On May 3rd 2023 Google Registry announced the release of eight new top-level domains (TLD). Two of these domains share the same naming conventions as common file names which are .zip and .mov. These TLDs could pose an increased risk to organizations through the use of social engineering attacks. For example https://github.com/kubernetes/kubernetes/archive/refs/tags/@v1.27.1.zip looks likes a legitimate domain to a GibHub repo to download a .zip file for kubernetes, however the link actually takes you to the domain of v1.27.1.zip.
How does Netskope mitigate the threat from these domains?
The Netskope platform can help prevent phishing attacks through the use of deep learning for phishing website detection and remote browser isolation which work across all top-level domains.
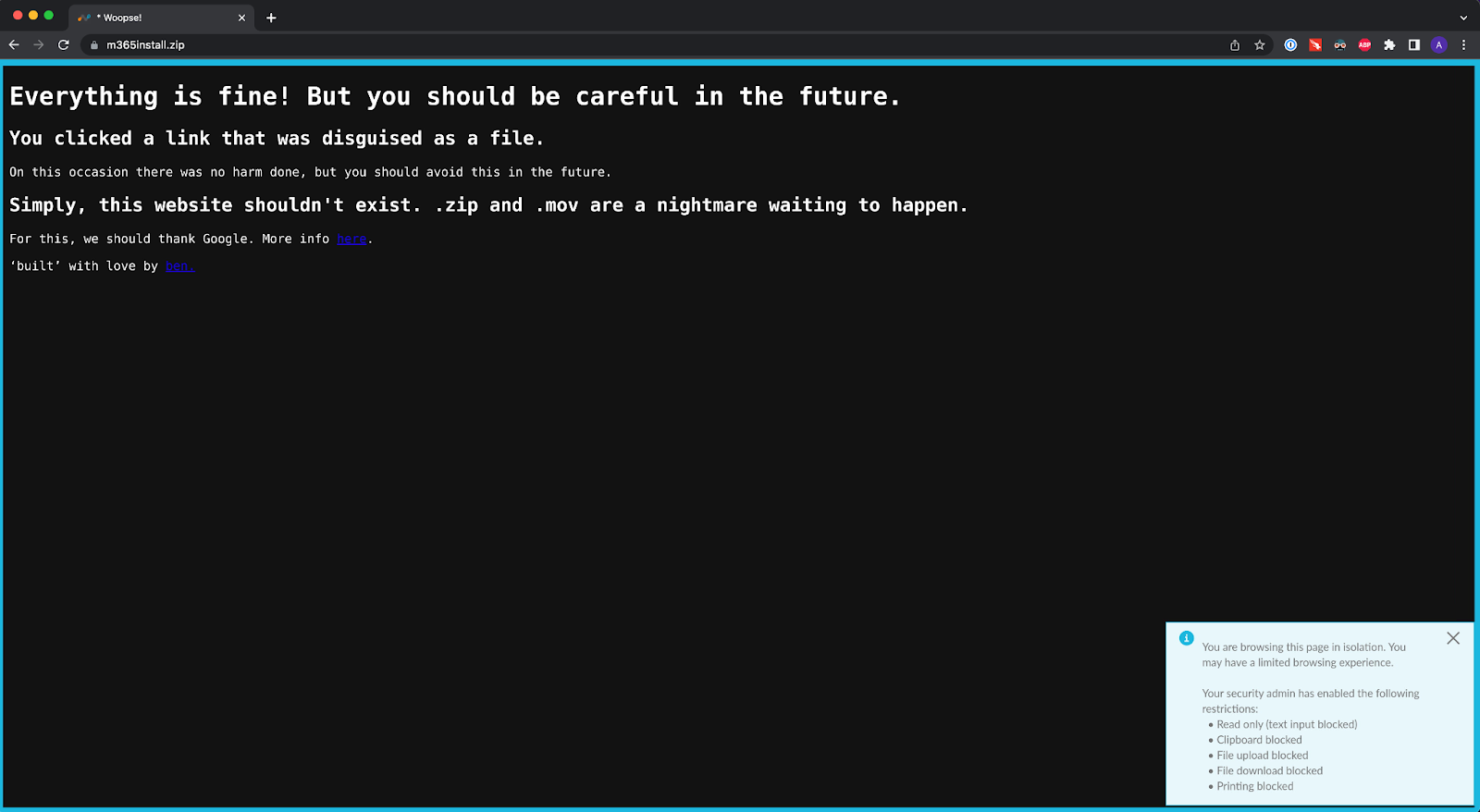
Figure 1: Testing RBI with m365install.zip domain
How can Netskope help provide insight into domain usage in an organization’s environment?
