
Netskope Global Technical Success (GTS)
GitHub - Block Google SSO for login
Netskope Cloud Version - 130
Objective
GitHub - Block Google SSO for login
Prerequisite
Netskope SWG and Next-Gen SWG license
Context
GitHub provides Single Sign-On (SSO) integration with Google accounts. This knowledge base article focuses on preventing end-users from utilizing Google SSO to access GitHub.
Do You Know?
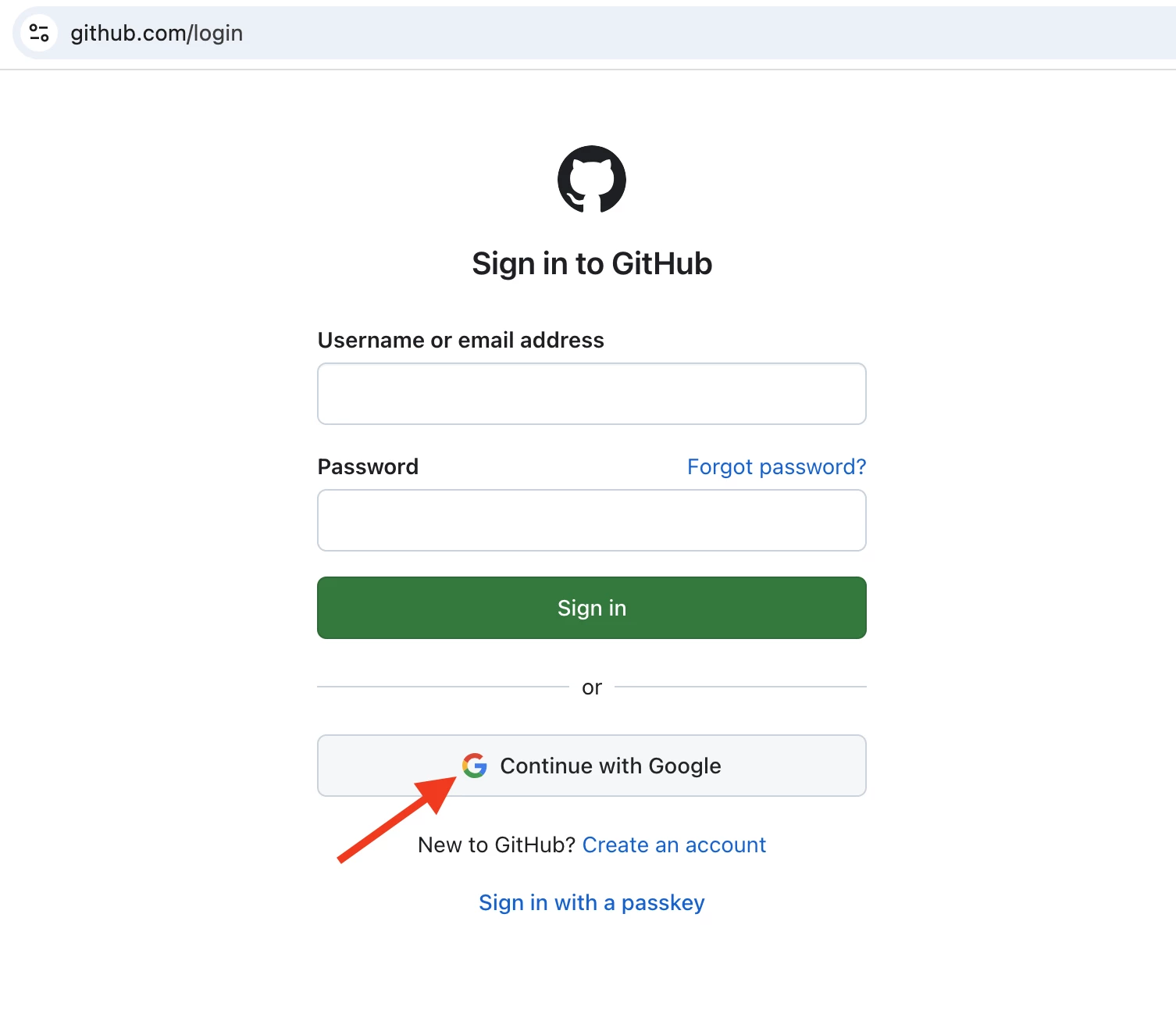
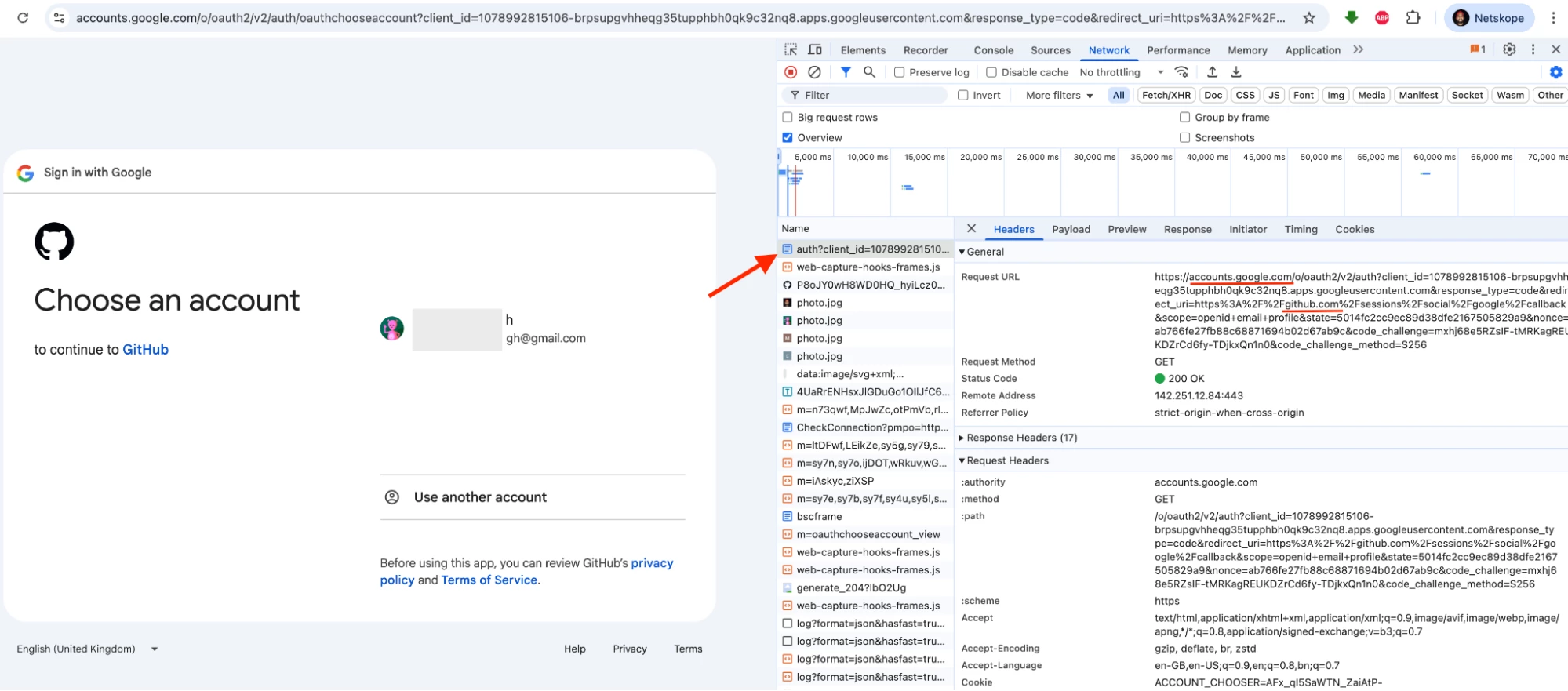
