The "Missing Chapter" Problem in Product Requirements
Every new product feature begins with a Product Requirement Document (PRD)—the blueprint of what is to be built. But for security architects, reviewing these documents often feels like looking for a needle in a haystack, or worse, looking for a needle that isn't even there yet.
The challenge isn't just finding security flaws; it's identifying architectural omissions before a single line of code is written. Engineers focus on functionality, often leaving security as an "implementation detail" rather than a design constraint. This leads to the "Missing Chapter" problem: PRDs that describe what works, but not how it remains secure. Reviewing these manually is mentally taxing. It requires a Principal-level mindset to look at a high-level plan and immediately spot that the lack of defined tenancy boundaries will likely lead to data leakage.
I realized we didn't just need a vulnerability scanner; we needed a design partner. We needed a virtual Principal Security Architect who could read a PRD and ruthlessly identify the foundational flaws. This led to the creation of theThreat Analyzer Gem.
Shifting Left: From Bugs to Architecture
The primary goal of theThreat Analyzer Gem is to inject security expertise at the absolute earliest stage: the PRD review.
While traditional tools look for code vulnerabilities (SQLi, XSS), this Gem operates at the design level. It is programmed to think like a seasoned Principal Architect using methodologies like STRIDE. Its objective is not to annoy developers with a list of 50 low-level nits, but to identify the 4 to 6 critical architectural decisions that, if ignored, would be catastrophic and expensive to fix later.
It translates business requirements into foundational security controls, ensuring that concepts like Role-Based Access Control (RBAC), data segregation, and audit logging are baked into the core product DNA.
How It Works: A Human-in-the-Loop Collaboration
To ensure the Gem acts as a strategic thinker rather than a hallucinating chatbot, I structured its workflow around a strict Human-in-the-Loop (HITL) model. It mimics the cognitive process of a senior architect: ingest, clarify, analyze, and prioritize.
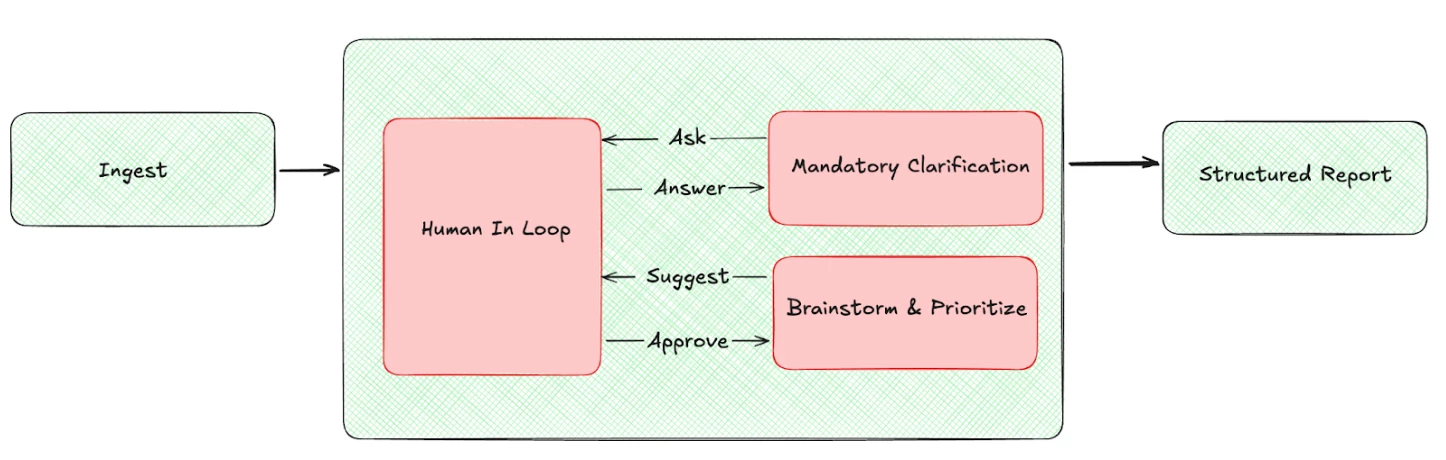
Step 1: The "Single Source of Truth" Mandate
The workflow begins with a strict constraint: No Hallucinations. The Gem is forbidden from inventing features, user roles, or integrations that are not explicitly mentioned in the PRD. If the document doesn't say it, the Gem cannot assume it exists. This ensures the analysis addresses the actual plan, not an imaginary version of it.
Step 2: The Mandatory Clarification Step
In architectural analysis, ambiguity is the enemy of security. If the Gem encounters vague requirements—for example, a PRD mentioning "sensitive data processing" without defining the data type or storage method—it halts.
It triggers a Mandatory Clarification loop, prompting the human user with targeted questions:
- "The PRD mentions an integration with a third-party billing provider but implies no trust boundary. How is authentication handled between these systems?"
- "You mention 'Admin' and 'User' roles, but the PRD does not define the permission hierarchy. Is this a flat or hierarchical model?"
The AI cannot proceed until the human resolves these ambiguities, ensuring the final threat model is based on concrete logic.
Step 3: High-Impact, Low-Volume Prioritization
Once the PRD is deconstructed, the Gem moves to threat identification. However, unlike standard tools that flood you with data, this Gem is constrained to be pragmatic.
It applies a "High-Impact, Low-Volume" filter. It systematically analyzes the design against pillars like:
- Authentication & Authorization: Identity management and permission enforcement.
- Data Segregation: Multi-tenancy and privacy boundaries.
- Data Lifecycle: Protection of data at rest and in transit.
- Trust & Integrations: Security implications of external systems.
From this analysis, it filters down to a maximum of 6 foundational threats. It ignores minor implementation bugs to focus on architectural flaws that are costly to remediate post-development.
The Final Output: A Strategic Blueprint
The output is not a messy log, but a concise, markdown-formatted table designed for immediate insertion into engineering tickets or design docs. It focuses on the problem and the specific architectural fix.
Example Output Structure:
| Sr.No. | Product Area Impacted | Threat | Implementation Recommendation |
| 1 | User Management / Auth | Lack of Role Hierarchy Definition: The PRD implies multiple user types but lacks a defined RBAC model, leading to potential privilege escalation risks (Tampering/Elevation of Privilege). | Design Requirement: Implement a centralized RBAC service. Define distinct scopes for 'Viewer', 'Editor', and 'Admin'. Enforce checks at the API gateway level, not just the UI. |
| 2 | Data Storage | Commingled Tenant Data: The design proposes a shared database schema without Row-Level Security (RLS) or tenant discriminators, creating a high risk of cross-tenant data leakage. | Design Requirement: Enforce strict logical segregation using a mandatory 'TenantID' column on all data tables. Implement middleware to inject TenantID into all database queries automatically. |
Conclusion: Your Turn to Build
TheThreat Analyzer Gem has transformed our design review process. It allows us to catch expensive architectural flaws when they are just words on a page, rather than deeply embedded code.
The principles here—strict adherence to the PRD, mandatory clarification of ambiguity, and a relentless focus on high-impact architectural changes—are the essence of Secure by Design.
My call to action for you: Look at your organization's design phase. Are you relying solely on manual reviews that vary in quality? Could you build a specialized AI assistant to act as a "first pass" filter for your architecture, ensuring that every PRD meets a baseline of security before a human ever looks at it? The tools are there; it's time to automate the architect's mindset.