Even with controls in place to help mitigate this threat, using Netskope Advanced Analytics can provide insights into where these domains show up in an organization’s environment and insights into potential missed malicious activity.
To start we can create a dashboard in Advanced Analytics to be able to monitor visits to these domains, bytes downloaded and uploaded, and other contextualizing information.
Under the Advanced Analytics tab go to “Personal.” Here we can create our own dashboard and tune them before sharing them organization wide. Select “New” in the top right hand corner then “New Report” in the drop down menu.
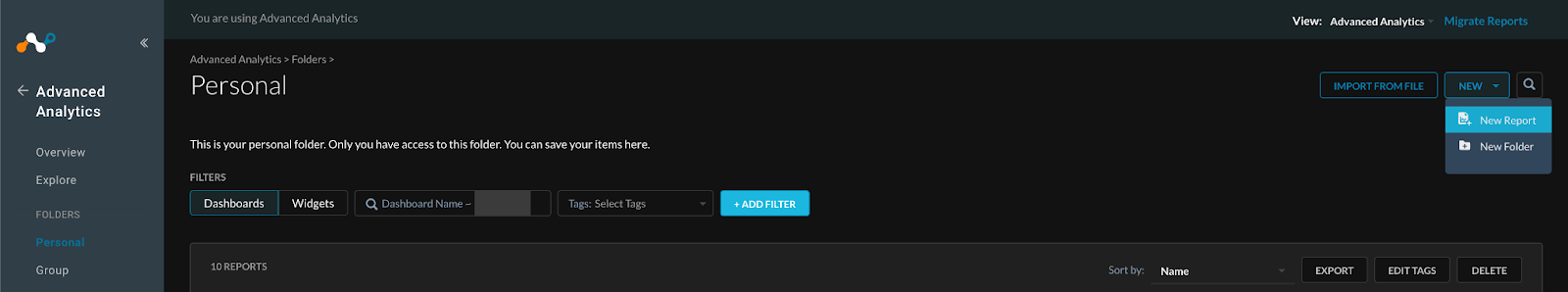
Figure 2: Creating New Advanced Analytics Dashboard
Select “Edit Dashboard”