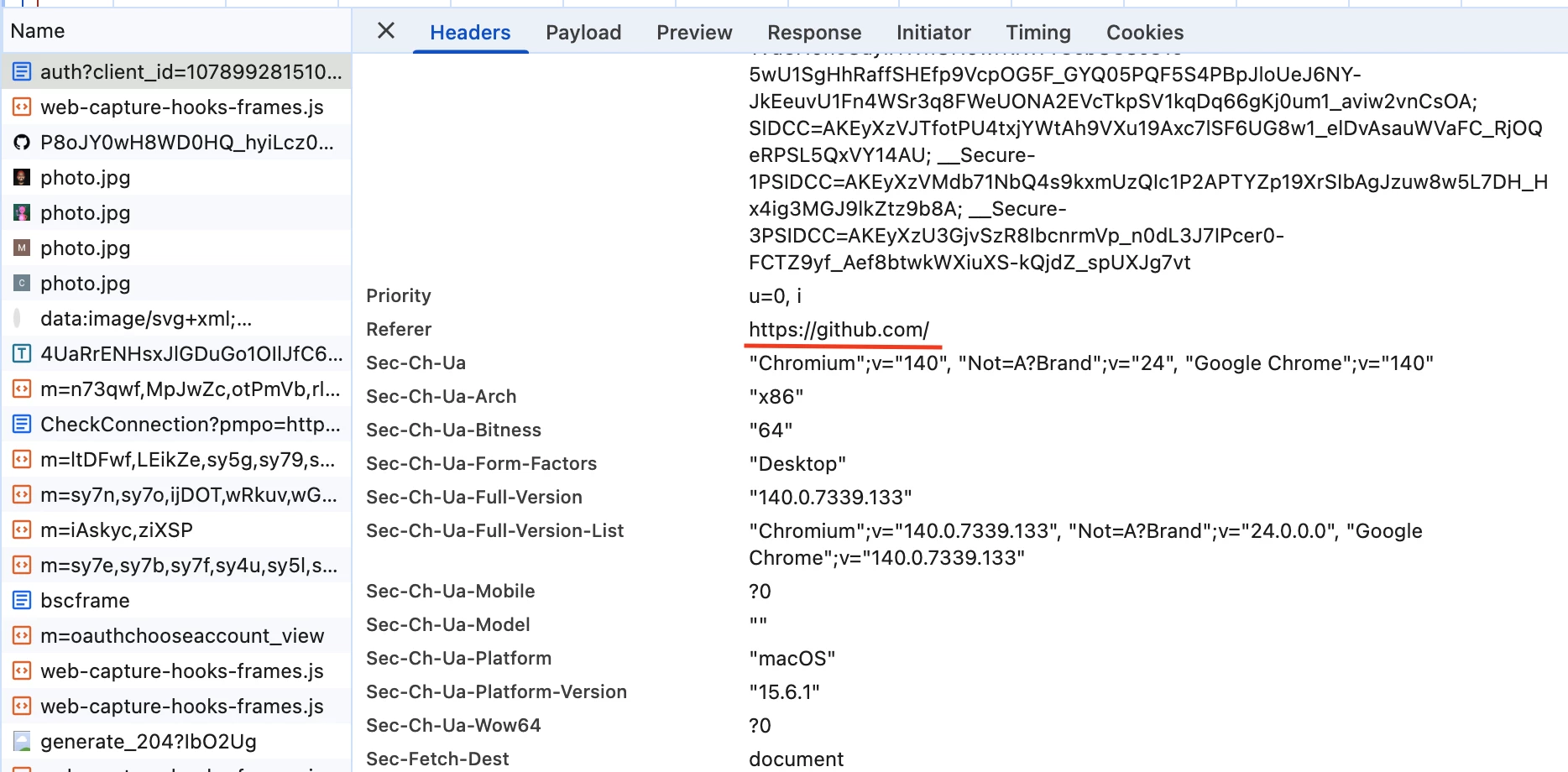
- When an end-user attempts to log in to GitHub using Google SSO, the traffic redirects to accounts.google.com
- Netskope recognizes this domain under a predefined cloud app called Google Accounts.
