With the growing popularity and use of ChatGPT, it is increasingly important to also monitor and secure private details and company confidential information from being shared with ChatGPT.
As the Customer Zer0 team (CISO group), we have implemented some DLP rules for ChatGPT. Please note that currently, Netskope does not yet have a predefined connector for ChatGPT. We would hence need to create a custom connector so that DLP rules can be applied instead of an outright block to the webapp. We want our users to continue to use ChatGPT with discretion in an enterprise environment. This custom connector can be built from HAR logs.
Here’s what we have in place:
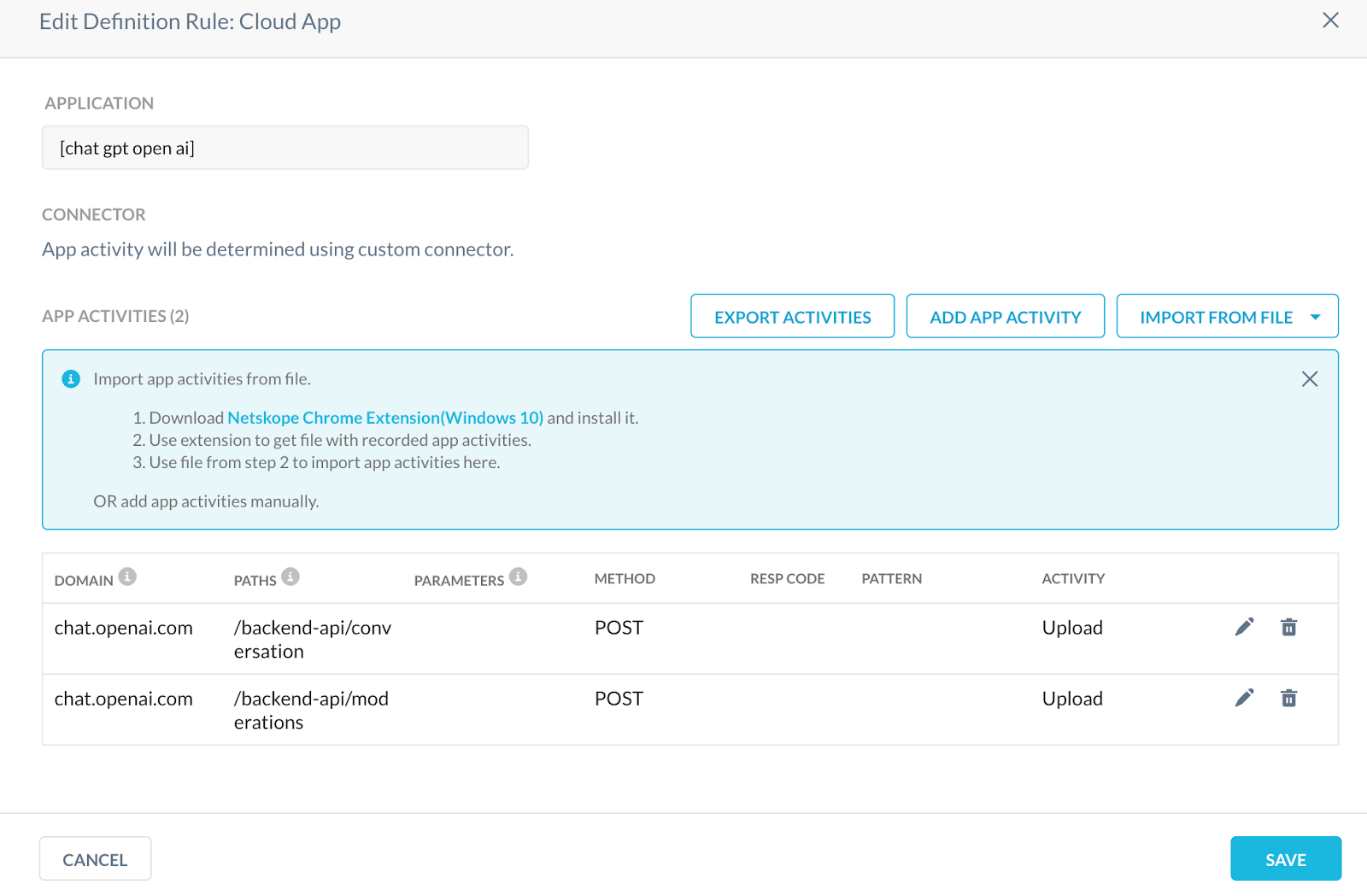
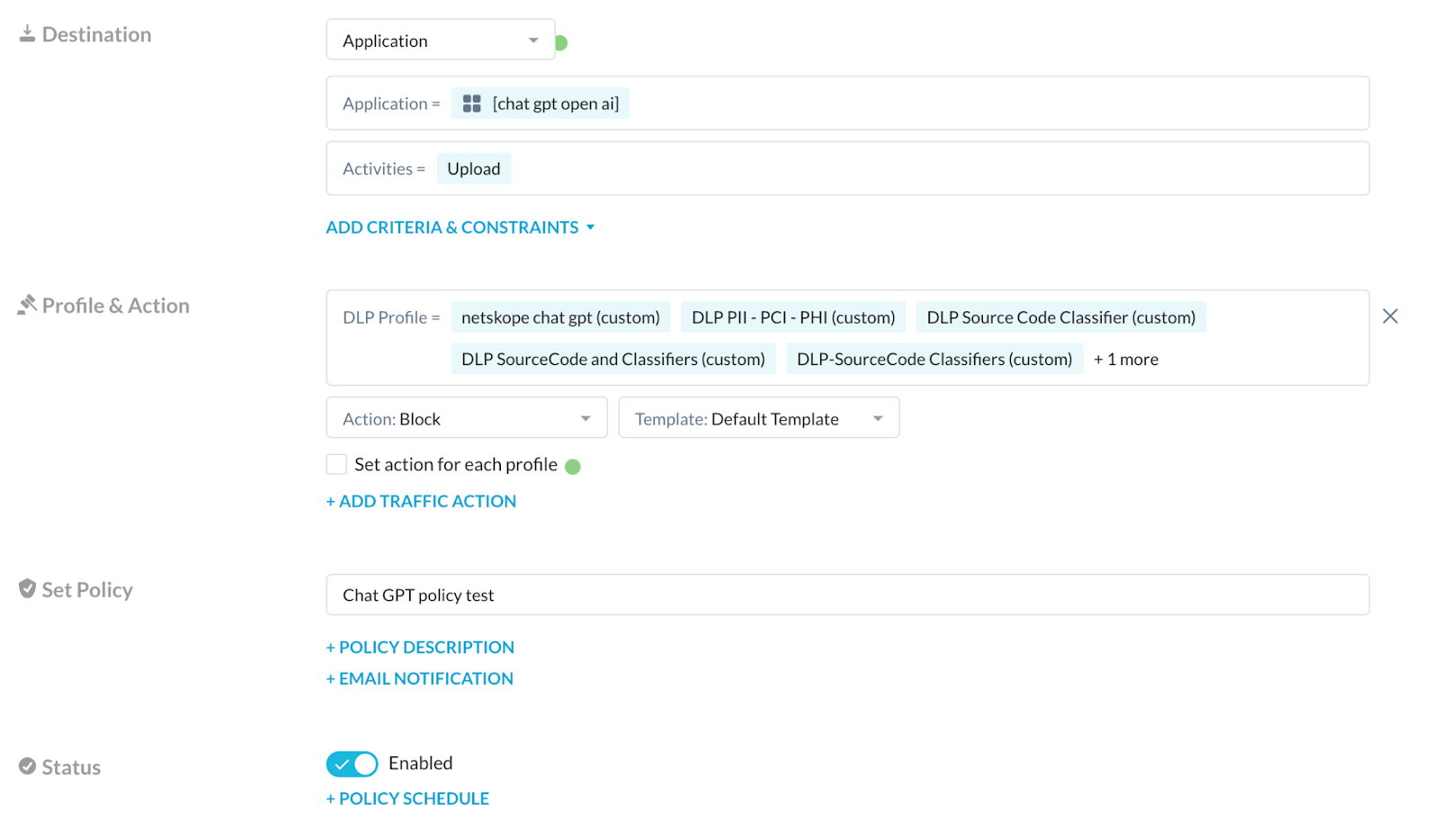
Realtime policy
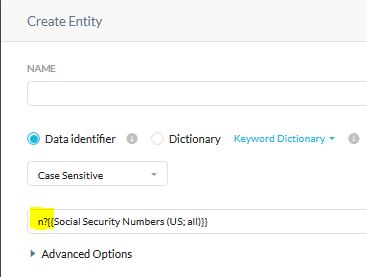
The Netskope chatgpt custom DLP profile contains the ‘netskope’ keyword.
