Are you facing excessive Netskope DLP alerts which are false positives?
The Netskope DLP solution provides a wide range of capabilities for detecting data theft and data mishandling. While setting up these policies, one of the common difficulties a security team faces is applying proper allowlisting mechanisms to reduce the amount of false positives. Luckily, the Netskope DLP solution has native effective ways that help allowlist certain applications, instances, users, and activities. Here are a some of those approaches to consider:
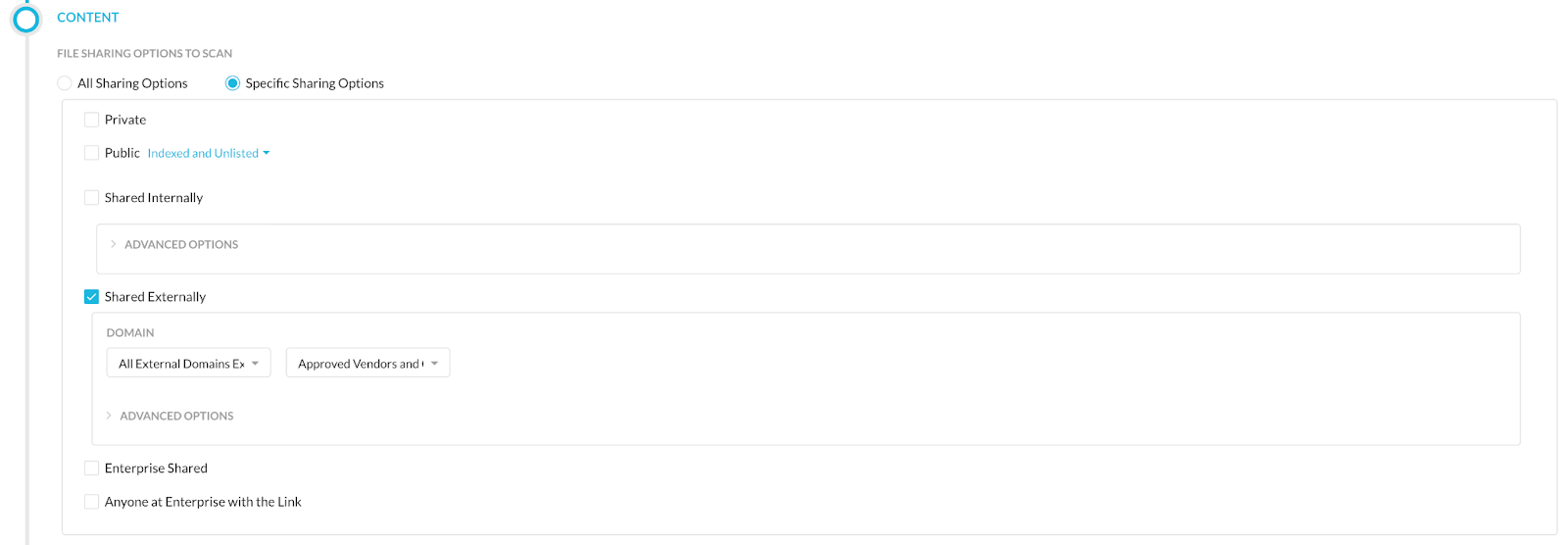
Exclude certain external domains from within API data protection policy:
This option helps analysts to exclude permitted vendors and partners from a particular API protection DLP policy. For example, an organization may be allowed to share sensitive financial information with its financial consulting firm. So the PCI DLP policy could exclude that particular domain/site for the “External Share” policy. The list of applications supporting this feature is mentioned below. This list may not be a comprehensive, as more supported applications may be added in the future:
- Google Drive
- Gmail
- Microsoft Office 365 Outlook
- Microsoft Teams
- Microsoft Office 365 OneDrive for Business
- Microsoft Office 365 Sharepoint Sites
- Box
- Dropbox
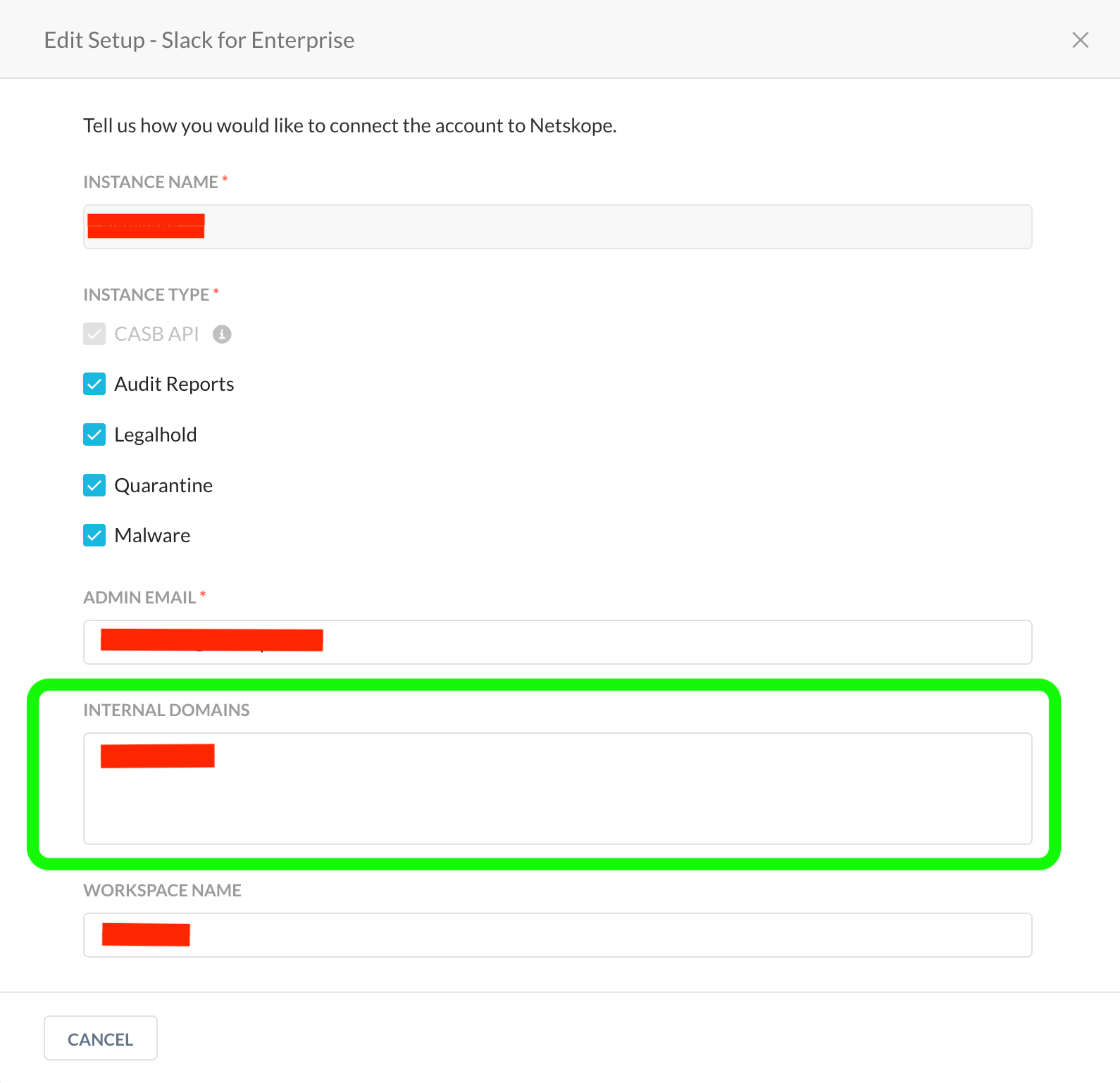
Allowlist internal domains for SaaS applications:
This feature allows analysts to add certain approved partner/vendor domains as internal domains, so all the added domains would be considered “Internal,” as per that particular SaaS application instance. File sharing policies which look for “External” users will consider these domains as “Internal” domains, preventing a lot of false positives. The list of applications supporting this feature is mentioned below. This list may not be the comprehensive, as more supported applications may be added in the future:
- Slack
- Slack Enterprise
- Microsoft Office 365 OneDrive for Business
- Microsoft Office 365 Outlook
- Sharepoint
- Microsoft Teams
- Workplace by Facebook
The sample snippet below indicates the feature for the SaaS application “Slack for Enterprise.”