Configuration
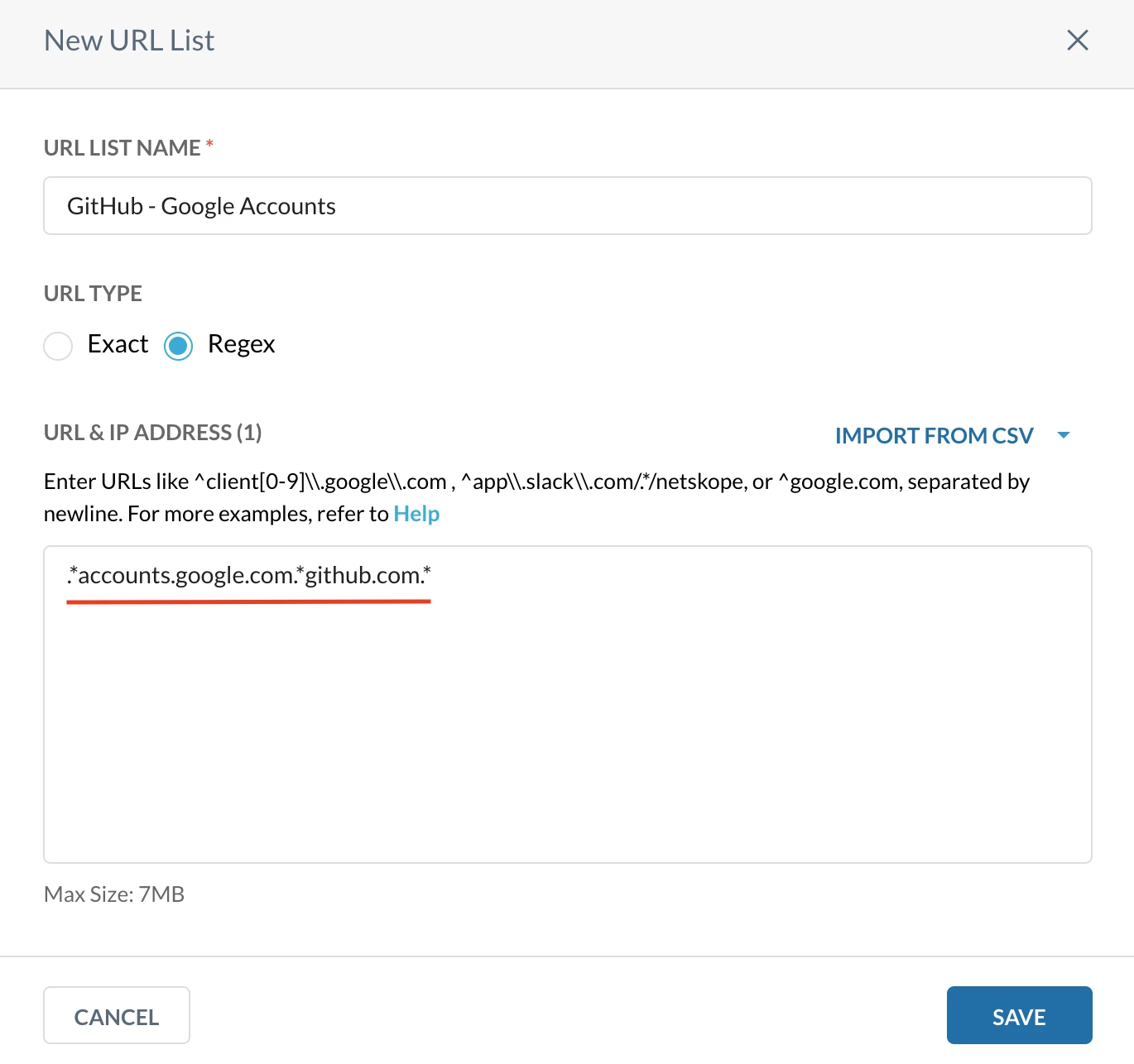
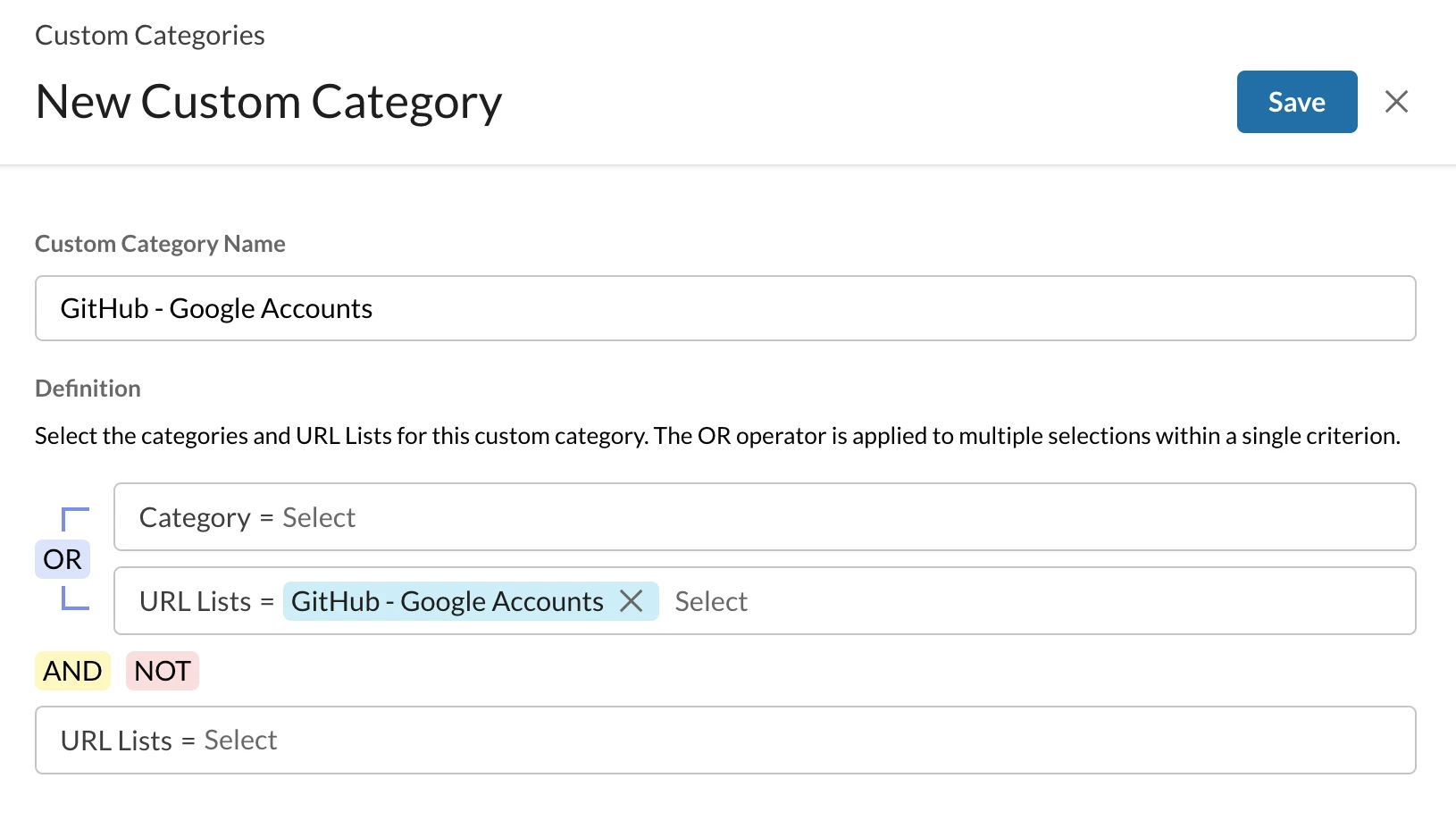
Step 1 - Create a custom URL category
Path: Netskope Tenant UI >>> Policies >>> Profile - - - URL Lists

