How to Finally Solve the BYOD, Contractor, and M&A Access Dilemma
Author: Stevan Pierce
Date: November 9, 2025
The perimeter is long gone, and the "unmanaged device" is the new CISO headache. How do you grant access to contractors, BYOD users, and new M&A employees without opening a Pandora's Box of data-leakage risk?
The Netskope One Enterprise Browser is an approach that isolates the application, not the device. It’s a hardened, corporate-managed browser that integrates directly into the Netskope One platform, acting as a new enforcement point for your Security Service Edge (SSE).
It is a self-contained corporate workspace that:
- Separates Work & Personal: Creates a distinct corporate profile on any device, managed or unmanaged, separating all corporate browsing activity and data.
- Provides Granular DLP: Enforces in-browser controls like copy, paste, print, and screenshots—stopping data leaks at the source.
- Delivers Agentless ZTNA: Bakes Netskope Private Access (NPA) capabilities directly into the browser, providing secure access to private apps without a full VPN client.
- Is Fast & Simple: Deploys via a self-service install, reduces IT overhead, and extends your existing Netskope security policies, making it ideal for BYOD and M&A.
This article explores the technical "how" and the strategic "why" of using the Netskope One Enterprise Browser to secure your applications and data.
The Modern Access Conundrum
For decades, security was simple: we built a wall around our castle. If you were "inside" (on the corporate network), you were trusted. If you were "outside," you were not.

Today, that model is shattered. Our data is everywhere—in SaaS apps like Salesforce and Google Workspace, and in private apps hosted in the public cloud. Our "users" are also everywhere—they are remote employees, third-party contractors, and partners.
This creates three critical challenges that security architects and CSOs face daily:
- The BYOD & Contractor Problem: You need to grant a contractor secure access to a single corporate application. They are using their personal laptop. Do you...
- ...ship them a $2,000 corporate laptop for a 3-month project? (Too slow, too expensive).
- ...let them install a full VPN client? (Absolutely not. You have no idea what's on that device, and you just gave it a network-level key to your kingdom).
- ...spin up a VDI/DaaS instance? (Costly, complex, and users hate the latency).
