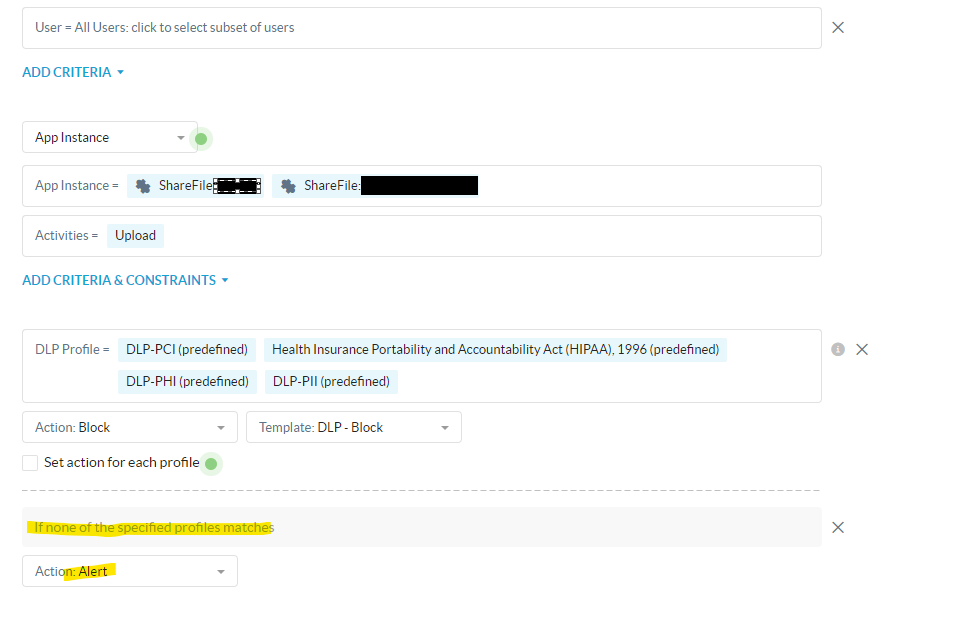
Hello,
I have a policy setup to block uploads to a specific instance of an application when any DLP profile matches otherwise alert via the traffic direction functionality in the RTP. This has been working fine for a while. Today, I went to add additional instances and when I had the user test, it was still being blocked, completely bypassing that rule and going to my default deny, its not matching DLP because if it was, it would be blocked by the policy I am talking about, its sliding right by my rule... I tried a separate RTP at the top with just the instance configured the same way with no luck. The only way I could get it to work was to remove the DLP profiles.
The specific instance I was testing with was a third instance that was sharepoint.
Has anyone seen this?
Nate