Path: Netskope Tenant UI >>> Policies >>> Profile - - - Custom Categories

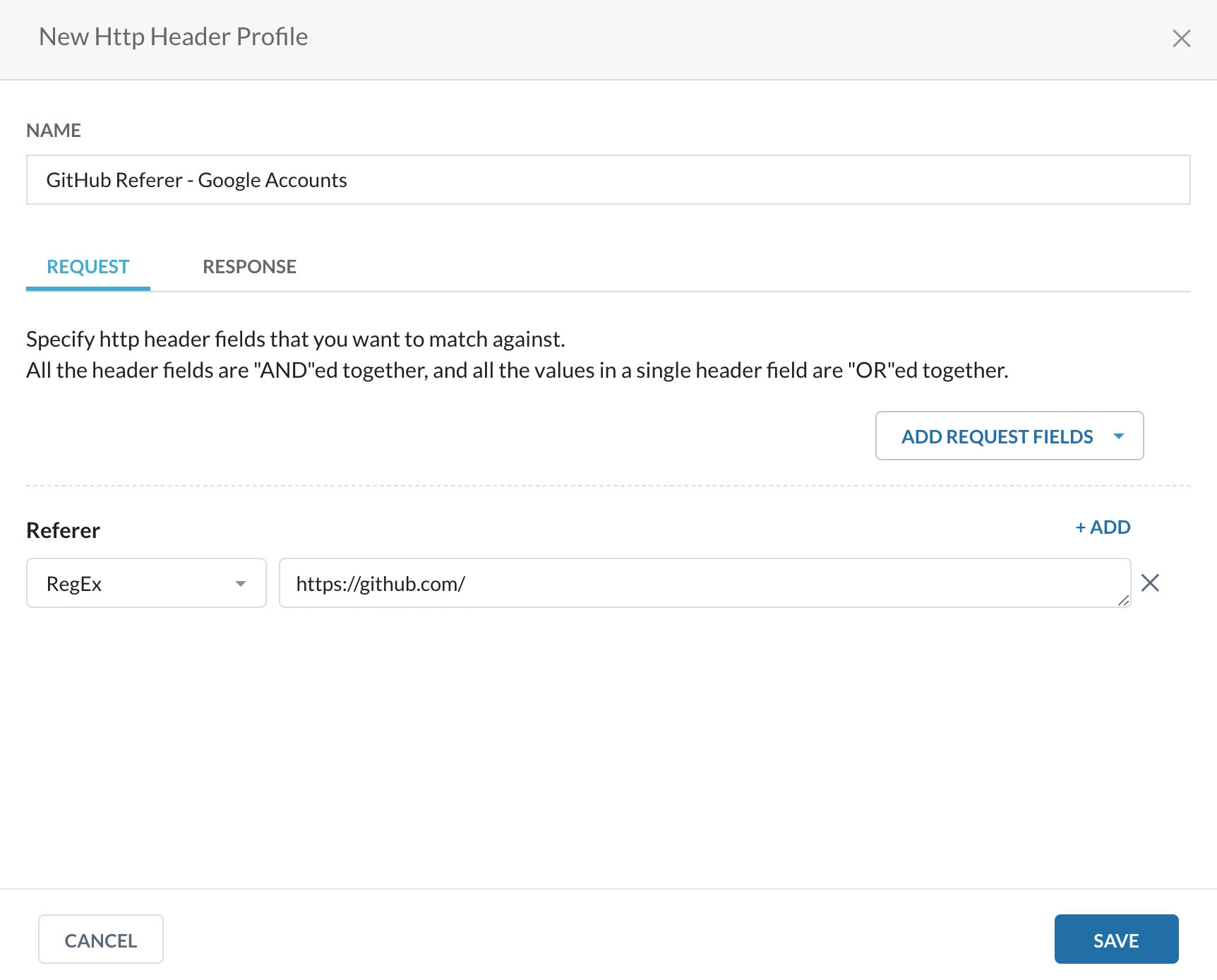
Step 2 - Create a HTTP Header profile