- The M&A Tsunami: Your company just acquired a 500-person firm. You need to give them access to your corporate SaaS apps today so they can be productive. You can't merge two complex corporate networks in 24 hours. How do you grant fast, secure, and isolated access?
- The "Trusted" Insider Risk: Even on a fully managed corporate device, what stops a well-meaning employee from copying sensitive customer data from Salesforce and pasting it into their personal webmail? The Netskope One Enterprise Browser can be deployed to managed devices to elevate security for users accessing critical data.
Traditional solutions are too heavy, too high-risk, or too slow. We need a new tool. We need to secure the browser, the new cockpit for all corporate work.
What is the Netskope One Enterprise Browser?
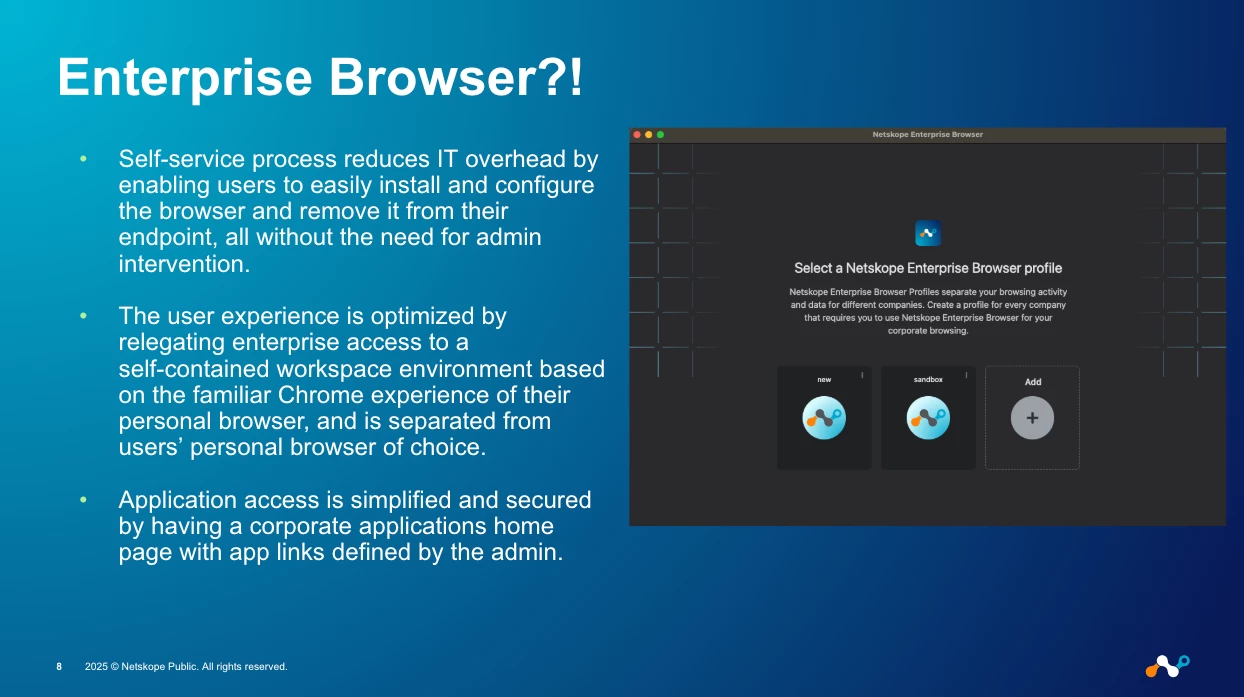
The Netskope One Enterprise Browser is a purpose-built, hardened browser based on the familiar Chrome experience. It's designed to be the only application a user on an unmanaged device needs to securely access corporate resources. It acts as a self-contained, corporate-managed workspace, completely separate from the user's personal browser.
It is natively integrated with the Netskope One platform, extending your SSE controls via Netskope's NewEdge network.
- Policy-Driven: It natively enforces your corporate SSE controls, from threat protection and URL filtering to advanced DLP.
- Self-Contained: It isolates corporate activity and data from the user's personal profiles and browsers.
- User-Friendly: It provides a simple, self-service install and removal process, dramatically reducing IT overhead.
- Centralized: It presents the user with an admin-defined "Company Workspace" homepage, simplifying access to both public and private apps.
Think of it as the perfect middle-ground: the deep security of VDI without the cost and latency, and the flexibility of a clientless solution without the gaping security holes.
The Technical Pillars of Netskope One Enterprise Browser Security
For security analysts and architects, here is how it works. The Enterprise Browser enforces security as part of your unified Netskope policy engine.
Pillar 1: Granular, In-Browser Data Protection (DLP)
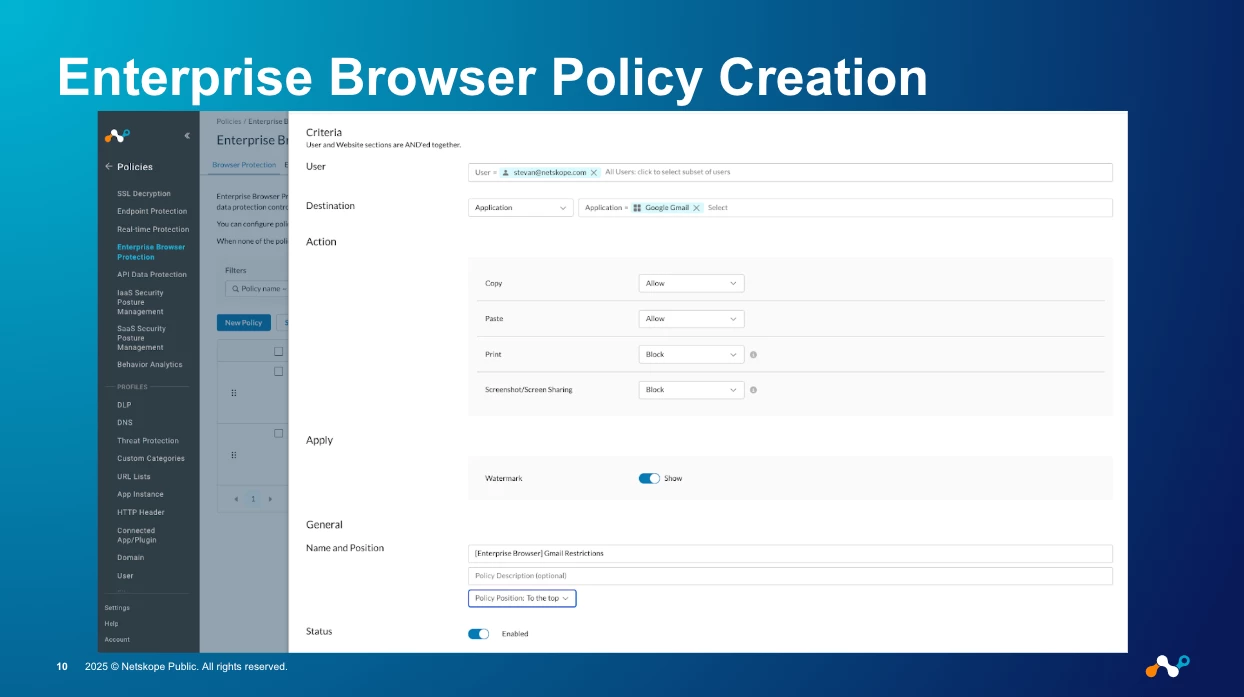
This is the game-changer. Your Netskope policies can now control the browsing experience itself. Instead of just blocking a URL, you can control granular user activities within that URL.