Figure 3: Newly created dashboard
Rename the dashboard and click “Add” and “Visualization” in the drop down menu
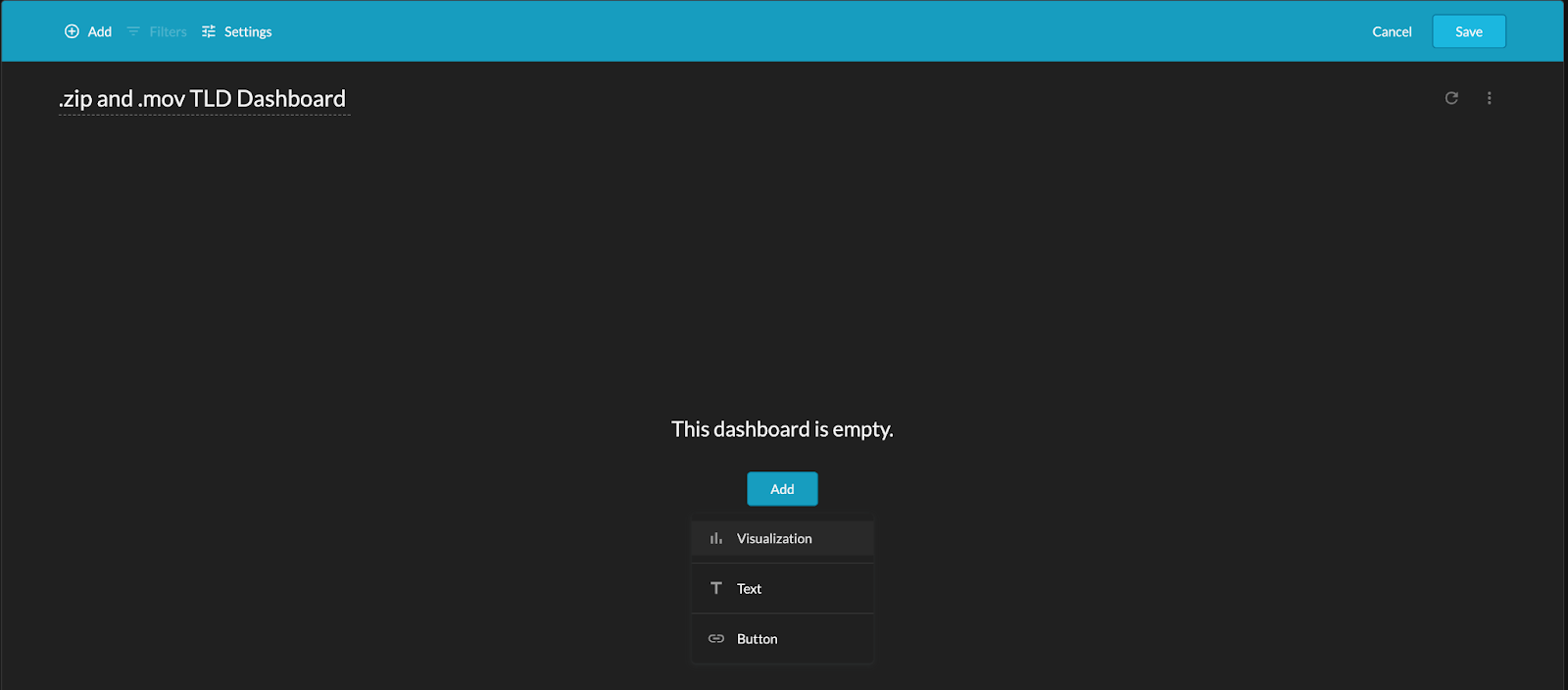
Figure 4: Adding Widget to Dashboard
To get good contextualization and filtering for this potential threat, select “Transaction Events.” In the left hand column, select “User,” “Application,” “Domain,” “Site,” “URI,” “Port,” “Protocol,” “Source IP,” “Source Country,” “Destination IP,” “Destination Country,” “Event Timestamp,” “Bytes Downloaded,” “Bytes Uploaded,” and “Total Bytes.” These fields provide an excellent view of the events and allows easy filtering based on the particular domains that is desired to be viewed without worrying about picking up .zip and .mov files that users may be uploading or downloading.