Path: Netskope Tenant UI >>> Policies >>> Profile - - - HTTP Header

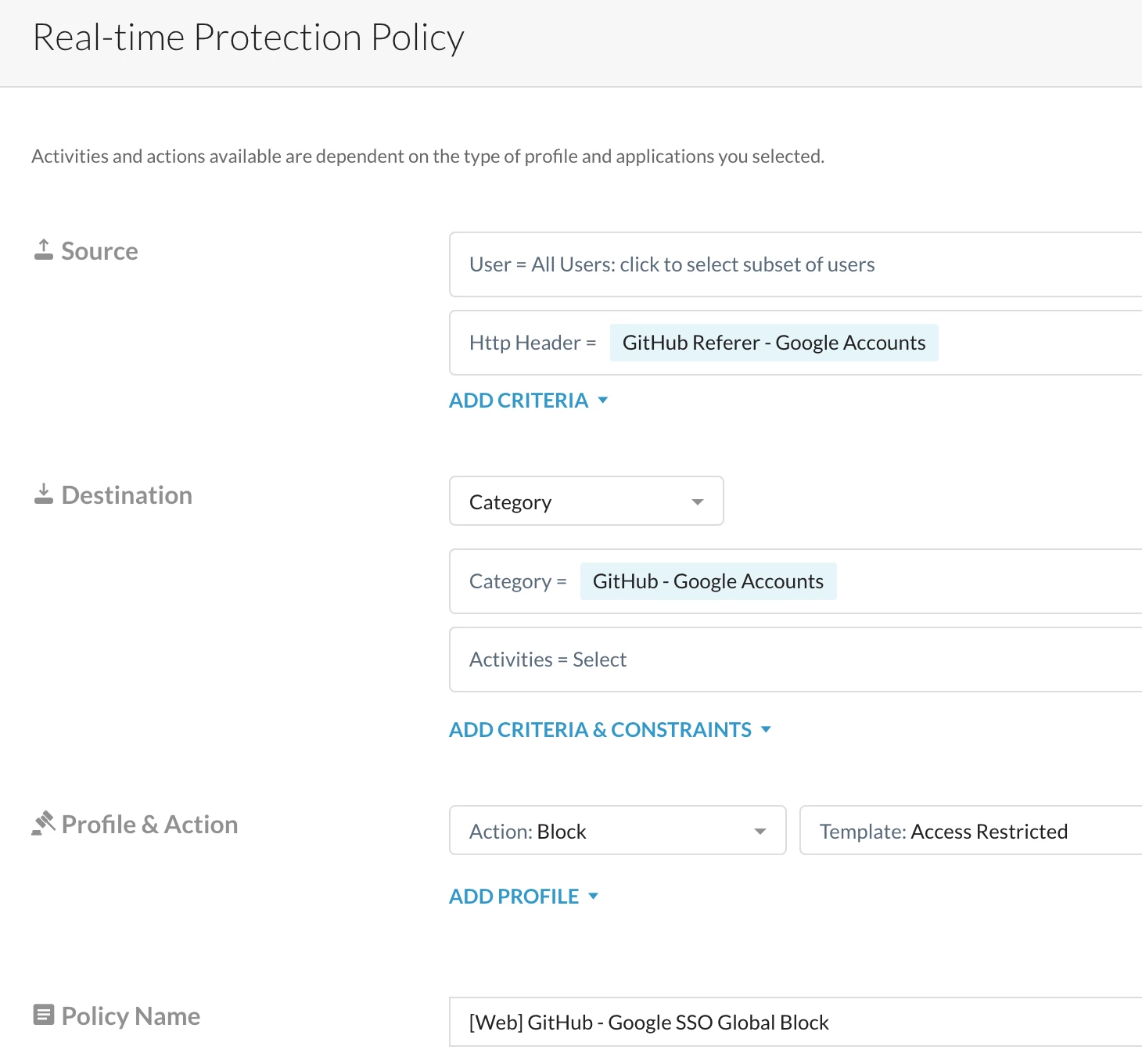
Step 3 - Create a Real-time protection policy