Within the Netskope UI, you'll find a new policy type: Enterprise Browser Protection. This allows you to define rules for specific users, groups, or applications to:
- Block Copy
- Block Paste
- Block Print
- Block Screenshot/Screen Sharing
- Enforce Watermarking
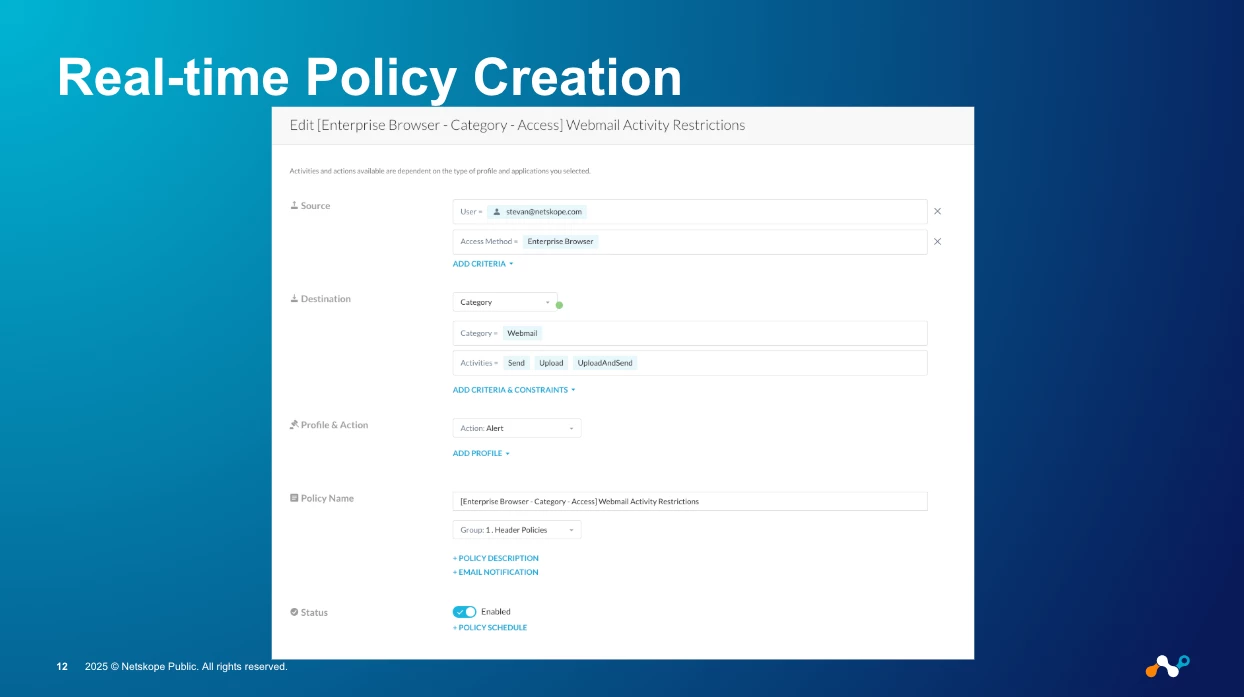
When the user tries to perform a blocked action, like printing, they are met with a simple, clear block message. If they take a screenshot, the policy can be configured to produce a blank screen. This stops data exfiltration before it happens, on any device.
