Examples:"mysql_root_password=abcd1234""password : lightsaber""password: Passw0rd!"
Passwords (Common) Matches many common nonsecure passwords.
Examples:"1123581321""123123""1234harryp0tter""abc999""iloveyou""letmein""passw0rd""password1""sp0ng3b0b""superman""wizard1""zxcvbnm"
Passwords (Secure)Detects many secure passwords.
Examples:"NLMU=R5@IswOTu-use8r""P3rf3c7P455w0rd""uEL3xPwfeqsz53gN""vFQ3nSk0pgF6"
Private Keys (Generic, Begin) Matches the start tag of many private key blocks.
Examples:"-----BEGIN PRIVATE KEY-----"
Private Keys (Generic, End)Matches the end tag of many private key blocks.
Examples:"-----END PRIVATE KEY-----"
Public Keys (Generic, Begin) Matches the start tag of many public key blocks
Examples:"-----BEGIN PUBLIC KEY-----"
Public Keys (Generic, End) Matches the end tag of many public key blocks.
Examples:"-----END PUBLIC KEY-----"
Secret Keys (AWS) Detects contextual AWS secret keys.
Examples:"aws_secret_key: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY"
Base64-Encoded Data computing/encodings/base64
Example:"TtC1dNGVa9C+0YDQteKAhT3igIXQomhl4oCF0IXQtdGBdXLRlnTRg+KAhUzQtdCwZNC1cseD"
Thanks @RL for proof reading.