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy

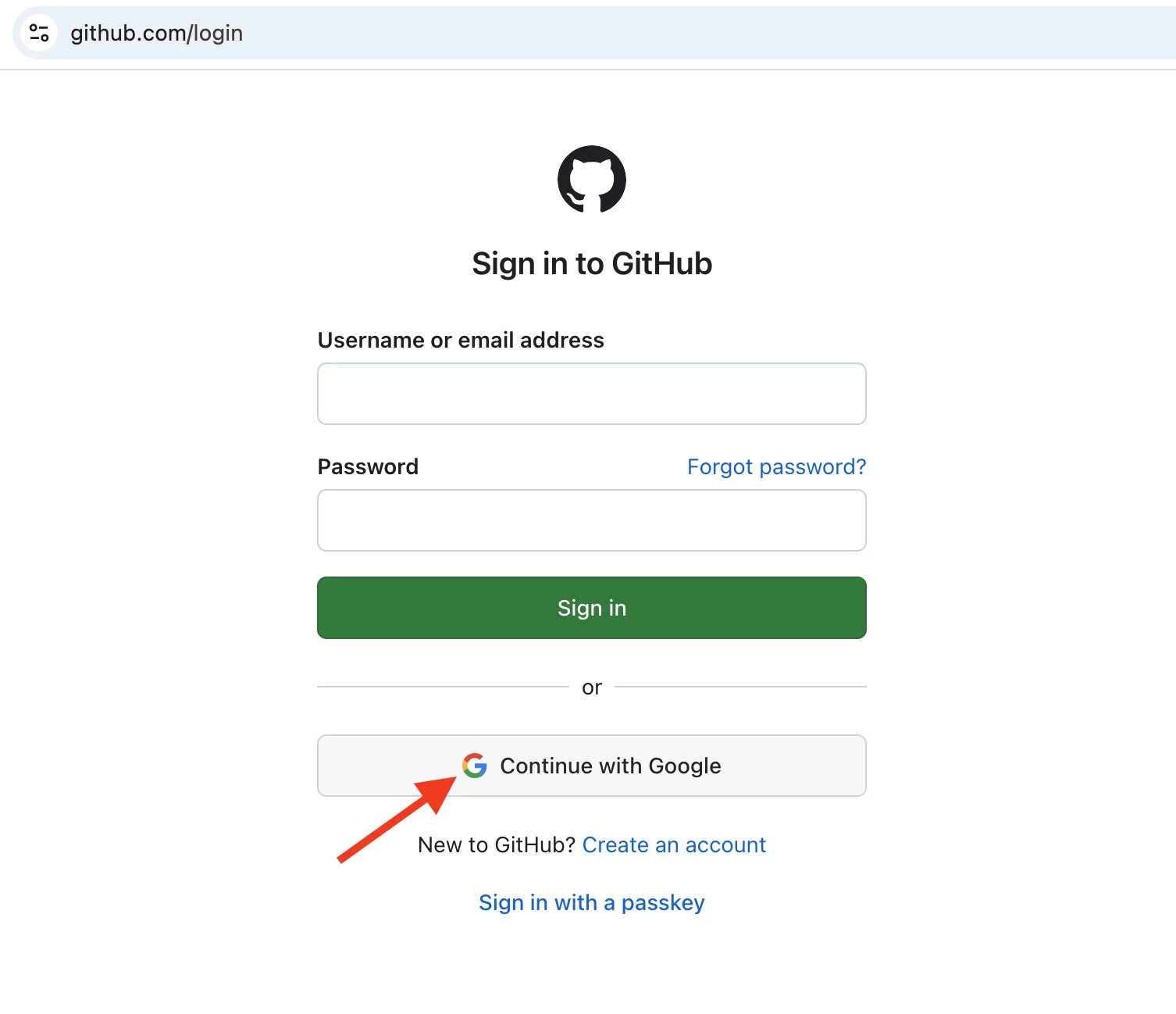
Verification
Access GitHub and attempt to log in using Google’s Single Sign-On (SSO)

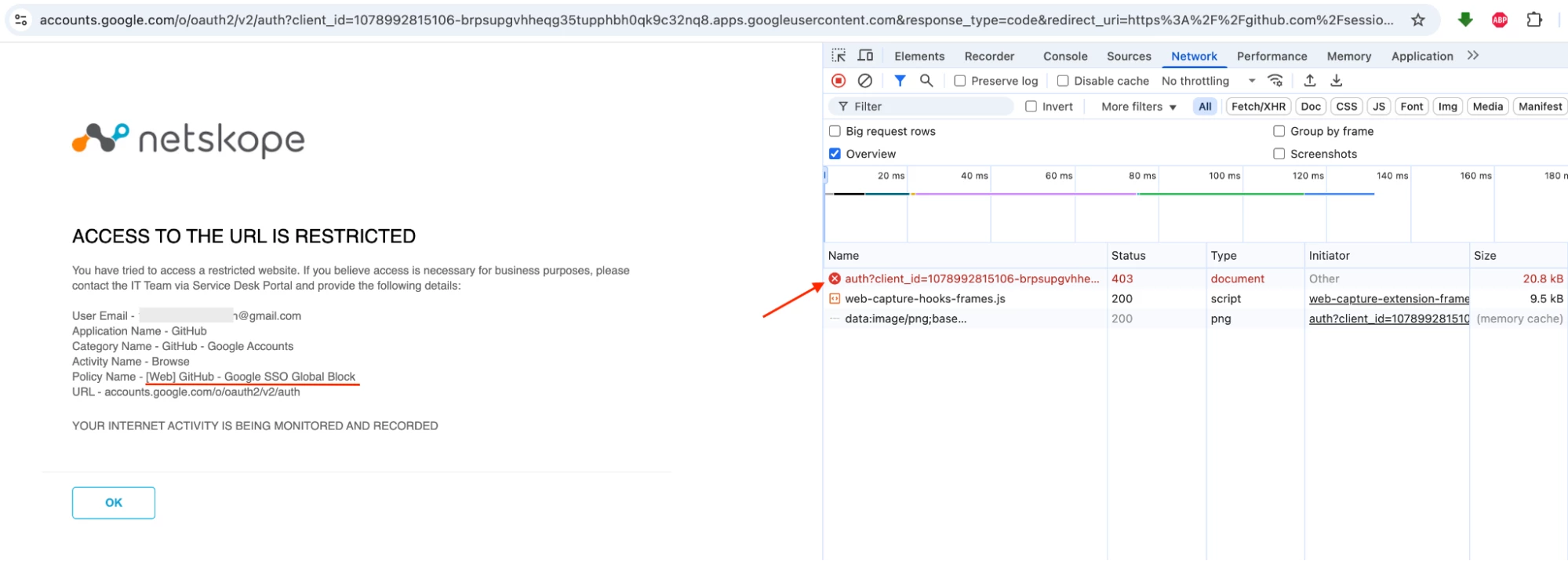
 Note - User Notification format used above Link
Note - User Notification format used above Link
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.