Results and end-user experience
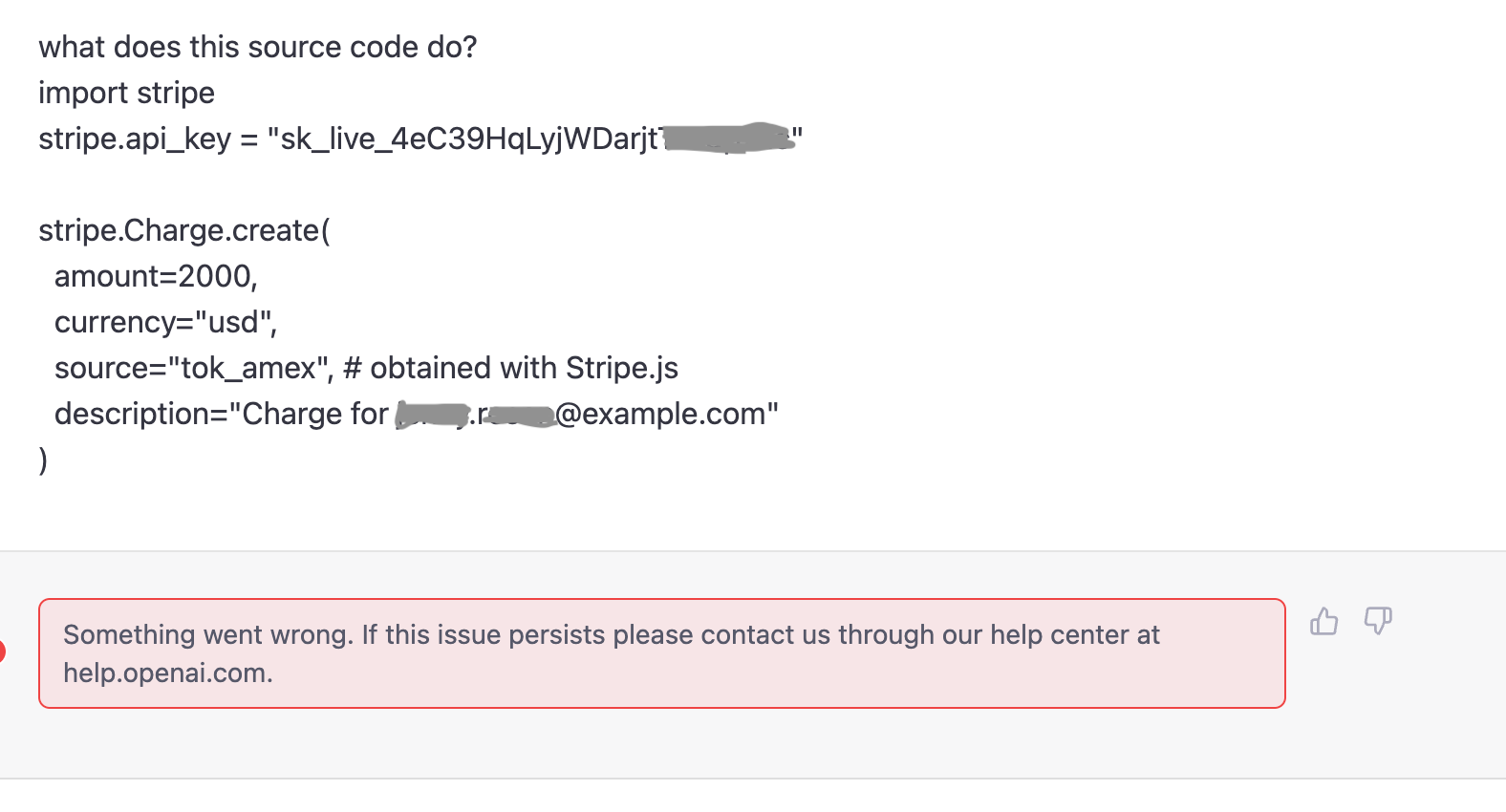
In this example, DLP source code classifier is getting triggered, and hence the question is not being posted to ChatGPT.