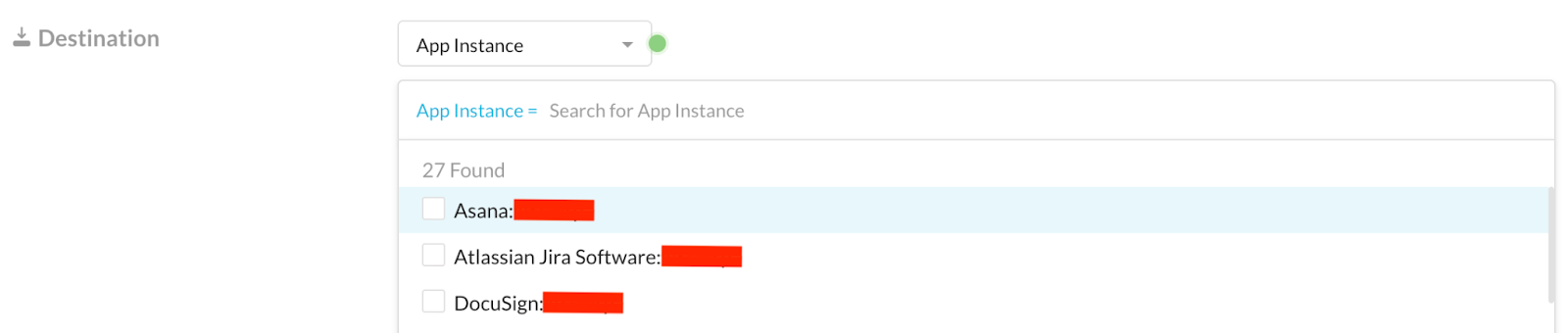
Allowlist with app instance:
While creating real-time policies, the application instances of certain applications could be saved to be excluded from certain DLP policies or to be allowlisted for some specific activities. For example, an organization “X” may allow uploading source code to only their private Jira instance, but would want to be alerted about source code uploads to all other Jira instances. In this situation, only the Jira instance of organization “X” could be allowlisted by creating a new specific “Allow” policy before the “Block all Jira source code uploads” policy. Possible applications supporting the app instance option are mentioned below. This list is not comprehensive as more supported applications may be added in the future:
- Google Drive
- Atlassian Jira
- Atlassian Confluence
- Docusign
- Github
- Slack
Exclude certain users’ domains from within APT/real-time protection policy:
This option helps analysts to exclude certain users who are allowed to perform a particular sensitive activity. For example, the CFO of an organization may be allowed to share sensitive financial information with consulting firms. So, the PCI DLP policy could exclude that particular user and apply restrictions to the rest of the organization or only be applied to specific users/departments, as per the requirement.
Allowlist with Netskope Cloud Ticket Orchestrator:
Netskope Cloud Exchange (CE) provides customers with powerful integration tools to leverage investments across their security posture. CE consumes valuable Netskope telemetry, external threat intelligence, and risk scores, enabling improved policy implementation, automated service ticket creation, and exportation of log events from the Netskope Security Cloud. Netskope Cloud Ticket Orchestrator (CTO) helps streamline investigations and response by helping automate service tickets, providing curated event details for filtering, managing deduplications, and mapping tickets to workflows.