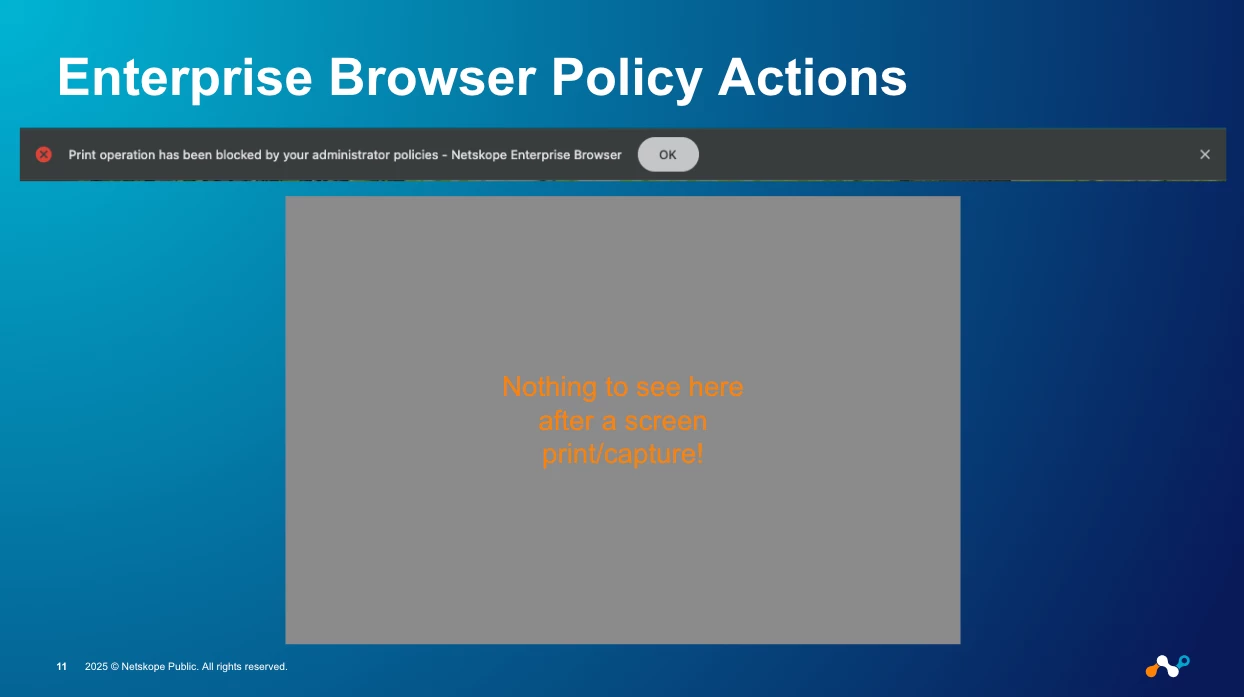
Pillar 2: Agentless Zero Trust Network Access (ZTNA)
This is the second "wow" feature. The Netskope One Enterprise Browser can access private applications—the internal-only wikis, dashboards, and tools—without a VPN client.