To filter Domains select the filter symbol within the left hand column
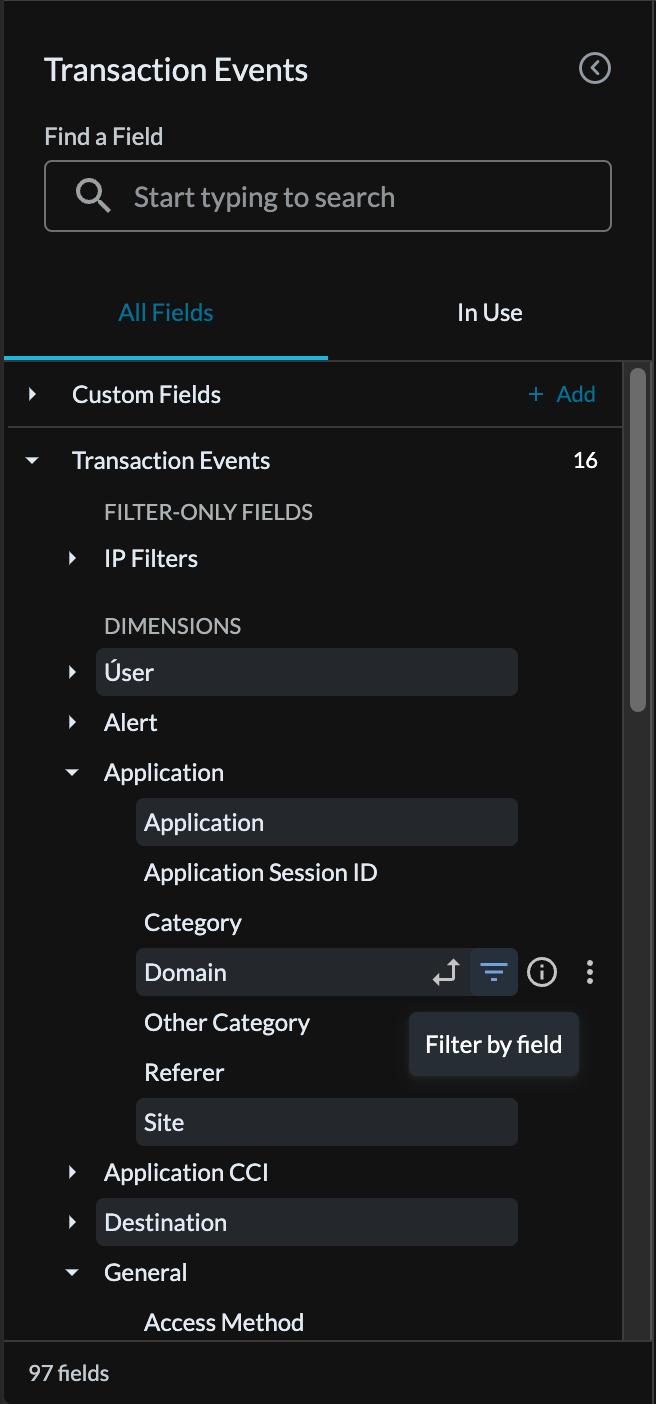
Figure 5: Filtering in Advanced Analytics
For the domain filter, select “ends with" from the drop down filter and put .zip in the filter field along with how far back to search.
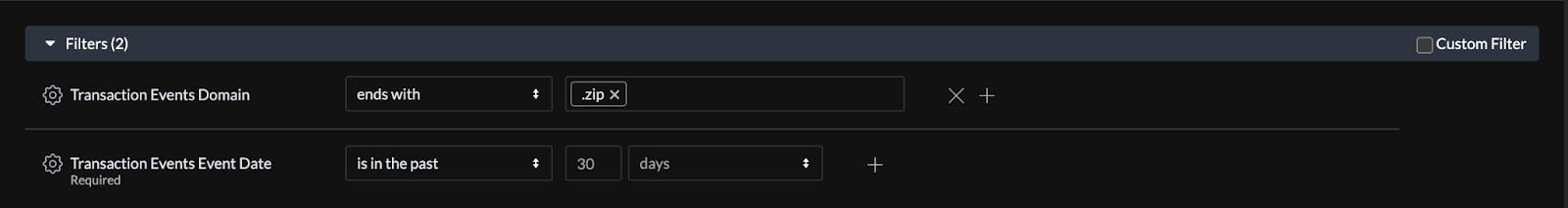
Figure 6: Filtering .zip domains
Hit “Run” and make sure the table “Visualization” is selected in the “Visualization” tab
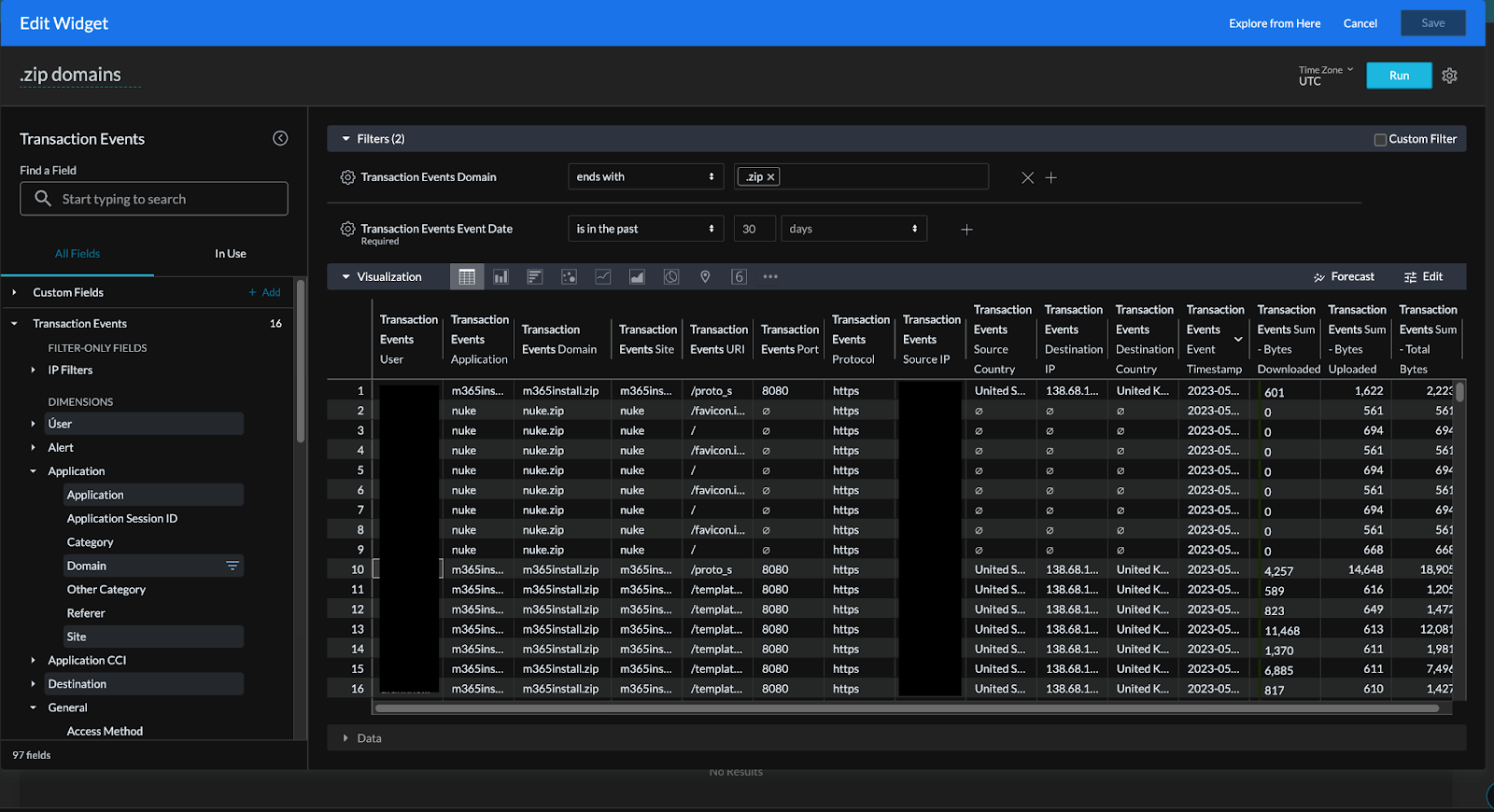
Figure 7: Visual Representation of data queried by widget
Once you save the widget, it will be present on the dashboard in which you can schedule run times, have it refresh every time it is loaded, and schedule delivery of the dashboard contents to team members. To find use of .mov domains repeat the same steps but add .mov into the domain filter field instead of .zip.
Now the organization has visibility into where .zip and .mov domains show up in the organization and users who go to them. From here leaders can make informed decisions on use cases and exposure to support other security policy decisions. Security personnel can look through the data for any suspicious activity such as an abnormal geographical location source or destination, large number of uploads or downloads, and abnormal port or protocol usage at a glance.