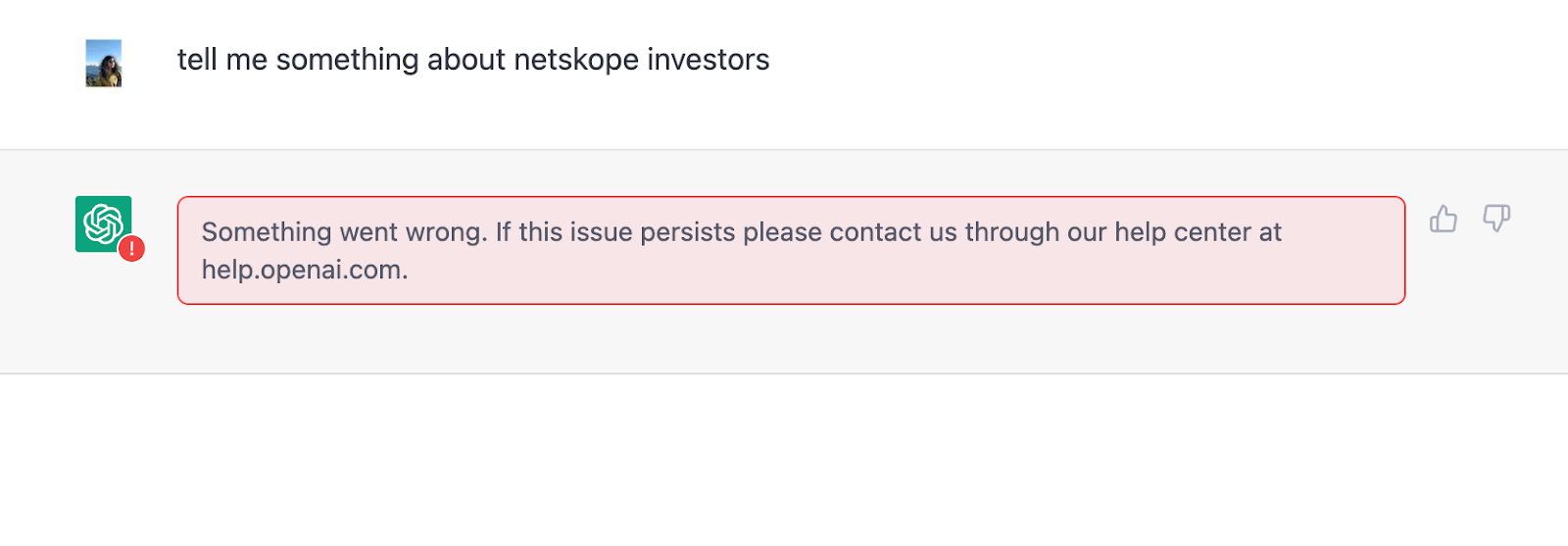
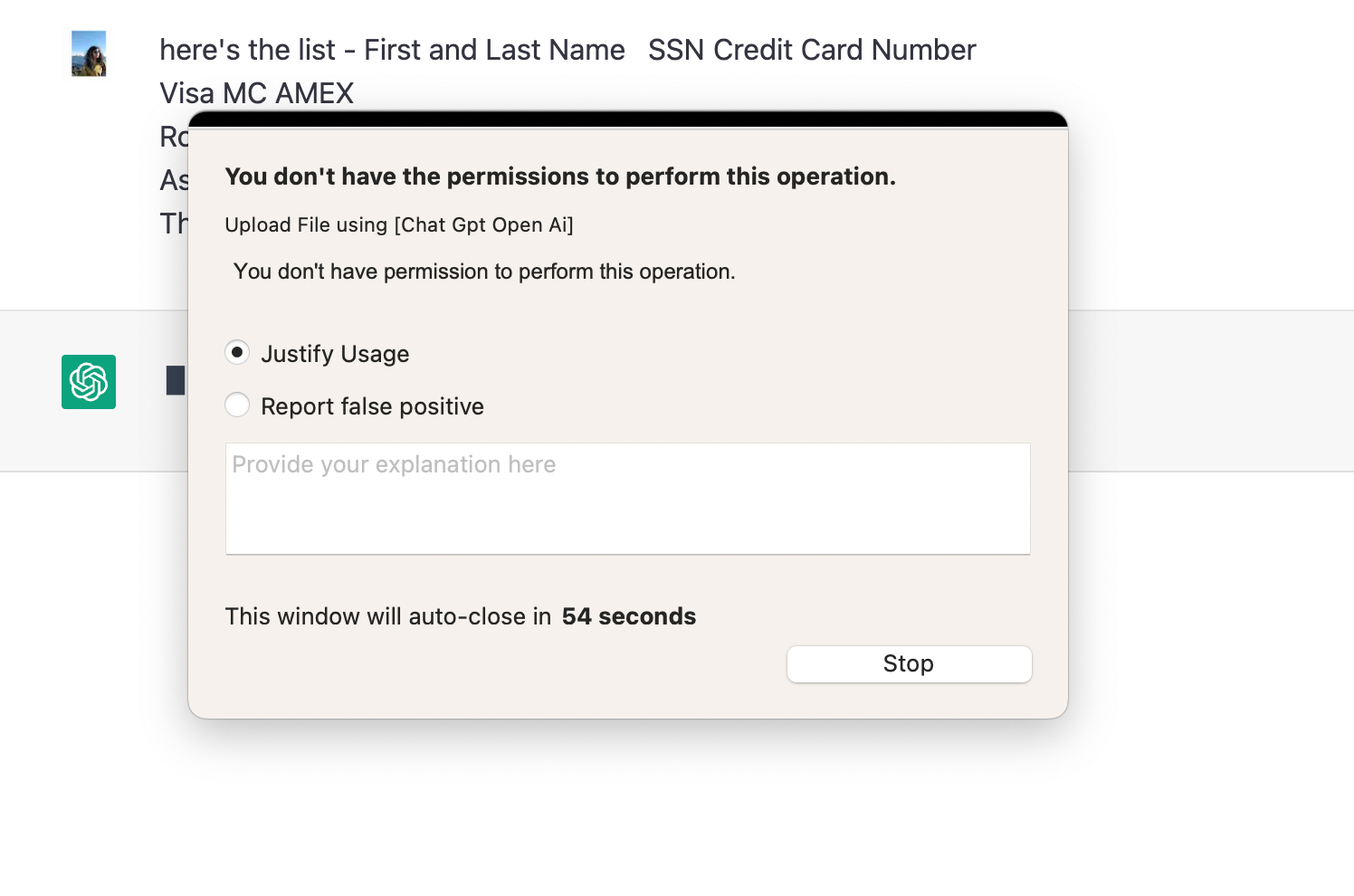
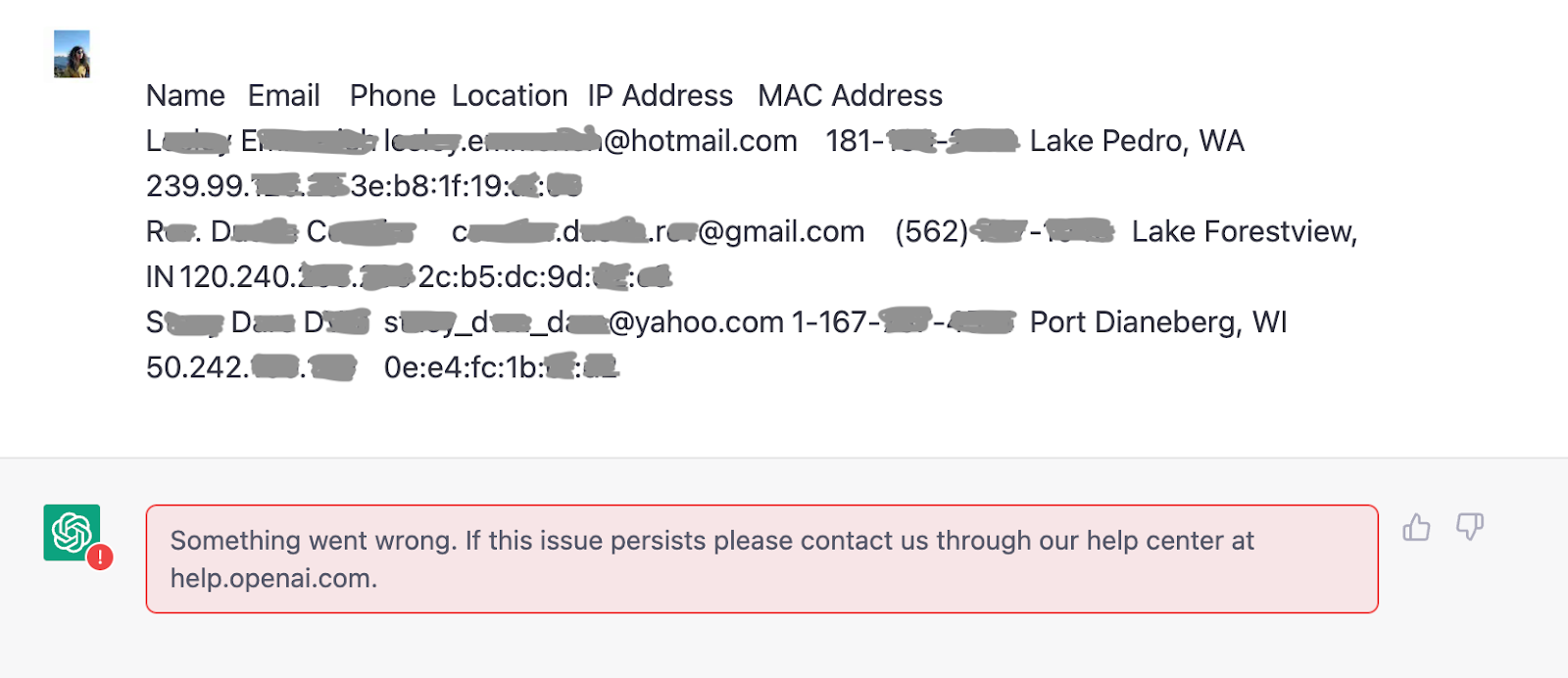
PII and PCI data being blocked from getting posted to ChatGPT.
Let us know which use cases you would like to implement for ChatGPT with Netskope DLP.
Note: This blog post was tested and developed when the predefined ChatGPT connector was not yet available to configure in Netskope's Real-time policies. With R104 now rolled out, the predefined ChatGPT connector is available to be configured in policies.
Please refer https://community.netskope.com/t5/Next-Gen-Secure-Web-Gateway-SWG/Netskope-Next-Gen-Secure-Web-Gateway-Controls-for-ChatGPT/m-p/3646 for more details.