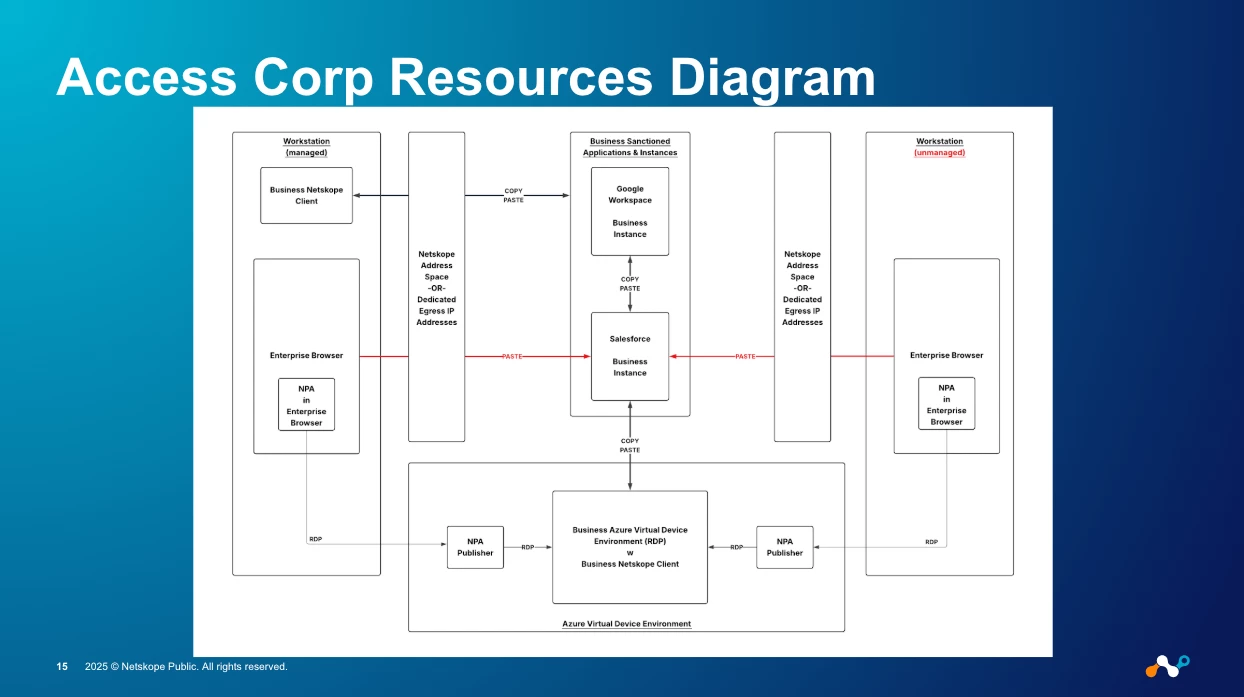
The browser has Netskope Private Access (NPA) capabilities baked in.
- For the Admin: You simply create a real-time policy in your Netskope tenant, allowing that user/group to access the defined private app. You can even set the "Access Method" to "Enterprise Browser" to create specific policies.
- For the User: They click a bookmark on their Company Workspace portal. The Enterprise Browser transparently and securely tunnels only that browser session to the private app via the NewEdge network.
The unmanaged device never gains network-level access. You've provided secure access to a private app on a BYOD device, solving a problem that was previously "impossible" or required a clunky VDI.
Pillar 3: Extension & Threat Governance
The browser-as-a-platform is a massive attack vector. Malicious extensions are a huge blind spot. The Netskope One Enterprise Browser gives you full control.
From the "Extension Governance" tab, you can create policies to:
- Block Extensions: Default to blocking all extensions.
- Allow Extensions: Create an exception list for approved extensions.
- Force Install: Ensure critical security or productivity extensions are always present.
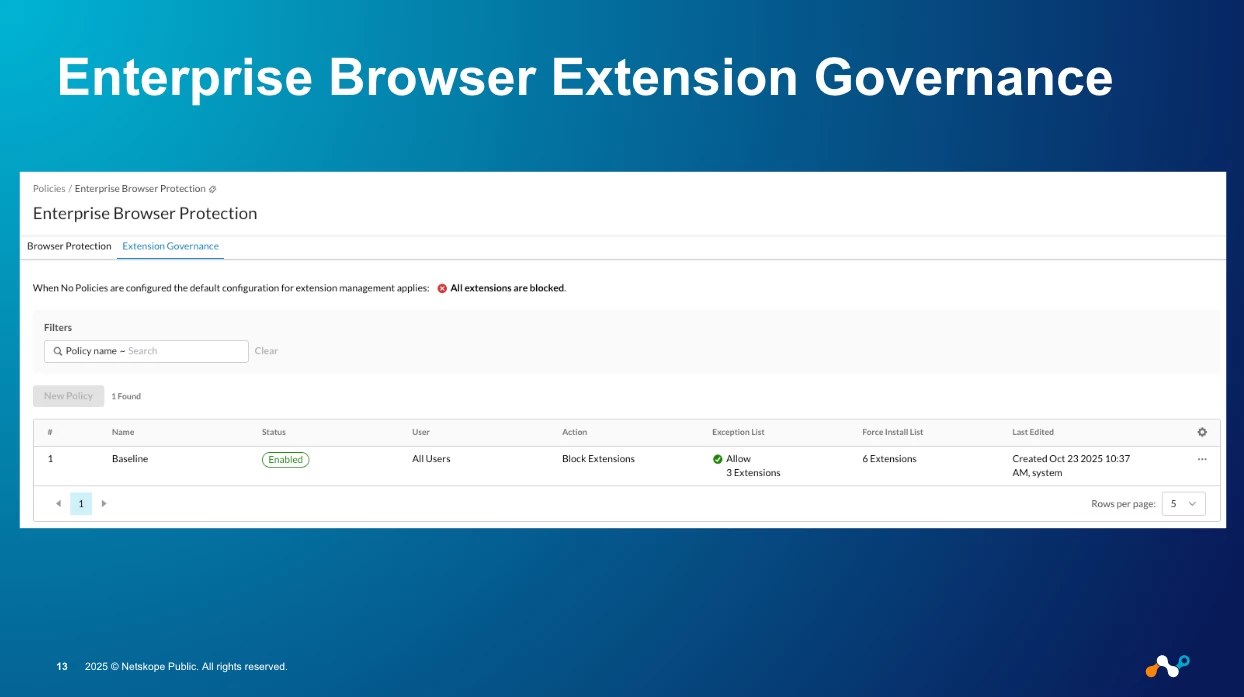
This, combined with Netskope's standard real-time threat protection and content filtering (which are extended to the browser), hardens the browser against both data leakage and incoming threats.