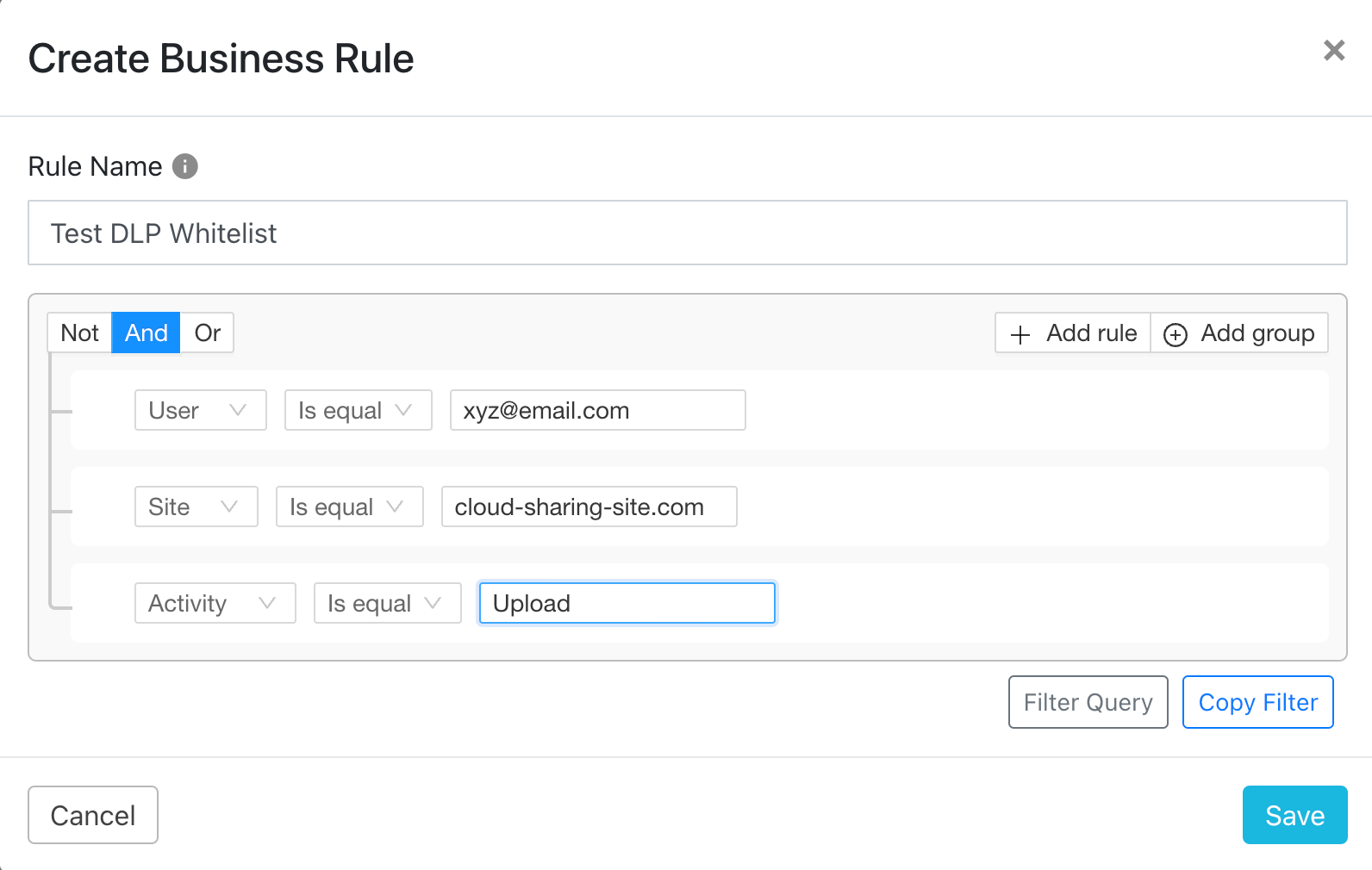
If there is a particular situation which cannot be allowlisted by any of the above methods, the best resort could be the Netskope Cloud Ticket Orchestrator which is part of Netskope Cloud Exchange. Granular business rules could be written in order to allowlist certain complicated exceptions. For example, one particular user “xyz@email.com” could be allowed to upload files to a cloud storage site by not creating a ticket for that particular user, while a ticket is created for any other users who upload files to the same cloud storage site. The only drawback of this method is that an alert is created in the Netskope Tenant by default, but the filtering could be used to create tickets for alerts excluding the allowlisted user.
Are you effectively whitelist using Netskope DLP to reduce false positives?