Pillar 4: Simplified User Provisioning & Management
Security tools that are hard to use don't get used. The Enterprise Browser is built for speed and simplicity.
- For the Admin: You don't manage individual browsers. You create "Company Workspaces" in the Netskope UI. Here, you define the application links (SaaS and private) that users assigned to this workspace will see.
- For the User: They receive an invite, perform a self-service install, and log in once via your existing SAML/SSO provider. They are then presented with a clean, simple portal showing their "Company Workspace" apps.
This self-service model means IT isn't bogged down with configuration tickets, and users (like new M&A employees) can get productive in minutes.
Putting It All Together: A Practical Use Case
Let's walk through the "Access Corp Resources" use case.
The Scenario: A new BYOD contractor needs access to Salesforce (a sanctioned SaaS app) and an internal-only Jira server (a private app). You must prevent them from copying customer lists out of Salesforce but allow them to paste notes into Salesforce cases.
The Workflow:
- Administration
- Create a "Contractor Workspace" in Netskope and add the Salesforce and Jira app links.
- Create an "Enterprise Browser Protection" policy that blocks "Copy" and "Print" for the Salesforce application when accessed by the "Contractor" group.
- Create a "Real-time Protection" policy allowing the "Enterprise Browser" access method to the "Jira - Private App" destination.
- End User
- Contractor receives an email. They download and install the Netskope One Enterprise Browser.
- They launch the browser, are routed to your Okta (or other SSO) login page, and authenticate.
- They land on their Company Workspace portal. They see two icons: "Salesforce" and "Jira".
- Actions
- The user clicks "Salesforce." They can view, edit, and paste text into cases. When they highlight a customer list and hit "Ctrl+C," the policy is enforced and the copy action fails. Data stays put.
- The user clicks "Jira." The browser's built-in NPA capability creates a secure, application-level tunnel. The Jira server login page appears. The user never saw a VPN client or a loading screen.
The Result: The contractor is productive in 15 minutes. Your corporate data is secure, even on an unmanaged device. Your IT team didn't have to configure a laptop or a complex VDI. This is what fast, secure, and easy operationalization looks like.
Requirements & Conclusion
This solution is powerful, and getting started is straightforward.
Key Requirements:
- Licensing: Enterprise Browser requires licensing. You'll need to speak with your account management team for access.
- SSO: The solution relies on Forward Proxy configurations, so any supported SAML/SSO provider will work. Netskope provides instructions for Okta, PingIdentity, and Msft Entra ID.
- Limitations: It's important to note that Enterprise Browser is NOT accessible for applications accessed through China PoPs.
The Final Word
The line between the corporate network and the public internet has been permanently erased. The browser is the new endpoint, and it demands its own security model.
The Netskope One Enterprise Browser provides that model. It gives security architects, analysts, and CSOs the one thing they've been missing: the ability to extend granular, zero-trust data and threat protection to any user on any device, without the baggage of clients, hardware, or complex network configurations.
Netskope One Enterprise Browser, secure the once unsecurable!
(Enhanced with Google Gemini)








